General Information
Preventing unauthorized downloading as well as the uploading of inappropriate software and data is important when trying to protect and administer a company’s computer network.
DeviceLock DLP is easy to install. Administrators can have instant access from remote computers when necessary. The administrator of the machine or domain can designate user access to printers, clipboard, iPhones and iPads, floppy drives, optical drives, other removable media, tape drives, Media Transfer Protocol (MTP), WiFi, and Bluetooth adapters, or USB, FireWire, infrared, serial and parallel ports. All types of file systems are supported.
DeviceLock DLP provides control over network communications. Administrators can designate user access to the FTP, HTTP, IBM Notes, SMB, SMTP, MAPI (Microsoft Exchange), Telnet and Torrent protocols, instant messengers (Skype, Telegram, Viber, WhatsApp, ICQ Messenger, Jabber, IRC, Mail.ru Agent), cloud storages (Amazon S3, Dropbox, Box, Google Drive, Microsoft OneDrive, etc.), Web Mail and social networking applications (AOL Mail, freenet.de, Gmail, GMX Mail, Hotmail (Outlook.com), Mail.ru, NAVER, Outlook Web App (OWA), Rambler Mail, T-online.de, Web.de, Yahoo! Mail, Yandex Mail, Zimbra; Facebook, Google+, Instagram, LinkedIn, LiveJournal, MeinVZ, Myspace, Odnoklassniki, Pinterest, StudiVZ, Tumblr, Twitter, Vkontakte, XING, Disqus, LiveInternet.ru).
DeviceLock extracts and filters the content of data copied to removable drives and plug-n-play storage devices, as well as that transmitted over the network. Administrators can create rules that specify which content can be copied and transmitted.
DeviceLock can audit user activity for a particular device type or protocol on a local computer. Based on the user’s security context, this capability allows you to audit activities that belong to a certain user or user group. DeviceLock employs the standard event logging subsystem and writes audit records to the Windows event log.
DeviceLock can generate real-time security alerts when significant incidents, events or problems occur. Real-time alerting simplifies event monitoring and log management and helps you response faster and more efficiently to security incidents and policy violations. Alerts are available via Simple Mail Transfer Protocol (SMTP), Simple Network Management Protocol (SNMP) and syslog.
DeviceLock supports data shadowing - the ability to mirror all data copied to external storage devices, transferred through serial and parallel ports or transmitted over the network. A full copy of the files can be saved into the SQL database. Shadowing, like auditing, can be defined on a per-user basis.
Moreover, the DeviceLock data shadowing function is compatible with the National Software Reference Library maintained by the National Institute of Standards and Technology (NIST) and with the Hashkeeper Database designed and maintained by U.S. DOJ National Drug Intelligence Center (NDIC).
The data logged by DeviceLock can be checked against hash databases (collections of digital signatures of known, traceable data) and used in computer forensics.
You may also create your own database with digital signatures (SHA-1, MD5 and CRC32 are supported) of critical files and then use it for tracing purposes. For example, you can trace which users are copying signatured files, at what time, and with which devices.
For information on how to use hash databases in cooperation with DeviceLock, please contact our technical support team.
More information about hash databases and their samples can be found on the National Software Reference Library’s Web site at
www.nsrl.nist.gov.
Also, DeviceLock provides instant searching of text across shadowed files and audit logs stored in the centralized database. DeviceLock can automatically recognize, index, search and display documents in many formats, such as: Adobe Acrobat (including encrypted files if the type of encryption in the file is one of the following: 40-bit RC4, 128-bit RC4, 128-bit AES and 256-bit AES, and the file permissions do not disable text extraction) (PDF), Ami Pro, AutoCAD (DWG, DXF), Archives (GZIP, RAR, ZIP), Lotus 1-2-3, Microsoft Access, Microsoft Excel, Microsoft PowerPoint, Microsoft Visio, Microsoft Word, Microsoft Works, OpenOffice (documents, spreadsheets and presentations), Quattro Pro, WordPerfect, WordStar and many others.
Note: Content in AutoCAD (DWG, DXF) file formats can be identified on Windows XP and later systems. |
In addition to the standard (per computer) way of managing permissions, DeviceLock also provides you with a more powerful mechanism - permissions and settings can be changed and deployed via Group Policy in an Active Directory domain.
Tighter integration into the Active Directory is a very important function of DeviceLock. It makes DeviceLock’s permissions management and deployment easier for large networks and more convenient for system administrators.
Integration into the Active Directory eliminates the need to install more third-party applications for centralized management and deployment. DeviceLock does not need to have its own server-based version to control the entire network, instead it uses standard functions provided by the Active Directory.
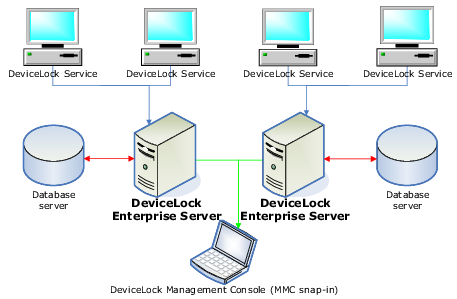
DeviceLock DLP consists of three parts: the agent (DeviceLock Service), servers (DeviceLock Enterprise Server and DeviceLock Content Security Server), and management consoles (DeviceLock Management Console, DeviceLock Group Policy Manager, and DeviceLock Enterprise Manager).
1. DeviceLock Service is the core of DeviceLock. DeviceLock Service is installed on each client system, runs automatically, and provides device and network protection on the client machine while remaining invisible to that computer’s local users.
2. DeviceLock Enterprise Server (DLES) is an optional component for centralized collection and storage of the shadow data and audit logs. DeviceLock Enterprise Server uses a database server (SQL Server or PostgreSQL) to store its data. You can install several DLES instances and database servers to balance the network load.
DeviceLock Content Security Server is another optional component which includes Search Server for instant search of text within shadowed files and other logs stored on DeviceLock Enterprise Server. For more information, see
DeviceLock Content Security Server later in this chapter.
3. The management console is the control interface that systems administrators use to remotely manage each system that has DeviceLock Service. DeviceLock ships with four different management consoles: DeviceLock Management Console, DeviceLock Enterprise Manager, and DeviceLock Group Policy Manager (integrates into the Windows Group Policy Editor). DeviceLock Management Console is also used to manage DeviceLock Enterprise Server and DeviceLock Content Security Server.