How DeviceLock Discovery Works
DeviceLock Discovery can scan remote computers by using one of the three methods.
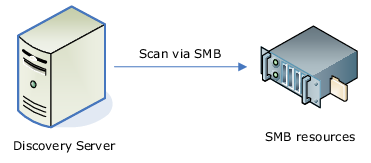
1. DeviceLock Discovery can scan remote computers via the SMB protocol (network shares).
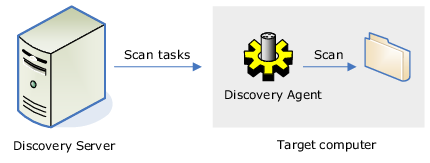
2. Alternatively, DeviceLock Discovery can perform the scanning via its own lightweight agent (DeviceLock Discovery Agent).
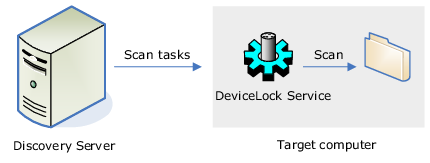
3. Finally, DeviceLock Discovery can scan remote computers by using a lightweight agent built into DeviceLock Service.
Depending upon a particular network configuration and system requirements, administrators may choose one or the other method.
SMB access is the easiest to deploy. Requiring neither DeviceLock software installation nor configuration for each local target endpoint, SMB access is a perfect method for remote background scanning of network shares on NAS devices, as well as files servers and other computers running any operating systems including those not directly supported by DeviceLock.
Using the DeviceLock Discovery Agent is ideal for scanning computers that have no DeviceLock Service installed. This method will require the deployment of the DeviceLock Discovery Agent throughout all computers to be scanned.
Leveraging the DeviceLock Service is a perfect solution for customers already using DeviceLock. As this method uses the existing installations of the DeviceLock Service, no additional deployment is required. However, this method will only scan Windows-based computers with DeviceLock Service already installed, and will neither be able to scan Mac computers nor computers and networks devices with unsupported operating systems such as NAS devices.
DeviceLock Discovery can be configured to perform certain actions on files being discovered. For example, it can be configured to delete or encrypt a certain file, modify its access rights, send an alert to an administrator, log the event or notify the user of the computer being scanned.
The results and logs are kept in a centralized SQL Server database. An HTML report is generated and kept in the same database. By analyzing the report, administrators can get a clear understanding on search results and review the findings of any content discovered by DeviceLock Discovery. The report is created every time a scanning task finishes.
Discovering documents in Elasticsearch
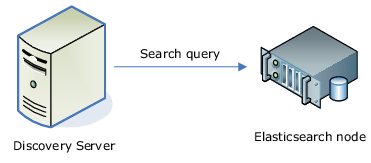
DeviceLock Discovery effectively discovers documents of interest in Elasticsearch - a distributed system that provides real-time indexing and search for a wide variety of data types. The Discovery Server requests a document search by the specified configurable parameters, and then applies the discovery rules and actions to documents received from Elasticsearch.
The DeviceLock Discovery agent is not installed on the Elasticsearch node. Discovery is done by direct HTTP access to Elasticsearch nodes. Discovery actions are limited to logging events and sending alerts. The Discovery Server cannot change or delete documents in Elasticsearch.
For further details, see
Elasticsearch Units.