
Growing security capabilities: MDR → XDR → SIEM
MSPs often rely on managed detection and response (MDR) integrations, which provides enterprise-grade security capabilities without the need for in-house analysts or complex infrastructure. As MSPs grow into medium-sized businesses, they typically expand into extended detection and response (XDR) integrations, giving greater visibility across multiple security layers (endpoints, networks and cloud) and more control over how they manage and respond to threats.
Once an MSP reaches a large-scale operation, it often adopts Security Information and Event Management (SIEM) platforms to aggregate and analyze data from multiple sources, including Acronis, and may even build its own Security Operations Center (SOC) to handle real-time threat monitoring, incident response and compliance at scale.
This blog focuses on Acronis SIEM Connector and a four-step activation for streamlined deployment.
MSPs turning into MSSPs: Why SIEM integrations matter
As MSPs evolve their security service offerings, the ability to consolidate threat intelligence and security events across multiple ecosystem vendors has become essential to competitive differentiation. Your customers expect unified threat visibility across all their security tools — consolidated into a single operational dashboard. This is no longer a nice-to-have; it's a must for MSPs competing in the managed security market.
The old way: A barrier for MSPs
Acronis introduced a SIEM Connector integration over two years ago to address market demand for security data collection. However, the initial implementation had limitations that created barriers to meeting this growing demand. Having a syslog server was a must to activate the integration, but not only that: the syslog server had to meet a long list of very specific prerequisites coupled with mandatory certificates generation. The result was that partners needed additional help and guidance to enable the SIEM Connector.
So just like in an old TV infomercial, we exclaimed: “There’s gotta be a better way!” And we found it…
Meet Acronis SIEM Connector 2.0: An easier way for MSPs
Acronis SIEM Connector 2.0 is built on the principle that enterprise-grade security integrations shouldn't require development-level configuration — they should be easy to use.
Compliance-first architecture
Acronis SIEM Connector implements tenant data isolation by design. Each customer tenant maintains an independent connection to their designated logs’ location. Disabled tenants are automatically filtered from the integration, ensuring compliance with data governance and isolation requirements.
Simplified deployment model
The Acronis SIEM Connector makes integration seamless! Integrated directly into Acronis protection plans, it uses the Acronis agent as the data writer, eliminating the complexities around generating certificates and applying custom settings to a syslog server. MSPs can store Acronis logs on any endpoint or a syslog server in the customer network with an Acronis agent installed. This agent-native approach significantly reduces deployment complexity and enables self-service activation for all organizations.
Extended data visibility
Version 2.0 expands the data scope beyond Alerts and Audit logs to include Event and Activity logs. This comprehensive data collection provides security teams with the extensive visibility required for effective threat detection and incident response.
Format Flexibility
Acronis SIEM Connector supports CEF and JSON formats, enabling seamless integration with diverse SIEM platforms and accommodating organizational preferences for log processing. Sometimes a SIEM wants JSON, and we think you should have the choice.
Check out the list of integrations which can be enabled through the Acronis SIEM Connector.
HIPAA Compliant Log Storage and Retention
Acronis SIEM Connector enables MSPs to maintain HIPAA compliance by allowing logs to be stored directly on any device on the customer network with an Acronis agent. The MSP can use this device as a server and store logs for the required minimum of six years. This capability eliminates the need for separate archival solutions and simplifies compliance audits, as all historical security events and logs remain readily accessible in a single location.
