
Locky is one of the most widespread and active ransomware families on the malicious threats landscape. There is a new version that just appeared a couple of days ago. It’s being delivered by the Necurs botnet through SPAM emails containing Microsoft Word macros exploiting the Microsoft’s Dynamic Data Exchange (DDE). DDE is a Windows feature that handles the electronic transfer of MS Office files using shared memory and data.
The new version of Locky ransomware (MD5: 1676f1817d6ed6d76fbde105f88e615a) is compiled on November 8 and downloaded from the following sources:
hxxp://gulercin.com/HJGdyt73 hxxp://euriskosrl.it/HJGdyt73 hxxp://fgmindia.com/HJGdyt73
Installation
The Locky is downloaded by a script embedded in the Microsoft Word Document. It copies itself as “svchost.exe” to the “%Temp%” folder:
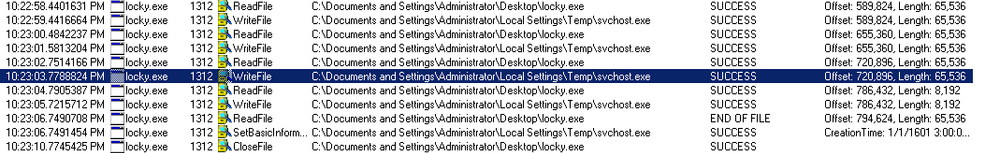
Then, it maps the “%Temp%\svchost.exe” to memory and restarts itself as “svchost.exe”.
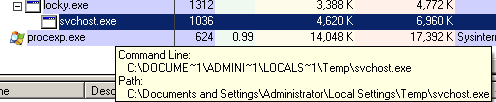
Then, the original Locky file is deleted using the following command:
Obfuscation
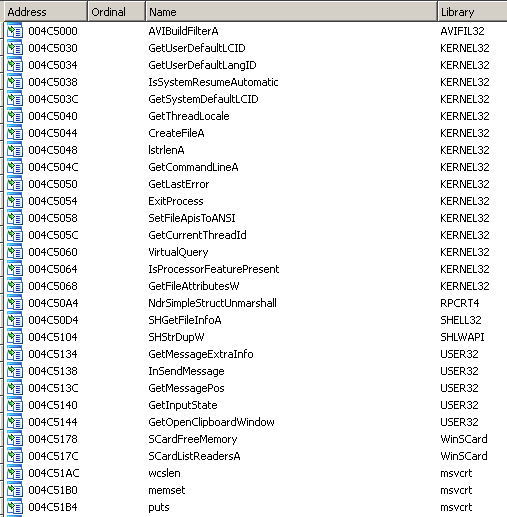
The code is highly obfuscated. Locky has a fake Import Address Table:
Similar to Cerber, the code starts with numerous JMP instructions:
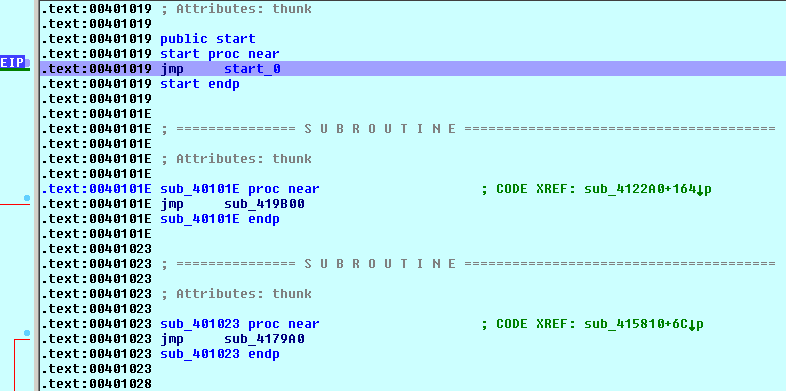
Then, there is junk code:
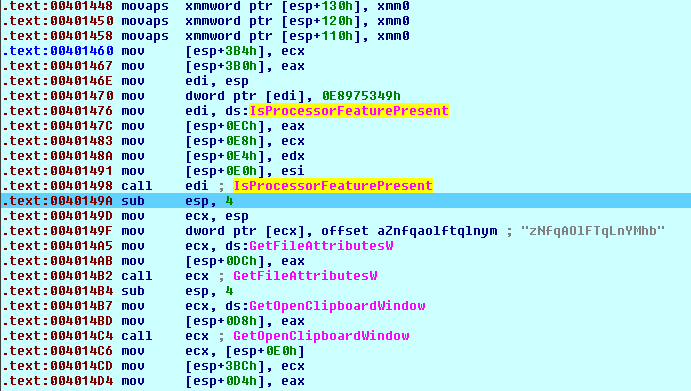
API functions are called indirectly using an internal address table and the code mixed with junk “nop” and “jmp” instructions.
