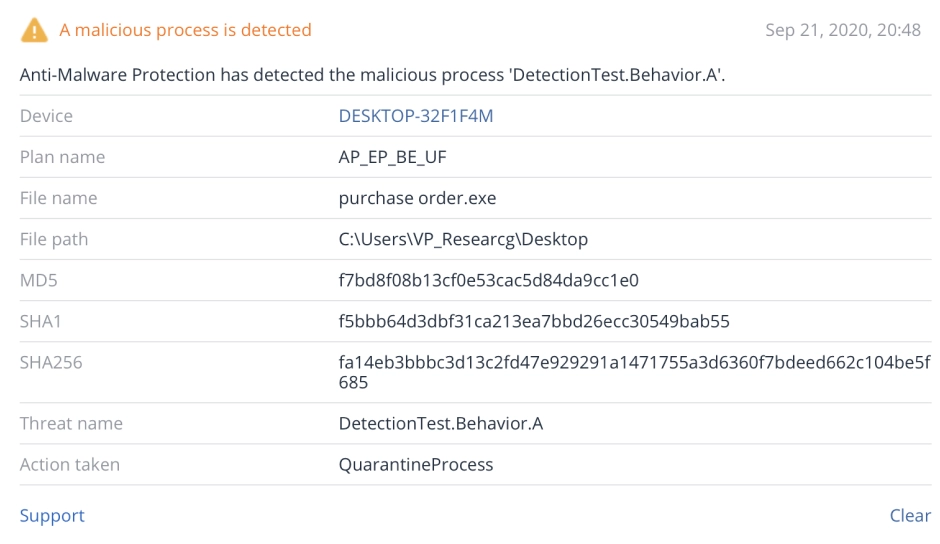
Technology
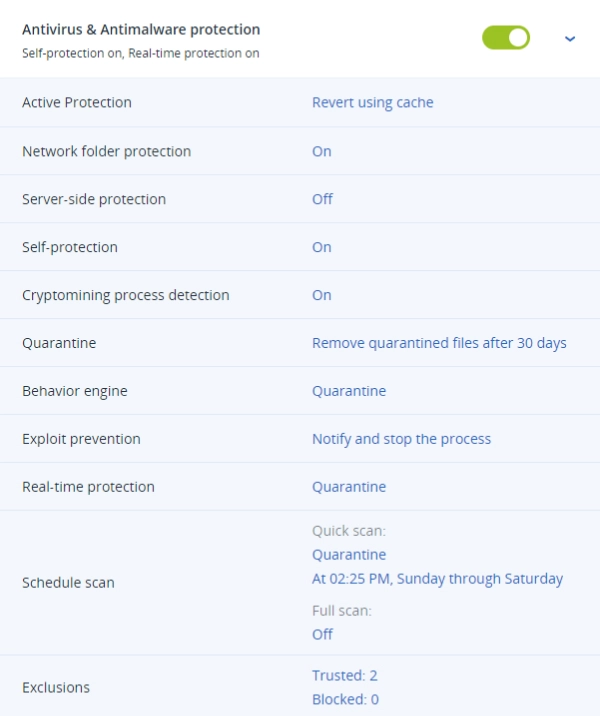
Anti Malware Advanced Protection
Acronis Cyber Protection Solutions deliver outstanding defense in depth (DiD) threat protection via a set of smartly integrated technologies, each of which works to prevent possible threats along dedicated stages.
