Defining and editing offline audit and shadowing rules
To define and edit offline audit and shadowing rules
1. If using DeviceLock Management Console, do the following:
a) Open DeviceLock Management Console and connect it to the computer running DeviceLock Service.
b) In the console tree, expand DeviceLock Service.
If using DeviceLock Service Settings Editor, do the following:
a) Open DeviceLock Service Settings Editor.
b) In the console tree, expand DeviceLock Service.
If using DeviceLock Group Policy Manager, do the following:
a) Open Group Policy Object Editor.
b) In the console tree, expand Computer Configuration, and then expand DeviceLock.
2. Expand Protocols.
3. Under Protocols, select Auditing, Shadowing & Alerts.
When you select Auditing, Shadowing & Alerts in the console tree, in the details pane you can view protocols for which you can define audit, shadowing rules and alerts. In the details pane you can also view the current state of offline rules for each protocol in the Offline column.
4. In the details pane, do one of the following:
•Right-click the protocol for which you want to define or edit rules, and then click Set Offline Auditing, Shadowing & Alerts.
- OR -
•Select the protocol for which you want to define or edit rules, and then click
Set Offline Auditing, Shadowing & Alerts 
on the toolbar.
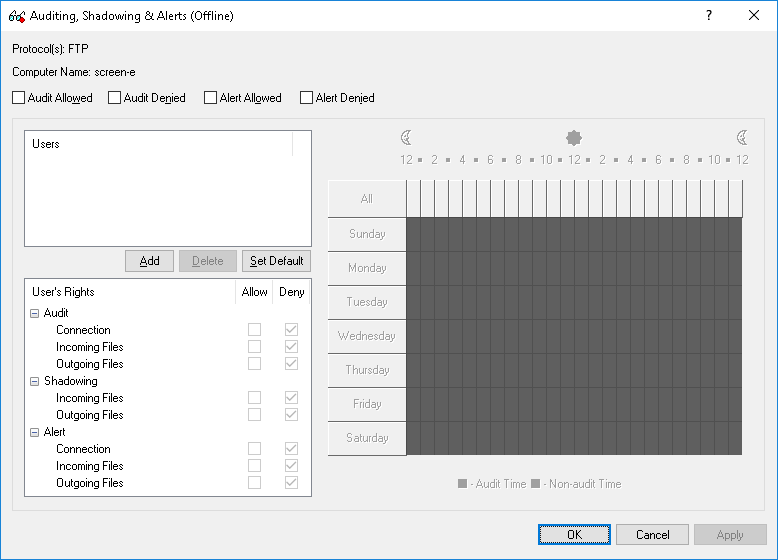
The Auditing, Shadowing & Alerts (Offline) dialog box appears.
5. In the Auditing, Shadowing & Alerts (Offline) dialog box, do the following:
To define the default audit and shadowing rules
a) In the upper-left area of the dialog box, specify which events are written to the Audit Log. Select the Audit Allowed check box to audit successful attempts to gain access to a protocol. Select the Audit Denied check box to audit unsuccessful attempts to gain access to a protocol.
b) In the upper-left pane of the dialog box, under Users, click Set Default.
To define audit and shadowing rules for an additional user or group
a) In the upper-left area of the dialog box, specify which events are written to the Audit Log. Select the Audit Allowed check box to audit successful attempts to gain access to a protocol. Select the Audit Denied check box to audit unsuccessful attempts to gain access to a protocol.
b) In the upper-left pane of the dialog box, under Users, click Add.
c) In the Select Users or Groups dialog box that appears, in the Enter the object names to select box, type the name of the user or group, and then click OK.
The users and groups that you added are displayed under Users in the upper-left pane of the Auditing, Shadowing & Alerts (Offline) dialog box.
d) In the upper-left pane of the Auditing, Shadowing & Alerts (Offline) dialog box, under Users, select the user or group.
You can select multiple users and/ or groups by holding down the SHIFT key or the CTRL key while clicking them.
e) In the lower-left pane of the Auditing, Shadowing & Alerts (Offline) dialog box, under User’s Rights, select either Allow or Deny to directly allow or deny the appropriate audit and shadowing rights.
Audit and Shadowing rights determine which user actions on protocols are logged to the Audit and/or Shadow Log.
In the right pane of the Auditing, Shadowing & Alerts (Offline) dialog box, you can specify days and hours (for example, from 7 AM to 5 PM Monday through Friday) when the selected user’s actions on protocols will be logged to either the Audit or Shadow Log. Use the left mouse button to select days and hours when the selected user’s actions on protocols will be logged. Use the right mouse button to mark days and hours when the selected user’s actions on protocols will not be logged.
To change audit and shadowing rules for an existing user or group
a) In the upper-left pane of the dialog box, under Users, select the user or group.
b) In the lower-left pane of the dialog box, under User’s Rights, select either Allow or Deny to directly allow or deny the appropriate audit and shadowing rights.
To remove an existing user or group and rules
•In the upper-left pane of the dialog box, under Users, select the user or group, and then click Delete or press the DELETE key.
When you remove a user or group, any rules for that user or group will also be removed.
6. Click OK or Apply.
 on the toolbar.
on the toolbar. on the toolbar.
on the toolbar. on the toolbar.
on the toolbar.