Defining offline Content-Aware Rules
Content-Aware Rules are created based on either the built-in or custom content groups. For detailed information on these groups, see
Configuring Content Groups.
You can enable offline alerts that are sent when a specific offline Content-Aware Rule fires. Such alerts are enabled immediately after setting up an offline Content-Aware Rule.
DeviceLock sends alerts on the basis of alert settings. These settings specify where and how the alerts should be sent. Before enabling alerts for a specific Content-Aware Rule, alert settings must be configured in DeviceLock Service options (see
Alerts).
To define an offline Content-Aware Rule
1. If using DeviceLock Management Console, do the following:
a) Open DeviceLock Management Console and connect it to the computer running DeviceLock Service.
b) In the console tree, expand DeviceLock Service.
If using DeviceLock Service Settings Editor, do the following:
a) Open DeviceLock Service Settings Editor.
b) In the console tree, expand DeviceLock Service.
If using DeviceLock Group Policy Manager, do the following:
a) Open Group Policy Object Editor.
b) In the console tree, expand Computer Configuration, and then expand DeviceLock.
2. Expand Protocols.
3. Under Protocols, do one of the following:
•Right-click Content-Aware Rules, and then click Manage Offline.
- OR -
•Select
Content-Aware Rules, and then click
Manage Offline 
on the toolbar.
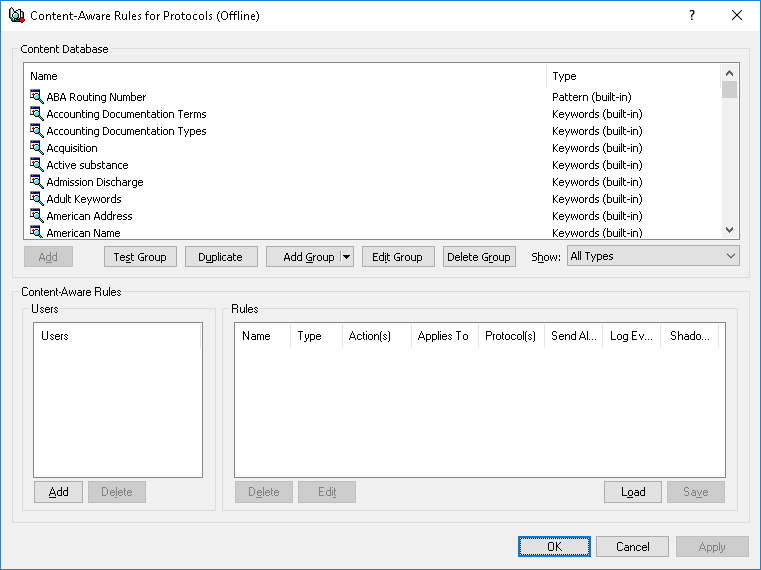
The Content-Aware Rules for Protocols (Offline) dialog box appears.
4. In the lower-left pane of the Content-Aware Rules for Protocols (Offline) dialog box, under Users, click Add.
The Select Users or Groups dialog box appears.
5. In the Select Users or Groups dialog box, in the Enter the object names to select box, type the names of the users or groups for which you want to define the rule, and then click OK.
The users and groups that you added are displayed under Users in the lower-left pane of the Content-Aware Rules for Protocols (Offline) dialog box.
To delete a user or group, in the lower-left pane of the Content-Aware Rules for Protocols (Offline) dialog box, under Users, select the user or group, and then click Delete or press the DELETE key.
6. In the lower-left pane of the Content-Aware Rules for Protocols (Offline) dialog box, under Users, select the users or groups for which you want to define the rule.
You can select multiple users or groups by holding down the SHIFT key or the CTRL key while clicking them.
7. In the upper pane of the Content-Aware Rules for Protocols (Offline) dialog box, under Content Database, select the desired content group, and then click Add, or double-click the desired content group.
Note: You can specify only one content group for a Content-Aware Rule. |
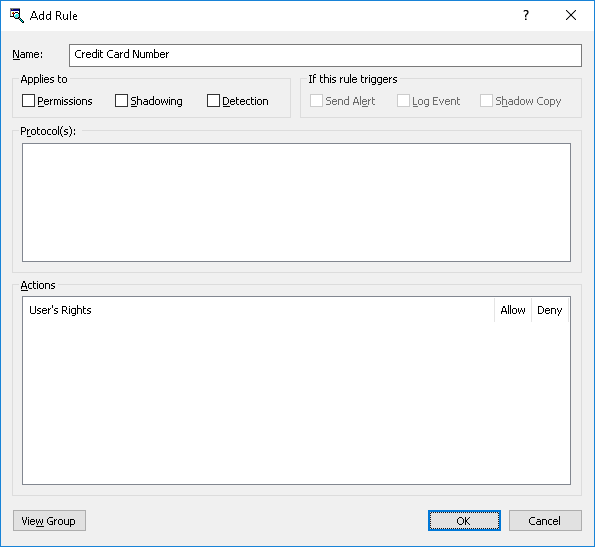
The Add Rule dialog box appears.