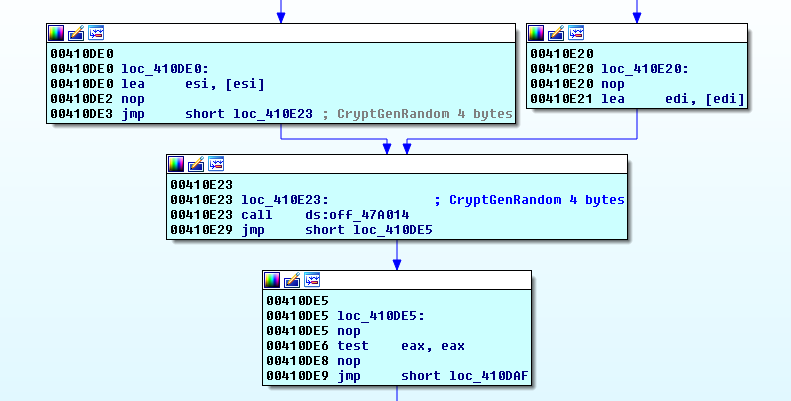
Encryption
Locky encrypts files on all local and mapped network drives.
In the beginning, the ransomware creates a list of files with the following extensions:
For example:
It imports the hardcoded RSA-2048 public key.
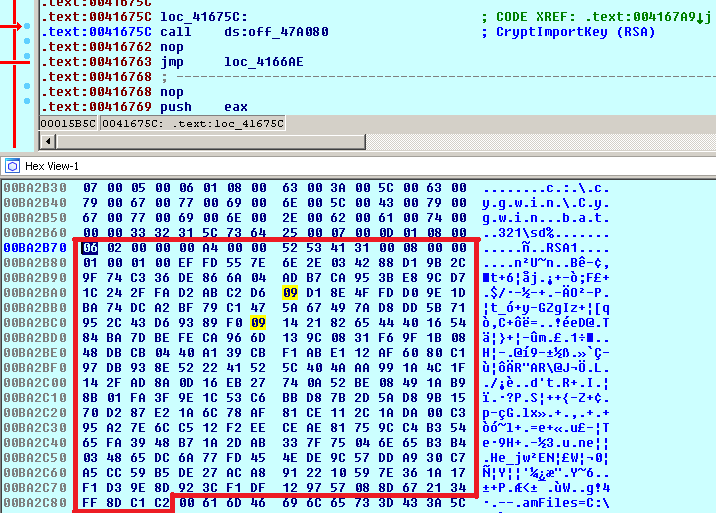
where:
1st byte: BLOB type = PUBLICKEYBLOB (0x06) 2nd byte: version = CUR_BLOB_VERSION (0x02) 5-8 bytes: algorithm id = CALG_RSA_KEYX (0x0000A400) 9-20 bytes: RSAPUBKEY {magic = ‘RSA1’, key length = 2048 bits, public exponent = 65537} 21-276 bytes: key data 256 bytes
Locky takes the name of an original file and renames it to “<ID>.asasin”.
