A new ransomware family was discovered in August 2019. Called HILDACRYPT, it is named after the Netflix cartoon “Hilda” because the TV show’s YouTube trailer was included in the ransom note of the original version of the malware.
HILDACRYPT camouflages itself as a legitimate XAMPP installer, which is an easy to install Apache distribution containing MariaDB, PHP, and Perl. However, the cryptolocker’s file name ‘xamp’ differs from the legitimate version. Moreover, the ransomware file does not have a digital signature.
Static analysis
The ransomware file is PE32 .NET Assembly for MS Windows. It is 135168 bytes in size. Both the payload code and the protector’s code are written in C#. According to the compilation timestamp, the binary was compiled on September 14, 2019.
While Detect It Easy claims the ransomware was packed with Confuser and ConfuserEx, these obfuscators are the same. ConfuserEx is simply the successor of Confuser, so their code signatures are extremely similar.
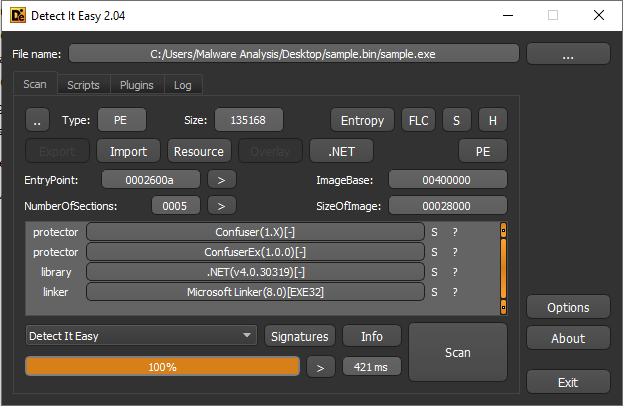
To be entirely accurate, however, HILDACRYPT is packed with ConfuserEx.
SHA-256: 7b0dcc7645642c141deb03377b451d3f873724c254797e3578ef8445a38ece8a
Attack vector
Most likely, the ransomware was found on one of the web programming sites pretending to be the legitimate version of XAMPP software.
The whole infection chain can be seen at app.any.run sandbox.
Obfuscation
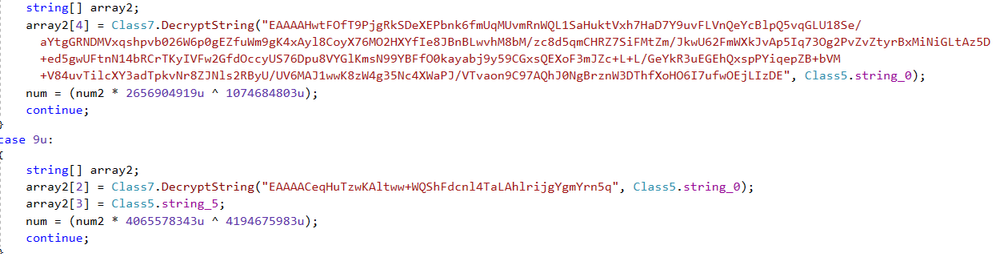
The ransomware’s strings are encrypted when stored. Once launched, HILDACRYPT decodes them with Base64 and AES-256-CBC.
Installation
First, the ransomware creates a folder in %AppData\Roaming% with a randomly generated GUID (Globally Unique Identifier). After adding the ‘bat’ file to this location, the ransomware then runs it with cmd.exe:
cmd.exe /c \ JKfgkgj3hjgfhjka.bat \ & exit
It then starts the batch script to disable system functions or services.
The script contains a long list of commands that deletes shadow copies, disables any SQL server, as well as backup and anti-malware solutions.
In addition to attacking popular backup and anti-malware solutions from Veeam, Sophos, Kaspersky, McAfee, and others, for example, it also tries (unsuccessfully) to stop the Acronis Cyber Backup services.
