Acronis Cyber Protect excels in remote endpoint monitoring and management, particularly for enterprises with IT-OT convergence, through several key functionalities:
1. Centralized Oversight: Provides a centralized dashboard for monitoring and managing all endpoints, including both IT and OT devices, offering a unified view of the security status across the enterprise.
2. Active Monitoring: Continuously tracks the health and security status of each endpoint, detecting anomalies that may indicate cyber threats or system failures, crucial for operational technology components.
3. Automated Alerts: Configurable alerts notify IT teams of issues in real-time, allowing for immediate action to protect sensitive operational systems and mitigate risks.
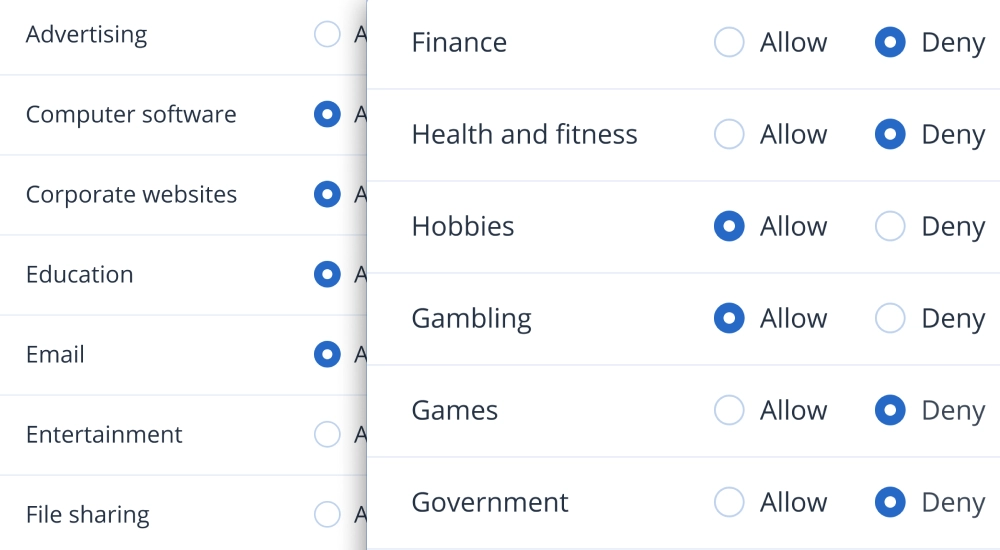
4. Policy Enforcement: Enforces security policies across diverse endpoints, ensuring that both IT systems and operational technologies like SCADA systems, PLCs, and other industrial control systems adhere to the same high security standards.
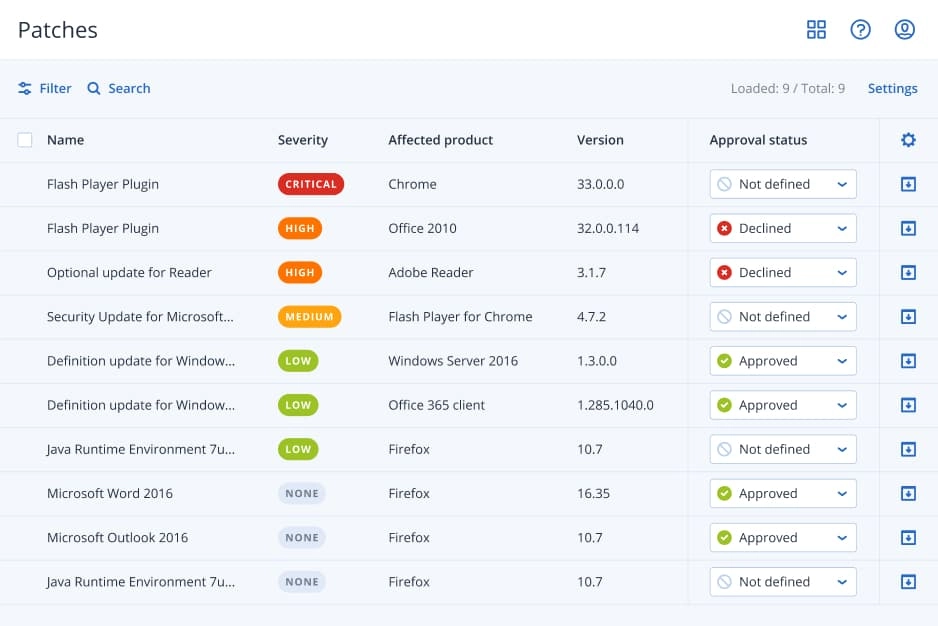
5. Patch Management: Manages and deploys patches remotely, addressing vulnerabilities swiftly and ensuring that both traditional IT environments and specialized OT equipment are up to date with the latest security patches.
6. Remote Assistance: Facilitates remote support and assistance for any endpoint within the network, which is particularly beneficial for troubleshooting and maintaining OT devices that are often distributed across various locations.
7. Scalability: The system is designed to scale with the enterprise, managing a growing number of endpoints without compromising performance or control.
8. Integration with Existing Systems: Seamlessly integrates with existing management systems and processes, providing enhanced visibility and control without disrupting current operations.
By focusing on these aspects, Acronis Cyber Protect ensures that enterprises with complex IT-OT environments can effectively monitor, manage, and protect their endpoints from a single platform, reducing complexity and enhancing operational efficiency.