Then, it reads the data from the file:
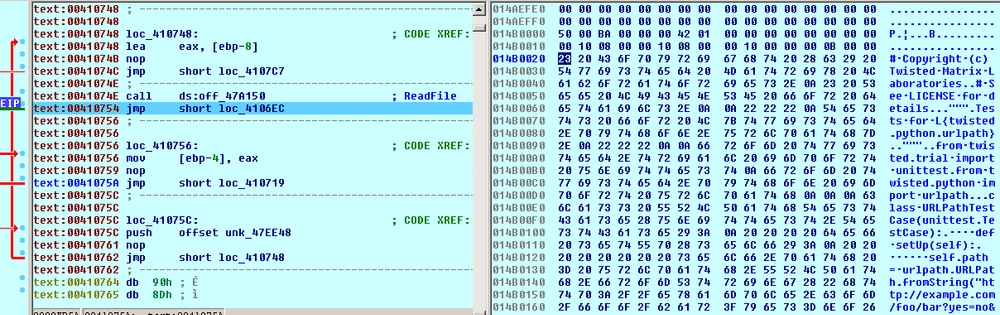
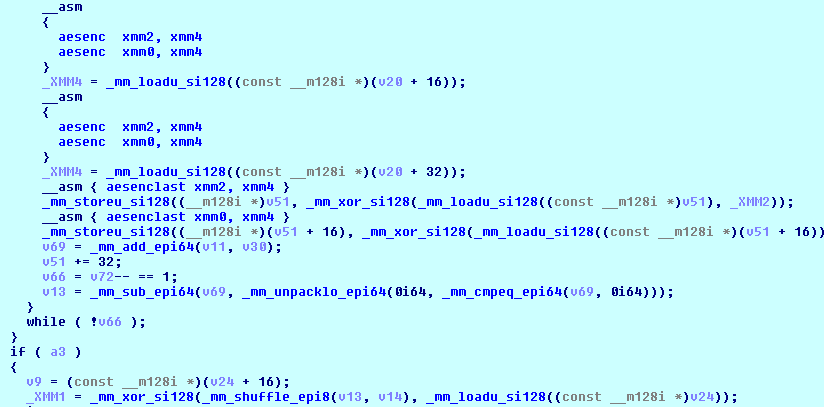
Encrypts the file’s content using the embedded AES algorithm with a 128-bit key.
Writes the encrypted file’s data to the original renamed file:
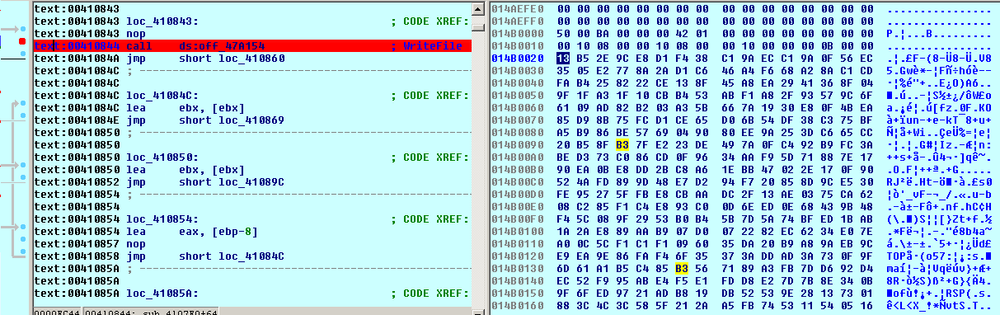
Adds the 836-byte block - the footer - with the encrypted file’s name and AES-128 key:
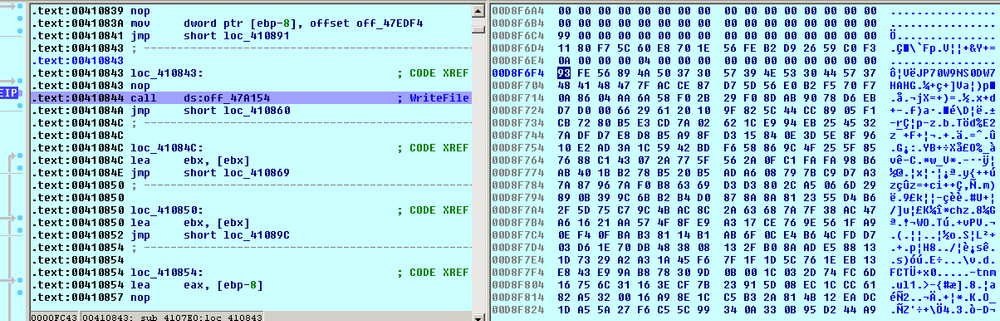
So, the whole file encryption process looks as follows:
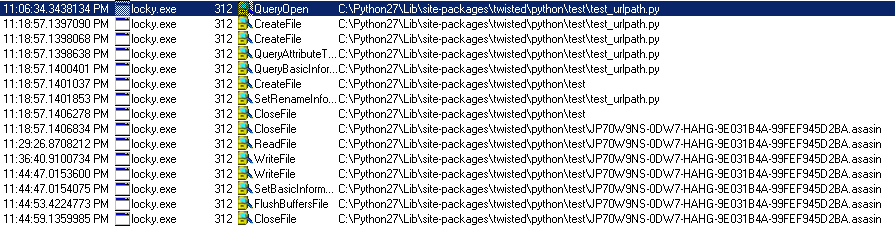
And the encrypted content of the file looks like this:
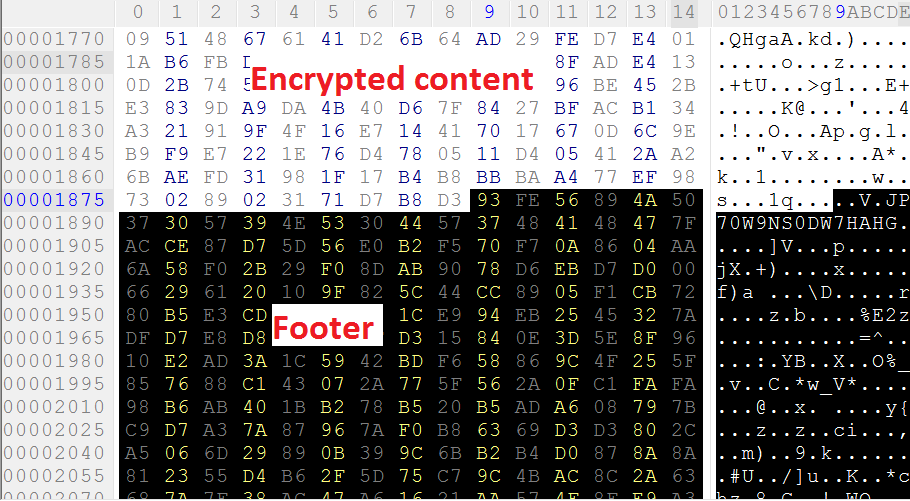
