Ransomware continues to be a very active, always evolving threat. One of the newest strains to emerge is Snake (also known as EKANS, which is simply “Snake” spelled backward).
First appearing at the end of December last year, the most interesting feature of Snake is that it targets industrial control systems (ICS) environments – not the individual machines, but the entire network.
The obfuscated ransomware sample, which was written in the Go programming language, was first observed in commercial malware repositories. It is designed to terminate specific processes on victim machines, including multiple items related to ICS operations, as well as delete Volume Shadow Copies to eliminate Window backups.
While there is currently no decryption available, systems that are running Acronis Active Protection – the AI-based anti-malware defense that is integrated into our cyber protection solutions – successfully detects Snake ransomware as a zero-day attack and stops it in its tracks.
Infection process and some technical details
The point of entry for Snake is an insecure RDP configuration. It is distributed via spam and malicious attachments, but also can be delivered via botnets, exploit packs, malicious ads, web injections, fake updates, and repackaged and infected installers.
According to our analysis, when executed, Snake will remove the computer's Shadow Volume Copies and then kill numerous processes related to SCADA systems, virtual machines, industrial control systems, remote management tools, network management software, and so on. Deleting Windows backup copies is a set-up trend and expected functionality in any new ransomware.
The ransomware checks for the existence of a Mutex value “EKANS” on the victim. If present, the ransomware will stop with a message “Already encrypted!”. Otherwise, the Mutex value is set and the encryption moves forward using standard encryption library functions. Primary functionality on victim systems is achieved via Windows Management Interface (WMI) calls, which begins executing encryption operations.
Before proceeding to file encryption operations, the ransomware force stops (kills) any processes listed in a hard-coded list within the malware’s encoded strings. A full list with assessed process function or relationship is provided as follows:
While encrypting files on infected machine, it will skip the ones located in Windows system folders:
SystemDrive :\$Recycle.Bin :\ProgramData :\Users\All Users :\Program Files :\Local Settings :\Boot :\System Volume Information :\Recovery \AppData\
- windir
It will append a random five-character string to an encrypted file extension, as well as 'EKANS' file marker. The encryption process is typically slow and, in cases of actual infection, done in non-working hours.
After finishing the encryption process, it will drop a ransom note named “Fix-Your-Files.txt”
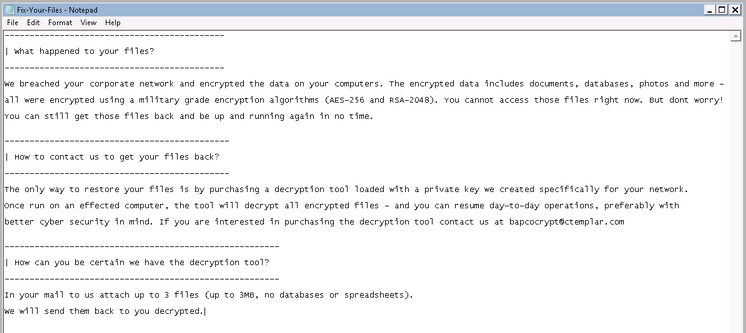
User access to the encrypted system is maintained throughout the process, and the system does not reboot, shutdown, or close remote access channels. This differentiates Snake/ EKANS from more disruptive ransomware such as the LockerGoga. The email address in the ransomware uses a privacy-focused email service similar to Protonmail, called CTemplar.
Acronis Active Protection detects from day zero
Whereas previously ICS-specific or ICS-related malware was solely the playground of state-sponsored entities, Snake / EKANS appears to indicate that cybercriminals pursuing financial gain are now involved in this space as well. While this ransomware is still being analyzed for weaknesses, at this moment any data affected by it cannot be decrypted.
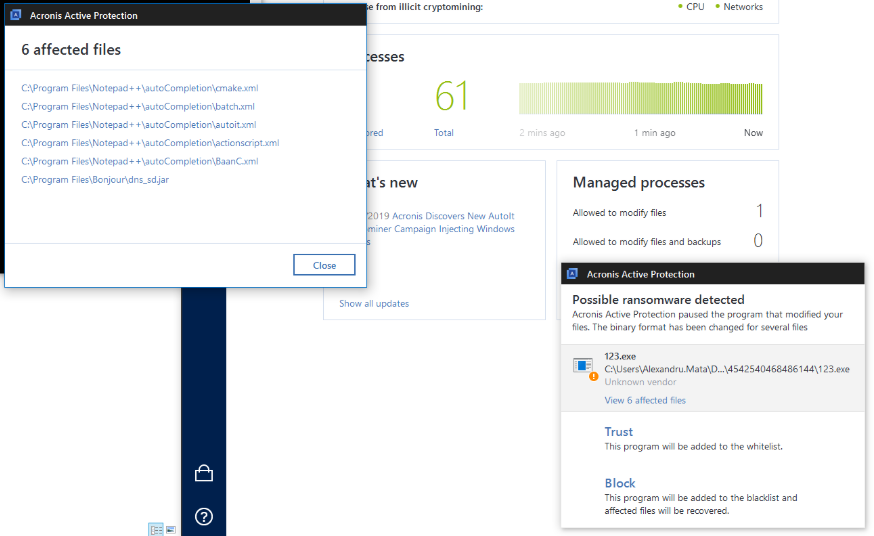
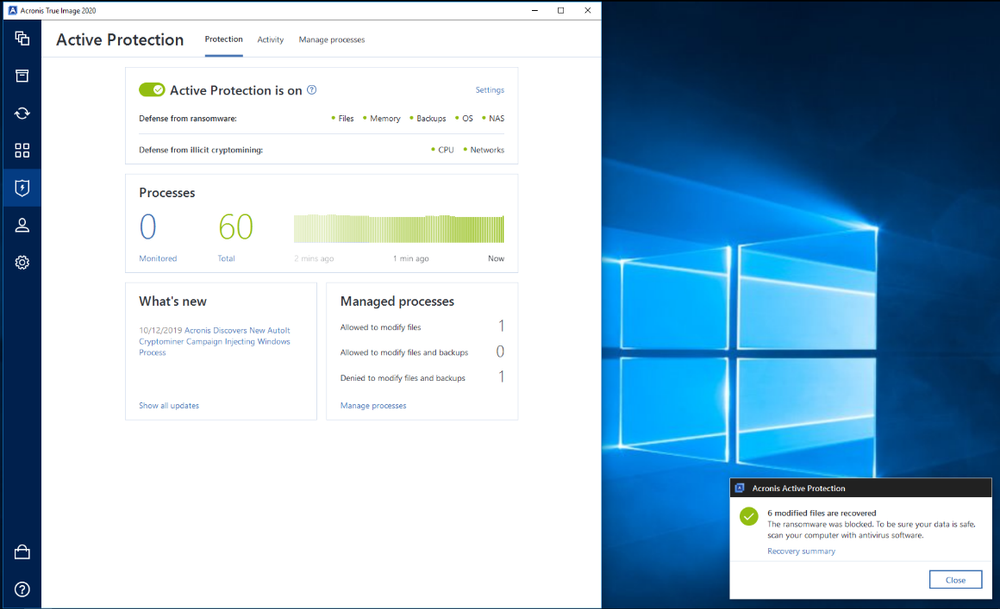
The good news is that Acronis Active Protection is able to detect Snake and stop the malicious process in real-time, while also reverting any affected files. We only can imagine how much damage can be done if this strain makes its way into industrial environments, paralyzing traffic control systems or energy plants.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



