Trojanized ScreenConnect installers evolve, dropping multiple RATs on a single machine
Since March 2025, Acronis TRU has observed a surge in attacks abusing trojanized ConnectWise ScreenConnect installers to target U.S.-based organizations, reflecting a persistent trend in RMM tool exploitation.
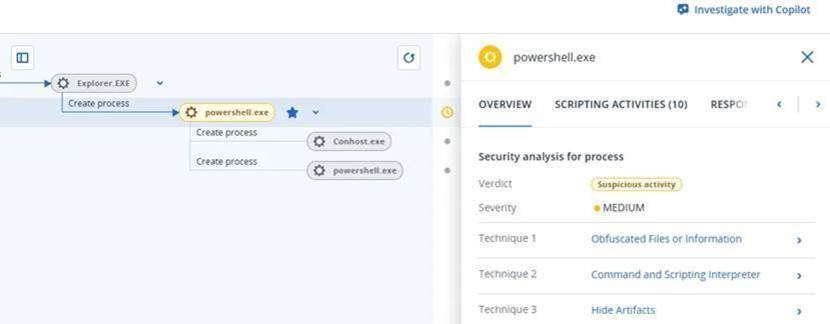
Attackers now leverage smaller ClickOnce installers that fetch components at runtime, evading traditional static detection methods. Once installed, the malicious ScreenConnect client connects to attacker-controlled servers, enabling rapid deployment of two remote access trojans: AsyncRAT and a custom PowerShell-based RAT. The homemade RAT performs system reconnaissance, exfiltrates data via Microsoft.XMLHTTP, and employs multiple obfuscation techniques to evade detection. Two weeks post-compromise, the infection chain evolves, using batch and VBS loaders to fetch encoded .NET assemblies and redeploy AsyncRAT.
Attackers distribute these malicious installers via phishing emails disguised as official or financial documents and reuse preconfigured Windows Server 2022 virtual machines across campaigns for faster redeployment. Additional RATs like PureHVNC are later deployed via WMI and process hollowing, establishing persistence and extending access to compromised hosts. The campaign demonstrates a highly automated, adaptive attack chain with layered persistence, multi-tool deployment, and a broad infrastructure likely shared among multiple threat actors.
Acronis Security + Endpoint Detection and Response (EDR) offers real-time monitoring, isolation of suspicious activity, and automated response to potential threats.
Microsoft September 2025 Patch Tuesday fixes 81 flaws, two zero-days
Microsoft's September 2025 Patch Tuesday delivers fixes for 81 security flaws, including two zero-day vulnerabilities in Windows SMB Server and Microsoft SQL Server. Of the total, nine are rated "Critical," with five enabling remote code execution, one tied to information disclosure, and two allowing elevation of privilege.
In detail, the update addresses 41 elevation of privilege flaws, 22 remote code execution vulnerabilities, 16 information disclosure issues, three denial of service vulnerabilities, two security feature bypasses, and one spoofing vulnerability. The SMB zero-day (CVE-2025-55234) could enable relay attacks, and Microsoft advises admins to audit their SMB servers before enforcing hardening measures like signing and extended protection.
The second zero-day (CVE-2024-21907) impacts Newtonsoft.Json in SQL Server, where crafted data could trigger denial of service via stack overflow.
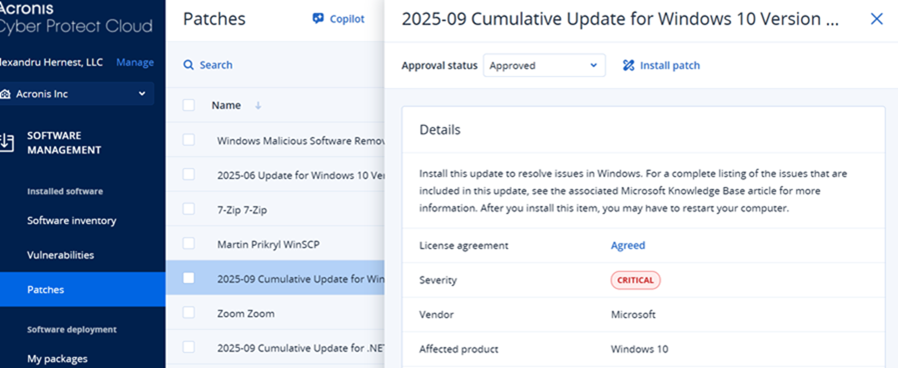
With AI-based patch stability scoring in Acronis RMM, MSPs can quickly see which updates are safe to deploy and which may cause issues, using clear risk labels like "Stable," "Caution," or "Critical." Combined with built-in Patch Management, this allows technicians to prioritize, automate, and confidently keep all systems up to date, reducing downtime and simplifying large-scale software maintenance.
