
The Purdue Reference Model for operational technology (OT) and industrial control system (ICS) security is a crucial framework widely used today — even in the face of new technological advancements.
However, the rapid evolution of technology and the increasing sophistication of cyberthreats have raised questions about whether the model can address modern security challenges.
Does the Purdue Model need some tweaks as manufacturers embrace new technologies? The answer is yes. But what exactly do manufacturers need to do?
The Purdue Model meets modern IT systems
The Purdue Model has lasted as long as it has because it breaks complex manufacturing systems down into manageable components. By segmenting systems, the model ensures that manufacturers can continue critical operations even when other systems, such as IT operations within the larger organization, are compromised. But as new manufacturing technologies have emerged, the Purdue Model has begun showing its age.
Developed in the 1990s, the Purdue Model came to prominence at a time when OT and IT systems were rarely interconnected. Today, OT and IT are frequently linked as more companies in manufacturing and industry move to take advantage of new technologies like industrial internet of things (IIoT) devices and cloud-based analytics of real-time production data.
The connection of the two types of systems has blurred the lines between them. As a result, manufacturers have struggled to adhere to the model. Designed almost entirely for OT, the Purdue Model is too rigid and hierarchical to work well with most combined OT-IT systems.

The Purdue Model is still relevant, but highly connected systems are open to new threats
The Purdue Model is still holding onto relevance as a logical and functional framework for designing and securing automation and control systems. The model breaks down industrial environments into a hierarchical structure. This enables manufacturers to ensure network segmentation and security measures and thus more tightly control how different system components interact with each other.
The practice of air gapping, or isolation from the enterprise LAN and external networks like the internet, is designed to minimize the risk of cyberthreats that might lead to a costly outage of real-time production systems like Supervisory Control and Data Acquisition (SCADA) servers and human-machine interfaces to lower-level automation technology.
Despite the advent of new standards like Industry 4.0 (also known as the Fourth Industrial Revolution) and the closely related Manufacturing 4.0, with their increased use of edge and cloud computing, some principles of the Purdue Model remain important to manufacturing and industry. However, the increasing integration of OT and IT is changing how manufacturers apply the model. The discrete levels that the Purdue Model defines — notably the boundaries between Levels 3 through 5: the operations control, OT and IT DMZ, and enterprise network levels — are becoming less distinct and more porous.
Along those same lines, cloud computing has enabled manufacturers to move complex computational tasks and data storage to remote computing resources (physical, virtual and cloud-based) that are managed outside the OT environment. This move has increased the scalability, flexibility and cost effectiveness of processing massive amounts of real-time processing telemetry, but it has also intertwined the security and reliability of OT systems with those of IT systems. That OT and IT integration exposes industrial systems to a much broader range of cyberthreats.
Manufacturers need to adapt the Purdue Model for changing technologies
Manufacturers need to adapt the Purdue Model to address new security challenges. The model can be surprisingly flexible. That’s because it’s not a physical hierarchy but rather a logical or functional one. The physical placement of components can change, but the functional roles and responsibilities defined by the levels of the Purdue Model remain largely the same.
Integrating edge and cloud computing into the Purdue Model can work …
For instance, manufacturers can integrate edge computing into the model by treating edge devices as part of the model’s lower levels. Similarly, they can adapt the model to accommodate cloud computing by extending its upper levels to include cloud-based services and applications.
With those adaptations, edge and cloud computing can provide enhanced data processing, storage and analytics capabilities, while maintaining the separation of components that the Purdue Model emphasizes.
… but not without challenges
But adapting the model for edge and cloud computing introduces new challenges, such as ensuring secure and reliable communication between on-premises systems and the cloud, managing data latency and addressing the potential for increased attack surfaces.
The dynamic nature of cloud environments can complicate security and compliance management because cloud configurations and services can change rapidly and frequently. As a result, manufacturers need to implement robust security measures, including encryption, secure communication protocols, continuous monitoring and more robust endpoint security measures like EDR.
They also need to establish clear policies and procedures for data management and access and maintain a balance between the benefits of cloud and edge computing and the need for operational resilience and security.
A zero trust model for access, authentication and authorization for OT resources is one popular approach, though it must be adapted to fit the limitation of OT systems. For example, many OT systems run on very old versions of Windows that may not support modern cybersecurity agents, which may require proxied security and fine-grained network segmentation to provide comparable security.
