21,000
partners
750,000
protected businesses
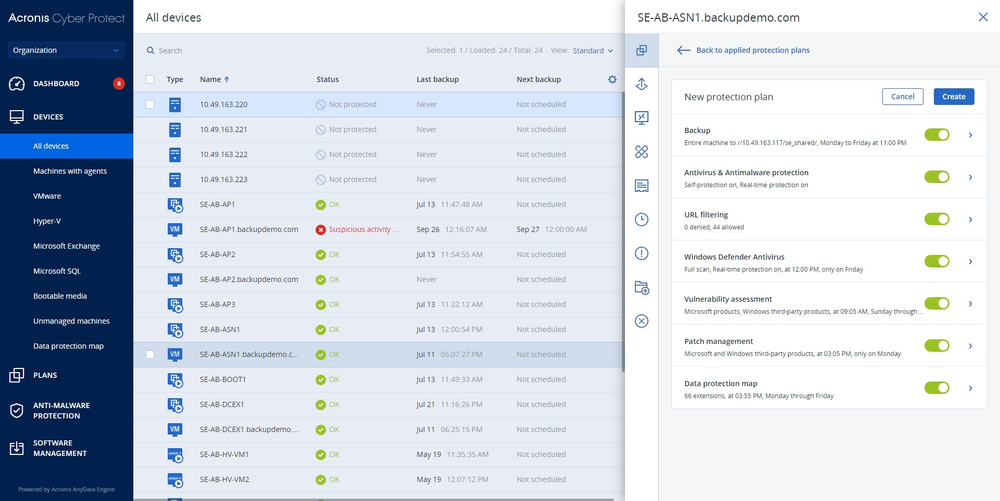
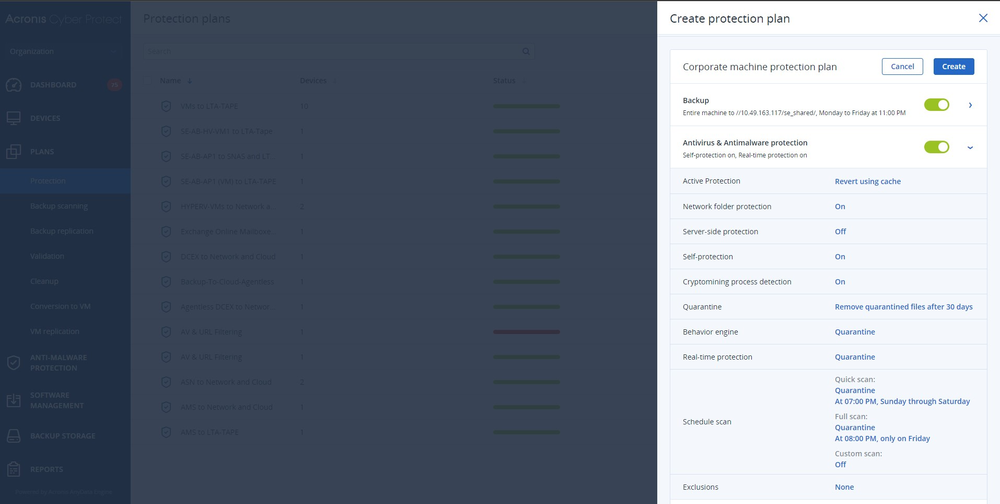
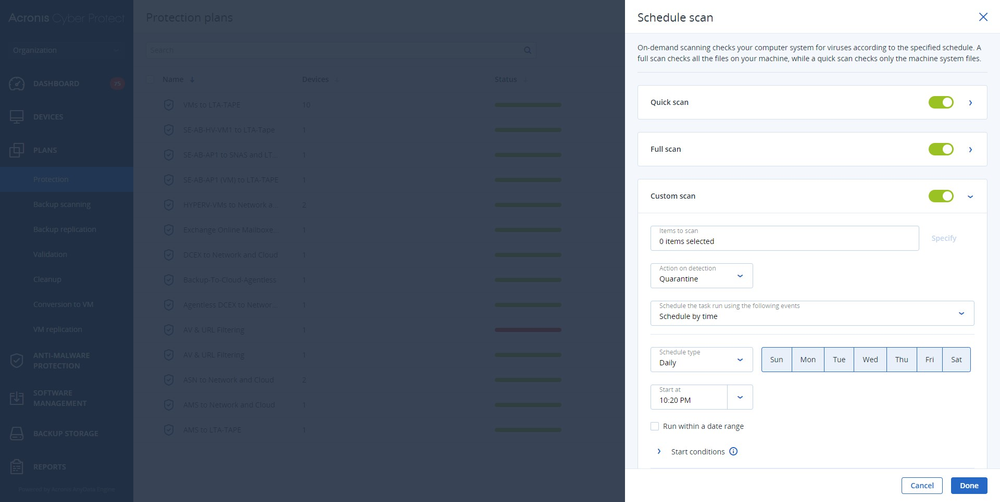
Unify ransomware defense and recovery
Acronis detects and neutralize new and advanced ransomware, providing powerful defense to safeguard valuable data and ensure business continuity.
