Every bit of lost data or minute of downtime can be tragic. Data is growing at approximately three times the rate of IT staff. On average, downtime can cost $5,600 per minute. That combination can be detrimental to a small or medium-sized business. You need to proactively protect your business-critical data, applications and systems, and the faster you can recover, the better. From backup with rapid restores to full disaster recovery, Acronis enables you to avoid business disruption.
- 200 minutesAverage time spent on resolving an incidence of IT downtime
- $155 millionAverage annual cost of IT downtime for businesses
- 70%Of organizations are likely to suffer business disruption by 2022 due to unrecoverable data loss

Customer satisfaction is the single most important aspect of any business as it leads to additional sales, reputational growth, and “word of mouth” recommendations. That’s why Acronis honored to be named an October 2019 a Gartner Peer Insights Customers’ Choice for Cyber Disaster Recovery as a Service (DRaaS)
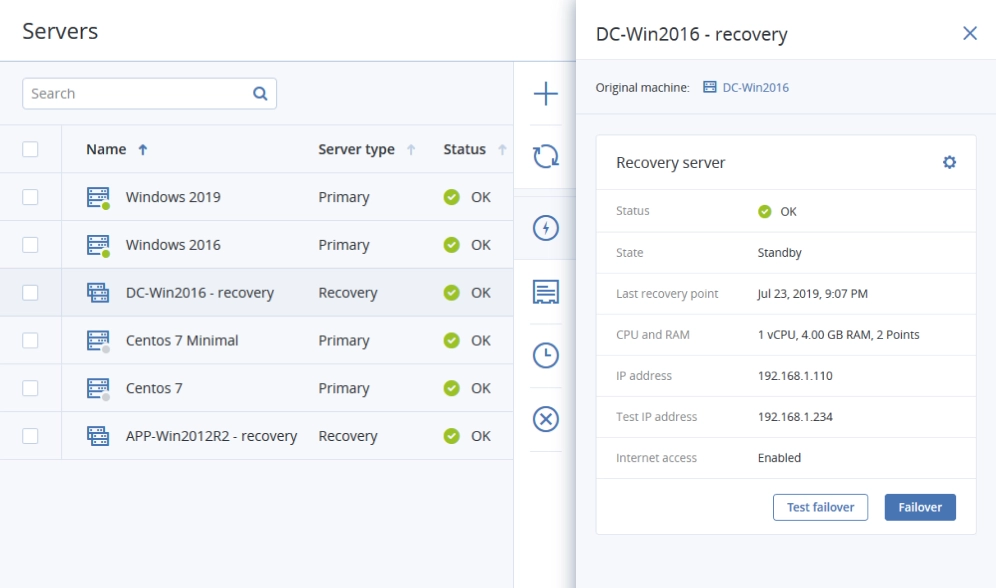
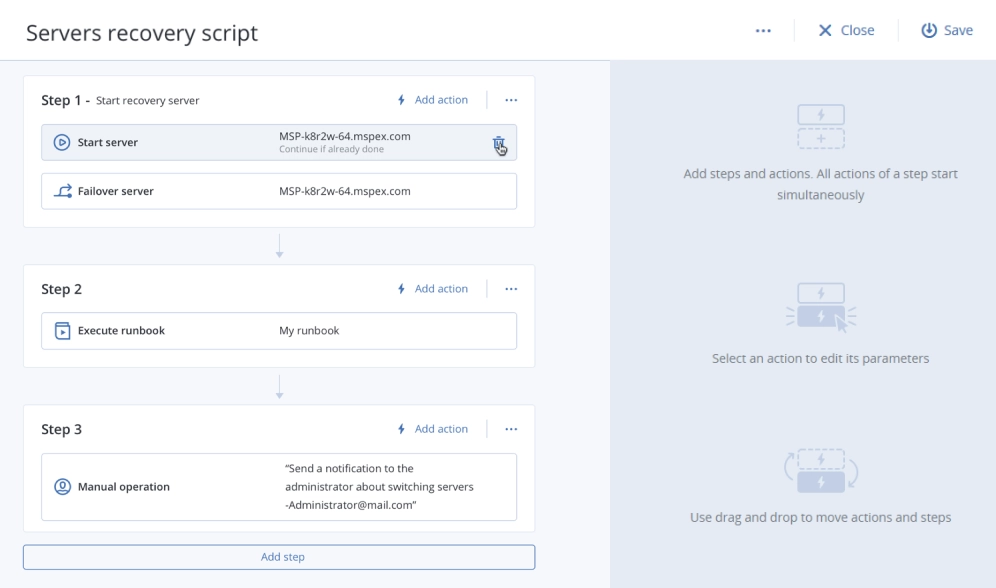
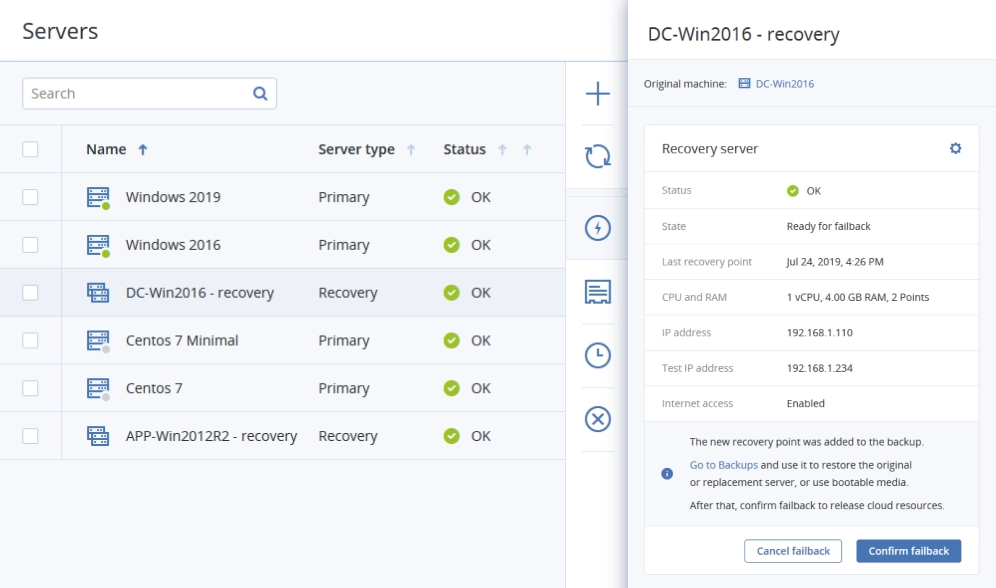
Acronis is the answer to help you meet your rapid data recovery needs – with out-of-the-box RTOs and RPOs of under a minute to an optional automated cloud-based disaster recovery implementation for critical apps.
Acronis
- Acronis Cyber ProtectIntegrated world-class recovery and advanced cybersecurity capabilities provide unmatched backup to create the first complete cyber protection solution for businesses of any size.
- Acronis Cyber Disaster Recovery as a ServiceGet up and running in mere minutes on your own, or let us introduce you to one of our certified partners to manage DR for you.

“[We can] recover individual files, application data, or the entire virtual platform, all from a centralized management console that is easy to use and administrate. It also offers RFR the flexibility to restore to the original or new location, including recovery to a completely different hypervisor. There is nothing stock about stock car racing. Making sure that our data is safe is critical, and Acronis has given us an additional layer of safety and much needed cyber protection.”
Implement a better disaster recovery solution
Faster recovery, even better protection
World’s fastest backup and recovery
Backup and restore data faster with a 15-second recovery time, and backup speeds that are twice as fast as the competition.AI-powered anti-ransomware protection
Proactively protect data by detecting zero-day attacks, stopping questionable behavior, and automatically recovering damaged files.Continuous data protection
Safeguard new data by capturing and backing up important changes in real-time.