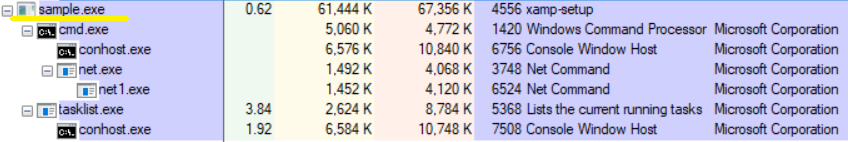
After disabling the mentioned above services and processes, the cryptolocker collects information about all running processes using the tasklist command to make sure that all the needed services were disabled.
tasklist v /fo csv
This command displays a detailed list of running processes separated with ‘,’.
"\"csrss.exe\",\"448\",\"services\",\"0\",\"1�896 ��\",\"unknown\",\"�/�\",\"0:00:03\",\"�/�\""

After this check, the ransomware starts the encryption process.
Encryption
File encryption
HILDACRYPT goes through all of the content of found drives, skipping the ‘Recycle.Bin’ and ‘Reference Assemblies\\Microsoft’ folders. (The second folder is skipped because it contains the vital files such as dll, pdb, etc. for .Net applications that may affect the ransomware.)
The following list of file extensions is used by the ransomware to find the files to be encrypted:
".vb:.asmx:.config:.3dm:.3ds:.3fr:.3g2:.3gp:.3pr:.7z:.ab4:.accdb:.accde:.accdr:.accdt:.ach:.acr:.act:.adb:.ads:
.agdl:.ai:.ait:.al:.apj:.arw:.asf:.asm:.asp:.aspx:.asx:.avi:.awg:.back:.backup:.backupdb:.bak:.lua:.m:.m4v:.max:
.mdb:.mdc:.mdf:.mef:.mfw:.mmw:.moneywell:.mos:.mov:.mp3:.mp4:.mpg:.mpeg:.mrw:.msg:.myd:.nd:.ndd:.nef:
.nk2:.nop:.nrw:.ns2:.ns3:.ns4:.nsd:.nsf:.nsg:.nsh:.nwb:.nx2:.nxl:.nyf:.tif:.tlg:.txt:.vob:.wallet:.war:.wav:.wb2:.wmv:
.wpd:.wps:.x11:.x3f:.xis:.xla:.xlam:.xlk:.xlm:.xlr:.xls:.xlsb:.xlsm:.xlsx:.xlt:.xltm:.xltx:.xlw:.xml:.ycbcra:.yuv:.zip:.sqlite:
