Working with search results
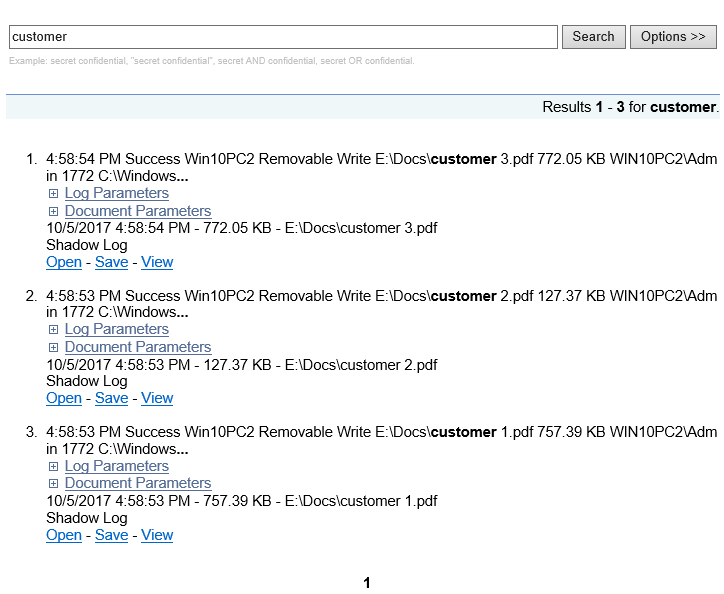
When performing a full-text search, the server returns a search results page that looks like this:
The search results page is divided into the following viewing areas:
•
Search query - Displays the search criteria that were used.
•
Statistics bar - Shows the number of results displayed on the current search results page.
•
Search results - Displays a numbered list of items containing information that matched the search criteria.
•
Results navigator - Shows how many results pages are returned, and allows one to navigate from page to page.
These areas are described in more detail in the sections that follow.
Search query
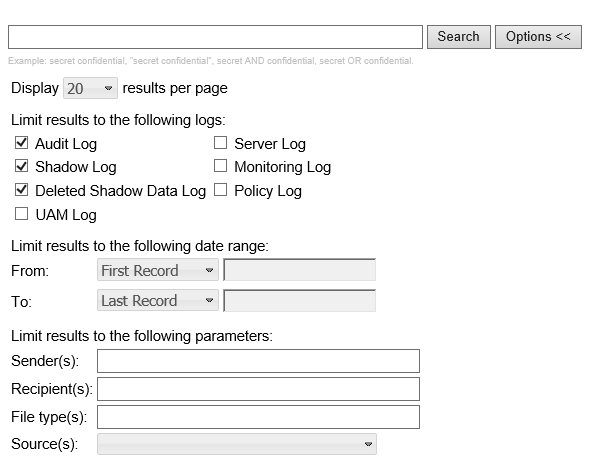
This area is located at the top of the search results page. Click Options to view all the search parameters that were used during the search:
For a description of the search parameters, see
Steps to perform a search.
Statistics bar
This area is located directly above the search results area, and it looks like this:
Search results
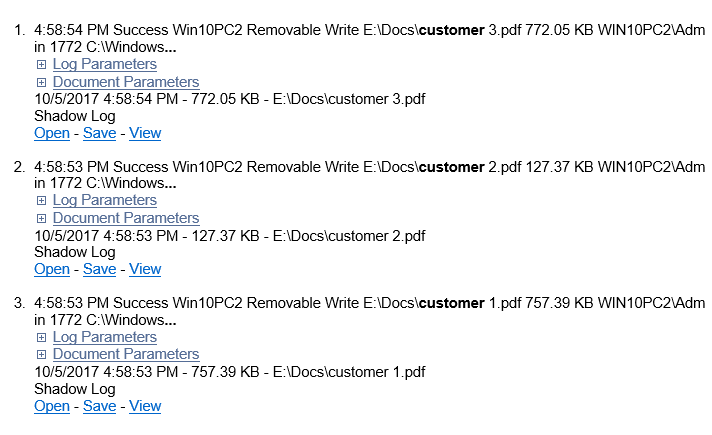
This area is located below the search query area and statistics bar, and it looks like this:
A search result includes the following items:
•Snippets - Text fragments containing query words (highlighted bold). These snippets allow one to see the context in which the query words were found. Only the first three snippets are displayed per search result.
