Executive summary
Acronis has developed a New Generation technology that proactively prevents zero-day infections, enabling users to prevent ransomware attacks and recover data without paying any ransom. Yesterday, we discovered a new mutation of Osiris ransomware that easily bypassed Windows Defender. Today, it wasn’t so lucky, but there is already a new version that fooled the traditional security software again. Acronis Active Protection™ is the only technology that is able to block all versions of Osiris ransomware attacks. And what’s more, it’s capable of instantly restoring any encrypted data without contacting the crooks or paying any ransom. This is possible because of integration with Acronis Cloud. The only trick is that it needs to run on your computer when the ransomware strikes.
Infection of Cockrell Hill Police Department in Texas that led to the loss of eight years of critical evidence data could’ve been prevented had Acronis product been installed there.
What you should know about the new Osiris ransomware.
- Osiris is the 7th generation of the Locky ransomware / crypto virus, traditionally spread by SPAM campaigns;
- It’s difficult to detect as it uses standard Windows components to download and execute the payload (scripts and libraries);
- Osiris has inbuilt detection of virtualization, which complicates the job of debugging and reverse engineering using a virtual machine; this algorithm is heavily modified compare to the initial version from June 2016.
- It infects local devices and easily spreads across the network to infect other computers and network folders;
- Osiris can also be distributed via CRM/Customer support systems (including cloud based) across organizational boundaries. Infected user in one organization can send an email to CRM system email address; its internal parser parses incoming email and puts malicious attachment to automatically generated ticket. Customer support engineer opens the tickets, open Excel attachment and infect the network.
- As Acronis predicted, ransomware crooks have started to attack backup solutions. Osiris directly attacks Microsoft Volume Shadow Copy Service (VSS) available in every copy of MS Windows and delete already created Shadows copies;
- Osiris uses strong encryption algorithms, therefore affected data cannot be decrypted by any third-part tools;
- It affects Windows and possibly Mac and Android devices;
Acronis Active Protection™, a combination of integrated security and backup solution, is capable of detecting and instantly recovering files attacked by Osiris.
Evolution of the Locky ransomware family
Locky ransomware has undergone another facelift, as cyber criminals roll out updates to one of the most common and damaging families of file-encrypting malware. The new ransomware is named Osiris, after the Egyptian god of the afterlife, and comes with improved features designed to attack backups and avoid being detected. It appends the .orisis extension to the end of the encrypted files and follows the standard pattern of infection: Invade, Encrypt, Extort. Riding on the back of Locky’s success, Osiris is one of the most serious cyber security treats computer users are facing today.
Locky ransomware was first discovered in February 2016 and has since undergone at least seven changes, trying to stay ahead of the security vendors trying to detect and stop this type of ransmoware.
A history of Locky ransomware
.locky — February 2016
.zepto — June 2016. One month later, Locky started supporting offline encryption with embedded RSA keys in case it wasn’t able to reach its C&Cs.
.odin — September 2016
.shit, .thor — October 2016
.aesir — November 2016
.zzzzz, .osiris — December 2016
Acronis Security Team investigated the following Osiris ransomware sample:
File Name: ekijLpDlRXB.zk
Size: 161625 bytes
MD5: 3545436c22a9a43e29396df87823013d
It should also be noted by some researchers that Osiris also affects Apple Mac and Android devices. Acronis Security Team is currently conducting investigate and a new report will be released separately.
How is Osiris ransomware distributed?
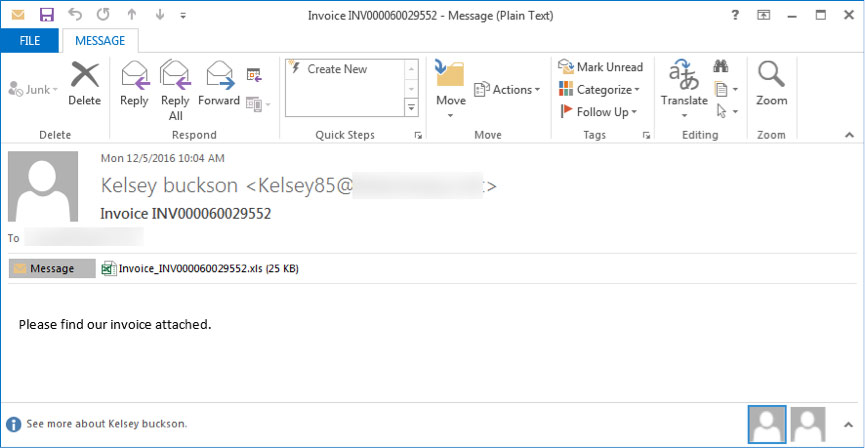
1. SPAM. Typically, Osiris ransomware is distributed through SPAM emails with the words “Invoice” or “Order Confirmation” in the subject line and a compressed attachment containing the malicious script. It can be an Excel file with a VBA macro or a .jse executable script (a dropper). When executed, it downloads a DLL file and runs it with the help of Rundll32.exe.