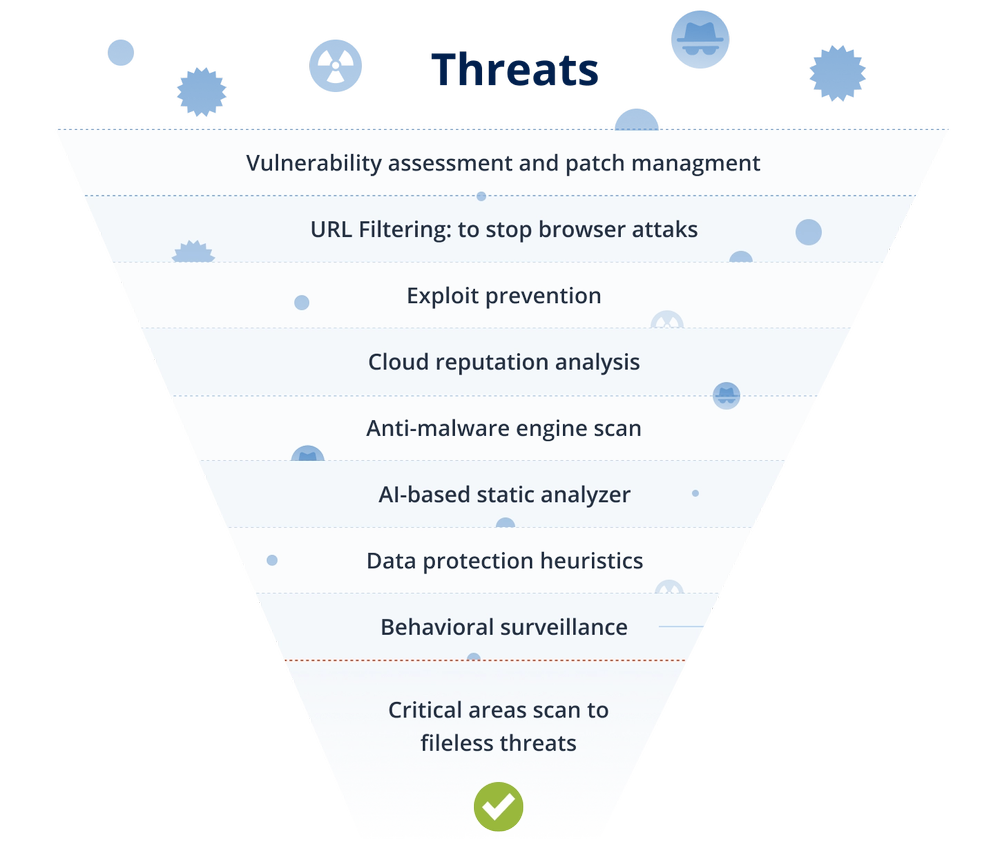
- Full stack protection technologiesContains AI-, behavior- and signature-based detection and response
- Security against any threatProtects against known/unknown malware and ransomware, and fileless attacks
- Combat emerging threatsUses behavioral heuristics and dynamic detection rules to combat emerging threats
- Detect any kind of malwareScans files for trojans, viruses, backdoors, worms, keyloggers, spyware, and others
What is malware?
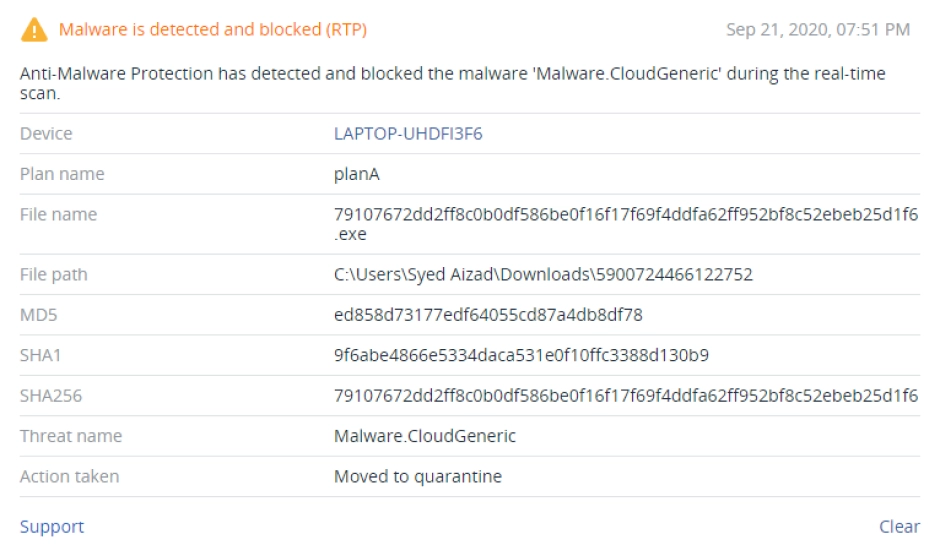
Malware is malicious software that is intentionally designed to damage a system or steal data. Malware is most often used by cybercriminals for financial gain, but can also be distributed as a form of protest or as an offensive weapon in the state-sponsored attacks that have become increasingly popular. Common forms of malware include viruses, trojans, worms, spyware, ransomware, botnets and any other type of potentially unwanted application.