•Log Parameters - Summary information found in the log for the search result, depending on the log type. Click the plus sign (+) to expand Log Parameters and view this information.
Note: Empty fields of log records are not displayed in Log Parameters. |
For search results retrieved from the Audit Log, the Log Parameters information includes:
•Type - The class of the event: Success - an allowed action; Failure - a denied action; Information - a content detection event; Warning - indication of a potential problem. Matches the Type column data in the server Audit Log Viewer.
•Computer - The name of the computer on which the event occurred. Matches the Computer column data in the server Audit Log Viewer.
•Date/Time - The date and time that the DeviceLock Service logged the event. Matches the Date/Time column data in the server Audit Log Viewer.
•Source - The type of device or protocol that caused the event. Matches the Source column data in the server Audit Log Viewer.
•Action - The user’s activity type. Matches the Action column data in the server Audit Log Viewer.
•Name - The name of the object (file, USB device, etc.) associated with the event. Matches the Name column data in the server Audit Log Viewer.
•Information - Other device- or protocol-specific information for the event, such as the access flags, the device or protocol name, device ID and description, etc. Matches the Information column data in the server Audit Log Viewer.
•Reason - The cause of the event. Matches the Reason column data in the server Audit Log Viewer.
•User - The name of the user associated with the event. Matches the User column data in the server Audit Log Viewer.
•PID - The identifier of the process associated with the event. Matches the PID column data in the server Audit Log Viewer.
•Process - The fully qualified path to the process executable file. In some cases, the process name may be displayed instead of the path. Matches the Process column data in the server Audit Log Viewer.
•Event - The number identifying the event type. Matches the Event column data in the server Audit Log Viewer.
•Received Date/Time - The date and time that the DeviceLock Enterprise Server received the event. Matches the Received Date/Time column data in the server Audit Log Viewer.
•Server - The name of the DeviceLock Enterprise Server host that received the event from the DeviceLock Service. Matches the Server column data in the server Audit Log Viewer.
•Consolidation Server - The name of the remote server from which the event was last received during log consolidation. Matches the Consolidation Server column data in the server Audit Log Viewer.
•Consolidated Date/Time - The date and time that the event was last received from the remote server during log consolidation. Matches the Consolidated Date/Time column data in the server Audit Log Viewer.
•DeviceLock Enterprise Server - The name of the DeviceLock Enterprise Server host from which the Search Server indexed the event data.
For search results retrieved from the Shadow Log or Deleted Shadow Data Log, the Log Parameters information includes:
•Status - The status of the record: Success - shadow copy successfully logged; Incomplete - shadow copy possibly not completely logged; Failed - shadow copy of data the transmission of which was blocked by Content-Aware Rules. Matches the Status column data in the server Shadow Log Viewer.
•Computer - The name of the computer on which the shadow copy was received. Matches the Computer column data in the server Shadow Log Viewer.
•Date/Time - The date and time that the shadow copy was logged by the DeviceLock Service. Matches the Date/Time column data in the server Shadow Log Viewer.
•Source - The type of the device or protocol involved. Matches the Source column data in the server Shadow Log Viewer.
•Action - The user’s activity type. Matches the Action column data in the server Shadow Log Viewer.
•File Name - The original path to the file or the auto-generated name of the data that originally was not a file (such as CD/DVD/BD images, data written directly to the media, or transferred through the serial/parallel ports). Matches the File Name column data in the server Shadow Log Viewer.
•File Size - The size of the data. Matches the File Size column data in the server Shadow Log Viewer.
•File Type - The real type of the file. Matches the File Type column data in the server Shadow Log Viewer.
•Reason - The cause of the event. Matches the Reason column data in the server Shadow Log Viewer.
•Protected - Indicates the protection status of the file. Matches the Protected column data in the server Shadow Log Viewer.
•Information - Other device- or protocol-specific information for the event, such as the access flags, the device or protocol name, device ID and description, etc. Matches the Information column data in the server Shadow Log Viewer.
•User - The name of the user who transferred the data. Matches the User column data in the server Shadow Log Viewer.