Osiris authors try to hide ransomware by not using .exe executables and instead using standard Windows components to launch their scripts and DLL files.
Sample of a SPAM email containing Osiris ransomware-infected attachment (Image courtesy of BleepingComputer).
2. Malicious advertising (Malvertising). Ransomware crooks use legitimate advertising networks to serve cleverly designed ads that distribute ransomware with little or no user interaction required. Some of the websites affected last year included BBC, MSN, and AOL, with cyber criminals taking advantage of the automated ad networks, which allowed them to serve malicious ads after the their account passed initial verification checks.
Infection of corporate networks
Just like Locky, the Osiris ransomware is classified as a Trojan crypto-virus with the worm-like distribution technique. It has the capacity to spread over the network without any user interaction with some victims reporting the need to shut down the domain controller to stop the spreading of the attack. Osiris is capable of infecting thousands of shared folders, network-attached drives, and other machines on the same network. The damage from losing that many devices on the same network can be fatal for any business.
Osiris can also be distributed via CRM/Customer support systems (including cloud based) across organizational boundaries. Infected user in one organization can send an email to CRM system email address; Its internal parser parses incoming email and puts malicious attachment to automatically generated ticket. Customer support engineer opens the tickets, open Excel attachment and infect the network.
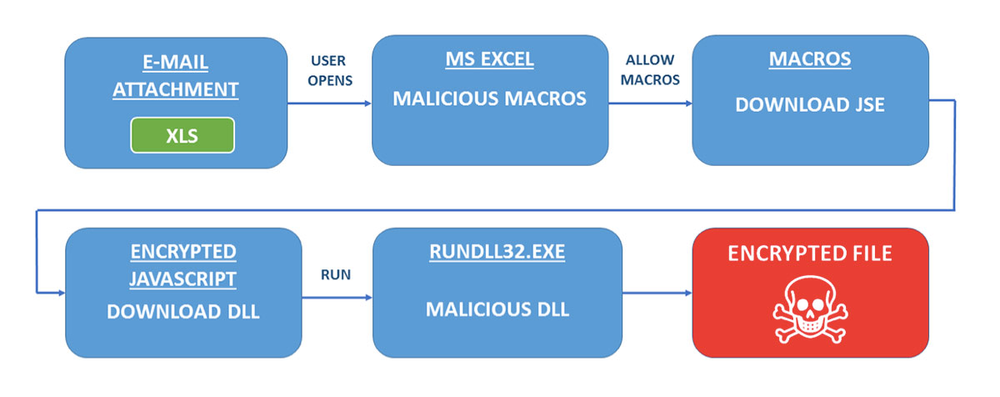
Osiris infection and execution
Osiris ransomware execution order
The version of the Osiris dropper that was sampled on 29/01/2017 was 71 KB in size, which is twice as large compared to the samples collected in December 2016. It is also currently undetectable by Windows Defender.
