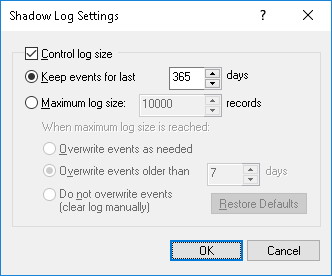
Shadow Log Settings (Server)
To control the log size and server actions when the log is overflowing, select the Settings command from the shortcut menu of this log viewer in the console tree. Then, view or change the settings in the dialog box that appears.
The log settings are similar to those of the Audit log, see
Audit Log Settings (Server).
When DeviceLock Enterprise Server needs to remove old records from the Shadow log because of the log settings specified, those records are moved to the
Deleted Shadow Data Log.
Note: The server removes old records either by the date indicated in the Received Date/Time column (for records received directly from the DeviceLock Service) or by the date indicated in the Consolidated Date/Time column (for records received from other servers using
consolidation). |
If the Shadow log has no space for new records and log settings do not allow the deletion of old records, the server does not remove shadow data from users’ computers. This prevents the loss of shadow data due to lack of space in the log. When some space becomes available in the log, the server moves the remaining shadow data from the users’ computers to this log.
It is a best practice to avoid the accumulating of shadow data on users’ computers. We recommend that you monitor the server log of DeviceLock Enterprise Server by using the
Server Log Viewer on a regular basis, watch for warning messages, and appropriately adjust the shadow log settings on the server.