How Acronis Cyber Protect for OT works with the Purdue Model
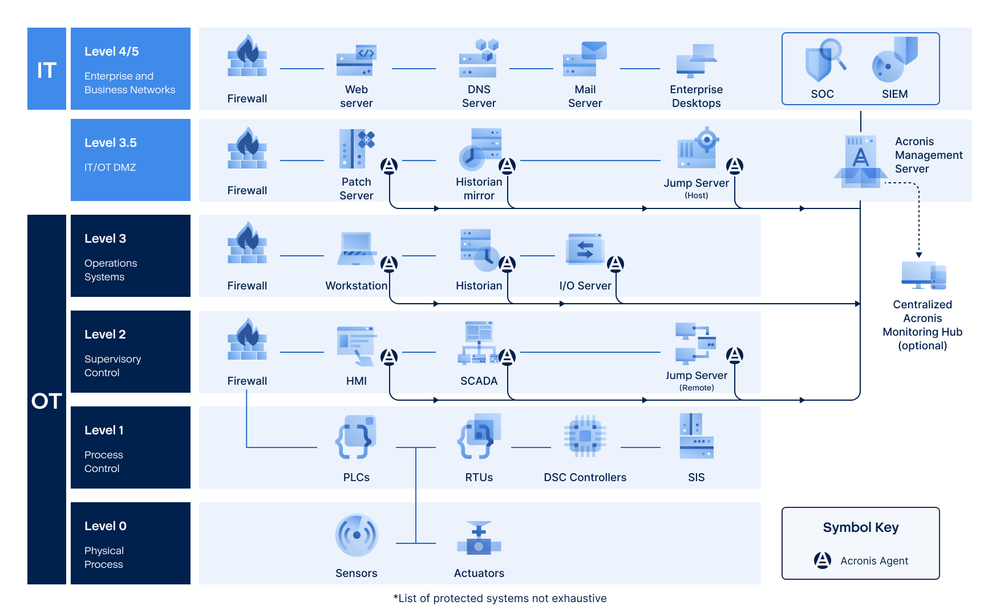
Manufacturers need a solution that can protect integrated OT and IT environments without requiring the abandonment of or radical changes to the Purdue Model. They need a way to adapt the model to modern interconnected environments.
Acronis Cyber Protect for Operational Technology delivers what manufacturers need. The solution integrates seamlessly with the Purdue Model, but also provides robust protection and management capabilities for integrated environments. Critical capabilities include:
Secure functioning between IT and OT in Purdue Model layers
The Acronis Management Server and Centralized Acronis Monitoring Hub ensures secure communication and management between IT and OT environments. At Levels 2, 3 and 3.5 of the Purdue Model, the Acronis Agent can be deployed on OT systems like Historians, SCADA servers, and human-machine (HMI) devices, giving manufacturers the ability to perform backup and recovery in integrated OT and IT environments. The agent can optionally deliver cybersecurity features like anti-ransomware protection that can greatly reduce and mitigate cyberthreats to OT systems.
In more converged OT/IT environments, the Acronis Agent can also be installed on systems throughout the Enterprise and Business Network Level of the Purdue Model, providing integrated cybersecurity and secure backup to front-office, back-office and general productivity applications.
Centralized management in a single console
Protecting both OT and IT systems with Acronis Cyber Protect for OT enables IT to monitor and manage backup and security operations from a single console. Management from a single point of view simplifies the management process and enables manufacturers to increase overall efficiency, effectiveness and integration of their IT and OT teams.
A unified view of the network gives administrators the ability to quickly identify and rectify issues and enables them to ensure that both IT and OT systems remain secure and operational. In a multitenancy deployment model, IT and OT teams, which are often separate within manufacturers’ operations, can continue to operate separately. Acronis Cyber Protect for Operational Technology still provides the organization as a whole with a unified view of backup and security operations.
Acronis Cyber Protect enables manufacturers to adapt the Purdue Model
Acronis Cyber Protect for OT offers capabilities that enable manufacturers to adapt the Purdue Model to cloud technologies and other advances that are bringing OT and IT together. With this solution, manufacturers can enhance efficiency and ensure secure integration of OT and IT systems.

About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



