
Trying to figure out the difference between endpoint security and management? Both are important, but they serve very different purposes. A truly resilient cyber strategy requires both working together. Here’s a quick breakdown to help you build a more resilient defense.
Endpoint protection is not the end of protection
2024–2025 trend: Endpoint protection at the center — But is it enough?
Industry analysts forecast global endpoint security spend to reach $27.46 billion in 2025, alongside a 44% year-over-year spike in weekly cyberattacks. In response, 60% of security teams are now integrating AI into their defense stacks. Clearly, endpoint protection has shifted from being a best practice to a board-level priority, and it has become the epicentre of security investments.
But here’s the problem: while organizations race to deploy advanced endpoint solutions, focusing on protection alone isn’t enough. Endpoint security vendors primarily concentrate on the ability to anticipate and withstand attacks, meaning they stop threats before they do damage. But most provide limited capabilities for recovery and adaptation after an incident. Without these aspects, you’re only solving part of the problem.
Endpoint security vs. endpoint management: What's the difference?
Although often used interchangeably, endpoint security and endpoint management are fundamentally different but equally important.
- Endpoint security focuses on protecting devices against cyberthreats like malware, ransomware, phishing and exploits through detection, prevention and rapid response.
- Endpoint management is about deploying, maintaining and optimizing devices, ensuring software is updated, policies are enforced and performance stays high.
To help you see the distinction, here is a quick comparison:
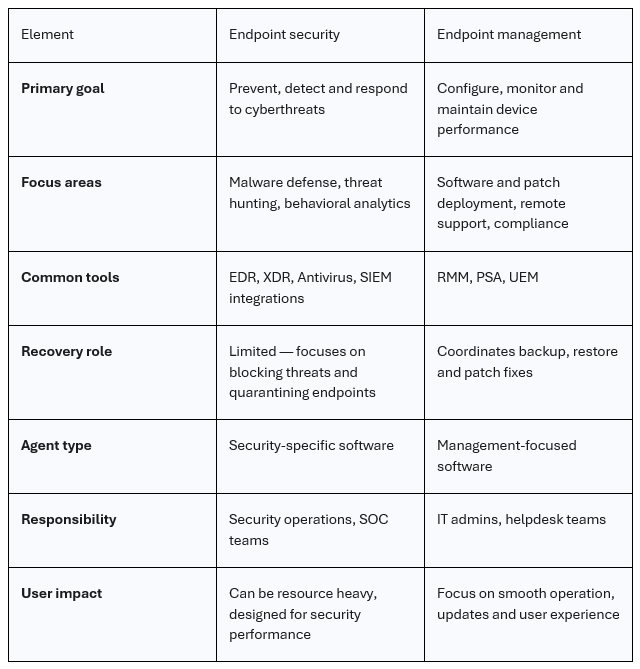
Why the distinction matters:
- Endpoint security protects against attacks but typically does not manage device health, software updates or user support.
- Endpoint management maintains device performance and compliance but lacks deep threat detection and prevention capabilities.
The problem of bloated agents and fragmented recovery
In many organizations, these functions remain siloed or supported by multiple separate agents and tools, which multiplies complexity and burdens endpoint performance. Most organizations run three or more separate agents on each endpoint:
- One agent for endpoint security (EDR / XDR and anti-malware).
- One agent for backup and recovery.
- One agent for remote management (RMM / PSA).
This approach creates agent bloat, a situation where:
- Performance takes a hit: Multiple resource-heavy agents slow down devices and frustrate users.
- Management is a nightmare: IT teams must maintain and update separate agents from multiple vendors.
- Recovery is disconnected: Critical restoration processes aren’t tied into security tools, slowing time-to-recovery.
- User experience suffers: Frequent interruptions and lagging impact productivity.
This fragmented model focuses on the first half of resilience (anticipate and withstand) but neglects the second half (recover and adapt).
The Acronis advantage: One lightweight agent for end-to-end resilience
Acronis is the only truly integrated solution that combines security, management and recovery in a single, lightweight agent — delivering unified cyber resilience without compromise. With Acronis Cyber Protect Cloud, you get:
- Next-gen endpoint protection: EDR, XDR, AI-powered anti-malware, exploit prevention, URL filtering.
- Full endpoint management: RMM, patch management, vulnerability scanning, asset tracking.
- Built-in data protection: Continuous backup, instant restore, disaster recovery orchestration.
- Single management console: Unified visibility and control across all endpoint functions.
- 300+ technology integrations: Easily connect with your existing IT and security tools for complete coverage.
This consolidation means:
- No more juggling multiple agents.
- No more degraded performance.
- Recovery is as fast, integrated and simple as protection.
Why this matters for your business
The cyberthreat landscape is intensifying, with attacks becoming faster, more sophisticated and more damaging. Relying solely on endpoint security or piecing together separate tools for management and recovery is an outdated and risky strategy. True cyber resilience demands a single platform that can seamlessly anticipate, withstand, recover and adapt without sacrificing performance or user experience.
Acronis Cyber Protect delivers that vision by replacing multiple agents with one lightweight, integrated solution that keeps your endpoints protected, managed and recoverable at all times.
To simplify operations, safeguard productivity and ensure business continuity, it’s time to move beyond agent bloat, because endpoint security alone is not the end of security.
Ready to see the difference?
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




