You are on Global website. Change region to view location-specific content:
Global
English
Select another region
Choose region and language
Worldwide
- GlobalEnglish
- Americas
- Asia-Pacific
- Europe, Middle East and Africa
- Worldwide

Ease the labor-intensive and resource-consuming processes of DLP deployment and managment by choosing from a flexible set of central management consoles with the same UI. Depending on the organization’s IT environment, SMBs or large enterprises can choose the console that best fit their needs.
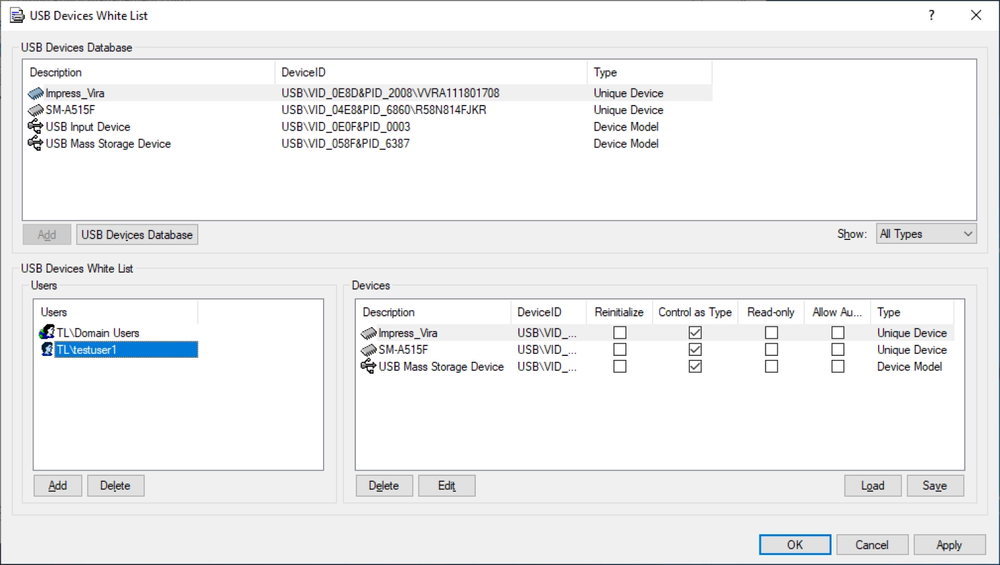
Allow granular controls over data access and transfer operations with the ability to manage exclusions to general DLP rules through wide allowlisting capabilities.
72% of employees share sensitive information. Prevent any data leaks headed your way.
Looking for help?
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.