Acronis cieszy się zaufaniem
- Najbezpieczniejsze tworzenie kopii zapasowych i odzyskiwanie danych po awariiZwiększ odporność firmy dzięki bezpiecznemu, niezmiennemu tworzeniu kopii zapasowych, błyskawicznemu odzyskiwaniu danych, zautomatyzowanemu, szybkiemu przełączaniu awaryjnemu i technologiom chroniącym przed oprogramowaniem ransomware.
- Kompleksowe możliwości w zakresie bezpieczeństwaZapewnij sobie spokój ducha i pomóż uniknąć kosztownych przestojów dzięki zintegrowanemu wykrywaniu i odpowiedzi urządzeń końcowych (EDR) oraz zautomatyzowanemu filtrowaniu adresów URL.
- Efektywne zarządzanie punktami końcowymi i automatyzacjaZminimalizuj przestoje i zwiększ czas pracy z automatycznym wykrywaniem anomalii, proaktywnym łataniem, zautomatyzowanymi skryptami i zdalnym dostępem do rozwiązywania problemów.
Proste, wydajne i bezpieczne tworzenie kopii zapasowych z szybkim odzyskiwaniem danych
Scentralizowane zarządzanie cyberbezpieczeństwem, kopiami zapasowymi, DR i punktami końcowymi
Zaawansowana cyberochrona dla każdego urządzenia końcowego w dowolnej lokalizacji - dzięki czemu idealnie nadaje się do dzisiejszych mobilnych i zdalnych środowisk pracy.

- Ciągłość biznesowa z odzyskiwaniem danych po awarii w chmurze
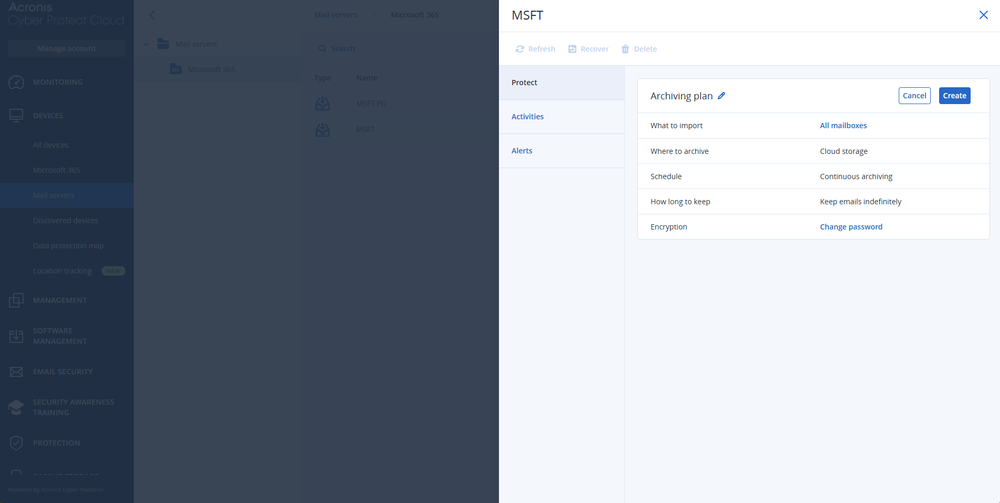
- Tworzenie kopii zapasowych w chmurze Microsoft 365 z nieograniczoną przestrzenią dyskową w chmurze
- Proaktywna ochrona rozszerzona o wykrywanie i reagowanie w urządzeniach końcowych
Zaawansowanym atakom można przeciwdziałać tylko za pomocą zaawansowanej ochrony.
- ProaktywnaOceny podatności, zarządzanie poprawkami, monitorowanie stanu bezpieczeństwa, wyszukiwanie zagrożeń, usuwanie złośliwego oprogramowania z kopii zapasowych i automatyczna ochrona nowych urządzeń.
- AktywnyCiągła ochrona danych, ochrona przed zagrożeniami w czasie rzeczywistym oraz oparte na uczenie maszynowym monitorowanie obciążeń w celu wykrywania problemów, zanim spowodują one przestoje.