•PID - The identifier of the process used to transfer the data. Matches the PID column data in the server Shadow Log Viewer.
•Process - The fully qualified path to the process executable file. In some cases, the process name may be displayed instead of the path. Matches the Process column data in the server Shadow Log Viewer.
•Received Date/Time - The date and time that the DeviceLock Enterprise Server received the event. Matches the Received Date/Time column data in the server Shadow Log Viewer.
•Server - The name of the DeviceLock Enterprise Server host that received the event from the DeviceLock Service. Matches the Server column data in the server Shadow Log Viewer.
•Consolidation Server - The name of the remote server from which the event was last received during log consolidation. Matches the Consolidation Server column data in the server Shadow Log Viewer.
•Consolidated Date/Time - The date and time that the event was last received from the remote server during log consolidation. Matches the Consolidated Date/Time column data in the server Shadow Log Viewer.
•DeviceLock Enterprise Server - The name of the DeviceLock Enterprise Server host from which the Search Server indexed the event data.
For search results retrieved from the UAM Log, the Log Parameters information includes:
•Computer - The name of the computer on which the user activity monitoring session was recorded. Matches the Computer column data in the server UAM Log Viewer.
•Date/Time - The date and time that the recording of the monitoring session started. Matches the Date/Time column data in the server UAM Log Viewer.
•Type - The types of recording available in this session: Video - The computer screen video recording only; Keylogger - The computer keystrokes recording only; Video, Keylogger - The computer screen recording and keystrokes recording. Matches the Type column data in the server UAM Log Viewer.
•Rule - The name of the rule that caused the recording. Multiple rules could be listed here if more than one rule triggered during this recording. Matches the Rule column data in the server UAM Log Viewer.
•Reason - The triggering criteria of the rule that caused the recording. In case of multiple rules, a separate list of triggering criteria is specified for each rule. Matches the Reason column data in the server UAM Log Viewer.
•Duration - The time span that recording lasted. Matches the Duration column data in the server UAM Log Viewer.
•User - The name of the user whose activity is recorded in this session. Matches the User column data in the server UAM Log Viewer.
•Received Date/Time - The date and time that the DeviceLock Enterprise Server received this session record from the DeviceLock Service. Matches the Received Date/Time column data in the server UAM Log Viewer.
•Server - The name of the DeviceLock Enterprise Server host that received this session record from the DeviceLock Service. Matches the Server column data in the server UAM Log Viewer.
•Consolidation Server - The name of the remote server from which this session record was last received during log consolidation. Matches the Consolidation Server column data in the server UAM Log Viewer.
•Consolidated Date/Time - The date and time that this session record was last received from the remote server during log consolidation. Matches the Consolidation Date/Time column data in the server UAM Log Viewer.
•DeviceLock Enterprise Server - The name of the DeviceLock Enterprise Server host from which the Search Server indexed the monitoring session data.
For search results retrieved from the Server Log, the Log Parameters information includes:
•Type - The class of the event: Success, Information, Warning, or Error. Matches the Type column data in the Server Log Viewer.
•Date/Time - The date and time when the event occurred. Matches the Date/Time column data in the Server Log Viewer.
•Event - The number identifying the event type. Matches the Event column data in the Server Log Viewer.
•Information - Event-specific information, such as error/warning descriptions, names and values of changed parameters, etc. Matches the Information column data in the Server Log Viewer.
•Server - The name of the DeviceLock Enterprise Server host on which the event occurred. Matches the Server column data in the Server Log Viewer.
•Record N - The record number. Matches the Record N column data in the Server Log Viewer.
•Consolidation Server - The name of the remote server from which the event was last received during log consolidation. Matches the Consolidation Server column data in the Server Log Viewer.
•Consolidated Date/Time - The date and time that the event was last received from the remote server during log consolidation. Matches the Consolidated Date/Time column data in the Server Viewer.
•DeviceLock Enterprise Server - The name of the DeviceLock Enterprise Server host from which the Search Server indexed the event data.
For search results retrieved from the Monitoring Log, the Log Parameters information includes:
•Type - The class of the event: Success, Information, Warning, or Error. Matches the Type column data in the Monitoring Log Viewer.
•Date/Time - The date and time when the event occurred. Matches the Date/Time column data in the Monitoring Log Viewer.