Integrated cyber protection
Acronis Cyber Protect proactively protects your business with a unique integration of data protection and cybersecurity – so you can prevent data loss from happening in the first place.
Unique integration
The integration of advanced anti-malware and backup enables you to automatically recover a clean copy of the corrupt data. Backups are protected against attacks on the agent and backup files, ensuring the data is clean. Automatic detection, prevention, and recovery streamlines your operations – reducing both the number of support calls and the time spent on each incident – making your team more efficient.Continuous Data Protection
Ensure users don’t lose their work in-progress by defining a list of critical apps that they frequently use. Acronis’ agent monitors every change made in the listed applications—no matter where the user saves the file – and continuously backs it up. If the system needs to be reimaged, you can restore the data from a backup and apply the latest changes, so no data is lost.Safe recovery
The OS image or applications in a backup can have vulnerabilities and can cause continuous reinfection if malware is still active in the network. Patching the machine and applying the latest anti-malware definitions allows users to restore the OS image with the latest patches, reducing the chance of a reoccurring infection.Malware scans in the Acronis Cloud
Prevent restoring infected files from backups with built-in malware scanning. By scanning full disk backups at a centralized location, Acronis Cyber Protect Cloud can help find malware – ensuring users restore a clean, malware-free backup.Acronis Universal Restore
Restore Windows and Linux systems to the same, similar, or dissimilar hardware during a failback procedure, including bare-metal, physical, virtual, or cloud environments.
Acronis
- Acronis Cyber ProtectIntegrated world-class recovery and advanced cybersecurity capabilities provide unmatched backup to create the first complete cyber protection solution for businesses of any size.
- Acronis Cyber Disaster Recovery as a ServiceGet up and running in mere minutes on your own, or let us introduce you to one of our certified partners to manage DR for you.
One solution for any workload
Physical and Virtual Machines
- Windows
- Mac
- Linux
Virtualization Platforms
- Virtualization Platforms
- Vmware vSphere
- Microsoft Hyper-V
- Citrix XenServer
- Red Hat Virtualization
- Linux KVM
- Azure VM
- Oracle VM Server
Applications
- Microsoft 365
- Google Workspace
- Microsoft Exchange
- Microsoft SQL Server
- Microsoft SharePoint
- Microsoft Active Directory
- Oracle Database
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.