Report Permissions/Auditing
The Report Permissions/Auditing plug-in generates a report that allows you to view and change security policies defined for device types and protocols across the network.
Before you can use this plug-in, you should select the information you want to include in the report, by clicking the
Settings button below the plug-ins list in the
Scan Network dialog box (see
Selecting Plug-ins).
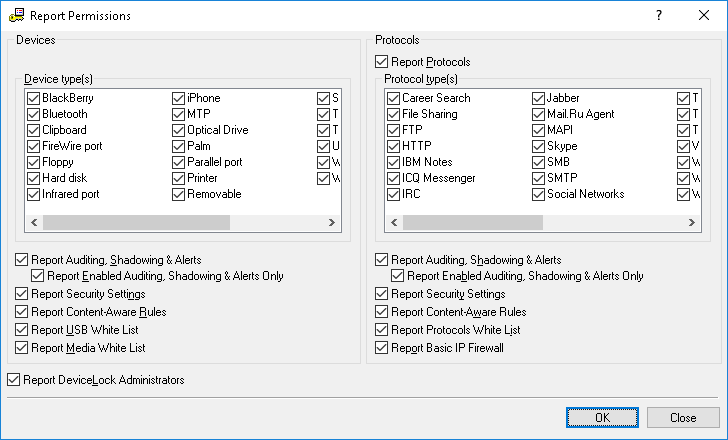
In the Report Permissions dialog box that appears when you click the Settings button, specify the information that you want to include in your report.
To receive information on the security policies defined for device types, under Devices, use the following options:
•Report Auditing, Shadowing & Alerts - Select this check box to report audit, shadowing rules and alerts that have been set. Also when this check box is selected, you receive information about whether the
Log Policy changes and Start/Stop events parameter is enabled in
Service Options.
•Report Enabled Auditing, Shadowing & Alerts Only - Select this check box to exclude devices for which audit, shadowing rules and alerts are disabled from the report.
This option is available only if the Report Auditing, Shadowing & Alerts check box is selected.
•Report DeviceLock Administrators - Select this check box to report accounts that can manage DeviceLock Service or view its settings and logs.
To receive information on the security policies defined for protocols, under Protocols, use the following options:
•Report Protocols - Select this check box to report security policies for protocols. Otherwise, information on all protocol-based policies will be excluded from the report.
If the Report Protocols check box is cleared, the Report Auditing, Shadowing & Alerts option and the Report Enabled Auditing, Shadowing & Alerts Only option are unavailable.
•Report Auditing, Shadowing & Alerts - Select this check box to report audit, shadowing rules and alerts that have been set for protocols.
•Report Enabled Auditing, Shadowing & Alerts Only - Select this check box to exclude protocols for which audit, shadowing rules and alerts are disabled from the report.
This option is available only if the Report Auditing, Shadowing & Alerts check box is selected.
•Report Basic IP Firewall - Select this check box to report Basic IP Firewall rules that have been set (see
Managing Basic IP Firewall).
This report always includes information about an installed DeviceLock Certificate (see
DeviceLock Certificates). Also, it always shows whether the
Use Group/Server Policy parameter is enabled in
Service Options.