.sqlite3:.sqlitedb:.sr2:.srf:.srt:.srw:.st4:.st5:.st6:.st7:.st8:.std:.sti:.stw:.stx:.svg:.swf:.sxc:.sxd:.sxg:.sxi:.sxm:.sxw:.tex:
.tga:.thm:.tib:.py:.qba:.qbb:.qbm:.qbr:.qbw:.qbx:.qby:.r3d:.raf:.rar:.rat:.raw:.rdb:.rm:.rtf:.rw2:.rwl:.rwz:.s3db:.sas7bdat:
.say:.sd0:.sda:.sdf:.sldm:.sldx:.sql:.pdd:.pdf:.pef:.pem:.pfx:.php:.php5:.phtml:.pl:.plc:.png:.pot:.potm:.potx:.ppam:.pps:
.ppsm:.ppsx:.ppt:.pptm:.pptx:.prf:.ps:.psafe3:.psd:.pspimage:.pst:.ptx:.oab:.obj:.odb:.odc:.odf:.odg:.odm:.odp:.ods:.odt:
.oil:.orf:.ost:.otg:.oth:.otp:.ots:.ott:.p12:.p7b:.p7c:.pab:.pages:.pas:.pat:.pbl:.pcd:.pct:.pdb:.gray:.grey:.gry:.h:.hbk:.hpp:
.htm:.html:.ibank:.ibd:.ibz:.idx:.iif:.iiq:.incpas:.indd:.jar:.java:.jpe:.jpeg:.jpg:.jsp:.kbx:.kc2:.kdbx:.kdc:.key:.kpdx:.doc:.docm:
.docx:.dot:.dotm:.dotx:.drf:.drw:.dtd:.dwg:.dxb:.dxf:.dxg:.eml:.eps:.erbsql:.erf:.exf:.fdb:.ffd:.fff:.fh:.fhd:.fla:.flac:.flv:.fmb:
.fpx:.fxg:.cpp:.cr2:.craw:.crt:.crw:.cs:.csh:.csl:.csv:.dac:.bank:.bay:.bdb:.bgt:.bik:.bkf:.bkp:.blend:.bpw:.c:.cdf:.cdr:.cdr3:
.cdr4:.cdr5:.cdr6:.cdrw:.cdx:.ce1:.ce2:.cer:.cfp:.cgm:.cib:.class:.cls:.cmt:.cpi:.ddoc:.ddrw:.dds:.der:.des:.design:.dgc:.djvu:
.dng:.db:.db-journal:.db3:.dcr:.dcs:.ddd:.dbf:.dbx:.dc2:.pbl:.csproj:.sln:.vbproj:.mdb:.md"
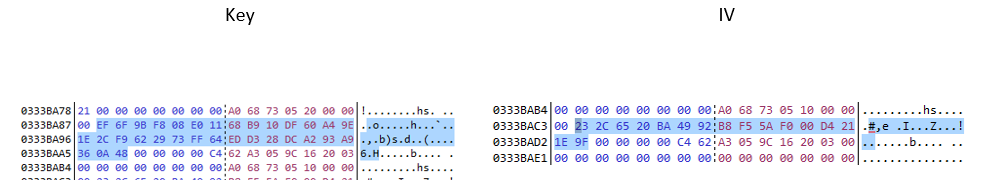
To encrypt the user’s files, the ransomware uses AES-256-CBC crypto algorithm. The key size is 256 bits and IV is 16 bytes.
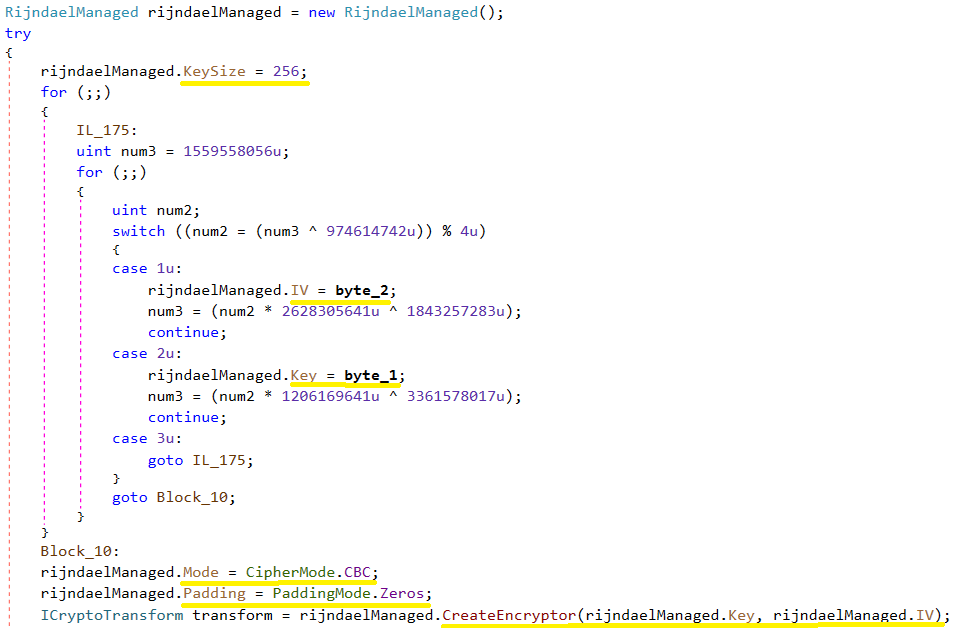
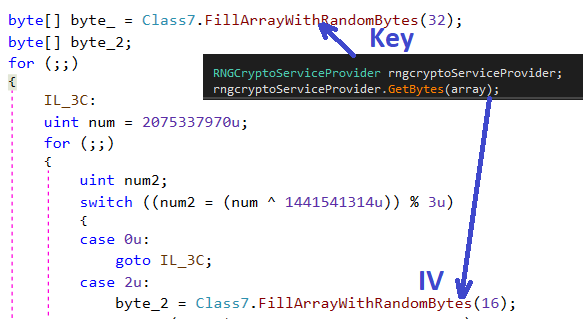
Byte_2 and byte_1 were generated randomly on the next screen via GetBytes().
