Cyber resilience is the term used to describe the quality of IT infrastructure that is pliable and robust enough to withstand changes and modifications and can rapidly return to a stable state. These changes and modifications can include a cyberattack, the onboarding of new employees, adding new endpoints or workloads to the network, hardware failures, or a merger or acquisition – in short, any activity that changes and “disturbs” the status quo. In some cases, a cyber resilient infrastructure can withstand a disturbance and quickly return to its normal or static state. In other cases, the infrastructure may withstand a disturbance and, as a result, create a new, dynamic state. Any disturbance introduces an opportunity for cybercriminals to attack your systems and data.
Disturbances to the status quo are considered business as usual, which is why every organization must by cyber resilient. Resilient organizations can go back to a stable state faster. However, to ensure your clients’ data, applications and systems are secure, you will need more than cyber resilience. You also need cyber protection against attacks, incidents and accidents – and the ability to recover after an attack.
Cyber Resilience Framework – How does it work?
There are many popular cyber frameworks today that employ three-step frameworks. But modern cybersecurity organizations, such as Acronis, believe the optimum framework should include five steps: prevention, detection, response, recover and forensics. The specific features for each of the framework elements are described below in Figure 1.
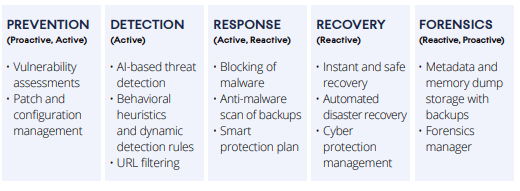
There are two important points to consider with this more comprehensive interpretation of a cyber resilience framework. First, when your customers recover from an attack, it is important that they do not retreat back into a vulnerable state. In this case, resilience does not mean returning to the state they previously were in, but rather to a state that makes the customer not vulnerable to the attack that had just occurred.
For example, if your customer is attacked because a patch was not applied and you subsequently recover their systems back to their original static state, they are still vulnerable because that patch has still not been applied. Instead, you want to apply the patch when recovering, which brings the customer’s systems to a new, dynamic state that is no longer vulnerable to such an attack.
Second, forensics is an essential component of the framework because it is not enough to just stop an attack and return to business as usual. Instead, you need to understand how the attack happened – because without that knowledge, you can’t determine what damage the attack has caused, if any. An attack can cause immediate or delayed damage, or it can be a precursor to future attacks. So, this knowledge is a critical ingredient for comprehensive cyber resilience.
Elements of Cyber Resilience
When it comes to implementation, the elements of cyber resilience must align with the “golden triangle”: technology, people and process.
Technology. Your customers need technology that:
- Provides the cyber protection they need for their data, applications and systems
- Is easy for people to use
- Integrates with your customers’ business processes
Next-generation, advanced cybersecurity technology can help block any email threat, including spam, phishing, business email compromise (BEC) and follow-on attacks, advanced persistent threats (APTs) and zero-day vulnerabilities before these threats reach end users.
People. All your clients’ employees must be trained to know what a cybersecurity attack looks like, what to do and what not to do. This training should be delivered on an ongoing basis since the cybersecurity landscape is changing so rapidly. People are not only the weakest link when it comes to security, but they are also the major source of danger. The wrong person in the wrong place – who doesn’t have the necessary skill set – can give you and your customers a false sense of security. A proper balance will have the right people at the right level in the right place.
Process. It is important that your customers have defined processes in place that address normal business operations and abnormal situations, such as an attack, unexpected downtime, data loss, etc. To implement these processes, you need a checklist that details the steps essential for supporting a normal business event, such as how to add a new server, employee, workstation, etc. to the network. These processes should also incorporate a cyber resilience component, so that changes do not introduce too much disruption and inadvertently bring your customers’ systems back to a vulnerable state.
Benefits of Cyber Resilience
The benefits of cyber resilience fall into three categories:
Strategic. If your clients’ organizations are cyber resilient, it is easy for them to implement new strategies and new systems, bring on more people and workloads, etc. Without cyber resilience, it is difficult and dangerous to implement new strategies.
Financial. If your clients’ organizations are resilient, removing or adding people/workloads/etc. – any changes your customers implement – should not drive up their costs or introduce dramatic risk.