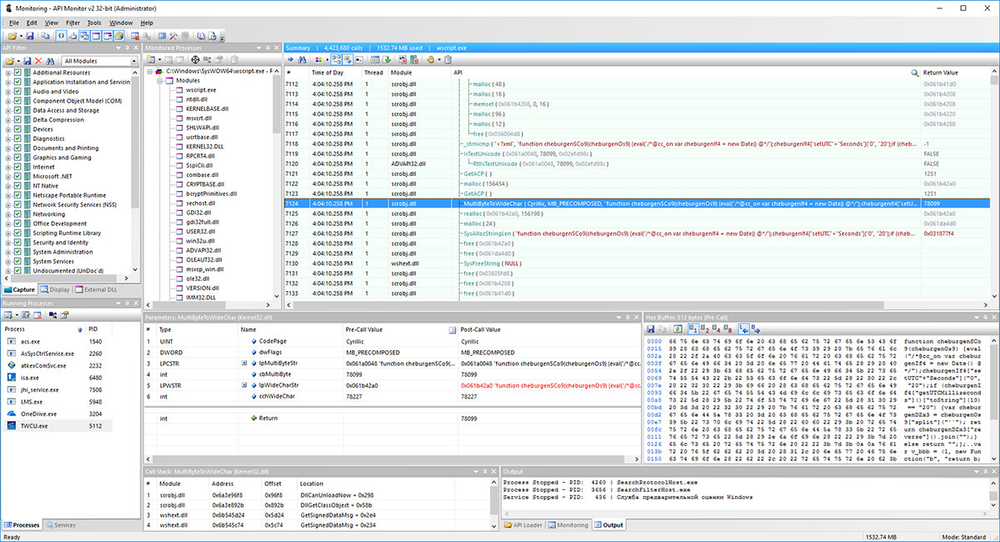
API Monitor screenshot showing the execution of the cheburgen function.
First attempts to download the payload was by contacting a Polish server.
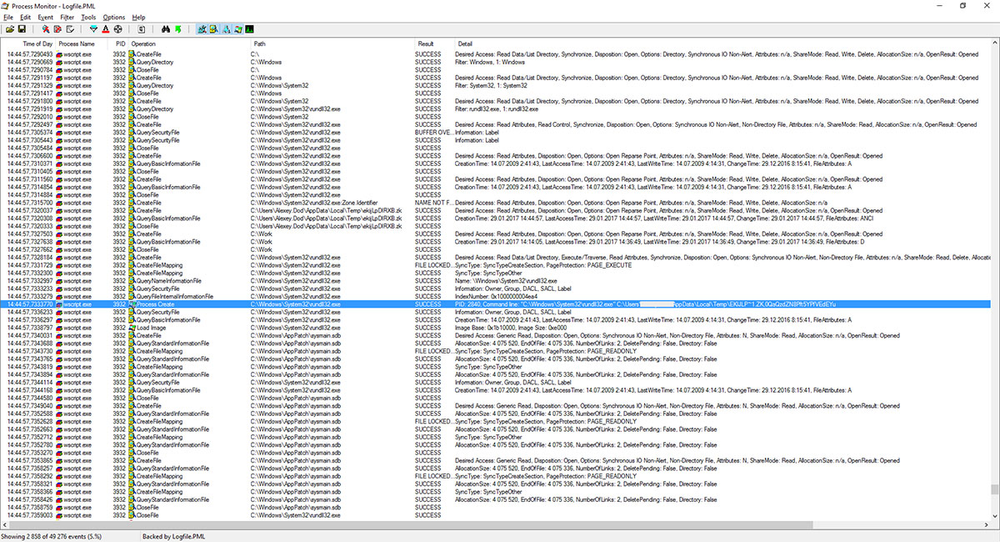
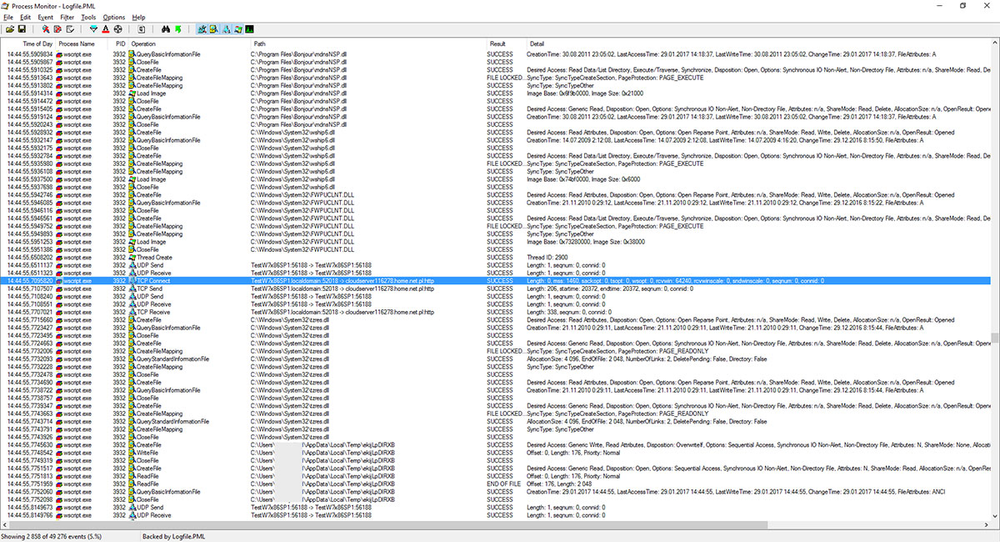
Process Monitor screenshot showing the dropper contacting home[.]net[.]pl
However, it later switched to a Russian server elixe[.]net which is currently blocked by most anti-malware programs.
