On March 22, 2018, the City of Atlanta, Georgia was struck by a ransomware attack that crippled municipals systems and forced the city’s IT team to verify every machine’s integrity. The strain of ransomware was determined to be Samas ransomware (also known as ‘SamSam’ or ‘Samsa’). Written by Ravikant Tiwari
SamSam was discovered in early 2016 and is believed to be spread through the Gold Lowell threat group. Previously, this ransomware has successfully targeted some high-profile victims, including several government, healthcare and ICS systems.
The notable incidents were attacks on:
- Colorado's Transportation Department
- Kentucky Hospital
- Mississippi Valley State University
- in Greenfield, Indiana;
- Adams Memorial Hospital in Decatur, Indiana;
- The municipality of Farmington, New Mexico;
- Cloud-based EHR (electronic health records) provider Allscripts;
- And an unnamed ICS (Industrial Control Systems) company in the U.S.
The total earning of the ransomware was estimated as nearly $850,000 ... and that’s before demanding $51,000 from the City of Atlanta last week.
Spreading Mechanism
Delivery of this ransomware is mainly done by exploiting software vulnerabilities, although there could be other distribution vectors that are not currently well known.
Some of the earlier attacks used JexBoss (an open-source JBoss Application Server testing/exploitation tool) and reGeorg / tunnel.jsp (a tunneling tool) to gain entry into a targeted network by scanning for and exploiting the server-side vulnerabilities, and vulnerabilities in multiple java frameworks, platforms and applications (e.g., Java Server Faces - JSF, Seam Framework, RMI over HTTP, Jenkins CLI RCE, Remote JMX, etc.).
It’s also believed to exploit vulnerable remote desktop protocol (RDP) services to gain access to computers.
Technical Details
The SamSam ransomware is a dotnet executable. Since its discovery, we have seen multiple variants of this ransomware that use different execution strategies and obfuscation techniques to conceal itself from AV and static analysis tools. The core file encryption routine hasn’t changed much though.
The latest variants of SamSam are distributed in at least two components – a loader and the actual SamSam ransomware, which is encrypted in a file with extension name ‘.stubbin’. This delivery format makes it nearly impossible for static detection mechanisms to detect the file.
The loader is a very simple and small dotnet assembly which reads the ‘.stubbin’ file from the current execution location, decrypts it with the key and initialization vector (IV) derived from the hardcoded password, and loads it. The IV ensures distinct ciphertexts are produced, even when the same plaintext is encrypted multiple times, independently, with the same key.
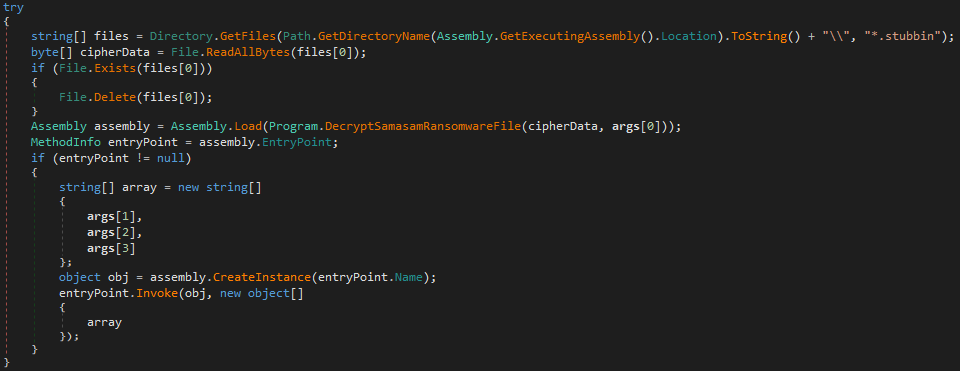
Figure 1: Loader code for SamSam
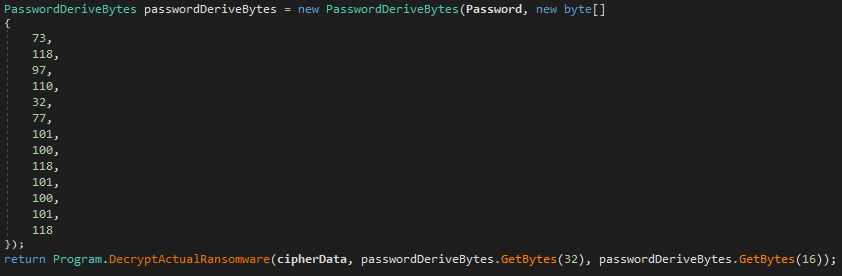
Figure 2: Hardcoded password and function call for decrypting SamSam ransomware
The earlier version of SamSam ransomware tries to delete all of the Windows shadow copies of user files before beginning to encrypt files. It also has a routine that kills any processes that might be locking the file SamSam wants to encrypt.