Operational. Your clients are always changing their operations – adding/removing endpoints, employees, workflows, etc.; but cyber resilient organizations are more efficient and productive when it comes to implementing any changes that disturb the status quo. But without cyber resilience, an organization is not capable of safely implementing these operational changes.
Organizations looking to evaluate their operational and cybersecurity practices can consider a no-cost Cyber Resilience Review (CRR). This CRR may be conducted as either a self assessment or an onsite assessment facilitated by Department of Homeland Security (DHS) cybersecurity professionals.
Why is enterprise and business cyber resilience relevant in the Covid 19 era?
COVID has accelerated virtually everything – including the introduction of the remote/hybrid workspace and the growth and complexity of your clients’ IT infrastructures; but this same acceleration has also created severe IT talent shortages. According to the New York Times, there will be 3.5 million unfilled cybersecurity jobs globally by the end of 2021 – up from one million positions in 2014.
While a hybrid work model has made it possible for any organization to hire anyone working anywhere, small-to-medium-sized businesses (SMBs) struggle to hire IT professionals because they cannot compete with the big brand companies that have the budgets and benefits enabling them to scoop up the best talent.
Covid has also accelerated new types of threats that are impacting remote workers. With many employees working from home, it has become easier than ever to trick and attack users while at the same time, it’s becoming more difficult for IT to track what these users are doing. To make matters worse, cybercriminals are introducing new types of attacks, such as killware, which can cause physical harm and even death.
With more complex IT infrastructures, higher demand for IT talent and the introduction of new cyberthreats, organizations face significant challenges which can only be addressed with modern cyber protection software.
Cyber protection provides security for your systems, applications and data. It also provides resilience because automation and machine intelligence (MI) minimize the need for human interaction and maximize protection from data loss due to human error. A modern cyber protection solution is also integrated so there is only one license, one agent, one backend, one management console, one user interface, and one vendor support line – in short, one comprehensive set of tools.
If you are using a variety of tools that are not integrated, your level of resilience – and that of your customers – will remain low because you are forced to manage multiple tools, creating a situation that is consistently prone to human error and potential gaps in IT security.
Achieve cyber resilience with Acronis Cyber Protect Cloud
Acronis Cyber Protect Cloud is an all-in-one cyber protection solution that addresses all aspects of cyber resilience for your clients’ businesses. It is the only solution that natively integrates cybersecurity, data protection and management to protect endpoints, systems and data. This synergy eliminates complexity, so managed service providers (MSPs) can protect their customers better with one integrated solution that keeps your costs down. It provides:
- The industry’s best backup and recovery with full-image and file-level backup and recovery to safeguard workloads on more than 20 platforms – with near-zero RPOs and RTOs.
- Essential cyber protection at no additional cost with an advanced MI-based behavioral detection engine that stops malware, ransomware and zero-day attacks on your clients’ endpoints and systems.
- Protection management that is built for MSPs to enable thorough post-incident investigations and proper remediation, while keeping costs down by collecting digital evidence and storing it in a secure central repository.
The Acronis Cyber Protect Cloud also enables MSPs to expand their offerings with advanced protection packs. These include:
- Advanced Security — take advantage of integrated cyber protection that includes full-stack malware prevention. This solution extends the endpoint capabilities of the Acronis Cyber Protect Cloud, helping MSPs reduce the risk to clients with enhanced anti-malware protection and remediation services.
- Advanced Backup— this integrated approach to cyber protection enables MSPs to extend the cloud backup capabilities clients require to proactively manage their data.
- Advanced Disaster Recovery — now MSPs can get their clients back to business in just minutes and ensure immediate data availability after a disaster strikes. The Advanced Disaster Recovery add-on helps make disaster recovery painless and increases efficiency with orchestration, runbooks and automatic failover.
- Advanced Email Security — block any cyberthreat, including spam, phishing, business email compromise, advanced persistent threats and zero-day attacks — before they reach end users.
- Advanced Management — enable automated patch management and overall protection management. The Advanced Management add-on is the ideal way to keep clients’ systems up to date while simplifying protection management efforts.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