•Event - The number identifying the event type. Matches the Event column data in the Monitoring Log Viewer.
•Task Name - The name of the monitoring task associated with the event. Can be empty if the event does not apply to a monitoring task. Matches the Task Name column data in the Monitoring Log Viewer.
•Computer Name - The name of the computer belonging to the monitoring task associated with the event. Can be empty if the event does not apply to a computer. Matches the Computer Name column data in the Monitoring Log Viewer.
•Information - Event-specific information, such as status, error, warning, etc. Matches the Information column data in the Monitoring Log Viewer.
•Server - The name of the DeviceLock Enterprise Server host on which the event occurred. Matches the Server column data in the Monitoring Log Viewer.
•Record N - The record number. Matches the Record N column data in the Monitoring Log Viewer.
•Consolidation Server - The name of the remote server from which the event was last received during log consolidation. Matches the Consolidation Server column data in the Monitoring Log Viewer.
•Consolidated Date/Time - The date and time that the event was last received from the remote server during log consolidation. Matches the Consolidated Date/Time column data in the Monitoring Viewer.
•DeviceLock Enterprise Server - The name of the DeviceLock Enterprise Server host from which the Search Server indexed the event data.
For search results retrieved from the Policy Log, the Log Parameters information includes:
•Type - The class of the event: Success, Information, Warning, or Error. Matches the Type column data in the Policy Log Viewer.
•Date/Time - The date and time when the event occurred. Matches the Date/Time column data in the Policy Log Viewer.
•Event - The number identifying the event type. Matches the Event column data in the Policy Log Viewer.
•Policy Object - The name of the policy object associated with the event. Can be empty if the event does not apply to a policy object. Matches the Policy Object column data in the Policy Log Viewer.
•Computer Name - The name of the computer that caused the event. Can be empty if the event does not apply to a computer. Matches the Computer Name column data in the Policy Log Viewer.
•Information - Event-specific information, such as status, error, warning, etc. Matches the Information column data in the Policy Log Viewer.
•Server - The name of the DeviceLock Enterprise Server host that logged the event. Matches the Server column data in the Policy Log Viewer.
•Record N - The record number. Matches the Record N column data in the Policy Log Viewer.
•Consolidation Server - The name of the remote server from which the event was last received during log consolidation. Matches the Consolidation Server column data in the Policy Log Viewer.
•Consolidated Date/Time - The date and time that the event was last received from the remote server during log consolidation. Matches the Consolidated Date/Time column data in the Policy Viewer.
•DeviceLock Enterprise Server - The name of the DeviceLock Enterprise Server host from which the Search Server indexed the event data.
•Document Parameters - Summary information retrieved from the document properties for search results from shadow logs Click the plus sign (+) to expand Document Parameters and view this information. This information varies depending upon the file type. For example, the following information is displayed in Document Parameters for a shadow copy of a Word document:
•Application - Microsoft Office Word.
•Author - The name of the user who created the document.
•Created - The date and time when the document was created.
•LastSaved - The date and time when the document was last saved.
•LastSavedBy - The name of the user who last saved the document.
•RevisionNumber - The number of times the changes to the document were saved.
•Template - The name of the template attached to the document.
•Title - The name of the document.
•TotalEditingTime - The number of minutes that the document has been opened for making changes since it was created.
For search results from the UAM Log, the Document Parameters area lists user-entered logins and passwords (if they were logged). The parameter name in this case is Passwords.
•The date and time of the log record.
•The size of the log record. This value is displayed only for shadow copies retrieved from shadow logs.
•The name of the log in which matches of the query occurred.
•Open,
Save,
View - On search results from the shadow logs, these links allow you to open, view, and save shadow copies. For details, see
Working with shadow copies.
On search results from the UAM Log, you can use these links to open, view, or save the recorded keyboard input (keylog). These links only appear on search results that contain a keylog. The keylog opens in the application that is registered to work with HTML files in the operating system. When viewing, the keylog is displayed in a console window. When saving, the keylog is stored as an HTML file.
Note: If the search produced no results, the search results page displays a message indicating that no matches were found. |
Results navigator
This area is located at the bottom of the search results page, and it looks like this:
To move forward or backward through search results, click Next or Previous, or click the page number.