Google patches sixth Chrome zero-day exploited in attacks this year
CISA has added CVE-2025-10585, a Google Chromium V8 type confusion vulnerability, to its Known Exploited Vulnerabilities (KEV) Catalog due to evidence of active exploitation.
This vulnerability poses high risks to federal systems, and under Binding Operational Directive (BOD) 22-01, Federal Civilian Executive Branch (FCEB) agencies must remediate it by the set deadline. While BOD 22-01 is mandatory only for FCEB agencies, CISA urges all organizations to prioritize fixing KEV-listed flaws as part of strong cyber defense practices. Google confirmed that an exploit for CVE-2025-10585 exists in the wild and released emergency Chrome updates for Windows, Mac, and Linux to address the issue.
This marks the sixth actively exploited Chrome zero-day patched in 2025, with previous fixes rolled out in March, May, June, and July. To ensure protection, Chrome users are advised to update immediately via the browser's settings, as further technical details remain restricted until most users are patched.
The Acronis #CyberFit Score enables you to quickly pinpoint systems requiring attention, while Acronis RMM, with its integrated Patch Management, streamlines the process of keeping your software up to date, minimizing risk and ensuring timely compliance across all managed systems.
Volvo North America confirms third-party data breach
Volvo North America has confirmed that employee data was compromised in a third-party breach involving its human resources software supplier, Miljödata.
The incident, discovered in late August, exposed sensitive personal details such as full names and Social Security numbers, with Volvo notifying affected staff in early September. Miljödata, which also provides services to hundreds of Swedish municipalities and organizations, was hit by a ransomware attack in which systems were encrypted and extortionists demanded payment of 1.5 bitcoin. Data from the attack was later published on the dark web, including nearly 870,000 unique email addresses. About 250 Miljödata customers, including 164 municipalities and four regions, have reported being affected to Sweden's privacy authority.
Miljödata has since strengthened its security measures and launched an investigation with cybersecurity experts to prevent future incidents. Authorities in Sweden, along with Volvo and other impacted organizations, continue to assess the scale of the attack and its potential long-term effects.
Acronis Active Protection detects and stops ransomware encryption attempts, safeguarding sensitive data from exfiltration and extortion.
UNC5221 uses BRICKSTORM backdoor to infiltrate U.S. legal and technology sectors
A China-linked cyber espionage group known as UNC5221 has been using the BRICKSTORM backdoor to target U.S. legal, SaaS, BPO, and technology sectors.
The goal is to gain long-term access, steal sensitive data, and collect intelligence related to national security, trade, and intellectual property. BRICKSTORM, a Go-based malware, enables attackers to manipulate files, execute commands, act as a SOCKS relay, and communicate via WebSockets, making it effective for stealthy operations. Reports show that the attackers often exploit Ivanti Connect Secure flaws or deploy additional tools like BRICKSTEAL and SLAYSTYLE to escalate privileges, move laterally, and maintain persistence. Researchers note that intrusions frequently evade detection for more than a year due to the group's use of appliances lacking EDR coverage and their ability to erase traces.
Evidence suggests BRICKSTORM is under active development, with new features designed to delay detection and maintain control during incident response. Experts warn that this campaign poses a significant threat, as UNC5221 could leverage its access to compromise downstream customers or discover new zero-day vulnerabilities for future attacks.
Acronis Security + Endpoint Detection and Response (EDR) offers real-time monitoring, isolation of suspicious activity, and automated response to potential threats.
Jaguar Land Rover cyber incident stalls plants, insurance not secured
Jaguar Land Rover (JLR), Britain's largest carmaker with a revenue of USD 38.7 billion, was in the midst of negotiating a cyber insurance policy when a major cyberattack struck in early September, forcing system shutdowns that halted production, sent staff home, and led to weekly losses of approximately USD 66.8 million.
JLR has extended its production pause until October 1 as it works with cybersecurity specialists, law enforcement, and the U.K.'s National Cyber Security Centre. Initially, JLR stated there was no evidence of stolen data, but it later confirmed that company data had been compromised without providing specifics. Reports indicate that the attack was claimed by Scattered Spider, a hacking group linked to social engineering campaigns against major U.K. retailers.
Jaguar Land Rover (JLR) was left without coverage during the recent cyberattack after its insurance deal with broker Lockton fell through. The prolonged shutdown has raised concerns among authorities and unions over the impact on thousands of workers, even as JLR prepares a phased restart of operations. In response, the UK Government has announced a loan guarantee worth up to USD 1.8 billion to support the company and its supply chain, with backing from UK Export Finance. The package is designed to protect jobs, stabilize suppliers, and underline the government's long-term commitment to the automotive sector through its Industrial Strategy.
A simple Backup solution and efficient Disaster Recovery option included in Acronis Cyber Protect allow you to return to normal operations quickly if systems are impacted by a cyberattack or failure.
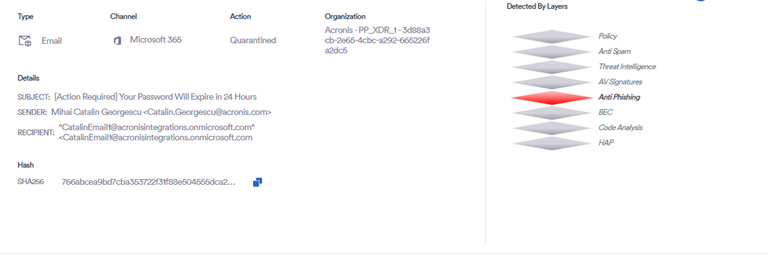
Phishing campaign evolves into PureRAT deployment, linked to Vietnamese threat actors
Researchers uncovered a phishing campaign that began with a Python-based infostealer and evolved into the deployment of PureRAT, a sophisticated remote access trojan.
The attack started with phishing emails delivering a ZIP archive containing a signed executable and malicious DLL, which triggered a 10-stage chain of loaders, encryption, and persistence techniques. By stage three, the attackers shifted from Python scripts to compiled .NET executables, using process hollowing, AMSI and ETW patching, and ultimately deploying PureRAT. PureRAT enabled encrypted communication, host fingerprinting, and the loading of additional malicious modules, while earlier stages focused on stealing credentials and browser data.
Evidence, including use of the Telegram Bot API and infrastructure traced to Vietnam, linked the campaign to the PXA Stealer family associated with Vietnamese threat actors.
Acronis Email Security helps address and mitigate email-borne threats, while Acronis Security + Endpoint Detection and Response (EDR) offers real-time monitoring and response, detecting suspicious activities and preventing malicious payloads.