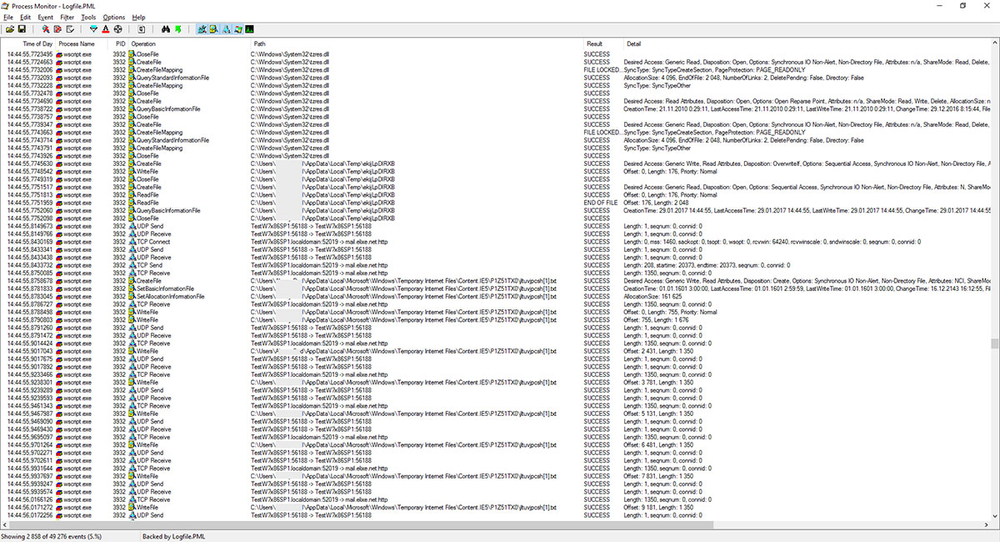
Process Monitor screenshot showing the process of downloading malware from elixe[.]net.
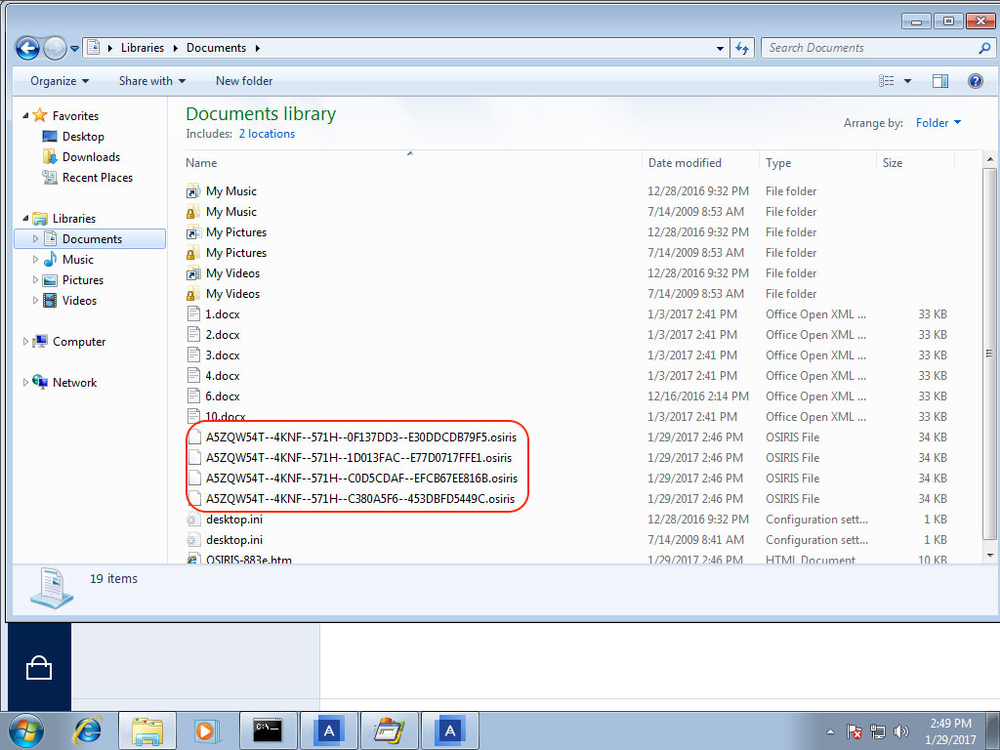
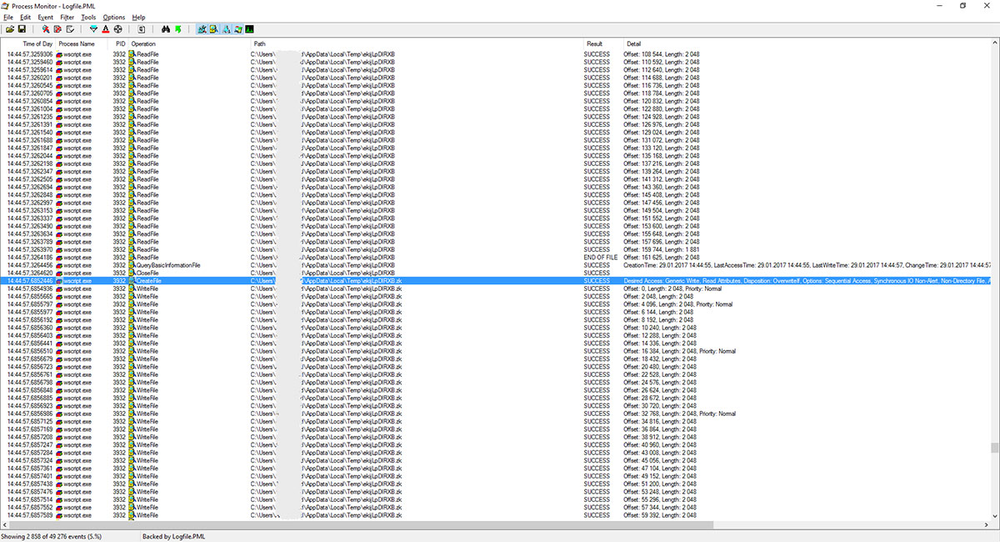
Process Monitor screenshot showing the process