- ReaktywnaSzybka reakcja na incydenty bezpieczeństwa i odzyskiwanie danych dzięki wycofywaniu ataków, zintegrowane odzyskiwanie danych po awarii i dodatkowe funkcje dochodzeniowe, takie jak kopie zapasowe kryminalistyczne i bezpieczny dostęp do pulpitu zdalnego.
Acronis Cyber Protect Cloud
Uzyskaj ochronę przed cyberzagrożeniami jako usługę zarządzaną przez partnera Acronis

Zobacz AcronisCyber Protect w akcji
Dowiedz się, jak zintegrowana ochrona cybernetyczna zmniejsza złożoność, zapewnia lepszą ochronę przed dzisiejszymi cyberzagrożeniami i maksymalizuje wydajność, oszczędzając czas i pieniądze.
Kompleksowa ochrona przed nowoczesnymi zagrożeniami
Wykrywanie i reagowanie w punktach końcowych
Zaawansowane i niezależne wykrywanie zagrożeń wraz ze świadomym badaniem zagrożeń i reagowaniem na nie.Ochrona przed złośliwym oprogramowaniem i program antywirusowy
Proaktywnie chroń swoje dane, aplikacje i systemy przed zaawansowanymi cyberatakami dzięki ochronie w czasie rzeczywistym, behawioralnej heurystyce wzmocnionej przez AI, technologiom zapobiegania złośliwemu oprogramowaniu, anty-ransomware i anty-cryptojacking.Bezpieczne wprowadzanie poprawek
Cyber Protect automatycznie tworzy kopie zapasowe przed zastosowaniem jakichkolwiek poprawek, aby zapewnić szybkie i łatwe odzyskanie danych, jeśli zainstalowane poprawki spowodują niestabilność systemu.Kopie zapasowe na potrzeby kryminalistyki (forensic)
Uprość przyszłą analizę, raportowanie zgodności i dochodzenia, zbierając cyfrowe dowody – takie jak zrzuty pamięci i informacje o procesach – z kopii zapasowych na poziomie dysku za pomocą trybu dochodzeń kryminalistycznych.Pokonaj oprogramowanie ransomware
Zapobiegaj ponownej infekcji dzięki zintegrowanemu skanowaniu antywirusowemu i usuwaniu złośliwego oprogramowania podczas procesu odzyskiwania. Zyskaj spokój ducha dzięki niezmiennej pamięci masowej na kopie zapasowe.Ciągła ochrona danych
Zabezpiecz nowe dane w momencie ich powstawania. Agent Acronis monitoruje każdą zmianę dokonaną w zdefiniowanych aplikacjach i nieustannie tworzy kopie zapasowe, aby ostatnie zmiany nie zostały utracone w przypadku konieczności ponownego wykonania obrazu komputera.Monitorowanie globalnych zagrożeń i inteligentne powiadomienia
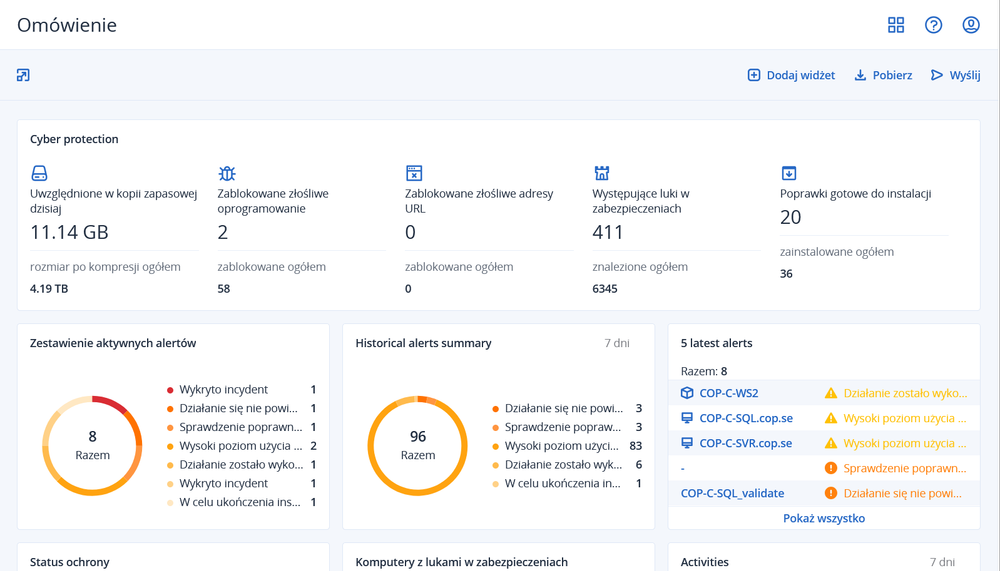
Korzystaj z globalnej sieci centrów operacyjnych Acronis Cyber Protection Operation Centers (CPOC), otrzymując w czasie rzeczywistym powiadomienia o złośliwym oprogramowaniu, lukach w zabezpieczeniach, klęskach żywiołowych i innych globalnych zdarzeniach, które mogą mieć wpływ na ochronę danych.Raportowanie o zgodności danych i mapa ochrony danych