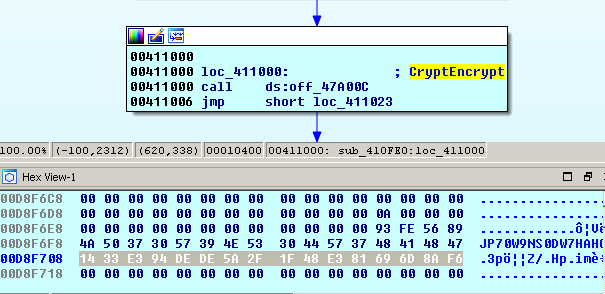
The footer (836 bytes) starts with 4-byte Locky label = “8956FE93h”
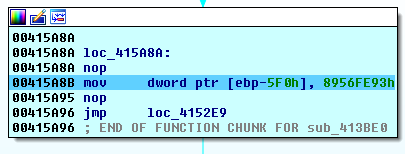
and victim’s ID = “JP70W9NS0DW7HAHG”. Then, 256 bytes go with the file’s key encrypted with the RSA-2048 master public key done with the help of MS CryptoAPI:
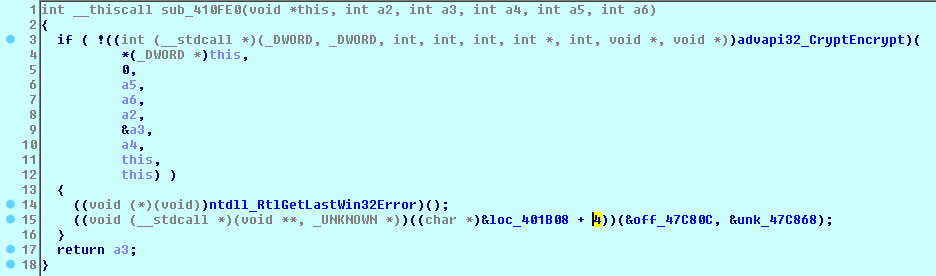
The remaining 560 bytes of the footer contain another Locky label = “0D41BA12Ah” at the beginning:
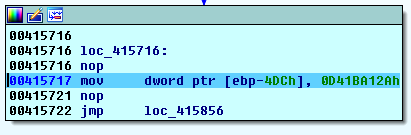
and the filename encrypted with the same embedded AES crypto algorithm used for the encryption of the file’s data. This is done to bypass the behavioral blocker of an antivirus.