of downloading of ekijLpDlRXB.zk into the user’s Temp directory.
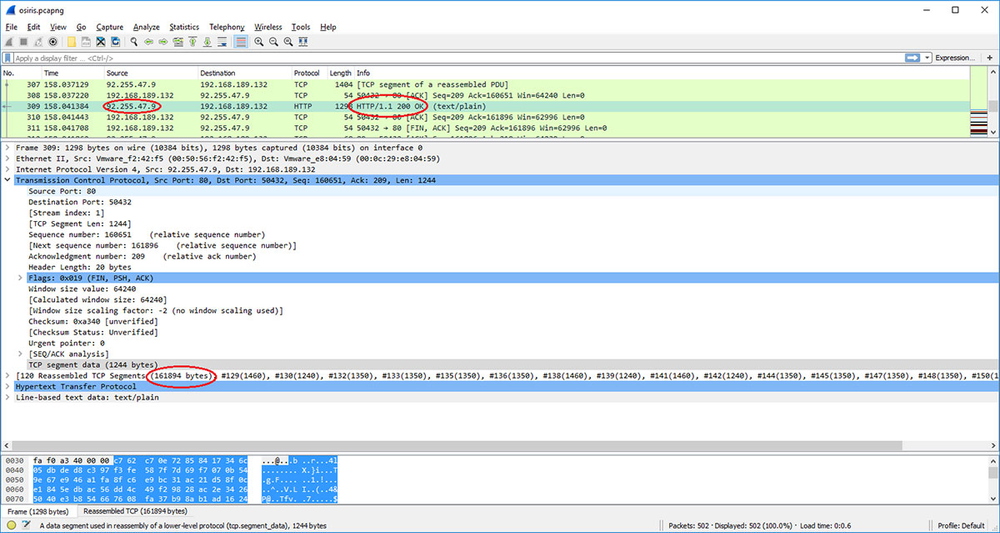
Wireshark screenshot showing the downloaded payload size of 161894 bytes. IP 92.255.47.9 potentially belongs to the pool of Osiris C&C IP addresses.
