Summary
- Acronis Threat Research Unit (TRU) analyzed recent samples of Akira and Lynx ransomware families to see the latest changes and tweaks implemented by the groups.
- Akira and Lynx share a RaaS model and double extortion tactics.
- Lynx is believed to incorporate elements of the leaked LockBit source code, and Akira shares similarities with Conti (which also influenced LockBit), suggesting a shared codebase heritage.
- They compromise systemsthrough stolen credentials, VPN vulnerabilities, reconnaissance, privilege escalation, de fense evasion, and data exfiltration/encryption, targeting SMBs with sophisticated yet recycled methods.
- The gangs disable security software, delete shadow copies, and clear event logs to avoid detection and hinder recovery.
- Fun fact: The Lynx ransomware sample we observed can print a ransom note on printers.
Introduction
In our ongoing efforts to track ransomware gangs and their activities, we’re spotlighting two groups that stood out in Q1 2025 and haven’t been covered in our previous research: Akira and Lynx.
- Akira has attacked over 220 victims, including many small businesses such as law firms, accounting firms and construction companies. It has also targeted potential managed service providers (MSPs), such as Hitachi Vantara[1] and Toppan Next Tech.[2]
- Lynx has hit around 145 victims. Its high-volume attack strategy points to a focus on small businesses, though specific examples are not widely available. One example reported is an attack on a Chattannoga, Tennessee-based CBS affiliate television station.[3]
While not all victims are MSPs, these gangs don’t discriminate when it comes to targets. They’re ready to strike any organization that promises a decent payout. That said, MSPs stand out as prime targets for cybercriminals because they provide access to a network of other customers, amplifying the potential reward.
[1] https://www.bleepingcomputer.com/news/security/hitachi-vantara-takes-servers-offline-after-akira-ransomware-attack/
[2] https://www.holdings.toppan.com/en/info/toppan_info20250408.pdf
[3] https://www.scworld.com/brief/cbs-affiliate-purportedly-compromised-by-lynx-ransomware-gang
Let’s dive deep into each of them:
1. Akira ransomware: An unpleasant comeback
2. Lynx ransomware focuses on private businesses
Akira ransomware: An unpleasant comeback
Akira ransomware emerged in 2022 with a low number of operations. In 2023 it entered the top 10 list of ransomware gangs, executing 174 attacks in that year. With that activity, spike analysis spotted that their samples shared a lot of similarities with Conti ransomware. Conti was linked to the Russian threat group called Wizard Spider, which in 2022 suffered a data leak that included source code and messages between its members. After that incident, Wizard Spider was dissolved. It is still unknown if Akira is a Wizard Spider rebranding or a new player that uses leaked code. In 2024, Akira again ranked in the top 10 list of ransomware gangs by the number of attacks (315 victims known).
Technical details
Delivery
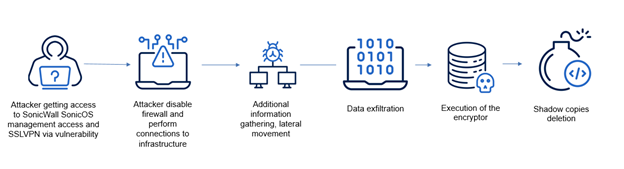
At the start of its operations, Akira ransomware used phishing attacks and vulnerabilities exploitation, including Cisco CVE-2023-20269, to gain access to victims. In 2024, Akira primarily targeted user VPNs by exploiting various vulnerabilities, including SonicWall Firewall CVE-2024-40766, which allowed attackers to disable firewalls and perform connections to infrastructure.
In 2025, TRU observed Akira operators using stolen / purchased admin credentials to attempt to gain access to machines / servers. When successful, they would disable security software. When unsuccessful, they would launch remote exfiltration and then encryption using legitimate tools that are often whitelisted and not scanned or monitored.
After obtaining access, attackers performed additional information gathering, lateral movement and detonation of the encryptor. Also, before encrypting files, Akira operators archived and exfiltrated victims files to their servers as a part of double-extortion scheme
Overview
The analyzed sample is a PE64 file written in C/C++ and compiled using Visual Studio Build tools. This file was first spotted in the wild at the end of 2024.