File encryption procedure
SamSam ransomware uses Rijndael block symmetric cipher for encryption with following configuration:
Before encrypting a new file, SamSam ransomware ensures there is enough space left on the disk for the operation.
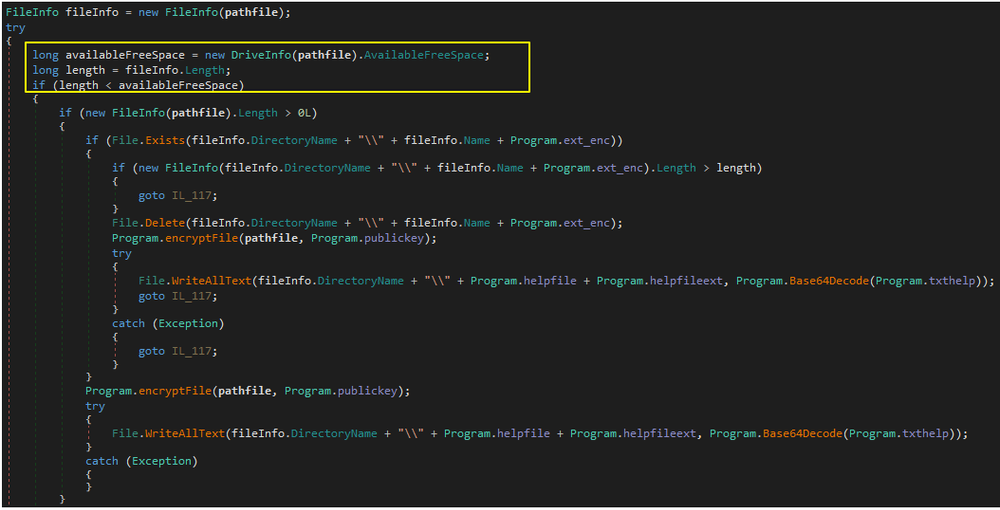
Figure 3: Checking available disk space
For each file, a separate Key and IV are generated using a cryptographic random number generator. This key and IV are encrypted with a hardcoded public RSA key and added as part of a custom header to a new file. To encrypt contents of the file, it reads it in chunk of 10240 bytes until the end of the file, encrypts the content, and writes it to a new file that has same filename but different extension (in this case it was ‘.encryptedRSA’). Finally, it deletes the original file from the disk.
Here is an example of the encrypted file’s header content.
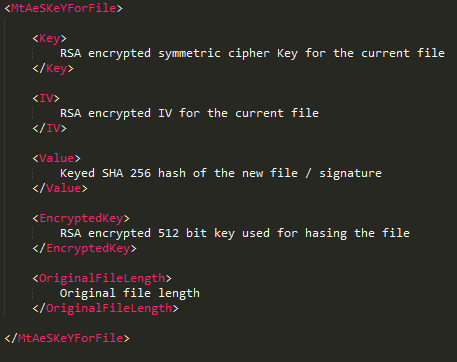
Figure 4: Header structure
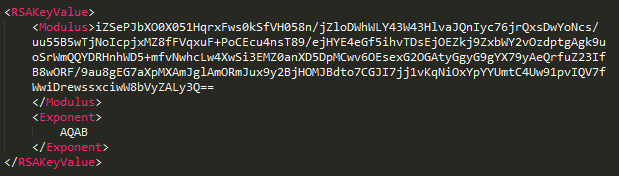
Figure 5: Hardcoded public RSA key
SamSam ransomware encrypts files that have the following extensions (although this extension list may be different in different variants of the ransomware).