- IDENTIFY
- Auto-discovery of new devices
- Vulnerability assessments
- Data protection map
- PROTECT
- Remote agent installation
- Backup and data protection
- Unified protection policies management
- DETECT
- Behavior-centric approach to detect unknown & advanced threats
- Defenses against malware and exploits
- Hard drive health control
- RESPOND
- Rapid incident prioritization & EDR telemetry for rich analysis
- Workload remediation with isolation
- Additional investigation via forensic backups and remote connections
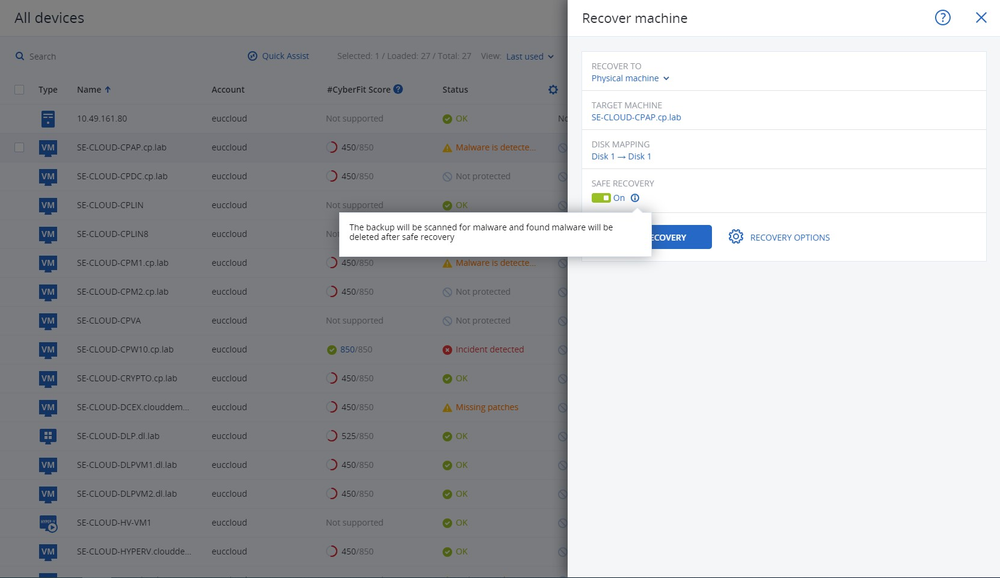
- RECOVER
- Pre-integrated backup and disaster recovery
- Rapid rollback of attacks
- Self-recovery & one-click mass recovery
- GOVERN
- Natively integrated cybersecurity, data protection, management
- Centralized policy management
- Single agent, management console, dashboard
Business
Acronis Cyber Protect
Service provider
Acronis Cyber Protect Cloud
| Users | Unlimited | Depends on service provider contract |
| Cybersecurity | ||
| Anti-ransomware protection with automatic rollback | | |
| Behavior-based detection | | |
| Endpoint Detection & Response (EDR) | | |
| Extended Detection & Response (XDR) | | |
| Data loss prevention (DLP) | | |
| Email Security | | |
| AI-guided incident analysis | | |
| GenAI Assistant: Acronis Copilot | | |
| Single-click response: contain, remediate, rollback, recover | | |
| MDR Service | | |
| Data Protection | ||
| File- and system-level backup and recovery | | |
| Automatic and manual attack rollback | | |
| Disaster Recovery (DR) | | |
| Flexible storage options: Cloud, on-prem, own, or third-party | | |
| Management | ||
| Deployment | On-premises or Cloud | Cloud |
| Centralized policy management for all services | | |
| Single agent, console, policy | | |
| Multi-tenancy | | |
| Role-based access | | |
| Pre-built integrations | | 200+ with most common tools: RMM, PSA, ticketing, billing, etc. |
| White-labeling | | |
| Ticketing | | |
What your peers are saying
Powered by industry-recognized, award-winning endpoint protection











Get answers to your questions
Frequently Asked Questions
What is Ransomware?