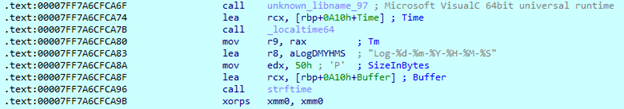
Execution starts from the WinMain function, which is large and contains a lot of code. At the start of the function, it obtains the current date and time and creates a log file in the same folder where it was executed.
The sample then obtains command line arguments and compares them with the saved list. Here are supported commands and their description
After saving values from arguments, the sample gets all available logical drives on the system. Each drive is checked for its type. If it matches the network drive value and the ‘-localonly’ argument is passed, this drive will be skipped.
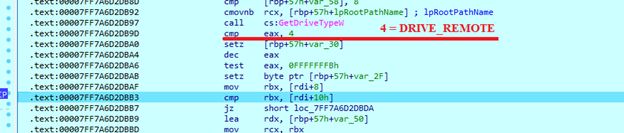
After saving values from arguments, the sample gets all available logical drives on the system. Each drive is checked for its type. If it matches the network drive value and the ‘-localonly’ argument is passed, this drive will be skipped.
The next step is to obtain a list of all running processes in the system. To do this the sample uses the ‘WTSEnumerateProcess’ function. This function is primarily used to enumerate processes on remote servers, but Akira uses ‘NULL’ value as a handle argument, meaning that this function will enumerate processes on the local system.
Next, it loads some symbols into one buffer, which then is decrypted in the loop. As a result, the PowerShell command is generated. This command will delete all shadow copies using the WMI object.
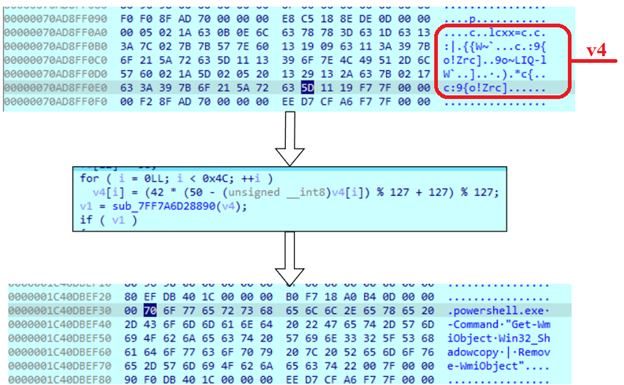
The sample then sets the authentication information that will be used to make calls on the local machine. Here it uses ‘CoSetProxyBlanket’ with the next arguments:
● dwCapabilities = 0 – no capabilities flag.
● pAuthInfo = NULL – DCOM uses the current proxy identity (which is either the process token or the impersonation token).
● dwImpLevel = 3 – The server process can impersonate the client's security context while acting on behalf of the client.
● dwAuthLevel = 3 – Authenticates only at the beginning of each remote procedure call when the server receives the request.
● pServerPrincName = NULL – no mutual authentication.
● dwAuthzSvc = NULL – no authorization.
● dwAuthSvc = NULL – no authentication.
Then, the sample loads strings that will be used in imports from the ‘fastprox.dll’ library, which is a WMI custom Marshaller. It also utilizes some imports from the COM library ‘wbemprox.dll’. Both COM and WMI are used here to control privileges and execute decoded Powershell commands.
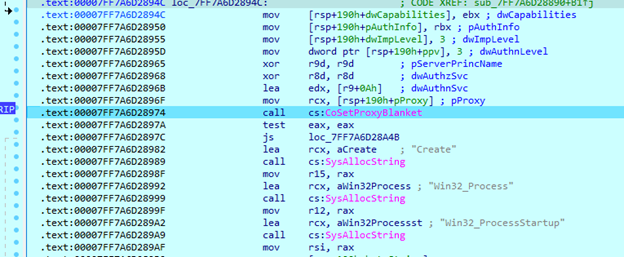
After command execution, the sample calls the ‘GetSystemInfo’ function and starts creating threads. It creates three different types of threads with different thread numbers:
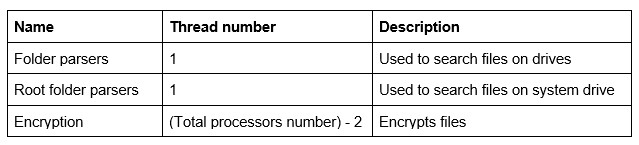
The number of encryption threads depends directly on computer CPU numbers that will be obtained using ‘GetSystemInfo’. For example, in a computer with six logical processors, it creates two threads for folders parsers — the other four will be used for encryption. Those numbers are written in the log file
File encryption
Akira uses both Windows API calls and functions from CRT (C runtime) in the file encryption routine. To iterate through folders in the system, it creates a directory iterator.