After the encryption, the encrypted file will contain the following data blocks:
Decryption Service
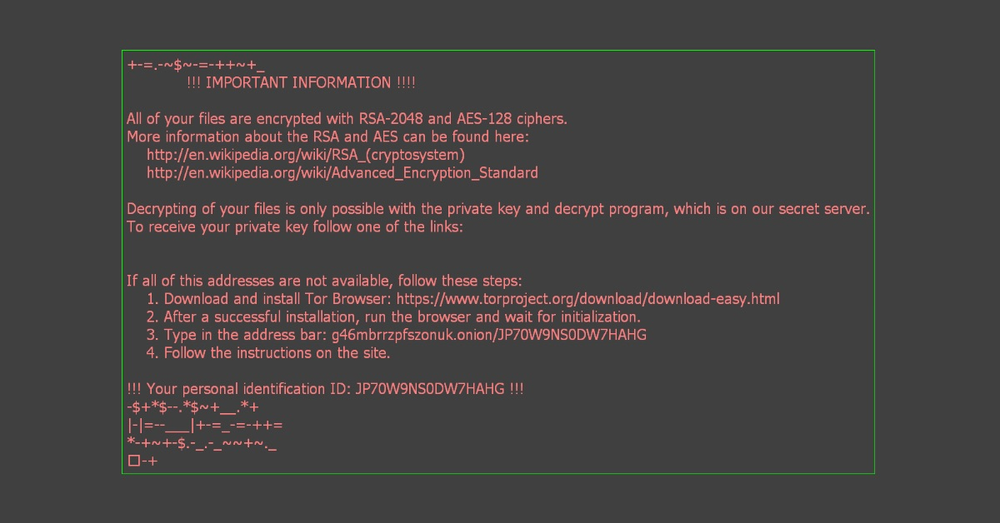
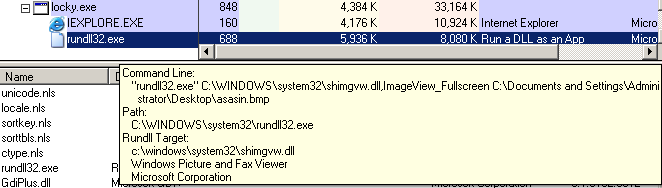
The cryptolocker creates an image, which is set as a wallpaper, and an html page with decryption instructions which are shown to the user:
"HKCU\Control Panel\Desktop\" "Wallpaper" = "%USER%\Desktop\asasin.bmp"
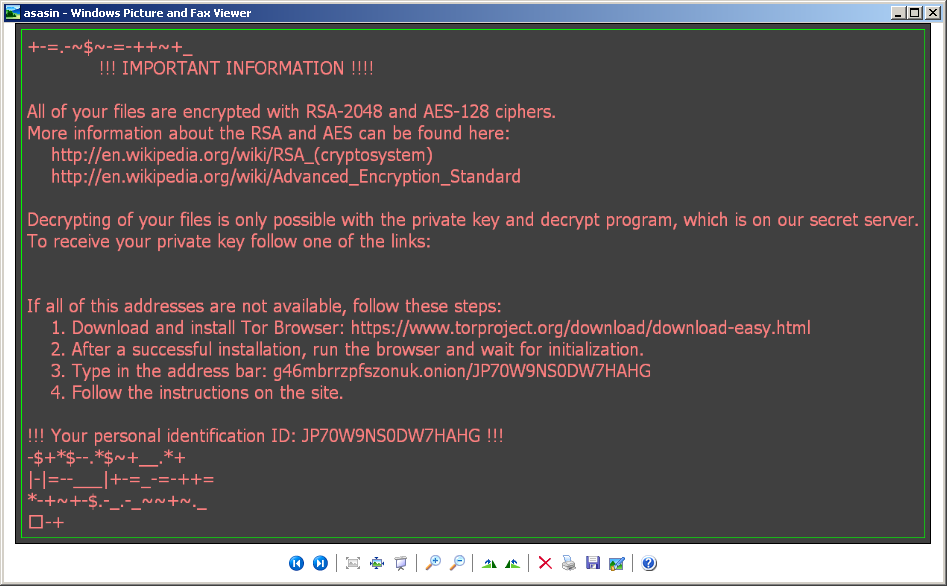
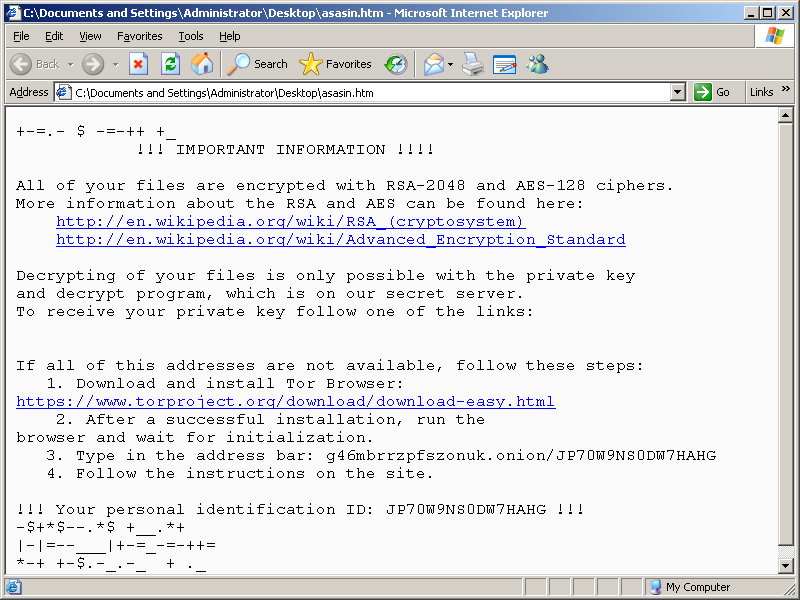
The decryption service is located in the Tor network:
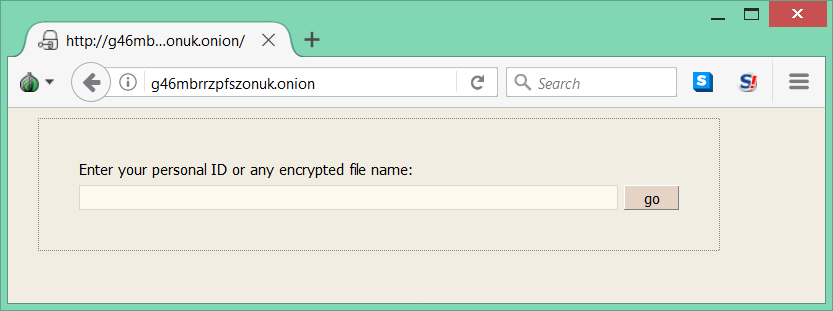
Important to mention that communication with C&C is not available in this version.
