
Has your computer ever been infected with malware? If so, then you know that unpleasant feeling of wondering what the consequences of falling victim to that cyber threat could be. Some users are lucky enough to avoid identity theft or their sensitive data being traded on dark web marketplaces. While others unfortunately experience these devastating effects of just one successful malware attack, leading to financial damages, stress, data loss, and, on some occasions, weeks to months of recovery time.
How can you best protect your computer and its sensitive information? The answer is to equip yourself with an effective malware scanner that can identify and remove malware at its early stages. In this article, we will talk in detail about the necessity of having a reliable anti-malware tool, how it works, and how to choose the right one for your computer.
What is a malware scanner?
Unlike basic virus scanner tools, modern malware scanners detect a much wider range of threats, helping you eliminate viruses and all types of malicious software.
Why you need a malware scanner?
Nowadays, every home user needs such a tool, since cyberthreats are multiplying daily, and they can easily infect your device without any early signs. Years ago, we were all afraid of street robbery; today, the biggest concerns are related to our digital safety because our devices contain precious memories captured in videos and photos, work-related documents, and sensitive personal data.
Today, we all use our computers and mobile devices for shopping, banking, work, entertainment, and other daily activities. Cybercriminals know that and target unprotected devices to get unauthorized access to all our personal data and to gain financial benefits.
Why your personal devices are Vulnerable?
Personal computers and mobile devices are increasingly targeted by hackers because they:
- Store valuable personal information, including passwords and financial data.
- Credentials for our social media profiles.
- Frequently lack enterprise-level security tools.
- Connect to multiple networks and web services.
- Commonly operate with outdated software, increasing the risk of vulnerability exploitation.
All these factors are a prerequisite for a potential malware infection; it's like a ticking bomb that waits to explode at the most inappropriate moment. The main difference is that the bomb does not make any noise; instead, it silently operates in the background, stealing sensitive information, exploiting system resources for cryptomining, or even encrypting devices and asking for ransom to be paid to restore access to our precious files.
Common myths about built-in security tools
One of the biggest mistakes you can make is believing that built-in security can provide you with reliable and effective protection against the evolving threats we face daily. These tools offer basic protection, but they can't adequately safeguard you against the latest sophisticated malware threats. Built-in scanners and software tools typically provide reactive rather than proactive protection, and they are able to detect malicious files and viruses only after our devices are infected.
On the other hand, advanced anti-malware tools offer you real-time protection, deeper scanning capabilities, more frequent definition updates, and specialized detection algorithms that enhance your system security posture. A reliable malware scanner indeed equips you with an essential additional protection layer that addresses different types of malware that might bypass the built-in protection software. Premium solutions also effectively remove threats that free virus removal tools frequently miss, delivering comprehensive protection against sophisticated hacking attempts and persistent malware.
Common types of malware targeting home users
Unlike the basic viruses of yesteryear, today's cyberthreats employ complex, multi-vector attack strategies. Malware now targets your computers and mobile devices with remarkable precision and, unfortunately, strikes when you least expect it.
- Spyware silently monitors your activities, collecting passwords and your sensitive information while running literally invisibly in the background.
- Ransomware encrypts your entire personal database including photos, videos, documents and work projects, then demands payment to restore your access to these files. Believe me, seeing a screen that provides instructions to follow in order to see your files again is one of the most unpleasant feelings you can experience today.
- Keyloggers are insidious malware that silently record every keystroke you make, capturing banking credentials, personal messages, and sensitive information without leaving a trace.
- Botnet malware secretly converts your device into a "zombie" computer controlled by hackers, who then use your system resources to launch devastating DDoS attacks against websites and services without your knowledge.
How malware can steal your data or lock your files
Malware uses a variety of techniques to take hold of your system. For example, when you download seemingly legitimate files and applications, malware can activate instantly, often before your security software can detect its presence. Beyond infected downloads, these threats also exploit known and zero-day vulnerabilities in software, creating hidden entry points that provide persistent access to hackers.
Once installed, malware can continuously collect your credentials, monitor your web activity, and access your personal files. Among these threats, ransomware is undoubtedly the most devastating malware type, encrypting your invaluable photos and documents in seconds while demanding payment for their release.
Phishing attacks represent yet another method used by cybercriminals to trick you into providing them with sensitive information. We've all received emails pretending to come from trustworthy websites, banks, delivery companies, and government institutions. If you open such an email and accidentally download the attached files, you essentially open Pandora's box for your devices. At this point, malware starts spreading across your system and begins the process of collecting all the valuable information cybercriminals need to gain financial benefits.
