Interactive Installation
Run Setup (setup.exe) and follow the instructions on the wizard pages that appear on the screen.
Note: •You should run setup.exe on each computer that is to be controlled with DeviceLock Service. •If you are upgrading a previous version, make sure that you have administrative access to DeviceLock Service, otherwise you will not be able to continue installation. |
On the License Agreement page, read the License Agreement and then click I accept the terms in the license agreement to accept the licensing terms and conditions and proceed with the installation.
On the Customer Information page, type your user name and organization.
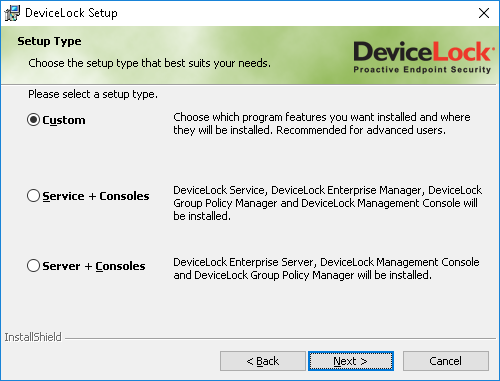
On the Setup Type page, select the required setup type.
You have the following two choices: either install both DeviceLock Service and DeviceLock management consoles using the Service + Consoles option or install only DeviceLock Service using the Custom option and selecting the DeviceLock Service component.
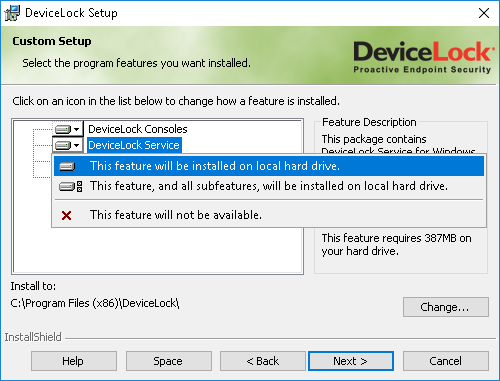
Note: On the Custom Setup page, you can select the RSoP component to install. This component enables support for DeviceLoc’s Resultant Set of Policy planning mode on domain controllers. The RSoP component is required only when DeviceLock management consoles are installed, but DeviceLock Service is not installed on the computer. For more information on RSoP planning mode, refer to Microsoft’s documentation at
technet.microsoft.com/library/cc758010.aspx. |
On the Custom Setup page, you can change the default installation folder. Click Change and then choose a folder in the dialog box that appears. The default folder is %ProgramFiles%\DeviceLock.
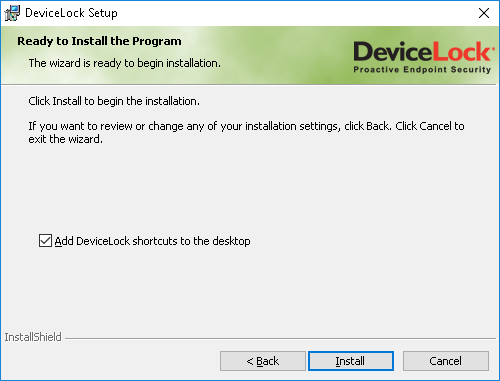
On the Ready to Install the Program page, click Install to begin the installation. Select the Add DeviceLock shortcuts to the desktop check box to add DeviceLock Management Console (the MMC snap-in), DeviceLock Enterprise Manager and DeviceLock Service Settings Editor shortcuts to the desktop.
If you choose to install DeviceLock management consoles as well, Setup may suggest that you generate a new DeviceLock Certificate. The following message will appear: “Do you want to create the new DeviceLock Certificate (the private and public key pair)? Click “No” if you already have DeviceLock Certificate and you don’t need to create the new key pair.”
You can always generate a new DeviceLock Certificate later, using the Certificate Generation Tool installed with DeviceLock management consoles. Hence, if at this step you are not sure whether you need the new certificate or not, just click the
No button and continue the installation. For more information on DeviceLock Certificates, see the
DeviceLock Certificates section later in this document.
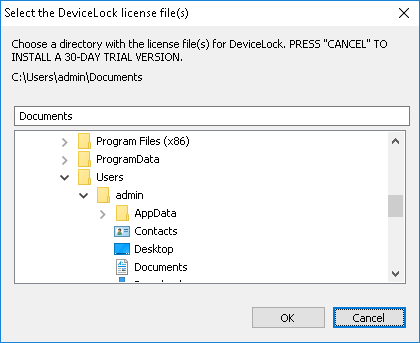
Also, if you select Service + Consoles, Setup may suggest that you load the DeviceLock license files. If you don’t have the license files, click Cancel to install DeviceLock in a 30-day trial mode.
For further information about DeviceLock licenses, see
Activating Client Licenses.
During the installation process, you can set special permissions for local devices and protocols.
