Server administrators and certificate
On the second page, you can define the list of users that have administrative access to DeviceLock Enterprise Server and install DeviceLock Certificate (the private key).
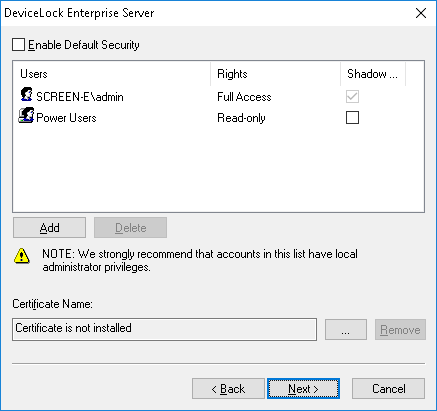
Enable Default Security
In the default security configuration all users with local administrator privileges (i.e. members of the local Administrators group) can connect to DeviceLock Enterprise Server using a management console and change its setting and run reports.
To turn on the default security, select the Enable Default Security check box.
If you need to define more granular access to DeviceLock Enterprise Server, turn off the default security by clearing the Enable Default Security check box.
Then you need to specify authorized accounts (users and/or groups) that can connect to DeviceLock Enterprise Server. To add a new user or user group to the list of accounts, click on the Add button. You can add multiple accounts at a time.
To remove a record from the list of accounts, use the Delete button. By pressing and holding down the Ctrl or Shift key, you can select and remove multiple records at a time.
To determine the actions allowed to a user or group, select the desired level of access to the server:
•Full access - Allows the user or group to install and uninstall DeviceLock Enterprise Server, connect to it by using DeviceLock Management Console, and perform any actions on the server, such as making changes to server settings, creating, editing and running monitoring tasks and report creation tasks, viewing reports, and configuring policies.
•Change - Same as full access to the server with the exception of the right to make changes to the list of server administrators or change the level of access to the server for the users or groups already in that list.
•Read-only - Allows the user or group to connect to DeviceLock Enterprise Server by using DeviceLock Management Console, view server settings, run report creation tasks and view reports. This option does not give the right to make any changes on the server, create, edit or run monitoring tasks, create or edit report creation tasks, or configure policies.
For users and groups with
Change or
Read-only access, the
Shadow Data Access option can be selected to allow access to shadow copies and user activity records. The users and groups with this option selected are allowed to open, view, and save shadow copies and user activity records from DeviceLock Enterprise Server logs by using Shadow Log Viewer (see
Shadow Log Viewer (Server)) and UAM Log Viewer (see
Viewing User Activity).
Without access to shadow data, DeviceLock Enterprise Server administrators do not have access to the content of shadow copies and user activity records. They cannot open, view, or save shadow copies and records of user activity.
Important: We strongly recommend that DeviceLock Enterprise Server administrators be given local administrator rights as installing, updating, and uninstalling DeviceLock Enterprise Server may require access to Windows Service Control Manager (SCM) and shared network resources. |
Certificate Name
You may need to deploy the private key to DeviceLock Enterprise Server if you want to enable authentication based on DeviceLock Certificate.
There are two methods of DeviceLock Enterprise Server authentication on remotely running DeviceLock Services:
•User authentication - The DeviceLock Enterprise Server service is running under the user’s account that has full administrative access to DeviceLock Service on the remote computer. For more information on how to run DeviceLock Enterprise Server on behalf of the user, see the
Log on as parameter description.
•DeviceLock Certificate authentication - In the situations where the user under which the DeviceLock Enterprise Server service is running can’t access DeviceLock Service on the remote computer, you must authenticate based on a DeviceLock Certificate.
The public key should be installed on DeviceLock Service and the corresponding private key on DeviceLock Enterprise Server.
To install DeviceLock Certificate, click the

button, and select the file with a private key. To remove DeviceLock Certificate, click the
Remove button.
For more information regarding DeviceLock Certificate, see the
DeviceLock Certificates section later in this document.
Click the Next button to apply changes and proceed to the third page of the configuration wizard.

 button, and select the file with a private key. To remove DeviceLock Certificate, click the Remove button.
button, and select the file with a private key. To remove DeviceLock Certificate, click the Remove button.