How would you feel if one day you woke up and saw your credit cards maxed out, your bank accounts drained, and a notification for a new loan in your name? You would likely feel devastated and scammed, wouldn't you? The unpleasant truth is that cybercriminals are ruthless, and they can turn your life around in a matter of hours. So don't ask yourself if you need a reliable malware scanner, but why aren't you using one now?
How malware scanners protect your device
Malware scanners continuously inspect your device's files and memory, comparing findings against an extensive database of known malware and other online threats. This comprehensive repository contains unique digital "fingerprints" or signatures that identify malicious software with precision.
But the best scanners don't stop there—they also employ behavioral analysis to detect zero-day threats by monitoring your system for any abnormal and suspicious activity. Advanced solutions even incorporate predictive analytics to anticipate future threats based on emerging attack patterns. Simply put, all of your files, registry entries, active processes, and startup programs are thoroughly inspected during a scan, ensuring that even cleverly disguised malicious files can't easily hide from detection.
Real-time vs. manual scans
Real-time scans monitor every file entering your system through downloads, email attachments, or external drives, scanning all incoming files for malware signatures before execution and preventing infection before it starts.
Manual scans provide periodic deep cleaning by checking files already stored on your device, including those that might have been added when protection was disabled or before the installation of security tools.
How scanners detect and remove hidden threats
Cybercriminals' aim to create malicious software that can efficiently slip through your security software. Fortunately, the best malware scanners prevent such infections by using heuristic analysis, which proves to be super effective against these cyberthreats by identifying suspicious behaviors rather than just matching known signatures. If your anti-malware tool detects potential spyware or other malware, the scanner isolates the infected files in a secure environment called a sandbox to safely test and observe its behavior without risking your system by preventing the harmful file or app from executing or interacting with your core system resources.
For deeply embedded threats, scanners employ specialized routines to remove malware from critical system areas, including boot sectors and system restore points, preventing reinfection even after malware removal. Nowadays, there are highly effective anti-malware tools that can successfully detect encryption attempts and fileless malware that exists only in the device's memory and threats disguised as legitimate software. After removal, these scanners repair the damaged files and settings, restoring your device to its secure state while preventing future reinfection.
Paid vs. free scan tools: What's the difference?
Free malware scanners offer basic protection, enabling you to scan and remove common threats like viruses, spyware, and trojans. However, they often lack advanced features like real-time protection or other important protection tools. This lack of advanced features makes them ineffective against phishing attacks and zero-day exploits. These free malware removal tools might be effective enough for basic users, but provide inadequate protection for those who regularly use their devices for banking, online shopping, and other activities involving sensitive personal information.
Paid malware scanners are entirely different; they provide you with everything offered by the free scanners, but also a set of advanced security tools. They offer real-time protection, password managers, identity protection, 24/7 access to customer support for whatever you need, and, most importantly, these scanners are constantly being updated with the main goal of effectively protecting you from zero-day threats.
Tools for Windows, macOS, Android, and iOS devices
Each operating system has its software vulnerabilities and faces unique security challenges. It's well known that Windows devices are being mostly targeted and benefit from robust anti-malware tools with advanced heuristic capabilities. Your Windows computer needs protection that can address common viruses and sophisticated malware.
For macOS, look for scanners specifically designed to detect Mac-focused threats — they exist despite the popular belief that Apple devices can't be infected with malware because of their effective built-in security tools. This is incorrect; these devices are currently experiencing a significant increase in malware attacks.
Android devices also need malware scanners with specialized mobile security tools that scrutinize app permissions and protect against malicious downloads and phishing attacks.
Devices relying on iOS operate in a more restricted environment but still need security software that provides web filtering and privacy protection tools.
Cloud-based vs. offline scanners
Cloud-based scanners use vast online databases to identify the latest threats without consuming significant system resources. They are remarkably effective at detecting both known and new malware threats by comparing suspicious files that have been flagged as harmful against constantly updated online repositories. These scanners are so effective because of their security intelligence detection systems, which collect information from millions of users worldwide.
Offline scanners, conversely, store their detection engines locally, making them effective even without internet connectivity. It is safe to say that they are particularly valuable for scanning your devices for malware that has already infected your system. But they can't provide you with the necessary protection against zero-day attacks.
The truth is that many premium solutions nowadays combine both approaches—using cloud resources for detection while maintaining core functionality offline—giving your device the needed protection regardless of its connectivity status.
Must-have features in a home malware scanner
If you want a good malware scanner for your computer but don't know how to choose one, we can help. Below, you will find the most essential features a robust malware scanner must provide to keep malware threats away.
Essential features every malware scanner should include:
- Real-time protection—This feature is monitors all files as they enter your system through downloads, email attachments, or external drives.
- Heuristic detection—Identifies suspicious behaviors rather than just using a behavior-based approach (matching known signatures). This feature is of utmost importance for detecting evolving threats.