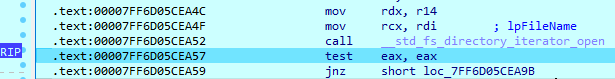
When any file is found, it searches for two symbols in its name – ‘\’ and ‘.’. This operation is used to determine whether a file is a folder. If the file is a folder, the sample will compare its name with the saved list. If the name matches, the folder will be skipped from encryption. If the file is not a folder, the sample will find its extension by searching for the last ‘.’ symbol in its name and also compare with saved extensions.
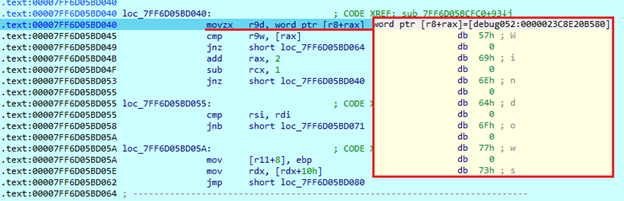
The following folders and file extensions are excluded from encryption, as it may disrupt system workability: $Recycle.Bin, System Volume Information, Boot, ProgramData, Windows, temp, .dll, .exe, .akira
Any other file will be opened with ‘GENERIC_ALL’ access rights. The sample gets the result of this operation using the ‘GetLastError’ function. The last error code is then compared with the value ‘20h’(32 in decimal), which is the ‘ERROR_SHARING_VIOLATION’ error. If it matches, the sample calls a function that will kill the process which blocks this file.
To kill processes, the sample uses Restart Manager API. After creating a session, it registers a resource, which is a blocked file name. Then, the sample finds a list of processes that handle this file. Before terminating processes from this list, the sample obtains its own PID to exclude itself from termination.
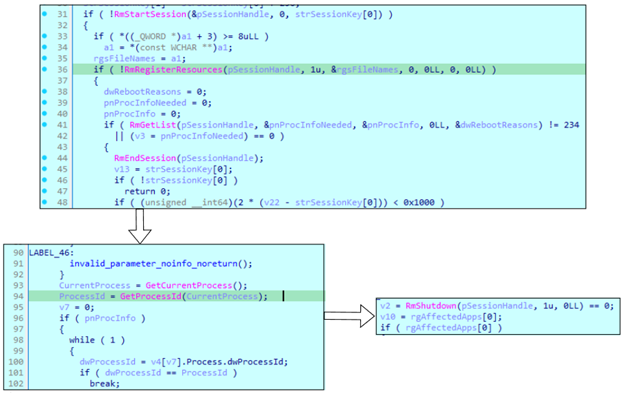
Akira uses ChaCha20 to encrypt files. If the file percentage was provided as an argument, Akira will calculate how much data it must read. It uses saved magic constants, which depend on the key size and which in this case is always 256.
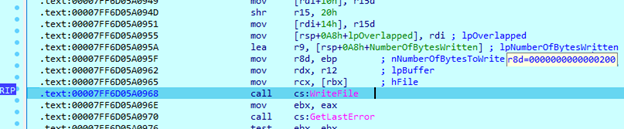
After encrypted data is written, it performs one more write operation using a 512 bytes (200 in hexadecimal) buffer. It contains a ChaCha20 key, encrypted with RSA.