Zapewnij generowanie raportów na temat zgodności, zdobywając szczegółowe informacje o przechowywanych danych i korzystaj z automatycznej klasyfikacji danych, aby śledzić stan ochrony ważnych plików.Cyberprzestępczość oparta na AI
Zautomatyzuj zadania IT z precyzją za pomocą skryptów opartych na AI. Zwiększ wydajność i zredukuj liczbę błędów, usprawniając zarządzanie punktami końcowymi na wszystkich urządzeniach.Monitorowanie oparte na ML
Zwiększ wydajność techników dzięki monitorowaniu predykcyjnemu. Zmniejsz czas przestoju dzięki wykrywaniu anomalii ML. Ustal priorytety i zredukuj liczbę alertów, aby szybciej rozwiązywać problemy.Zdalny pulpit
Używaj jednej aplikacji do płynnego dostępu i obsługi urządzeń z systemami Windows, macOS i Linux przy użyciu wysoce bezpiecznego, zastrzeżonego protokołu NEAR.Inwentaryzacja sprzętu i oprogramowania
Przechowuj aktualne informacje o zasobach sprzętowych i oprogramowaniu, aby właściwie planować wymianę oraz śledzić aktualizacje.
Sprawdzona w branży ochrona danych













- 100% wskaźnik wykrywaniaW certyfikacji AV-Test pod macOS, Acronis wykrył 100% złośliwego oprogramowania i miał zero fałszywych alarmów.
- 0% fałszywych powiadomieńW teście AV-Comparatives Acronis był jednym z zaledwie czterech rozwiązań, które nie wygenerowały fałszywych powiadomień.
- 100% wysokiej wydajnościWe wszystkich ośmiu kategoriach wydajności AV-TEST Acronis uzyskał ocenę wydajności „Bardzo szybki” lub „Szybki”.
Profesjonalne usługi Acronis
Jeśli Twoja organizacja posiada złożoną infrastrukturę IT lub ograniczone zasoby IT, profesjonalne usługi Acronis mogą pomóc Ci w projektowaniu, integracji, wdrażaniu i ciągłej obsłudze rozwiązania Acronis.
Usługi konsultingowe
Zdobądź doświadczenie Acronis i skróć czas potrzebny do uzyskania korzyści z inwestycji w Acronis.- Ekskluzywne
Usługi wdrożenia
Dzięki Usługom Wdrożenia Acronis możesz jako pierwszy wprowadzić na rynek usługi ochrony danych, migracji infrastruktury i odzyskiwania danych po awarii. Usługi inspekcji
Zmniejsz koszty utrzymania i ciesz się poczuciem spokoju, wiedząc, że dane Twoich klientów są chronione zgodnie z najlepszymi praktykami Acronis.Usługi edukacyjne
Umożliw swojemu personelowi obsługę ochrony danych, migracji oraz usług związanych z odzyskiwaniem danych po awarii, zarazem skutecznie wspierając swoich klientów.
Ochroń więcej zasobów na większej liczbie platform
Physical
Applications
- Microsoft Exchange
- Microsoft SQL Server
- Microsoft SharePoint
- Microsoft Active Directory
- Oracle Database
Virtual
- VMware vSphere
- Microsoft Hyper-V
- Citrix XenServer
- Red Hat Virtualization
- Linux KVM
- Oracle VM Server
Endpoints
- Windows PC
- Mac

Potrzebujesz pomocy?