- Damages a system or steals data
- Used by cybercriminals for financial gain
- Includes viruses, trojans, worms, spyware, ransomware, etc.
Effectiveness proven by independent testing laboratories
- Stops drive-by downloadsIntercepts HTTP/HTTPS requests and stops attempts to silently download malware
- Blocks malicious websitesProtects against any phishing sites and blocks sites that distribute malware
- Focus on current cyber threatsIdentifies scams using themes that leverage actual threats, such as COVID-19
- Extensive threat intelligenceIntegrates intelligence from industry partners into Acronis’ detection technologies
White paper
Acronis multilayered cybersecurity
Understand how Acronis uses multiple defense layers to prevent, detect, and respond to modern cyber threats.
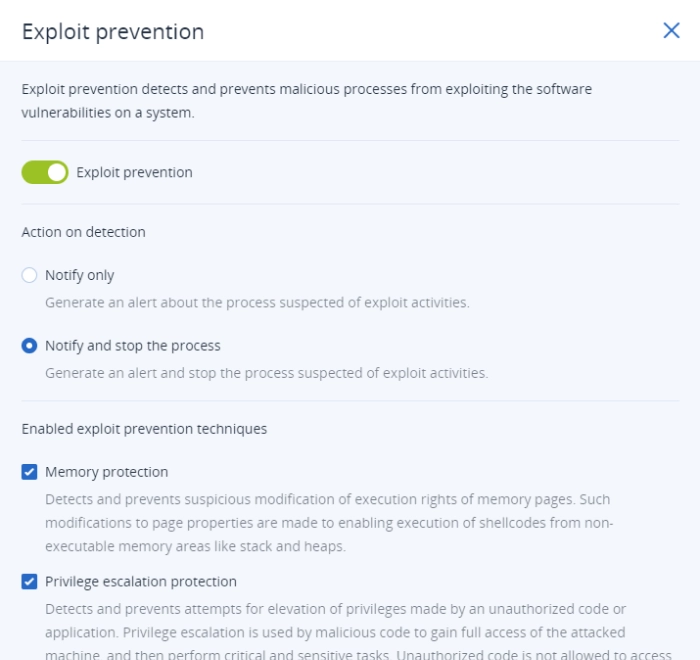
- Vulnerability patchingCovers unpatched vulnerabilities so dangerous malware can’t exploit them
- Protection against any exploitIs effective against every known exploit technique, including memory exploits
- Behavior-based exploit preventionA special set of behavioral heuristics that’s constantly updated by Acronis experts
- Prevent fileless exploitsWorks well against fileless attacks, that signature-based techniques can’t detect
- Globally updated signaturesFaster access in every region due to Acronis data centers located around the globe
- Nearly-instantanenous updatesNew detections are available for every customer within minutes of the first encounter
- AI-enabled data processingMore effective detection models, thanks to AI-enabled data processing
- Zero false positivesIncreased accuracy of false free verdicts due to allowlisting, sandboxing, etc.
- Machine learningHelps confirm malicious processes and injections into legitimate ones
- Static AI analyzerDetect malware triggered without execution
- Defense in depthDifferent models are used to effectively detect different threats
- Continous improvementNew models are tested every hour to improve efficiency and combat evolving threats
- Protection against any malwareExtends the power of Acronis Active Protection to address every type of malware link
- Powerful exploit preventionEffectively deals with fileless attacks and various exploit prevention techniques
- Dynamic detection rulesProtection against polymorphic and obfuscated malware
- Smart protection plansCan be updated at any moment to add protection against new, emerging threats
- Improved detection rateMore aggressive behavioral heuristics for more effective detection of malware
- Automatic allowlistingAutomatically allowlists applications for time-efficiency
- Manual allowlistingSupports manual allowlisting, if needed
- Zero false positivesProven zero false positives by independent third party tests
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.