Airport disruptions in Europe caused by ransomware attack
A ransomware attack targeting Collins Aerospace, the external provider of check-in and boarding systems, caused major disruptions at several European airports over the weekend.
Heathrow, Brussels, Berlin Brandenburg, and airports in Ireland, such as Cork and Dublin, were affected, though the impact in Ireland was minor. Attackers compromised the MUSE (Multi-User System Environment) system, which enables airlines to share check-in desks and boarding gates instead of maintaining separate infrastructure. According to ENISA, the incident led to more than 100 flight delays or cancellations, forcing thousands of passengers to be processed manually. Disruptions continued into Monday, with airports advising travelers to confirm flight status while Collins Aerospace worked to restore services.
Law enforcement agencies, including the UK's National Cyber Security Centre, are investigating and urging organizations to strengthen defenses against cyberattacks. Key findings from Acronis TRU note that ENISA confirmed this as a third-party ransomware attack, with the strain identified but undisclosed and the threat actor remaining unknown. Analysts observed that the tactics resemble those of groups like Scattered Spider, which aim at central service providers for broad-scale disruption. Experts also warn of possible data exfiltration, as modern ransomware operations often combine outages with double or triple extortion methods.
Active Protection detects and blocks ransomware-related activities, keeping your data safe from encryption or extortion. Additionally, a simple Backup solution and efficient Disaster Recovery option included in Acronis Cyber Protect allow you to return to normal operations quickly if systems are impacted by a cyberattack or failure.
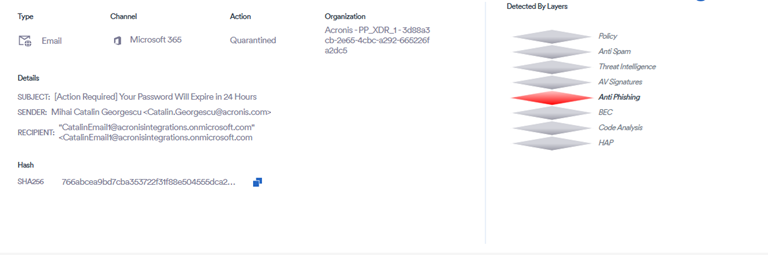
FileFix attacks use fake Facebook security alerts to trick victims into running infostealers
Acronis TRU researchers identified the first sophisticated, in-the-wild FileFix campaign, marking its evolution from earlier proof-of-concept demonstrations.
This variant of ClickFix tricks victims into copying and pasting malicious commands into File Explorer, delivering the StealC infostealer and malware downloader onto Windows machines. The campaign features a multilingual phishing site styled as a Facebook Security alert, layered with obfuscation and anti-analysis techniques to evade detection. Attackers used steganography to embed PowerShell scripts and encrypted payloads into AI-generated JPG images, which are silently processed once downloaded. The attack chain involves multistage payloads with heavy obfuscation, encryption, and sandbox-evasion measures, culminating in a Go-based loader that delivers StealC v2. StealC targets browsers, cryptocurrency wallets, messaging apps, cloud accounts, and even Azure and AWS keys.
Multiple evolving FileFix variants have been observed worldwide within weeks, showing rapid adaptation and a global targeting scope. This campaign underscores how quickly proof-of-concept techniques can mature into real-world threats, highlighting the urgent need for updated phishing awareness and robust endpoint defenses.
Acronis Security + Extended Detection and Response (XDR) detects the attack both at the moment the PowerShell payload is executed and at the moment the payload executable is launched. Acronis Security Awareness Training (SAT) equips employees with the knowledge to detect and prevent cyber threats through interactive learning and smart phishing simulations.
Screenshot 1
Screenshot 2
Iranian hackers exploit 100+ embassy email accounts in global phishing targeting diplomats
An Iran-linked hacking group has carried out a large-scale spear-phishing campaign targeting diplomats through more than 100 compromised embassy and consulate email accounts worldwide.
The campaign, attributed to operators associated with the group Homeland Justice, used emails disguised as legitimate diplomatic communications to target government entities across Europe, Africa, the Middle East, Asia, and the Americas.
Attackers relied on phishing emails carrying malicious Microsoft Word documents that tricked recipients into enabling macros, which deployed malware designed for persistence, command-and-control communication, and data harvesting. The emails exploited geopolitical themes to enhance credibility and urgency. Many of the phishing messages originated from hijacked accounts, including one belonging to the Oman Ministry of Foreign Affairs in Paris, adding legitimacy to the operation.
Acronis Email Security helps address and mitigate email-borne threats, while Acronis Security + Endpoint Detection and Response (EDR) offers real-time monitoring and response, detecting suspicious activities and preventing malicious payloads.