Following the successful download, ekijLpDlRXB.zk is activated through rundll32.exe using the following command:
"C:\Windows\System32\rundll32.exe"
C:\Users\User.Name\AppData\Local\Temp\EKIJLP~1.ZK,0QaQzdZN8Pft5YPfVEdEYu
(May vary. It contains payload with link, file name and generated C&C)
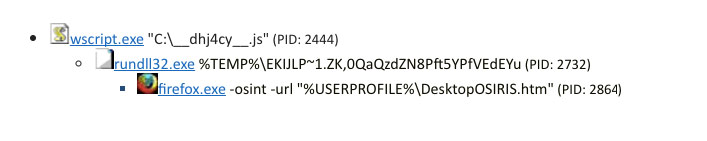
Process Monitor screenshot showing the process execution through runndll32.exe
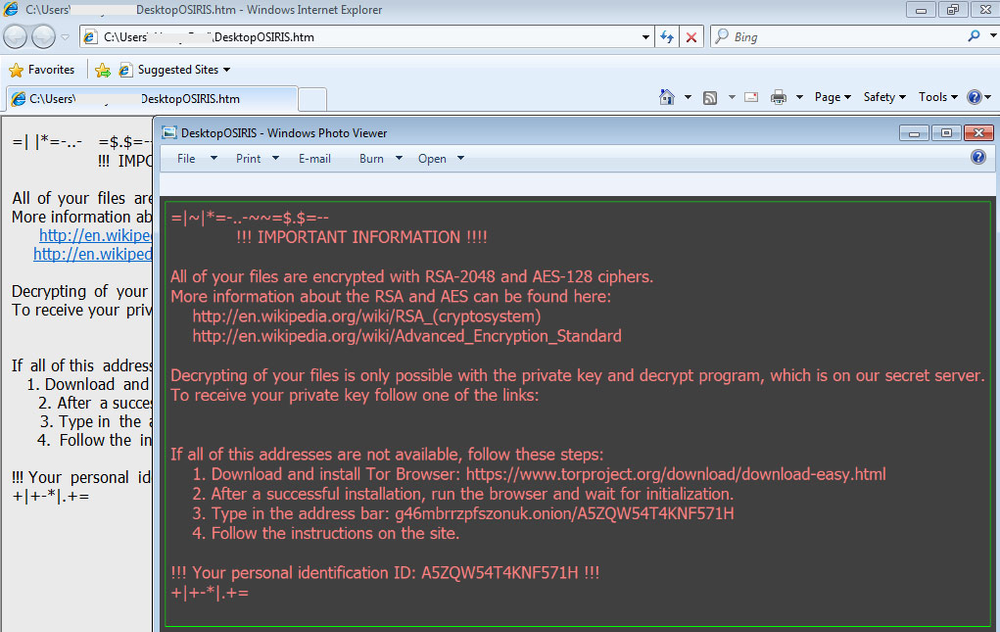
Once activated, Osiris immediately starts encrypting files and then displays the ransom note using the default browser such as Firefox:
firefox.exe -osint -url "%USERPROFILE%\DesktopOSIRIS.htm"
Osiris messages demanding the ransom.
Can Osiris detect virtualization?
It appears that the VM detection mechanism introduced in July 2016, did not produce expected results. In Osiris the authors supposedly improved the logic by replacing GetProcessHeap() function with GetOEMCP(), updated the criteria of virtualization detection based on CPU cycles (20 instead of 10), and increased the number of checks (from 1 to 2). Also they changed criteria of VM detection, decreasing difference of execution time in virtual and physical environments from 10 to 3 times.
