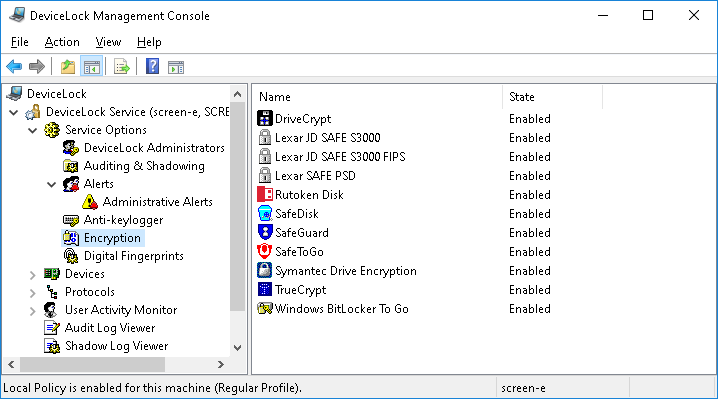
Encryption
DeviceLock Service can recognize disks (USB-drives and other removable devices) that store data in an encrypted form, and apply so-called “encrypted” permissions for such disks (see
“Encrypted” Rights Category). This feature makes it possible to prevent sensitive data from being written to media that does not provide encryption.
The encryption products and technologies that DeviceLock supports are listed in the details pane when
DeviceLock Service >
Service Options >
Encryption is selected in the console tree:
The list in the details pane provides the following information:
•Name - The name of the data encryption product or technology.
•State - Indicates whether integration is enabled for the given product or technology:
•Enabled - “Encrypted” permissions can be applied.
•Disabled - “Encrypted” permissions have no effect.
To enable or disable integration, right-click in the list and then choose the
Enable or
Disable command. To set the state of Not Configured, use the
Undefine command in the
DeviceLock Service Settings Editor and
DeviceLock Group Policy Manager.
Data Encryption Products and Technologies
As of this time DeviceLock provides integration with the following third-party products and technologies used for encrypting data on removable storage devices:
Note: DeviceLock does not ship with third-party encryption products and does not require them for its own functioning. The integration of DeviceLock with a third-party encryption product will only work when the third-party product is properly installed, configured, and functioning on the computer running DeviceLock Service. |
If you do not want DeviceLock Service to apply “encrypted” permissions to devices encrypted by a particular product or technology listed above, disable integration by using the
Disable command on the respective name in the details pane (see
Encryption).
For more information on “encrypted” permissions, refer to the following sections of this manual:
DriveCrypt
DeviceLock Service can detect DriveCrypt Plus Pack (DCPP) encrypted removable storage devices and apply “encrypted” permissions to them when the DriveCrypt Plus Pack product is installed on the computer running DeviceLock Service with integration enabled for DriveCrypt.
For details on DriveCrypt Plus Pack, refer to the Web site at
www.securstar.biz.
Lexar JD SAFE S3000, Lexar JD SAFE S3000 FIPS
DeviceLock Service can detect Lexar™ SAFE S3000 and/or SAFE S3000 FIPS USB flash drives and apply “encrypted” permissions to them if it has integration enabled for Lexar JD SAFE S3000 and/or Lexar JD SAFE S3000, respectively.
For details on Lexar SAFE S3000 and SAFE S3000 FIPS, refer to the “USB Flash Drive” section on Lexar’s Web site page at
www.lexar.com/support/frequently-asked-questions.
Lexar SAFE PSD
DeviceLock Service can detect Lexar™ SAFE PSD S1100 USB flash drives and apply “encrypted” permissions to them if it has integration enabled for Lexar SAFE PSD.
Rutoken Disk
DeviceLock Service can detect Rutoken encrypted USB flash drives and apply “encrypted” permissions to them if it has integration enabled for Rutoken Disk.
For details on the Rutoken technology, see
www.rutoken.ru (in Russian).
SafeDisk
DeviceLock Service can detect SafeDisk encrypted containers on USB flash drives and other removable media and apply “encrypted” permissions to them if it has integration enabled for SafeDisk.
For details on ViPNet Safe Disk, refer to the Web site at
infotecs.biz.
Note: To access SafeDisk containers and work with their contents, users should have at least read access to unencrypted Removable devices. |
SafeGuard
DeviceLock Service can detect Sophos SafeGuard Easy encrypted USB flash drives and other removable media and apply “encrypted” permissions to them if it has integration enabled for SafeGuard.
For details on Sophos SafeGuard Easy, refer to the Sophos Web site at
www.sophos.com/products/safeguard-encryption.aspx.
SafeToGo
DeviceLock Service can detect SafeToGo™ encrypted USB flash drives and apply “encrypted” permissions to them if it has integration enabled for SafeToGo.
For details on SafeToGo™, refer to the Web site at
safetogo.eu.
Symantec Drive Encryption (formerly PGP Whole Disk Encryption)
DeviceLock Service can detect removable storage devices encrypted by Symantec Drive Encryption and apply “encrypted” permissions to them when the Symantec Drive Encryption product is installed on the computer running DeviceLock Service with integration enabled for Symantec Drive Encryption.
For details on Symantec Drive Encryption, refer to
support.symantec.com/en_US/drive-encryption.html. For instructions on how to install and use PGP® Whole Disk Encryption with DeviceLock, see the
PGP/DeviceLock Integration Guide created by PGP.
TrueCrypt
DeviceLock Service can detect removable storage devices encrypted by TrueCrypt and apply “encrypted” permissions to them when the TrueCrypt product is installed on the computer running DeviceLock Service with integration enabled for TrueCrypt.
For details on TrueCrypt, refer to the Web site at
www.truecrypt.org.
Note: If the TrueCrypt volume type is “File-hosted (container)”, then, to access that container and work with its content, users should have at least read access to unencrypted Removable devices. |
Windows BitLocker To Go
DeviceLock Service can detect BitLocker To Go encrypted drives and apply “encrypted” permissions to them if it has integration enabled for Windows BitLocker To Go.
For details on the BitLocker Drive Encryption technology included in Windows 7 and later versions of Windwos, see Microsoft’s documentation at
go.microsoft.com/fwlink/?linkid=76553.
Note: If integration with Windows BitLocker To Go is enabled, the “Deny write access to removable drives not protected by BitLocker” Group Policy setting cannot be enabled. (This setting is located in Computer Configuration\ Administrative Templates\Windows Components\BitLocker Drive Encryption\Removable Data Drives.) |
Mac OS X FileVault
DeviceLock Service for Mac can detect FileVault encrypted external drives and apply “encrypted” permissions to them if it has integration enabled for Mac OS X FileVault. Integration with FileVault is not supported on the Windows operating system, so the Mac OS X FileVault item does not appear on the Encryption list in the details pane if the console is connected to a Windows-based computer.
For details on FileVault, refer to the Apple Web site at
support.apple.com/HT204837.