Encryption evolution
Conclusion
Highly active in 2024, Akira continues to operate in 2025. While the sample analyzed shares some similarities with Conti's leaked source code, it is evolving and has become one of the most dangerous threats this year. Finally, how much time Akira gives their victims to pay their ransoms is unclear — ransom notes reveal only that the price is calculated for each victim, depending on the stolen data, which may include bank data. TRU observed one victim whose data was leaked no more than five days after it was breached by Akira.
Detected by Acronis
IoCs
Files
SHA256
88da2b1cee373d5f11949c1ade22af0badf16591a871978a9e02f70480e547b2
Network indicators
URL
https://akiral2iz6a7qgd3ayp3l6yub7xx2uep76idk3u2kollpj5z3z636bad.onion
https://akiralkzxzq2dsrzsrvbr2xgbbu2wgsmxryd4csgfameg52n7efvr2id.onion
Lynx ransomware focuses on private businesses
First observed in mid 2024, Lynx shares many similarities with INC ransomware, which was analyzed by TRU in 2023. Working as a ransomware-as-a-service group, Lynx threat actors constantly search for affiliates, posting on Russian underground forums and searching for new affiliates. The poster claimed that Lynx targets only the private business sector, has its own builder, supports Windows and Linux versions and provides a service to store stolen files. Also, affiliates will have access to the data leak site admin panel.
In April 2024, a user on an underground forum posted an offer to sell three copies of the INC ransomware builder for 300,000 — possibly rubles — each. The functionality described in the post is similar to analyzed samples of INC ransomware, but whether it was real INC source code is unknown.
Shortly after that, the Lynx ransomware appeared. Because the INC group is still active in 2025, it is unlikely that INC simply rebranded. Lynx most likely purchased the INC builder on the underground forums and adjusted the code.
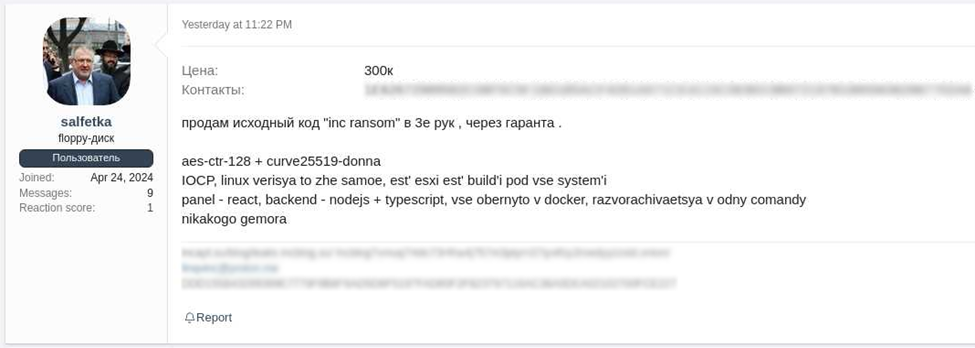
Translation from Russian:
“Selling INC ransomware source code for only 3 buyers.
aes-ctr-128 + curve25519-donna
IOCP, Linux version the same, have ESXI build compatible for all systems
Panel - react, backend -nodejs + typescript, all wrapped to Docker, all can be started up in one command, no complications”
Technical details
Delivery
Lynx typically uses phishing emails to deliver their malware to victims. When attackers gain access to the victims' computers, they first gather system and infrastructure information, attempt to obtain user credentials, and perform lateral movement to infect more computers in the network. Having access to the victims' computers also allows attackers to investigate installed software and search for vulnerabilities that can later be exploited for ransomware execution.
In 2025 attacks, we’ve seen that if security software is found, Lynx will try to uninstall it. When this step is performed, attackers first exfiltrate files to the servers and then detonate the encryptor.