VM detection is supposed to prevent security firms from testing this ransomware inside a virtual machine. The algorithm, however, is not effective, as Acronis Security Team was successful in performing tests in a virtual environment. Function pseudo-code is below:
BOOL passNewImprovedVMCheck()
{
unsigned __int64 tsc1;
unsigned __int64 tsc2;
unsigned __int64 tsc3;
BOOL firstPassResult;
BOOL secondPassResult;
int i = 0;
// Try this 20 times fighting with fluctuations (older Locky variants used 10 times) - the first pass, the older Locky had only 1 pass
for (i = 0; i < 20; i++)
{
tsc1 = __rdtsc();
// This function execution should be faster than CloseHandle on the physical machine
GetOEMCP();
tsc2 = __rdtsc();
// This function execution should take more time than GetOEMCP on the physical machine
CloseHandle(0);
tsc3 = __rdtsc();
// Did it take at least 3 times more (was 10 times more in the older Locky variants)
// CPU cycles to execute CloseHandle than it took to execute GetOEMCP()?
if ( ( LODWORD(tsc3) - LODWORD(tsc2) ) / ( LODWORD(tsc2) - LODWORD(tsc1) ) >= 3)
firstPassResult = TRUE;
}
if (!firstPassResult)
{
// The consistent small ratio of difference between GetOEMCP and CloseHandle execution times - so we're probably in a VM!
return FALSE;
}
// Do the second pass
...
if ( ( LODWORD(tsc3) - LODWORD(tsc2) ) / ( LODWORD(tsc2) - LODWORD(tsc1) ) >= 3)
secondPassResult = TRUE;
}
if (!secondPassResult)
{
// The consistent small ratio of difference between GetOEMCP and CloseHandle execution times - so we're probably in a VM!
return FALSE;
}
return TRUE; }
Ransomware attacks on backup
To prevent victims from restoring files from backup without paying the ransom, Osiris disables Volume Shadow Copy Service (VSS). This technology included in Microsoft Windows and allows taking manual or automatic backup copies or snapshots of computer files or volumes, Osiris also deletes already created shadow copies by running command “vssadmin.exe Delete Shadows /All /Quiet” in quiet mode. This action prevents users from performing a system restore from the saved data on the infected computer.
Microsoft VSS doesn’t contain security measures to protect itself and created shadow copies from deletion or alteration. Acronis predicted such attacks against the backup solutions and implemented self-protection techniques in its own products. Independent tests prove that Acronis efforts have been successful!