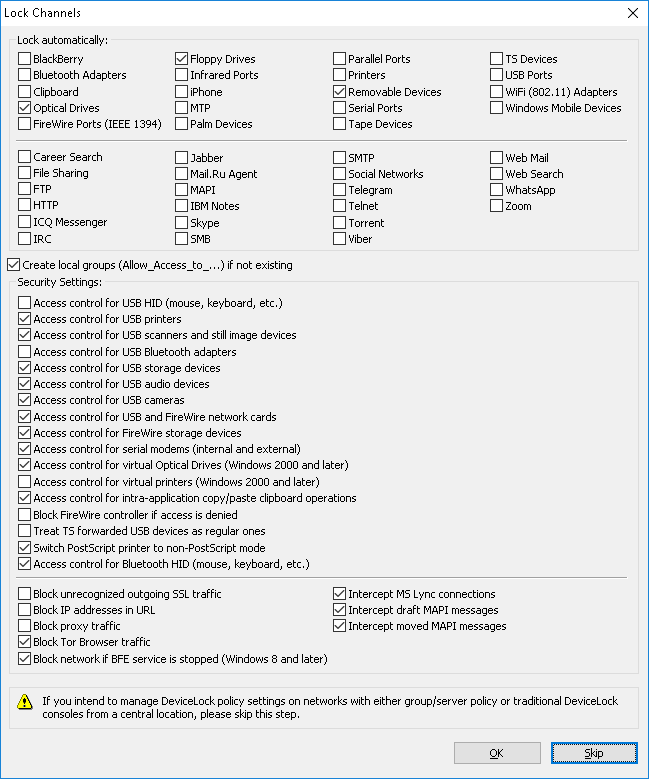
Select devices and/or protocols you would like to set permissions to. Select the Create local groups (Allow_Access_to_...) if not existing check box for Setup to create the special local user group Allow_Access_To_ for each channel type (e.g. Allow_Access_To_Floppy for floppy drives), if these do not exist on the local computer.
Setup assigns Read, Write, Format and Eject generic rights to members of the Administrators group and the SYSTEM account. Members of the Allow_Access_To_ group will have Read, Write and Eject generic rights.
Also, you can define security settings to exclude certain types of devices from the access check (see
Security Settings (Regular Profile)).
Select Access control for USB HID, Access control for USB printers, Access control for USB scanners and still image devices, Access control for USB Bluetooth adapters, Access control for USB storage devices or Access control for FireWire storage devices to allow DeviceLock Service to control security for Human Interface Devices (mouse, keyboard, etc.), printers, scanners and still image devices, Bluetooth adapters or storage devices (such as flash drives) plugged into the USB and FireWire port. To allow access control for Web cameras and/or audio devices plugged into the USB port, check Access control for USB cameras and/or Access control for USB audio devices. To allow access control for USB and FireWire network cards, check Access control for USB and FireWire network cards. Otherwise, even if the USB and/or FireWire ports are locked, the devices listed above will continue to function as usual when connected to those ports. To allow access control for serial modems (internal and/or external), select Access control for serial modems. To disable locking of virtual (software emulated) CD/DVD/BD, uncheck Access control for virtual Optical Drives. To disable control of virtual printers (those which print to files), uncheck Access control for virtual printers. To allow access control for copy/paste clipboard operations within an application, select the Access control for intra-application copy/paste clipboard operations check box. Otherwise, even if the clipboard is locked, access control for copy/paste operations within one application is disabled. To disable FireWire controllers when the Everyone account has No Access permissions for the FireWire port device type, select the Block FireWire controller if access is denied check box. To allow access control for Bluetooth Human Interface Devices (mouse, keyboard, etc.), select Access control for Bluetooth HID (mouse, keyboard, etc.).
Select the Switch PostScript printer to non-PostScript mode check box to make PostScript printers act like non-PostScript printers. This resolves an issue in which DeviceLock Service is unable to create a correct shadow copy of printed data and perform content analysis of data sent to printers that use a PostScript driver.
Select the Treat TS forwarded USB devices as regular ones check box to allow DeviceLock Service to control access to all USB devices redirected during a Citrix XenDesktop/MS RemoteFX session according to the rights set for the USB port device type. Otherwise, DeviceLock Service controls access to all USB devices redirected during a Citrix XenDesktop/MS RemoteFX session according to the USB Devices Access right set for TS Devices.
Also, you can define security settings for protocols (see
Managing Security Settings for Protocols).
To allow DeviceLock Service to audit and block all unrecognized outgoing SSL traffic, select the Block unrecognized outgoing SSL traffic check box. Otherwise, even if the protocols are locked, all unrecognized outgoing SSL traffic is not blocked and audit is not performed for it.
To allow DeviceLock Service to block all URLs containing the host IP address when users have “allow access” permissions for the HTTP protocol, select the Block IP addresses in URL check box. This setting blocks, for instance, access to Web-sites by IP address.
To allow DeviceLock Service to audit and block all traffic that flows through a proxy server, select the Block proxy traffic check box. The following proxy servers are supported: HTTP, SOCKS4, and SOCKS5.
To allow DeviceLock Service to block connection to the Tor network, preventing the use of the Tor Browser, select the Block Tor Browser traffic check box.
To force DeviceLock Service to block all network traffic when the Base Filtering Engine system service is stopped, select the Block network if BFE service is stopped (Windows 8 and later) check box.
To allow DeviceLock Service to intercept network traffic from Microsoft Lync 2010 or Microsoft Office Communicator, select the Intercept MS Lync connections check box.
To allow DeviceLock Service to control draft folder messages that Outlook saves to the Exchange Server, select the Intercept draft MAPI messages check box.
To allow DeviceLock Service to control messages that Outlook imports to the Exchange Server from e-mail message export files (.msg files) or other (external) mailboxes, select the Intercept moved MAPI messages check box.
Click OK to apply changes. Click Skip if you prefer to wait until after installation to set permissions to these devices using DeviceLock management consoles.
Then, on the Installation Wizard Completed page, click Finish to complete the installation. On this page, there is the option to go to the DeviceLock home page. This option is selected by default.
Note: You can uninstall DeviceLock as follows: •Use Programs and Features in Control Panel (Add or Remove Programs on earlier versions of Windows) to remove DeviceLock. - OR - •Select Remove DeviceLock on the Windows Start menu. |