You are on United States website. Change region to view location-specific content:
Global
English
Select another region
Choose region and language
- Americas
- Asia-Pacific
- Europe, Middle East and Africa
- Worldwide













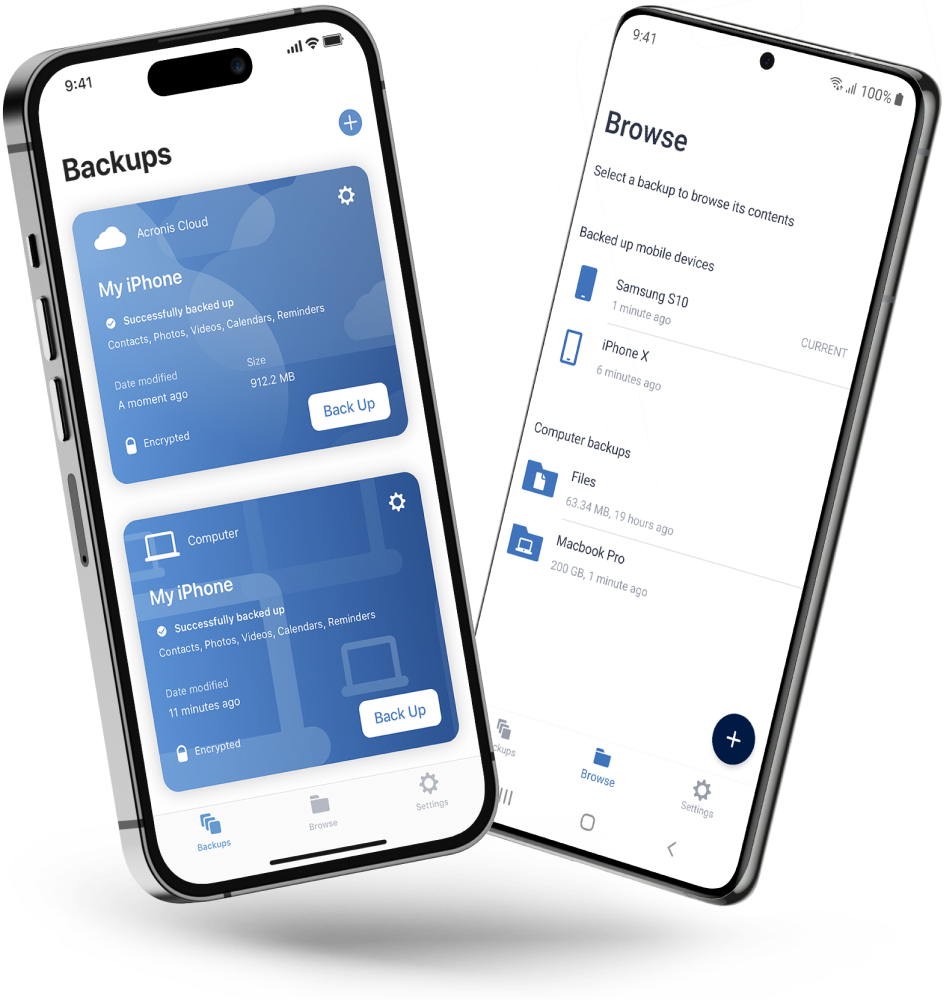
Never worry about losing your photos, videos, contacts or important files again. With the Acronis Mobile app, you can easily back up everything that matters on your phone and keep it safe in the cloud. Access your files anytime, anywhere from the Acronis Cloud, whether you're switching devices or just want peace of mind. It’s fast and always ready to protect your digital life.
Looking for help?
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.