How to protect your systems against Osiris ransomware
Manual “decryption” of Osiris files is difficult and only possible if the users has backups that hadn’t been also encrypted.
Acronis Active Protection™ has been confirmed to successfully protect computer systems against Osiris ransomware. The innovative, patent-pending ransomware protection technology introduced in Acronis True Image 2017 New Generation is based on behavioral heuristics and easily detects and stops Osiris ransomware activity. It also allows the user to instantly recover any affected files.
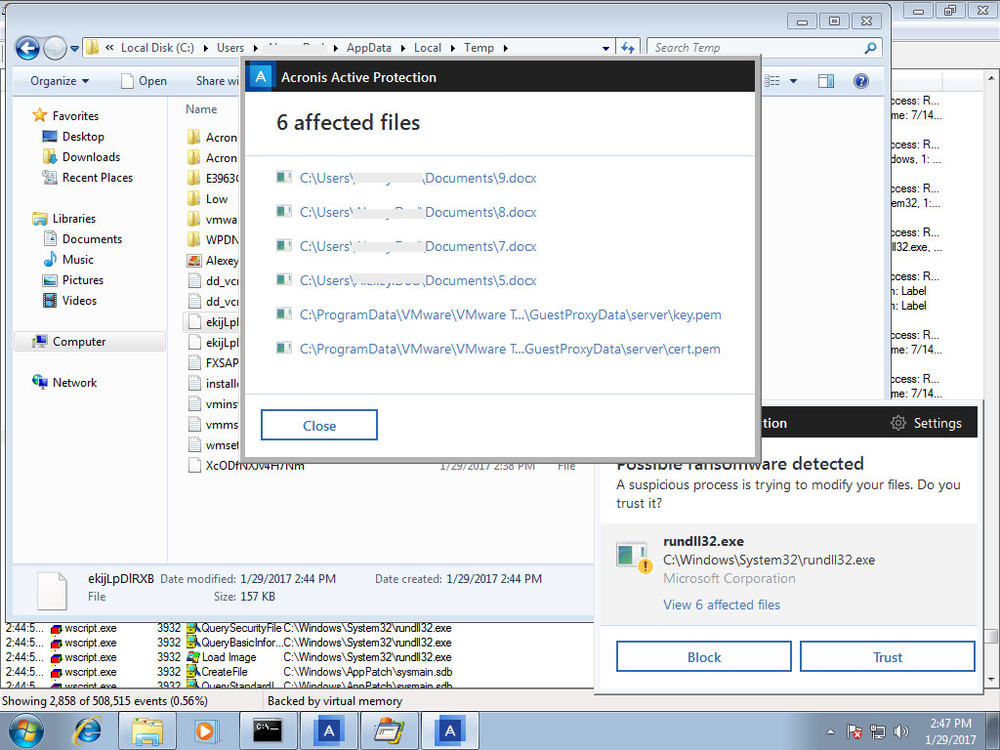
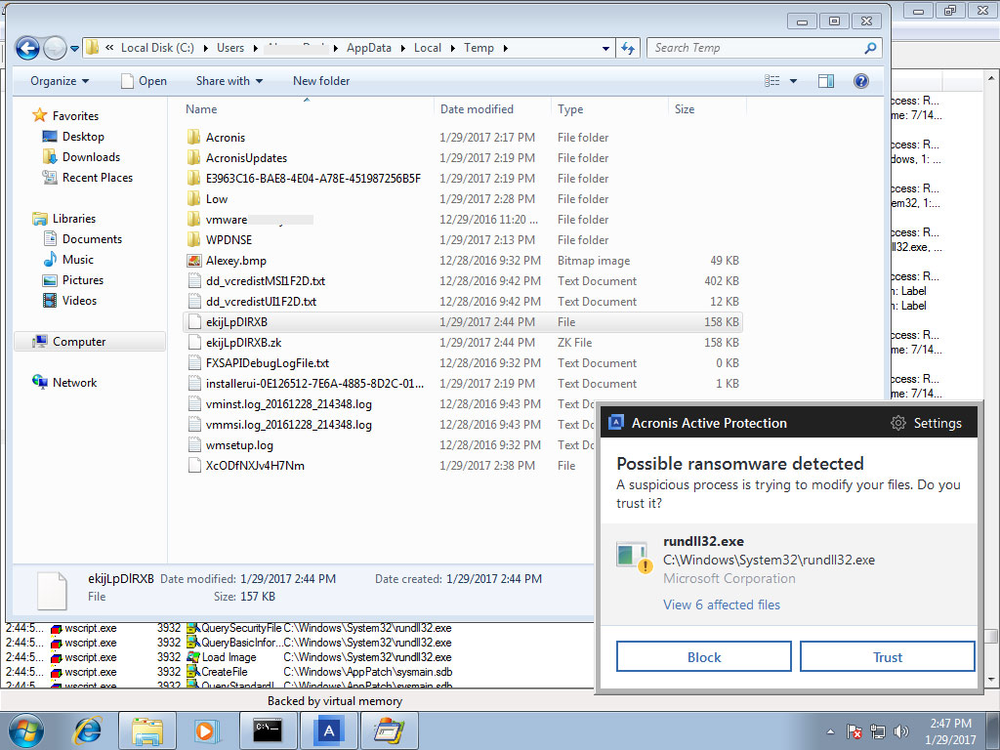
Osiris ransomware is detected on a computer running Acronis True Image 2017 New Generation with Acronis Active Protection enabled.
The screenshot shows that the attack was stopped, but 6 files have already been encrypted.
The 4 files encrypted by .osiris ransomware
All files are Instantly Restored to their original state by Acronis Active Protection™ without any ransom paid.
Can you afford to lose 8 years of data to Osiris?
This variety of Osiris ransomware is believed to be responsible for the infection of Cockrell Hill Police Department in Texas that led to the loss of eight years of critical evidence data.
In a public statement, the police department said the malware arrived "from a cloned email address imitating a department issued email address" and after taking root, requested 4 Bitcoin in ransom, worth about $3,600 today, or "nearly $4,000" as the department put it, The Register reported. The data was lost because the department did not have an appropriate
In other news, ransomware crooks attacked the Romantik Seehotel Jaegerwirt hotel on the Alpine Turracher Hoehe Pass in Austria, hacking their electronic key system and locking hundreds of guests in or out of their rooms until the ransom was paid.
Can you afford to become the next victim of the Osiris ransomware?
Protect your systems now! To find out how, please download Acronis Active Protection: Constant data availability in a changing threat landscape.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



