Overview
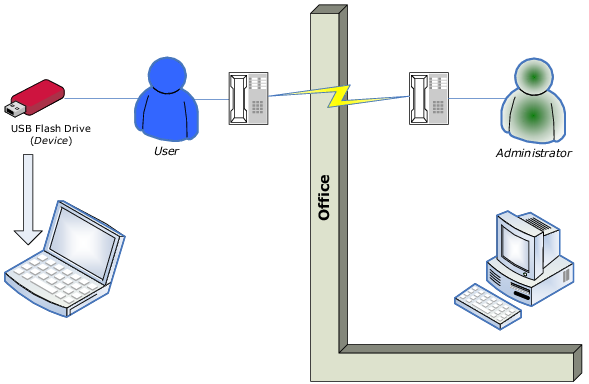
The DeviceLock Temporary White List function enables the granting of temporary access to USB devices when there is no network connection. Administrators provide users with special access codes over the phone that temporarily unlock access to requested devices. The following diagram illustrates the process of granting temporary access to USB devices.
A Temporary White List works like a device white list (see
USB Devices White List (Regular Profile)), with the distinction that a network connection is not required to add devices and grant access to them.
Note: Using Temporary White List it is possible to grant access to USB devices that were blocked on both levels: the USB port level and the type level. If some white listed device (for example, USB Flash Drive) belongs to both levels: USB and type (Removable), the permissions (if any) for the type level are ignored as well as for the USB level. |
Creating and activating a Temporary White List is a matter of following these step-by-step instructions:
1. The administrator generates a cryptographic certificate (DeviceLock Certificate) using the Certificate Generation Tool (see
Generating DeviceLock Certificates). A DeviceLock Certificate consists of two keys: private and public.
2. The administrator deploys the DeviceLock Certificate (the public key) to a user’s computer. This enables the Temporary White List on the user’s computer.
3. When a user needs to access some USB device, they run the
Temporary White List Authorization Tool from the Windows Control Panel. Then, the user selects the particular device from a list and generates an alpha-numeric code (Device Code). The user provide that code to the DeviceLock Administrator (for example, over a phone or via an Internet chat session).
4. The administrator then runs the
DeviceLock Signing Tool, loads the respective DeviceLock Certificate (the private key), enters the Device Code, selects an appropriate temporary access period (5, 15, etc. minutes, until the device is unplugged or until the user is logged off), generates an Unlock Code, and relays that Unlock Code to the user.