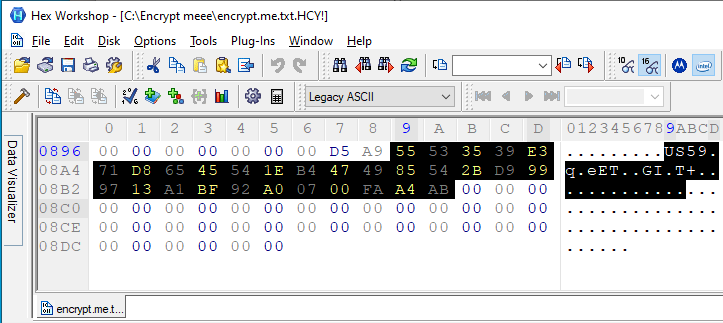
Encrypted files get an ‘HCY!’ extension. This is an example of an encrypted file. The Key and IV mentioned above were created for this file.
Keys encryption
The cryptolocker stores the generated AES key in the encrypted file. The first part of the encrypted file has a header containing the data such as ‘HILDACRYPT’, ‘KEY’, ‘IV’, ‘FileLen’ in an XML format and looks as follows:

The AES Key and IV are encrypted with RSA-2048 and encoded with Base64. The RSA public key is stored in one of the encrypted strings in an XML format in cryptolocker’s body.
<RSAKeyValue><Modulus>28guEbzkzciKg3N/ExUq8jGcshuMSCmoFsh/3LoMyWzPrnfHGhrgotuY/
cs+eSGABQ+rs1B+MMWOWvqWdVpBxUgzgsgOgcJt7P+r4bWhfccYeKDi7PGRtZuTv+XpmG+m+u/
JgerBM1Fi49+0vUMuEw5a1sZ408CvFapojDkMT0P5cJGYLSiVFud8reV7ZtwcCaGf88rt8DAUt2iSZQix0aw8PpnCH5/
74WE8dAHKLF3sYmR7yFWAdCJRovzdx8/qfjMtZ41sIIIEyajVKfA18OT72/
UBME2gsAM/BGii2hgLXP5ZGKPgQEf7Zpic1fReZcpJonhNZzXztGCSLfa/jQ==
</Modulus><Exponent>AQAB</Exponent></RSAKeyValue>
The RSA public key is used for AES file key encryption. The public RSA key is Base64 encoded and consists of modulus and public exponent 65537. For decryption, the private RSA key is needed, and that is owned by the attacker.
After RSA encryption, the AES key is encoded with Base64 stored in the encrypted file.
Ransom notes
When encryption is completed, HILDACRYPT drops an ‘html’ file to the folders where it encrypted files. The ransomware note contains two email addresses by which a victim should contact the attacker.
- hildalolilovesyou @ airmail . cc
- hildalolilovesyou @ memeware . net

The ransom note also has the message ‘No loli is safe ;)’ that refers to anime and manga characters that have the physiques of a prepubescent girl.
Conclusion
HILDACRYPT being a new ransomware family, there is an even newer version of it. The encryption model does not allow victims to decrypt files encrypted by the ransomware. The cryptolocker employs active protection techniques to shut down protection services that belong to backup solutions and anti-viruses. The author of HILDACRYPT is clearly a fan of anime and the “Hilda” TV series on Netflix.
As usual, the good news is that Acronis Cyber Backup and Acronis True Image can protect your computer against HILDACRYPT ransomware – and service providers can similarly protect their customers with Acronis Backup Cloud. That’s because not only do these cyber protection solutions offer backup, but they also include our integrated Acronis Active Protection, an AI-enabled and behavior-based technology that is uniquely able to deal with zero-day ransomware threats.
IoCs
‘HCY!’ file extension
HILDACRYPTReadMe.html
‘xamp.exe’ with one ‘p’ symbol and without a digital signature
SHA-256: 7b0dcc7645642c141deb03377b451d3f873724c254797e3578ef8445a38ece8a
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