As always, Acronis Active Protection stops the threat
We tested Acronis True Image 2018 and as expected, it successfully detected and blocked the new Locky ransomware. It provided easy and reliable protection for user files against being encrypted.
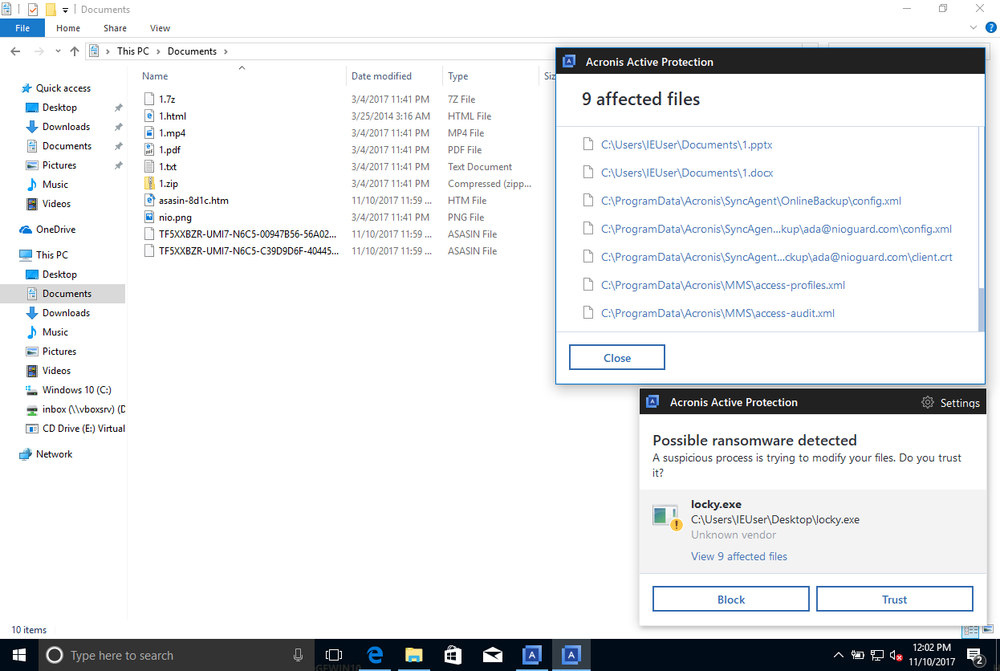
Acronis data protection solutions come with built-in active protection against ransomware — Acronis Active Protection. If you’re using Acronis True Image, Acronis Cyber Backup, or Acronis Backup Cloud, make sure it’s enabled. It will detect the threat, block the attack, and restore the affected data.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