- Quarantine functionality—Isolates suspicious files safely while providing you with the opportunity to decide whether to delete or restore them (in case of false positives).
- Removable device scanning—Automatically scans USB drives and external storage when connected to prevent infection.
- Low system impact—Your scanner must leverage intelligent resource management to run seamlessly in the background without slowing your device performance (by using GPU and hard disk space), which would affect your daily activities and important tasks.
- Easy-to-use interface— One of the most important factors to consider is selecting anti-malware software that provides you with a user-friendly interface, enabling you to use 100% of its protection capabilities.
- Minimal setup requirements—Look for protection software that installs quickly with smart default settings that protect your device immediately without complex configuration.
- Automatic updates—Downloads new threat definitions without manual intervention to ensure protection against the latest zero-day exploits.
- Customizable scan scheduling—This feature allows you to use and set different types of scans at convenient times, from quick to full scans. Pro tip: Run a quick scan once per week and a full scan at least twice a month.
- Web protection—Blocks access to malicious websites and warns about potentially dangerous downloads before they reach your device. This feature should include comprehensive protection against suspicious sites and potentially harmful web content.
- Email security—Scans attachments and links in emails to prevent phishing attacks and malware infection.
- Ransomware protection—Specifically defends against encryption attacks that can lock your personal files. The most effective anti-malware tools can automatically backup your files when they detect encryption attempts.
- Multi-device coverage—Protects all your devices (computers, tablets, smartphones) under a single subscription.
- Integration with other tools—Compatible with firewalls, VPNs, and additional security solutions to create a comprehensive defense system.
- Backup and recovery—The best anti-malware solutions come with advanced backup and recovery features, ensuring that you won't lose a single file under any circumstances.
- Reliable customer support—Provides access to security experts who can help if you encounter sophisticated threats or are just having problems with using the software.
Best malware scanners for home users in 2025
Many home users want to equip their devices with reliable anti-malware software, but with so many options on the market, they can't select the right one that would perfectly fit their needs and requirements. But we are here to help with that task by listing the top three malware scanners for 2025.
Acronis True Image
Provides reliable and effective malware protection and includes the following exclusive great features:
- AI-Powered Protection—Uses behavioral analysis to detect and block zero-day threats before they damage your devices.
- Active (Real-time) Protection—The software is capable of immediately blocking unauthorized encryption attempts and suspicious file modifications.
- Integrated Backup Solution—Creates automatic incremental backups, allowing quick system restoration to a safe state if needed.
- Flexible Backup Options—Schedule hourly, weekly, or monthly backups with full, incremental, or differential options.
- Low System Impact—Maintains optimal device performance while providing enterprise-grade protection against ransomware.
- User-Friendly Interface—Manage protection settings, backups, and system scans from a single, intuitive console.
- Cloud Storage Integration—Supports both local and cloud backup options for maximum data protection flexibility.
- Regular Security Updates—The system receives continuous updates to its behavioral analysis engine to prevent emerging threats from infecting your devices.
- Quick recovery—You can restore your entire database swiftly with a few clicks.
Bitdefender
This protection software provides the security needed for having peace of mind knowing that all of your devices are protected.
- Efficient virus detection capability
- Chat safely in your social media accounts.
- Extends battery life on laptops and tablets because of its lightweight software.
- The basic package includes premium malware protection features.
- Web protection enables you to surf the web safely.
Total AV
Total AV is another antivirus software that you can trust.
- Removes viruses and other malware
- Real-Time Antivirus Protection
- Protects mobile devices, desktops, and laptops.
- Safeguards your identity online
- Lightweight and user-friendly software.
How to run a proper malware scan at home using Acronis True Image
To run your first full scan with Acronis True Image, follow these simple steps:
- Step 1: Open Acronis True Image.
- Step 2: Navigate to the “Protection” tab from the menu.