Overview
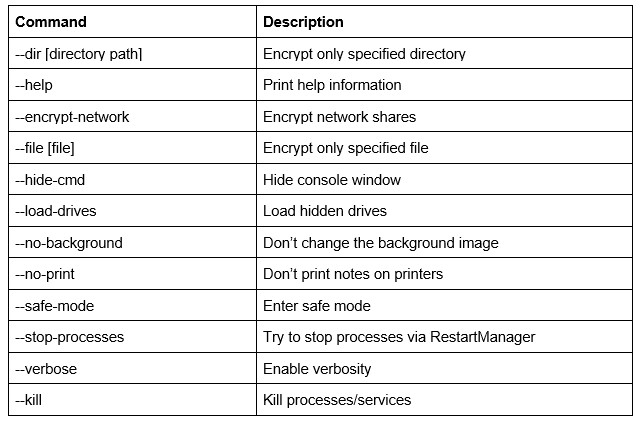
The analyzed sample is a PE32 file, written in C\C++. It is not packed or obfuscated. The sample supports multiple commands. Each command and its description is saved in the code:
After it gets arguments from the command line, the Lynx sample compares them with saved ones. If it matches, the sample sets the appropriate value to ‘1’. If it does not match, the sample sets the value ‘0’. The result will be saved to the global variable.
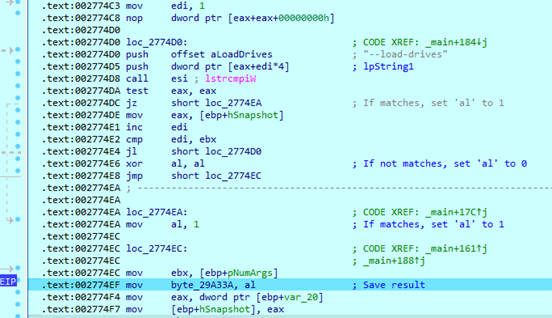
When an argument requires additional information, such as the directory path in ‘--dir’ argument, Lynx also saves this data using an additional offset from the command line string.
Console output
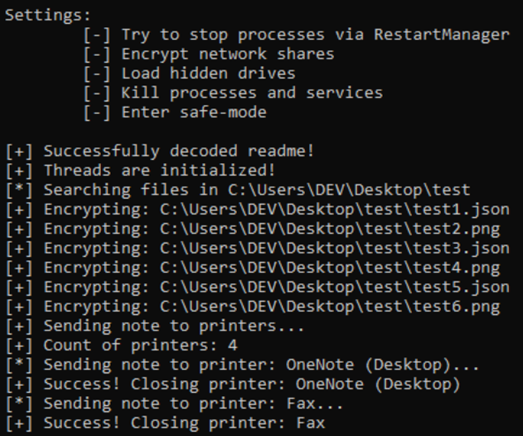
If ‘--verbose’ argument is passed, the Lynx sample will output different information such as settings, some operations status and encryption progress.
Hidden drives mount
This argument will force Lynx samples to search and mount any hidden drive in the system. Here it loads a saved list of drive letters and starts checking each one. When any drive is found, it checks if its type is DRIVE_NO_ROOT_DIR. If the type matches, it mounts it using the ‘SetVolumeMountPointW’ function.
Processes termination
There are two methods that Lynx uses for process termination; both of them are enabled using command-line arguments. When the ‘--kill’ argument is passed, it creates a snapshot of all running processes in the system and starts iterating them. Each process name is compared with the saved list, and if it matches, it will be terminated.
The ‘--kill’ argument is also responsible for service termination. Here it uses SC Manager and ‘EnumServicesStatusExW’ function to obtain a list of all running services on the system. The Lynx sample will then compare this list with saved names. When a match is found, the ‘ControlService’ function will be called with the ‘SERVICE_CONTROL_STOP’ flag.
The following processes will be terminated in order to avoid file-share violation errors during encryption:
sql, veeam, backup, exchange, java, notepad
Terminated services:
sql, veeam, backup, exchange
When the ‘--stop-process’ argument is provided, the sample uses Restart Manager API to terminate processes during the encryption process. This function will be called only if the file that Lynx tries to encrypt is busy by another process. The sample will register this file as a resource to determine the process. It will also get its own PID to exclude itself from termination.

Shadow copies
Before starting the encryption routine, the Lynx sample searches for all drives on the system. Each drive is checked for its type. For encryption, it accepts only drives with flags ‘DRIVE_REMOVABLE’, ‘DRIVE_FIXED’ and ‘DRIVE_REMOTE’. When appropriate drive is found, it opens handle to it and executes the ‘DeviceIoControl’ function with ‘53C028h’ parameter as control code, which is a ‘IOCTL_VOLSNAP_SET_MAX_DIFF_AREA_SIZE’.