Ransomware is malicious software designed to infiltrate and compromise a victim's endpoints and servers, encrypting critical files and preventing access to those systems until a ransom is paid. The consequences of a successful ransomware attack can be severe. It can result in losing sensitive and valuable data, financial damage from operational disruptions, reputational harm, regulatory penalties and potential legal implications.
Acronis Cyber Protect offers robust protection against ransomware through its advanced security features, including real-time threat detection, AI-based behavioral analysis and proactive vulnerability assessments.
With Acronis, you can ensure data integrity and prevent potential damage caused by ransomware attacks. Additionally, it provides secure backup and recovery capabilities, allowing you to restore your systems and files in case of a successful attack.Can I recover from Ransomware?
To effectively prevent ransomware attacks, it is crucial to implement a multi-layered security approach that encompasses various proactive measures. Relying on a single security solution is no longer sufficient, given the evolving and sophisticated nature of ransomware threats.
Acronis Cyber Protect offers comprehensive protection measures. It combines AI-driven anti-malware, secure backup solutions, vulnerability assessments and patch management to identify and mitigate ransomware risks proactively.
Moreover, Acronis safeguards your systems, detects suspicious activities and provides secure backups that allow you to restore data without paying a ransom. By leveraging Acronis Cyber Protect, you can secure your defenses and minimize the chances of falling victim to ransomware attacks.Can ransomware steal data?
Yes, ransomware can steal data in addition to encrypting files. Some advanced ransomware strains have data exfiltration capabilities, enabling cybercriminals to steal sensitive information before encrypting it.
Acronis Cyber Protect not only prevents ransomware attacks but also provides comprehensive data protection. Its secure backup solutions create multiple copies of your data, which can be restored in the event of a ransomware attack, ensuring that your valuable information remains protected and inaccessible to unauthorized parties.How should companies handle ransomware?
Companies should proactively protect against ransomware by implementing a robust cybersecurity strategy. This includes using comprehensive security solutions like Acronis Cyber Protect, which offers real-time threat detection, continuous data backup and AI-based malware protection.
Companies should also conduct regular employee training on recognizing and avoiding phishing attempts and suspicious attachments. In case of a ransomware incident, companies should follow incident response protocols, isolate infected systems, notify law enforcement and leverage Acronis Cyber Protect's recovery capabilities to restore operations swiftly and securely.How to detect ransomware?
Detecting ransomware requires a combination of advanced security measures. Acronis Cyber Protect employs AI-driven behavioral analysis, heuristic detection and signature-based scanning to identify ransomware threats in real time. It continuously monitors system activities, network traffic, and file behavior to detect any anomalies or malicious patterns commonly associated with ransomware attacks.
By leveraging Acronis Cyber Protect's powerful detection capabilities, companies can quickly identify and respond to ransomware incidents, minimizing potential damage and ensuring data and system integrity.Why is cyber insurance important for businesses?
Cyber insurance has become a useful hedge for businesses against the financial and reputational damage caused by modern cyberthreats. With the increasing frequency and sophistication of cyberattacks, organizations face significant risks such as data breaches, ransomware attacks and business interruption. Cyber insurance provides financial protection by covering expenses related to incident response, legal fees, data recovery and even potential extortion payments. It helps businesses recover from financial losses and manage the costs of incident investigation, notification and customer remediation.
Moreover, cyber insurance offers coverage for third-party liability, safeguarding businesses from lawsuits arising from data breaches or privacy violations. By transferring the risk to an insurance provider, organizations can gain peace of mind, enhance their cyber risk management strategies and ensure business resilience in the face of cyberthreats.