Figure 6: Extension name list
After successfully encrypting files, the ransomware presents the following screen and demands a ransom:
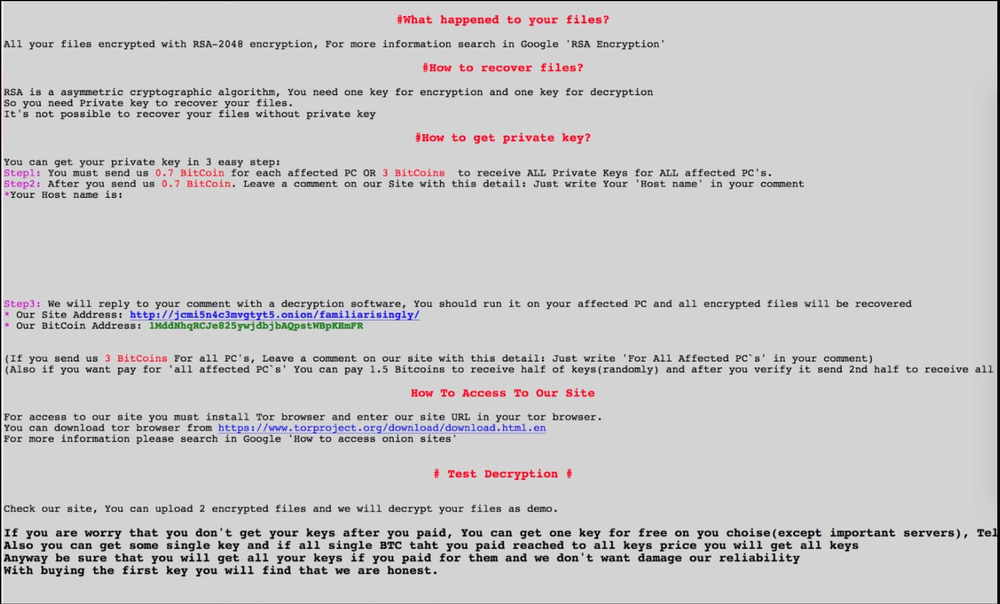
Figure 7: Recent variants ransom note
Backup files are under attack
If you’re familiar with backup file extensions, you will see that this sample of SamSam ransomware actually attacks Acronis backup files (*.tib) along with Windows backup files (*.bkf). If the ransomware is not detected and the backup service can’t protect its files, they will be encrypted and data will be lost.
“Back at the beginning of 2017, we predicted that there will be more and more ransomware attacks targeting backup files in order to cut any chance for users to restore their data and make them pay,” recalls Nikolay Grebennikov, VP of Engineering in Acronis. “Back then, we saw the importance of having multilayered data protection, integrating a combination of backup and security technologies into one product. We did it by releasing Acronis Active Protection, a set of technologies we are continuously improving in order to address 0-day threats to data. Thanks to this technology, any Acronis customers with Active Protection-enabled products are safe and secure”.
As expected, Acronis Active Protection successfully detects different variations of SamSam ransomware, such as the following three popular strains, and quickly restores encrypted files:
6bc2aa391b8ef260e79b99409e44011874630c2631e4487e82b76e5cb0a49307 939efdc272e8636fd63c1b58c2eec94cf10299cd2de30c329bd5378b6bbbd1c8 45e00fe90c8aa8578fce2b305840e368d62578c77e352974da6b8f8bc895d75b
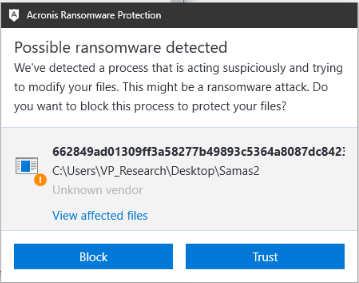
Figure 8: Acronis Active Protection successfully detects SamSam ransomware
But Acronis Active Protection not only detects and blocks ransomware. It also includes a self-defense mechanism that protects its own Windows process, ensuring that undetected ransomware cannot access and encrypt Acronis backup files. This is the multilayered protection mentioned above, which really provides the ultimate level of data security.
The effectiveness of Acronis’ self-defense capabilities was recently proven by an independent test that compared several corporate backup solutions. Nioguard testing laboratory reported that Acronis Backup delivered a “successfully passed tests” rating between 81 to 87 percent, while the next-best competitor scored a mere 19 percent. You can check the full report here.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




