In an evaluation performed in May–June by well-known German testing laboratory AV-Test, Acronis Cyber Protect Cloud with Advanced Security achieved a perfect score. Acronis Cyber Protect Cloud blocked 10 out of 10 advanced threats crafted by laboratory experts to test the ability of security products to manage with new and unknown threats. AV-TEST evaluated how well the security products stand up against data stealers and ransomware that deploy sophisticated attack methods, such as InlineExecute-Assembly, SetWindowsHookEx DLL Injection, Mavinject LOLBin or Binary Padding. Let's review the methods and methodology in more detail.
Methodology
The test was performed under Windows 10 and amounted to five scenarios with data stealers and five with ransomware.
All attack scenarios were documented according to the standard of the MITRE ATT&CK database. The individual sub-techniques, for example "T1566.001", are listed in the MITRE database for "Techniques" under "Phishing: Spearphishing Attachment". Each test step is thus defined among the experts and can be logically understood. In addition, all attack techniques are explained, along with the malware’s success.
An Advanced Threat Protection test was performed to exactly replicate an actual attack: via spearphishing email, the attackers land on the Windows system. Either the protection systems detect the attacker immediately or when it starts running. In the results chart, this is confirmed with the green field under "Initial Access“ or under "Execution." If this does not occur, the attackers go to work: The data stealers gather information on existing data to exfiltrate it to a C2 server. The ransomware also collects information, but generally it only sends a file list to the C2 server. Afterwards, the encryption of the data begins. When everything is encrypted, a text file is displayed on the screen to initiate the ransom demand.
A special feature in this test: the lab awarded points for detecting significant attack steps — up to four points for every data stealer and up to four points for ransomware. Thus, the best possible protection score in this test was 35 points: (5 x 4 points + 5 x 3 points).
Now let’s explain the attack techniques used.
Inline Execute-Assembly
Inline Execute-Assembly is basically when a Windows process is abused in a .NET runtime environment. A process is singled out, infected with malware code and then launched. In addition, the Anti-malware Scan Interface (AMSI) is circumvented using an AMSI bypass, the scan API provided by Microsoft that is used by some anti-malware solutions. Furthermore, the Event Tracing for Windows function is disabled so that the process routine cannot be traced any further. A good security solution can still prevent further damage, however, such as the siphoning off or encryption of data.
SetWindowsHookEx DLL injection
DLL injection involves executing a malware code in the context of another legitimate Windows process. There are various options for achieving this. A somewhat unobtrusive technique is the installation of a system-wide, injected process (hook) with a hook procedure contained in a malicious DLL. Each attached process running the specified event also loads the malicious DLL and enables the attacker to execute their own code within the affected process. AT-Test methodology carries out information theft or launches ransomware by injecting into explorer.exe process.
Mavinject LOLBin
The Microsoft Application Virtualization Injector (mavinject.exe) is Microsoft utility that is delivered as standard with newer versions (updates) by Windows. It can be used to inject DLLs into external processes. This binary file is a legitimate and digitally signed Windows application through which process injections via this application are more inconspicuous than other techniques. AV-Test used it to carry out information theft or ransomware through explorer.exe or in a newly launched notepad.exe.
Binary padding
Binary padding inflates the file with junk data to deceive the malware scanner. Sometimes the file is padded so heavily that the file size is too large for many anti-malware engines. Due to the continuously altered content, the malware also has constantly altered hash values. As a result, it is also not detected by hash-based block lists and static antivirus signatures. In this test, DLL file was written to a hard drive and padded with a conspicuous number of 0 bytes (30 to 60 MB) before it was used in further steps.
Flawless results
Acronis Cyber Protect Cloud with Advanced Security scored 35 out of 35 possible points, blocking with most threats at the initial access stage, which is the best possible scenario.
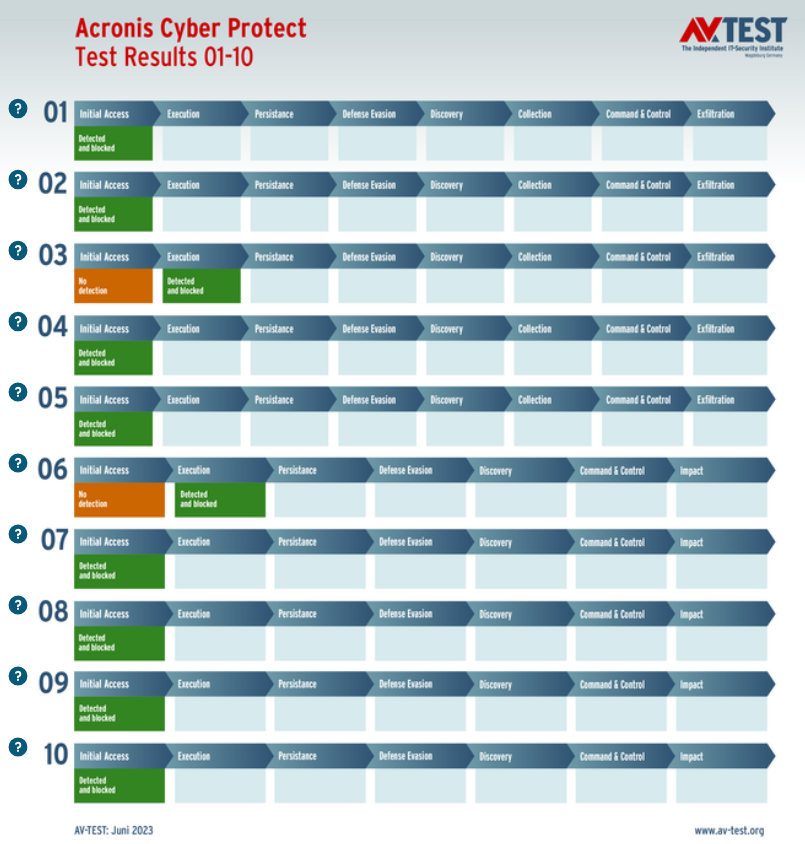
As in previous tests, Acronis Cyber Protect Cloud passed the test error free; however, the product did not earn a certification badge because AV-TEST certifies only those products that achieve certification in regular monthly tests and fulfillment of all their criteria. AV-Test experts praised the results: “The attackers allow a protection solution no margin for error. But even when the methods of attack are devious and the malware brand new, the products in this test were not caught off guard. On the contrary, they quashed every attack in the entire test.”
To learn more about Acronis Cyber Protect Cloud, register for a live demonstration here.