This is an undocumented control code that will change the maximum size for a shadow copy. As the ‘lpInBuffer’ contains value ‘1’, setting such a low size will force shadow copies to be deleted. After those operations are completed, all found drives will be passed to the encryption routine.
File search process
The Lynx sample creates threads with ‘sub_275600’ function as the start address. The number of threads is the number of processors — obtained with the ‘GetSystemInfo’ call — multiplied by four.
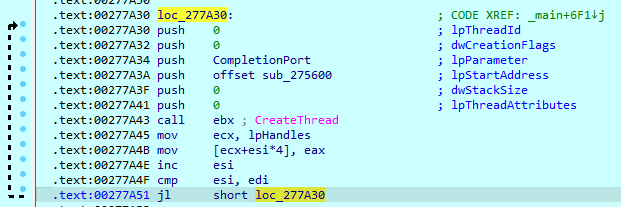
Threads with this start address are used to search files. When the Lynx sample enters a folder, it creates a ransom note in that folder and starts searching for files using ‘FindFirstFile’ and ‘FindNextFile’ functions. If the found file is a folder, the sample will compare its name with the saved list. If the folder name matches, it will be skipped.
When a found file is not a folder, the sample also can exclude it from encryption. It compares extensions and file names. If file size is 0, it also will be skipped.
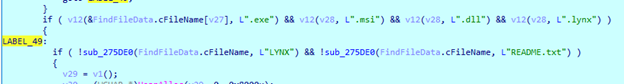
When an appropriate file is found, the sample first checks whether it is busy with another process. If the ‘--stop-process’ argument is passed, the sample will kill the process that holds the file, if not, the file will be skipped. Then, the sample determines whether the sample has write access to this file. This is done by writing a chunk of data to the end of the file. Before the writing process, the sample sets 36 bytes of ‘2’ to the buffer. The number of characters that must be set to the buffer, as well as the buffer size that must be written to the file, is calculated using the sum of ‘LYNX’ string length and 32.
If Lynx fails to write that file, it will try to get its ownership. Here it tries to obtain ‘SeTakeOwnership’ privilege and change file ownership by creating and setting a new ACL structure, which will grant write privileges.
File encryption
At the start of the thread routine, Lynx decodes the string, saved in Base64 format:
8SPEMzUSI5vf/cJjobbBepBaX7XT6QT1J8MnZ+IEG3g=
This value is an ECC public key, which will be used to generate the AES key. Each thread initializes crypto providers with ‘CRYPT_VERIFYCONTEXT’ and ‘PROV_RSA_AES’ flags. Then the sample generates 32 random bytes using the ‘CryptGenRandom’ function.
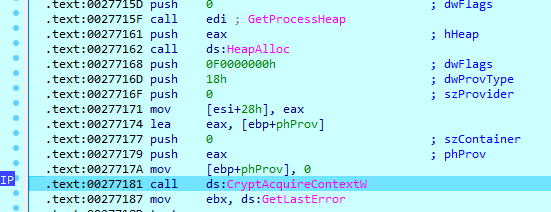
Then sample calculates the hash of the generated key. SHA512 constants are saved in the binary.
After the thread reads the found file, the sample creates an encryption thread, passes a completion signal to it and exits. The encryption thread obtains data from the previous one, which includes read file data and encryption keys. Depending on the ‘GetQuedCompletionStatus’ result, the sample will jump to one of five cases.
During the debugging process, the first case that was triggered was two. Here the sample first checks some values and then performs a write operation on the current file. It will write ‘116’ bytes of data, which includes the encrypted key.
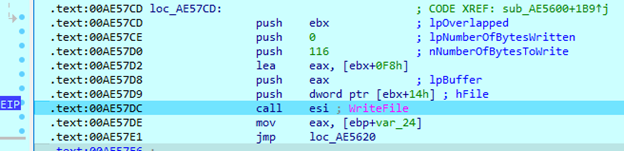
The sample then enters ‘Case 0’, where it checks if the current encryption block offset is not bigger than a file size. When it enters this case for the first time, the block offset will always be ‘0’ and will cause the thread to read file data. But when the condition is met, the sample indicates that the file has no more data to encrypt and will force the thread to write an encrypted block to the file. Also, it will set the case statement to value ‘3’.
