Muji halts online sales after ransomware hits delivery supplier Askul
On October 20, 2025, Japanese retailer Muji suspended domestic online operations due to a ransomware attack on logistics partner Askul, disrupting e-commerce and shipments since October 19, with data theft confirmed and potential exfiltration.
Supply-chain ransomware targets logistics systems for operational shutdowns, enabling extortion via data leaks and halting retail workflows, with ripple effects on integrated payment and inventory databases.
Immediate actions if affected: isolate impacted networks, scan for ransomware, restore from offline backups, and audit third-party vendor security postures.
Acronis Cyber Protect's Active Protection blocks encryption attempts; EDR/XDR detects anomalous file access.
F5 Networks breach exposes BIG-IP source code and undisclosed vulnerabilities
On October 16, 2025, F5 disclosed a nation-state breach (China-linked UNC5221) granting persistent access to its BIG-IP development environment, exfiltrating source code and undisclosed vulnerabilities for potential exploit crafting.
BIG-IP handles critical traffic management, so source code theft risks zero-days enabling lateral movement, data exfiltration, and supply-chain compromises in enterprise networks.
Immediate actions if affected: inventory BIG-IP assets, apply F5's October 15 patches, harden management interfaces per CISA ED 26-01, and audit for anomalies.
Acronis EDR/XDR detects persistence like unusual network probes from BIG-IP compromises; immutable backups secure application delivery data, with vulnerability assessment aiding endpoint scans for downstream impacts.
Microsoft October Patch Tuesday fixes 172 vulnerabilities including six zero-days
On October 15, 2025, Microsoft patched 172 flaws, including six zero-days: CVE-2025-24990 (modem driver EoP, CVSS 7.8, exploited), CVE-2025-59230 (RasMan EoP, CVSS 7.8, exploited), CVE-2025-47827 (Secure Boot bypass, CVSS 4.6, exploited), CVE-2025-2884 (TPM 2.0 info leak, publicly disclosed), CVE-2025-59234 (Office UAF RCE, publicly disclosed), and CVE-2025-59236 (Excel UAF RCE, publicly disclosed).
These enable privilege escalation, code execution, and info disclosure on Windows systems, risking persistent access and data breaches.
Immediate actions if affected: install October updates immediately, disable unused modems/RasMan, and verify Secure Boot integrity.
Acronis Cyber Protect's patch management handles Windows updates; vulnerability assessment detects exposed drivers, with EDR flagging EoP chains.
Netcore Cloud Pvt Ltd exposure—40 billion unencrypted records found
A marketing firm reportedly left a 13 TB publicly accessible database containing roughly 40 billion unencrypted records, including email addresses and banking or healthcare details.
The exposure highlights how simple misconfigurations can cause catastrophic data leaks without any active attack.
Sensitive personal data at this scale increases ransomware, phishing, and identity-theft risks for downstream clients.
Enable Acronis Cyber Protect DLP + backup-scanning to automatically detect sensitive data within backups and ensure encryption and access controls prevent exposure.
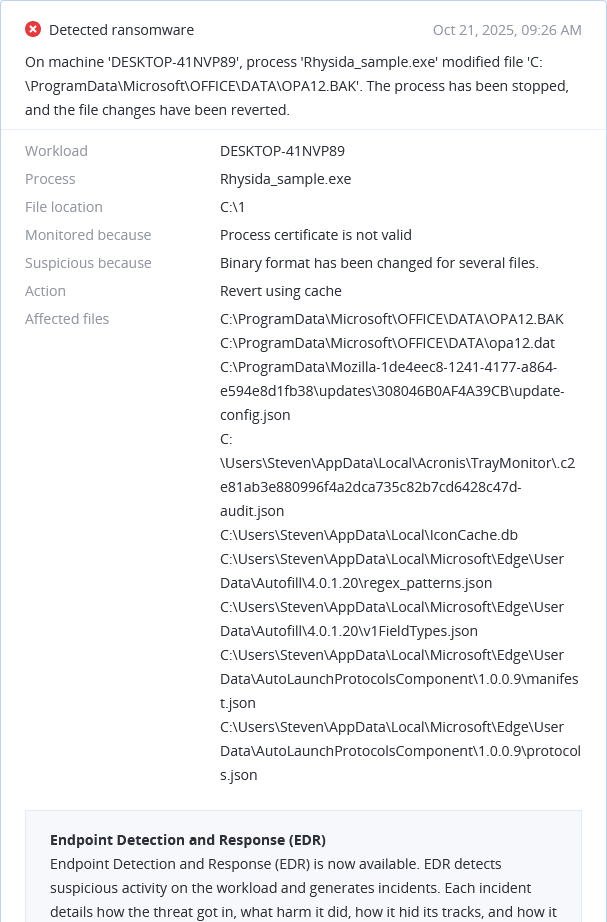
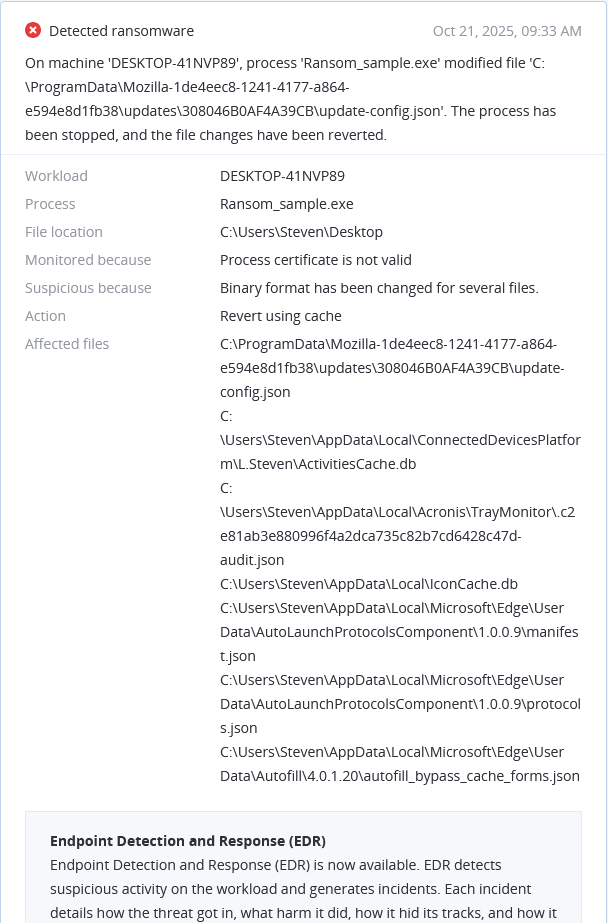
Microsoft revokes 200 fraudulent certificates used in Rhysida ransomware attacks
On October 17, 2025, Microsoft revoked 200 fake certs abused by Vanilla Tempest (Russian actors) to deliver Rhysida ransomware via SEO-poisoned Microsoft Teams installers since September 2025.
Fraudulent certs bypass defenses for stealthy encryption, with SEO tactics targeting enterprises for widespread disruption and extortion.
Immediate actions if affected: scan for MSTeamsSetup.exe variants, update endpoint tools, revoke suspicious certs, and isolate infected systems.
Acronis Cyber Protect's Active Protection detects/blocks Rhysida encryption; anti-malware neutralizes payloads, with patch management ensuring timely Microsoft app updates.