Defining firewall rules
When defining firewall rules, consider the following:
•When the Allow and Deny rules are applied in conjunction, all Allow rules override the Deny rules for both incoming and outgoing traffic.
•Protocol permissions take precedence over firewall rules, except for rules with the
Override Protocols Permissions option enabled, which block access regardless of those permissions.
Important: Rules with the
Override Protocols Permissions option enabled do not block access allowed by Protocols White List rules for the protocols Any and/or SSL. They also do not block access via protocols not
recognized in NetworkLock, provided that access is allowed by other firewall rules. |
•Some applications, for example, Windows built-in applications (such as Remote Desktop) use system processes to transfer data. To block such applications, you must create and apply a firewall rule to the account that is used by the application’s data transfer process.
•When users try to establish a connection to which they are denied access, they receive a Basic IP Firewall blocked message, if
Basic IP Firewall blocked message is enabled in
Service Options. For details on this message, see the
Basic IP Firewall blocked message parameter description in
Service Options.
•The communication between DeviceLock Service and DeviceLock Enterprise Server as well as between DeviceLock Service and DeviceLock Management Console is always allowed, regardless of firewall settings.
•The administrator can enable alerts to be sent upon triggering a particular firewall rule. Alerts are enabled when defining the rule.
DeviceLock sends alerts on the basis of alert settings. These settings specify where and how the alerts should be sent. Before enabling alerts for a firewall rule, DeviceLock Service alert settings must be configured (see
Alerts).
To define a firewall rule
1. If using DeviceLock Management Console, do the following:
a) Open DeviceLock Management Console and connect it to the computer running DeviceLock Service.
b) In the console tree, expand DeviceLock Service.
If using DeviceLock Service Settings Editor, do the following:
a) Open DeviceLock Service Settings Editor.
b) In the console tree, expand DeviceLock Service.
If using DeviceLock Group Policy Manager, do the following:
a) Open Group Policy Object Editor.
b) In the console tree, expand Computer Configuration, and then expand DeviceLock.
2. Expand Protocols.
3. Under Protocols, do one of the following:
•Right-click Basic IP Firewall, and then click Manage.
- OR -
•Select
Basic IP Firewall, and then click
Manage 
on the toolbar.
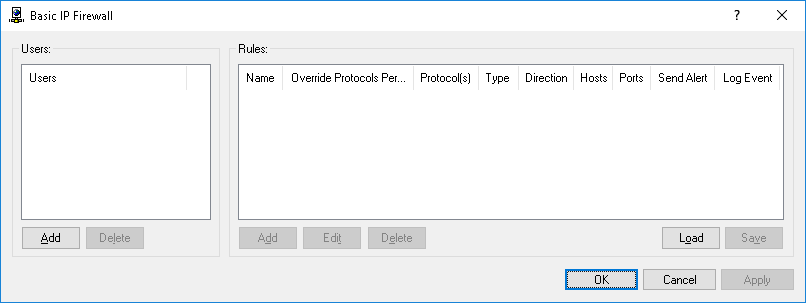
The Basic IP Firewall dialog box appears.
4. In the left pane of the Basic IP Firewall dialog box, under Users, click Add.
The Select Users or Groups dialog box appears.
5. In the Select Users or Groups dialog box, in the Enter the object names to select box, type the names of the users or groups for which you want to define the firewall rule, and then click OK.
The users and groups that you added are displayed under Users in the left pane of the Basic IP Firewall dialog box.
To delete a user or group, in the left pane of the Basic IP Firewall dialog box, under Users, select the user or group, and then click Delete.
6. In the left pane of the Basic IP Firewall dialog box, under Users, select the user or group.
You can select multiple users or groups by holding down the SHIFT key or the CTRL key while clicking them.
7. In the right pane of the Basic IP Firewall dialog box, under Rules, click Add.
The Add Rule dialog box appears.
8. In the Add Rule dialog box, specify the firewall rule parameters:
•To specify the rule name, in the Name box, type a name.
•To block access to the hosts specified by the
Hosts setting, select the
Override Protocols Permissions check box. For more information, see the
Override Protocols Permissions parameter description.
•To specify the protocol, under
Protocol, select the check box next to the protocol of your choice. For more information, see the
Protocol parameter description.
•To specify what actions the firewall takes for all connections that match the rule’s criteria, under
Type, click either of the following options:
Allow or
Deny. For more information, see the
Type parameter description.
•To specify the direction of traffic to which the rule applies, under
Direction, select the appropriate check box. For more information, see the
Direction parameter description.
•To specify additional actions to be performed when the rule triggers, under
If this rule triggers, select the appropriate check box. For more information, see the
If this rule triggers parameter description.
•To specify the remote hosts to which the rule applies, in the
Hosts box, type host names or IP addresses separated by a comma or semicolon. For more information, see the
Hosts parameter description.
•To specify the ports on remote hosts to which the rule applies, in the
Ports box, type port numbers separated by a comma or semicolon. For more information, see the
Ports parameter description.
9. Click OK.
The rule you created is displayed under Rules in the right pane of the Basic IP Firewall dialog box.
10. Click OK or Apply.
The users or groups to which the firewall rule applies are displayed under Basic IP Firewall in the console tree.
When you select a user or group to which a firewall rule applies in the console tree, in the details pane you can view detailed information regarding this rule (see
Firewall Rules for details).
 on the toolbar.
on the toolbar. on the toolbar.
on the toolbar. on the toolbar.
on the toolbar.