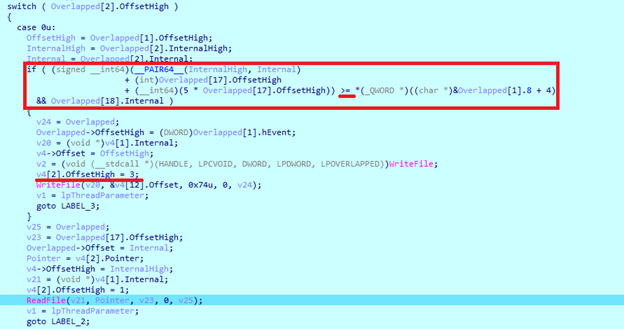
Next the sample enters ‘Case 1’. Here it takes file size and removes ‘116’ from it. This is done to remove an already written chunk of data from encryption.
After all preparations are done, the sample enters a loop where it encrypts file data. Here it calls the ‘sub_AE1110’ function, which uses AES to encrypt the key. As a result, value v32 is used as a keystream(v16), which will be XORed with file data. For each 16 encryption loop iterations the keystream will be generated again.
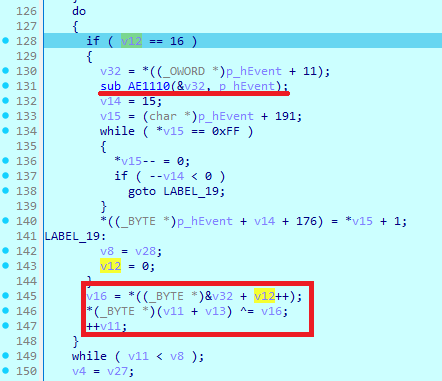
Finally, the sample writes encrypted data to the file and enters ‘Case 3’, where it appends ‘.LYNX’ extension to the file. After that, the thread clears its memory and starts waiting for the next file.
Ransom note
Lynx stores a ransom note message in Base64 format. Lynx loads it and passes it to the ‘CryptStringToBinaryA’ function, which is called with the ‘CRYPT_STRING_BASE64’ flag.
While the decoded message doesn’t contain a victim ID, it is appended after the decoding process. This ID is hardcoded and different for each sample.
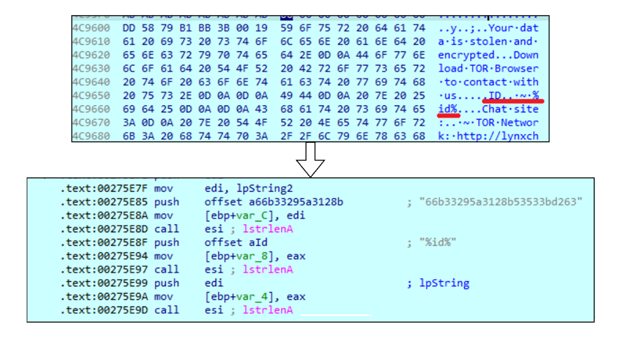
After the encryption process is done, the sample uses imports from the ‘Winspool’ header to find all connected printers. It will check printer names, compare them with saved names to avoid them and send ransom notes to all found printers.
Besides text files, the ransom note is also written as a desktop wallpaper at the end of the encryption process.
Conclusion
While it is unknown if Lynx is simply INC ransomware rebranded, we do know that it shares code similarities. The analyzed samples can terminate processes, mount hidden drives, delete shadow copies and encrypt files on network shares. While the file's encryption is strong, attackers also upload files to their servers as a part of a double extortion scheme, forces victims to pay a ransom not only for decryption but also for nondisclosure of their private data.
IoCs
Files
SHA256
571f5de9dd0d509ed7e5242b9b7473c2b2cbb36ba64d38b32122a0a337d6cf8b