At Acronis, we’ve taken the ability for security software to defend itself seriously right from the start. In 2017 and 2018, our solutions were tested for self-defense capabilities by independent labs, and their research revealed Acronis Cyber Protection Solutions delivered excellent results.
Of course, we continue to improve our technologies with every release and constantly research what we can improve in all aspects of cyber protection.
Given our mission of delivering cyber protection solutions that ensure the safety, accessibility, privacy, authenticity, and security (SAPAS) of data, in preparing for our upcoming Acronis Cyber Protect Cloud launch, we improved the self-defense capabilities even further.
In 2019, Acronis became a member of the Microsoft Virus Initiative, passed all of the required tests, and became officially recognized as a security solution for Windows. That allows the upcoming Acronis Cyber Protect Cloud to use the Early Launch Antimalware (ELAM) driver and Protected Process Light (PPL) feature of the Windows operating systems.
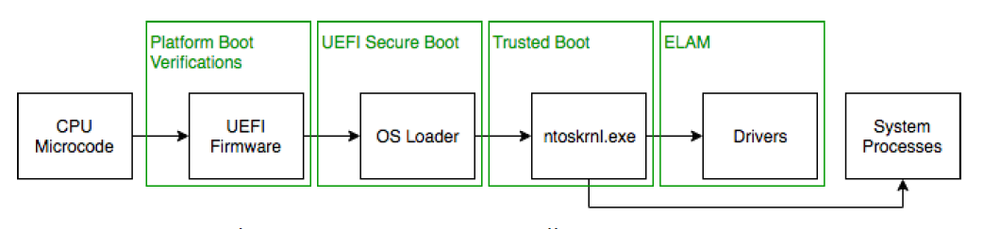
As shown by Broderick Ian Aquilino in his “Relevance of Security Features Introduced in Modern Windows OS” (2019), “ELAM ensures that no malicious third-party drivers that may potentially be a rootkit are initialized before an antimalware software has completely loaded.”
The ELAM feature provides a Microsoft-supported mechanism that allows antimalware (AM) software to start before other third-party components. AM drivers are initialized first and allowed to control the initialization of subsequent boot drivers, which enables them to potentially block unknown boot drivers from malicious rootkits and bootkits. When a system starts, ELAM scans all third-party apps and drivers and sends the system kernel a report that includes all of the device and software drivers. Those are then classified as one of the following four groups: good, bad, bad but boot critical, and unknown. All drivers are loaded in Windows by default, except for those marked as bad drivers.
Microsoft has another connected technology, Protected Process Light (PPL), which ensures that the operating system only loads trusted services and processes. To be trusted, they should have an internal or external signature that meets the Windows requirements. PPL loosened some of the restrictions on which DLLs are considered valid for loading into a protected process and introduced different signing requirements for the main executable. Now, the only type of protected process that a third-party can create in Windows operating systems is an antimalware PPL (AM-PPL).
Acronis created its own ELAM driver for its cyber protection products and uses this driver for the AM-PPL protection of the Acronis Cyber Protect Cloud service. Acronis’ ELAM driver allows the listing of specific certificate hashes that are used to allow or deny a DDL from loading as a PPL protected process.
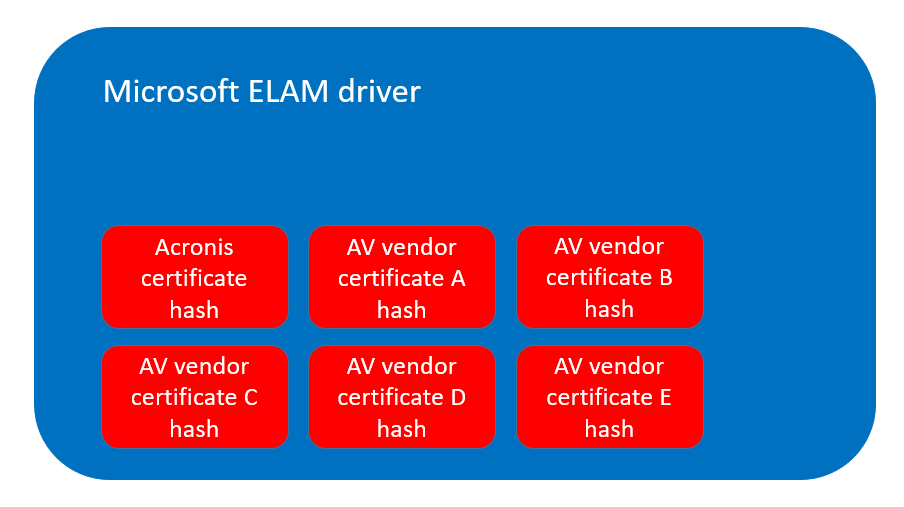
Acronis’ ELAM driver allows the listing of specific certificate hashes that are used to allow or deny a DDL from loading as a PPL protected process
Why is all this important?
Not so long ago, SafeBreach Labs discovered a new vulnerability in Symantec’s Endpoint Protection software. This vulnerability allows hackers to bypass Symantec’s self-defense mechanism and achieve defense evasion, persistence, and privilege escalation by loading an arbitrary, unsigned DLL into a process that is signed by Symantec and runs as NT AUTHORITY\SYSTEM. You need to have admin rights to exploit it but, as we know, getting admin privileges is not that hard.
Exploiting such a vulnerability is very useful for cybercriminals because they can do whatever they want in the system without being detected ... and this is not what you expect from a security solution.
In the case of Acronis Cyber Protect, the service is based on an ELAM driver that is protected against the kind of attack described above and service does not even invoke an exploitable code path (IWbemServices as described in SafeBreach’s vulnerability disclosure).
More than that, Acronis Cyber Protect should not be vulnerable to this type of attack since the threat is based on loading the arbitrary unsigned (or even signed with some “not approved by vendor” certificate) DLL in the security solution's main service.
Final thought
There’s one trend that’s been constant in cybersecurity: cybercriminals are always looking for ways around the defenses that users put in their way. As hackers look to disarm antimalware software directly, the importance of strong, reliable self-defense mechanisms becomes critical for any solution built for the current and future threat landscapes.
About Acronis
Acronis is a Swiss company, founded in Singapore. Celebrating two decades of innovation, Acronis has more than 1,800 employees in 45 locations. The Acronis Cyber Protect Cloud solution is available in 26 languages in over 150 countries and is used by 20,000 service providers to protect over 750,000 businesses.