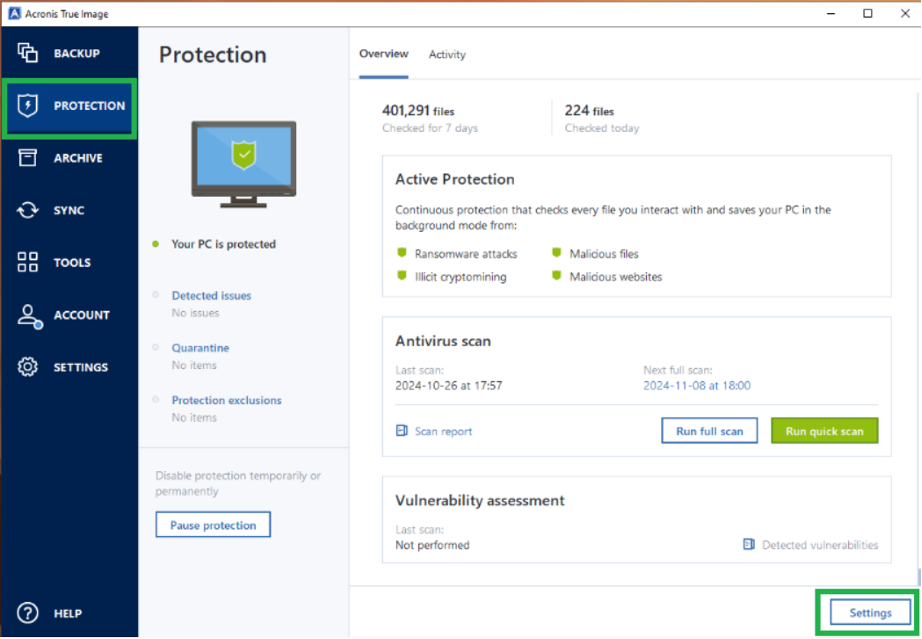
- Step 3: Left-click on the button that says “Run full scan.”
If malware is detected, suspicious files are automatically quarantined for analysis, allowing you to later delete or restore them as needed.
What to do after malware is removed
After successfully removing malware from your device, immediately change all your passwords—especially for banking, email, and social media accounts. Use unique, complex passwords for each service. Check for potential data breaches by reviewing recent account activities and transaction histories. Services like HaveIBeenPwned can help determine if your email was compromised in known breaches.
Making sure your system is fully clean after malware removal
Run a second full scan to ensure no infected files remain on your system. Check your installed third-party applications and browser extensions for unfamiliar items. Review startup programs and scheduled tasks for suspicious entries that could indicate remaining infection vectors.
Tips to avoid reinfection
- Keep all software updated, including your operating system and third-party applications, as even a single unpatched program can serve as an entry point for malware.
- Enable automatic updates whenever possible.
- Install a reliable real-time protection solution with regular definition updates.
- Be cautious with email attachments and downloads, even from seemingly legitimate sources.
- Consider implementing multi-factor authentication for sensitive accounts, adding an extra protection layer beyond passwords.
- Back up your important files regularly to external storage or secure cloud services to minimize damage from future infections.
FAQs
Do I need a separate malware scanner if I have antivirus?
- Yes, your antivirus alone may not provide complete protection. A dedicated malware scanner offers additional protection against sophisticated threats like spyware and ransomware that traditional antivirus programs might overlook.
Can malware scanners slow down my PC?
- They can impact your PC performance, but modern security tools are designed to minimize this effect. If you notice your system becoming sluggish, consider scheduling intensive scans when you are not using your computer, such as when you are not home or during the night. Most scanners also offer low-resource modes that balance protection with performance for your daily activities.
Is it safe to use free scanners?
- Free scanners from established security companies generally provide basic protection without risk. But keep in mind to avoid downloading their software from unfamiliar websites or clicking on pop-up advertisements offering free scans—these are often disguised threats targeting your personal information.
How often should I scan my laptop or phone?
- Run a quick scan once or twice weekly and a full system scan at least once every month. Additionally, scan your device immediately after connecting to unsecured public Wi-Fi, downloading files from unverified sources, or noticing unusual device behavior.
Summary
In 2025, we are witnessing a pandemic of malware attacks, which have doubled since COVID-19 hit the world. The consequences can be severe for any user: losing your entire database, having your activities silently monitored, having your banking information and credentials stolen to max out credit cards and drain accounts, finding unauthorized loans in your name, or discovering your device resources are being hijacked for cryptomining.
A single successful malware attack can entirely turn around your life, keeping you awake at night wondering why this happened and if you could have prevented it. While no security solution can make you completely immune to online threats or guarantee 100% detection rates, a quality malware scanner significantly reduces the risk of falling victim to cybercriminals.
If you haven't equipped your computer with robust protection, ask yourself what is the price of your cherished videos and photos that have captured the happiest moments of your life, like watching your children grow, your first vacation as a family, or the moments shared with your friends. The answer is clear: they are priceless because they are part of your life, part of you.
Why risk losing them forever? You can prevent such catastrophic scenarios leading to destructive consequences with just one wise decision. Take care of your digital future by starting to use the right malware scanner that will protect you from both known and zero-day malware attacks. Acronis True Image provides you with everything needed to have peace of mind knowing that you won't lose a single file from your database under any circumstances.
Do not hesitate anymore and take care of your devices; equip them with the efficient and reliable protection that they need. Do it today, because tomorrow it may be too late. Become part of the Acronis True Image family. We guarantee that you won't regret it for a second, and you won't stay awake in the middle of the night wondering what may happen if your device gets infected with malware.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