Często zadawane pytania
Czy Acronis Cyber Protect jest dobry?
Acronis Cyber Protect to kompleksowe rozwiązanie do ochrony cybernetycznej, które łączy funkcje tworzenia kopii zapasowych i ochrony danych z zaawansowanymi funkcjami cyberbezpieczeństwa. Został zaprojektowany, aby zapewnić firmom jedno rozwiązanie, które chroni różne rodzaje obciążeń przed szerokim zakresem cyberzagrożeń.
Dzięki temu kompleksowemu podejściu, które zapewnia pełną ochronę z jednej platformy, został uznany za rozwiązanie typu "wszystko w jednym" dla wszystkich rodzajów firm.
Acronis Cyber Protect to doskonałe oprogramowanie ochronne oferujące zarówno funkcje antywirusowe, jak i funkcje tworzenia kopii zapasowych.
Ile licencji potrzebuję dla mojego środowiska?
Licencja jest wymagana dla każdego komputera lub komputera fizycznego, który chcesz zabezpieczyć za pomocą kopii zapasowej. W przypadku, gdy produkt jest używany na klastrze, każdy węzeł klastra musi być licencjonowany.Jaka jest różnica między wersją Standard a Zaawansowaną?
Acronis Cyber Protect Advanced oferuje szereg zaawansowanych funkcji i korzyści w porównaniu z wersją Standard, takich jak scentralizowane zarządzanie planami tworzenia kopii zapasowych, kopia zapasowa na taśmy, migawki pamięci masowej SAN, program Acronis Notary, Acronis ASign i inne.
W przypadku instalacji agenta wewnątrz VM i kopii zapasowej opartej na agencie, obowiązują następujące zasady:
- Licencja zaawansowana jest wymagana w przypadku następujących hiperwizorów: XenServer, KVM, RHV, Oracle VM Server
- Standardowa licencja może być używana pod VMware vSphere, Microsoft Hyper-V, Virtuozzo.
Aby zapoznać się z pełną tabelą porównawczą opcji, zapoznaj się z tym artykułem.
Jaka jest różnica między wdrożeniem lokalnie a wdrożeniem w chmurze?
Wdrożenie w chmurze oznacza, że serwer zarządzania znajduje się w jednym z centrów danych Acronis. Korzyścią z tego podejścia jest to, że nie musisz utrzymywać serwera zarządzania w swojej sieci lokalnej. Ten typ wdrożenia jest dostępny tylko dla licencji subskrypcyjnych i na chwilę obecną nie obejmuje niektórych funkcji wersji zaawansowanej. Ten typ wdrożenia jest zalecany, jeśli masz środowisko tylko dla środowiska Mac lub pojedynczego Mac do zabezpieczenia (ponieważ serwer zarządzania nie może być zainstalowany na Macu).
Wdrożenie lokalnie oznacza, że wszystkie komponenty produktu są zainstalowane w Twojej sieci lokalnej. Musisz użyć tej metody, jeśli twoje komputery nie są podłączone do Internetu.
Możesz znaleźć bardziej szczegółowe informacje tutaj.
Co to jest Acronis Cloud Storage i jak jest licencjonowane?
Acronis Cloud Storage to opcja przechowywania, która zapisuje kopie zapasowe w bezpiecznych i zabezpieczonych Centrach Danych Acronis. Licencje na Acronis Cloud Storage są oparte na subskrypcji i zależą od poziomów pojemności magazynowania. Można zapisywać kopie zapasowe z nieograniczonej liczby komputerów i dowolnego typu platformy do przechowywania w chmurze, w tym kopie zapasowe urządzeń mobilnych. Kwota jest dzielona między wszystkie urządzenia zarejestrowane na koncie*.
(!) Należy pamiętać, że do korzystania z usługi Acronis Cloud Storage wymagana jest co najmniej jedna licencja Acronis Cyber Protect.
*Nie dotyczy darmowego miejsca w chmurze. Bezpłatna przestrzeń dyskowa w chmurze dostępna w ramach licencji subskrypcyjnej jest ważna tylko dla licencjonowanego obciążenia i nie może być udostępniana innym obciążeniom.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.