Network connection diagram for Acronis Cyber Protect
This topic contains the connection diagrams for Acronis Cyber Protect.
Visit our Knowledge Base for a list of ports, services, and processes that Acronis Cyber Protect uses:
- For Windows, see Windows services and processes (65663).
- For Linux, see Linux components, services, and processes (67276).
Network connection diagram - Cyber Protect processes
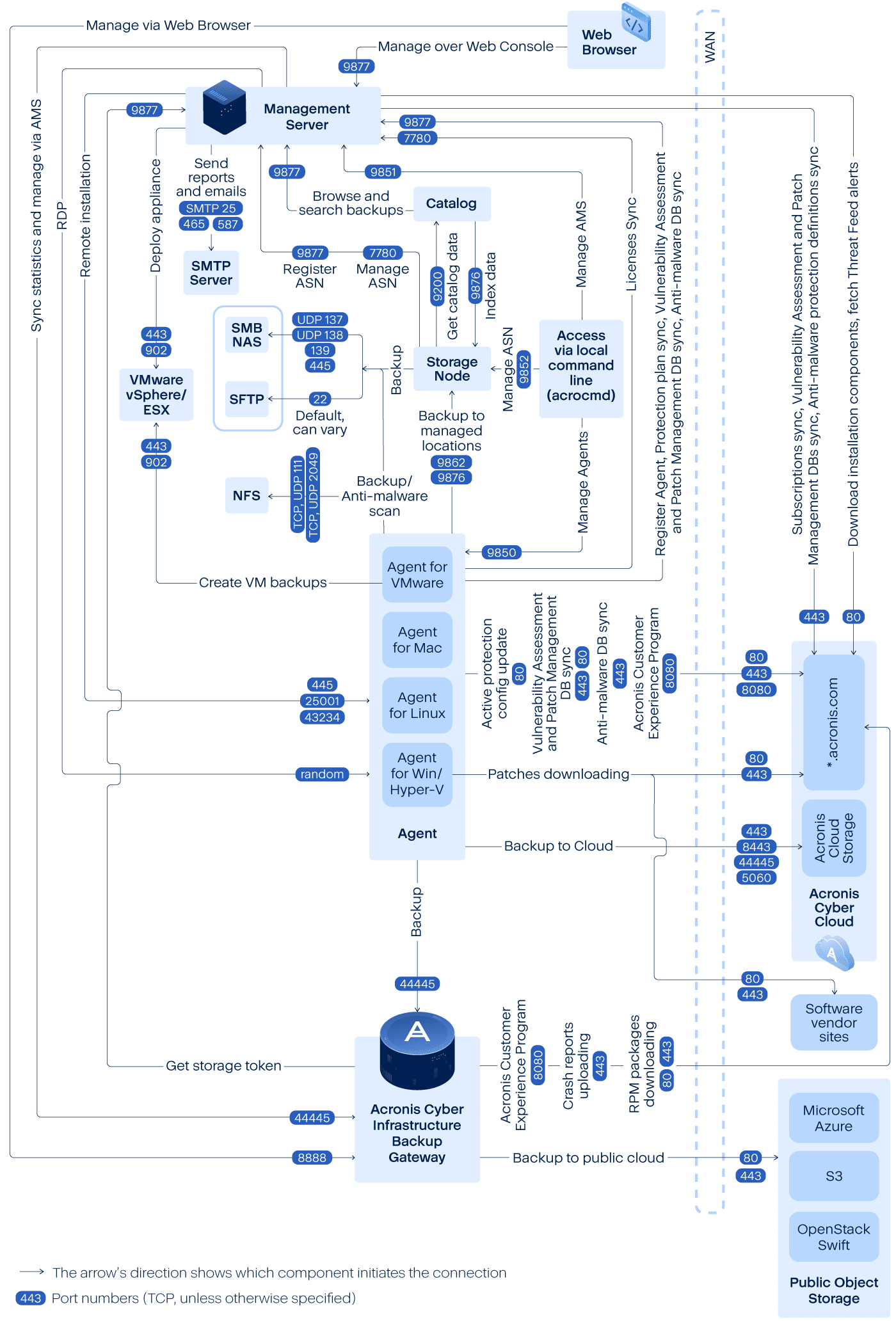
The outgoing ports in the network diagram are dynamic. Some services can also use dynamic ports for inbound connections. When you troubleshoot network issues, ensure that the traffic through dynamic ports is allowed.
The dynamic ports are managed by the operating system and are assigned randomly. The default dynamic port range in Windows is 49152 – 65535. This range may vary according to the operating system and can be changed manually.
Management server is the central component of Acronis Cyber Protect. It exposes two TCP ports: 7780 and 9877. Port 9877, protected with TLS, is used to provide both the REST API and a web-based user interface. The REST API endpoints authenticate requests by using JWT tokens represented either as a separate HTTP header or encoded as an HTTP cookie. Port 7780 implements the ZeroMQ protocol with ZMTP CURVE authentication and encryption. Port 7780 is used by the agents and storage node to exchange management messages with the management server asynchronously. The management server also communicates with the cloud services to download updates over standard HTTP and HTTPS ports.
Storage node is the storage component of Acronis Cyber Protect. It exposes TCP port 9876. This port is used for sending and receiving backup data. Transport is protected with TLS and authentication is done using mutual TLS. The application-level protocol is Acronis proprietary. The storage node communicates to backend storage systems by using the appropriate protocols and authentication mechanisms.
Catalog is a supporting component of Acronis Cyber Protect. It indexes data on the storage node, accessing it on port 9876 and exposes the index on port 9200.
Backup gateway implements the next generation of Acronis proprietary data access protocol. The same component is used in Acronis Cyber Cloud, if the customer opts-in for cloud backup. TCP port 44445, registered at IANA, is used by the gateway. Data protection is done via TLS and the authentication is done using mutual TLS. The backup gateway also may use port 8888 for the HTTPS-based management service.
Agent communicates with the management server, storage node, and backup gateway over the ports, as described above. The agent may also communicate with standards-based file services (SMB, NFS) when they are used as a backup destination. Standard ports and appropriate authentication protocols are used in this case. Agent for VMware uses the VMware vSphere API over the ports defined by VMware vSphere when such functionality is configured.
The vulnerability assessment for Linux is implemented via a CVSS service deployed in Acronis Cyber Cloud. Protection agents choose dynamically the closest data center via ping from the list https://cloud.acronis.com/services.json.