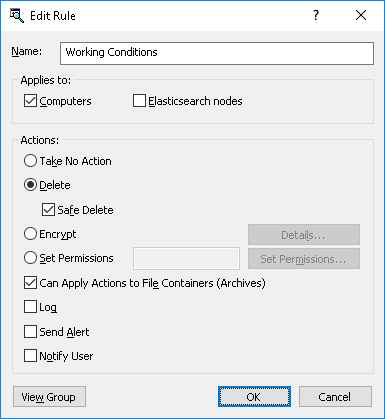
Using the “Edit Rule” dialog box
When having detected any content that matches a given rule, DeviceLock performs the action specified by that rule. Use the Edit Rule dialog box to view or change the action of a particular rule:
1. Open the DeviceLock Management Console, and then, in the console tree, select DeviceLock Content Security Server > Discovery Server > Rules & Actions.
2. In the details pane, right-click the rule, and then click Edit Rule on the shortcut menu to open the Edit Rule dialog box:
3. Use the following settings provided in the Edit Rule dialog box:
•Name - View or change the name of the rule.
By default, the rule has the same name as its content group. The name of the rule can be changed if needed.
To view this rule’s content group, click the View Group button in the bottom left corner of the dialog box. The console displays the properties of the group in a separate dialog box, allowing property values to be viewed but not modified.
•Applies to - Choose the unit type/s for which this rule can be used in discovery tasks:
•Computers - The rule can be used to discover files on computers or servers.
•Elasticsearch nodes - The rule can be used to discover documents in Elasticsearch.
Note: Rules that apply to Elasticsearch nodes can only log events and send alerts. Other actions are not available in this case. |
•Take No Action - Select to leave the detected content intact. This option should be used when configuring the rule to log a discovery event, alert or notify about the discovery.
•Delete - Select to delete the detected content. The following option is available:
•Safe Delete - Deletes the detected content using a secure erase procedure as defined in US DoD 5220.22-M.
•Encrypt - Select to encrypt the detected content using Windows EFS (Encrypted File System). To enable this action, you have to configure file encryption as follows:
a) Select the Encrypt option, and then click the Details button.
b) In the Encryption Details dialog box that appears, click Add.
c) In the dialog box that appears, select a certificate from the list of available encryption certificates.
Note: The list of available encryption certificates corresponds to the list of Personal Certificates of the user under whose account the management console is launched. You can view Personal Certificates in the Certificates console. For details, see Microsoft’s article at
technet.microsoft.com/library/cc512680.aspx. During the encryption, a Recovery Agent EFS certificate is added. |
Encryption does not function when using a remote file system in agentless scanning or when SMB resource scanning is performed. This limitation is specific to EFS and not to DeviceLock Discovery.
Note: If a file matches multiple rules with the Encrypt action, it will be encrypted with all certificates specified in all matching rules. |
•Set Permissions - Select to set file access permissions on the detected content. Click the Set Permissions button to open the standard file permissions dialog provided by the operating system.
Note: If a file matches multiple rules with the Set Permissions action, the resulting permission settings on the file will be determined by joining all access control lists (ACL) from all matching rules. |
Permission conflict resolving: If a file matches multiple rules that specify mutually exclusive permissions, the resulting ACL on that file will be configured by setting individual access parameters. For example, suppose a given file matches two rules, one of which specifies Allow Full Control while the other one specifies Deny Write for the same user. In this case, the resulting ACL will be as follows: Allow Read, Read & Execute; Deny: Write.
If the different rules specify different users or user groups, any access control rights specified by these rules are joined together, and the resulting ACL is determined by Windows.
•Can Apply Actions to File Containers (Archives) - Select to allow applying an action (Delete, Set Permissions, Encrypt) to the entire compressed archive (such as a ZIP or RAR file) in which the matching content was discovered. If this option is not selected, the action will not be applied to the container.
Note: This option also affects saved emails (EML), Adobe Portable Document Format (PDF) files, Rich Text Format (RTF), AutoCAD files (.dwg, .dxf), and Microsoft Office documents (.doc, .xls, .ppt, .vsd, .docx, .xlsx, .pptx, .vsdx). |
•Log - Select to have the rule record a discovery event to the tasks Log (see
Tasks Log Viewer).
•Send Alert - Select to have the rule alert the administrator about the detected content.
•Notify User - Select to have the rule notify the user with a message displayed in the system tray.
Note: User notification is not available in Agentless mode. |