Acronis provides protection against a broad range of such cyber threats, making it easier for businesses to qualify for cyber insurance in the face of newly strict standards imposed by issuers.What is the best protection against ransomware?
A growing number of MSPs continue to seek ways to consolidate their vendor lists to reduce costs, improve efficiency and achieve comprehensive protection. Not only does taking a multilayered approach help close security gaps, but also fortify resilience.
Acronis Cyber Protect Cloud is a comprehensive solution that combines cybersecurity, data protection and management, enabling MSPs to meet the unique needs of clients, including qualifying for cyber insurance, adhering to industry regulatory compliance and safeguarding business continuity — all at an affordable price. Acronis empowers you to centrally manage, provision, and scale cybersecurity, backups, recovery, and endpoint management through a single console, eliminating the need to manage multiple individual tools and saving valuable resources and time.What is the 3-2-1 rule for ransomware?
Adopting a 3-2-1 backup strategy is one of the most effective ways to safeguard data against security vulnerabilities. The 3-2-1 strategy ensures that organizations have three copies of sensitive data: your production data and two backups — one housed in a different geographical location and one copy housed off-site. By separately storing secure backups in both local and off-site locations, businesses reduce the risk of data loss regardless of the location or cause — including natural disasters, human error and cyberattacks.
For instance, if a fire destroyed one of the off-site backup locations, the data would be safe where it was backed up locally and in the remaining off-site location. This empowers your MSP business to quickly and easily restore the data to your clients and minimize downtime for their business.How can I build a ransomware incident response plan (IRP)?
Building a ransomware incident response plan is critical to streamlining and outlining how your MSP business will respond to ransomware if your clients are attacked. A comprehensive IRP involves ten fundamental steps to help minimize the financial, reputational and operational harm to you and your clients following an attack. This includes:- Defining security objectives.
- Establishing a designated incident response team.
- Developing an incident classification framework.
- Outlining how you will detect and identify ransomware threats.
- Containing and remediating the threat.
- Recovering data and restoring it.
- Implementing communication protocols.
- Ensuring legal compliance.
- Documenting and reporting the incident to necessary stakeholders.
- Training and educating your IR team, clients and their employees on your ransomware response plan.
- Documenting and reporting the incident to necessary stakeholders.
- Ensuring legal compliance.
- Implementing communication protocols.
- Recovering data and restoring it.
- Containing and remediating the threat.
- Outlining how you will detect and identify ransomware threats.
- Developing an incident classification framework.
- Establishing a designated incident response team.
- Defining security objectives.
What are some methods of prevention against ransomware for MSPs and their clients?
Ransomware prevention as an MSP business boils down to three core themes to better protect your clients: enhancing visibility, taking a zero-trust architecture approach and leveraging AI-based detection.
To learn more about preventing ransomware attacks, read: The Ultimate Guide to Ransomware Protection and RecoveryWhat are the three fundamental measures for fighting ransomware as an MSP?
Endpoint security is vital for businesses, especially as they grow and increase the number of devices connected to their network. To effectively secure your clients’ endpoints, endpoint detection and response (EDR) or endpoint protection platforms (EPPs) are essential to safeguarding IT environments. While EPP focuses on monitoring and managing devices, EDR goes a step further by emphasizing threat detection and response to mitigate cyber risk.
Regular patch management is crucial to address vulnerabilities and reduce the risk of attacks. Automated patch management can streamline this process and ensure compliance and system performance.
Additionally, data backup is essential to counter ransomware attacks — following the 3-2-1 rule of backup to maintain multiple copies of critical data on different storage media.What are the top ransomware protection strategies for MSPs?
As an MSP business, you can ensure your clients are holistically protected against ransomware through leveraging the NIST Cybersecurity Framework. The core functions of NIST include Identify, Detect, Protect, Respond and Recover.
The NIST Framework was designed to help organizations enhance their security posture. By ensuring protection layers to address each function, you can close security gaps, mitigate cyber risk and fortify business resilience to clients.
To learn more, explore the whitepaper, “Cyber Protection Across the NIST Framework for MSPs.”
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.