Streamlined deployment: Four-step activation
Acronis SIEM Connector introduces a significantly simplified activation workflow. Enabled through the SIEM LogForwarding plan, it eliminates manual syslog configuration and certificate generation by leveraging native agent capabilities. Organizations can begin collecting and forwarding Acronis security data to their SIEM platform in four straightforward steps:
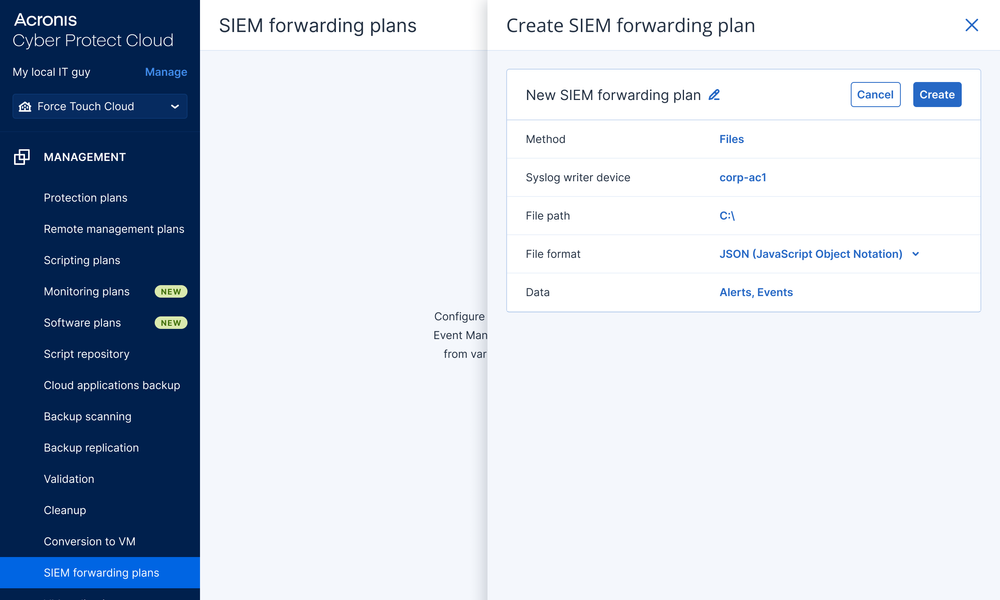
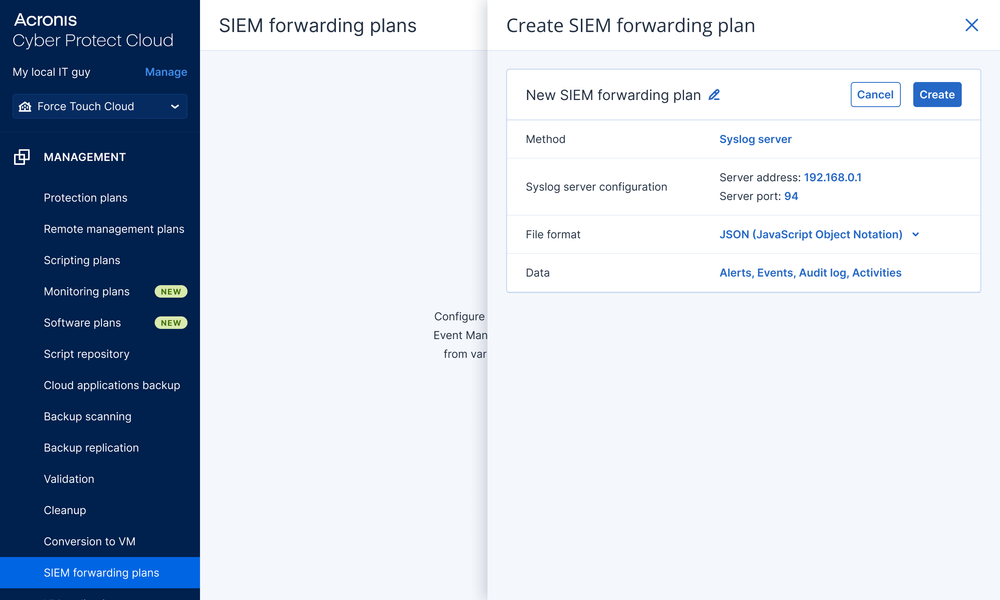
- Create an Acronis SIEM LogForwarding plan.
- Designate a writer device: Select a Windows or Linux device within your network infrastructure and specify the file path for local data storage. Alternatively, select a target syslog server — certificate generation is not required.
- Select data format: Choose your preferred output format (CEF recommended for broad SIEM compatibility or JSON for alternative log processing).
- Configure data collection parameters: Specify which Acronis data streams to forward: Alerts, Events, Tasks or Audit Logs.
That’s it! No certificates generation. No calls to our engineering team (unless you need help with something else... we’re always happy to help).
Microsoft Sentinel integration
The Acronis SIEM Connector is now available for Microsoft Sentinel, reinforcing Acronis' commitment to our MISA (Microsoft Intelligent Security Association) membership. The Sentinel integration includes 12 custom hunting queries and four detection rules, enabling security teams to rapidly investigate and respond to threats within the Microsoft security ecosystem.
Ready to make security integration easier?
The Acronis SIEM Connector is available now in Acronis Cyber Protect Cloud. Simply create a SIEM LogForwarding plan and start collecting Acronis logs.
Have questions? Take a look at the documentation.

About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