8. In the Add Rule dialog box, in the Name box, type the name of the Content-Aware Rule.
By default, the rule has the same name as its content group. The name of the rule can be changed if needed.
To view this rule’s content group, click the View Group button in the bottom left corner of the dialog box. The console displays the properties of the group in a separate dialog box, allowing property values to be viewed but not modified.
9. Under Applies to, specify the type of operation associated with the rule. The available options are:
•Permissions - Specifies that the rule will apply to access control operations.
•Shadowing - Specifies that the rule will apply to shadow copy operations.
•Detection - Specifies that the rule will apply to detection operations.
•Permissions, Shadowing - Specifies that the rule will apply to both access control and shadow copy operations.
•Permissions, Detection - Specifies that the rule will apply to both access control and detection operations.
•Shadowing, Detection - Specifies that the rule will apply to both shadow copy and detection operations.
•Permissions, Shadowing, Detection - Specifies that the rule will apply to all available operations: access control, shadow copy, and detection.
Note: To successfully create/save a rule that applies either to detection operations only or to detection operations combined with other operations, at least one of the following options must be selected for this rule: Log Event, Send Alert or Shadow Copy (see step 10 of this procedure). Otherwise, the rule cannot be saved and the following message appears: “Log Event, Send Alert or Shadow Copy should be specified.” |
10. Under If this rule triggers, specify the following additional actions to be performed when the rule triggers:
•Send Alert - Specifies that an alert is sent whenever the rule triggers.
•Log Event - Specifies that an event is logged in the Audit Log whenever the rule triggers.
•Shadow Copy - Specifies that a shadow copy of data is created whenever the rule triggers.
When alerts, audit and/or shadowing are enabled or disabled in a Content-Aware Rule, the rule setting takes precedence over the respective setting for the protocol.
Example: If audit is enabled for a particular protocol and disabled in a rule for that protocol, the triggering of the rule does not cause audit events. If audit is enabled in the rule, then the triggering of the rule causes audit events, even if audit is disabled at the protocol level.
The rule can also inherit the alert, audit and/or shadowing setting from the protocol level. This is the default option, represented by the indeterminate state of the check boxes (neither checked nor cleared). The state of each check box can be changed individually.
Example: When a rule inherits the audit setting from the protocol level, the triggering of the rule causes audit events only if audit is enabled for the protocol controlled by that rule.
11. Under Protocol(s), select the appropriate protocol(s) you would like this rule to be applied to.
Content-Aware Rules can be applied to the following protocols: Career Search, File Sharing, FTP, HTTP, IBM Notes, ICQ Messenger, IRC, Jabber, Mail.Ru Agent, MAPI, Skype, SMB, SMTP, Social Networks, Telegram, Viber, Web Mail, Web Search, WharsApp, and Zoom.
Under Action(s), if you multi-select protocols that have different combinations of configurable access rights, the dialog box will display the superset of access rights for the selection list: those that are common to all selected protocols, and those that do not necessarily apply to all protocols. As would be expected, if a particular access right that is displayed is not common to one or more particular selected protocols, it’s setting will not/cannot be applied to those protocols and will only apply to protocols where the setting is supported.
12. Under Action(s), specify which user actions are allowed or disallowed on protocols, which user actions are logged to the Shadow Log, and which user actions are detected.
If the rule applies to shadow copy operations combined with other operations, the Read user right becomes unavailable. If the rule applies to detection operations combined with other operations, only Allow action becomes available. For detailed information on user rights and actions that can be specified in Content-Aware Rules, see
Access Control,
Content-Aware Shadowing and
Content-Aware Detection for protocols.
13. Click OK.
The rule you created is displayed under Rules in the lower-right pane of the Content-Aware Rules for Protocols (Offline) dialog box.
14. Click OK or Apply to apply the rule.
The users or groups to which the Content-Aware Rule applies are displayed under Content-Aware Rules in the console tree.
When you select a user or group to which a Content-Aware Rule applies in the console tree, in the details pane you can view detailed information regarding this rule (see
List of Content-Aware Rules for Protocols).
You can define different online vs. offline Content-Aware Rules for the same user or sets of users. For information about how to define online Content-Aware Rules for protocols, see
Managing Content-Aware Rules.
 on the toolbar.
on the toolbar. on the toolbar.
on the toolbar. on the toolbar.
on the toolbar.