If you don’t know what ransomware is, read on. You’re in danger of losing all of the files on your computer. Ransomware is a small piece of criminal software that highjacks your computer by encrypting your files, denying you access to them, and then demands online payment for their release. It’s one of the most shameless forms of cyber extortion, and in some cases, actual blackmail.
The threat is very real. If you use email, browse websites, spend time on social networks, connect to local networks (at work, at home, or in public spaces), or use removable USB drives, whether on a desktop, laptop, smartphone or tablet, you are always a click or two away from a ransomware infiltration. Prevent ransomware - don’t be a victim. Outsmart cyber-criminals with a few simple steps. It’s easy, but only if you know what to look for.
How do you get ransomware?
Ransomware is most commonly distributed by email, social network messages and infected websites.
Email phishing attacks
Most ransomware is distributed by the popular malware infection technique known as “phishing”, in which you receive an email that is designed to look like it comes from someone you know or should trust. The goal is to get you to open an attachment or click on a web link in the email, which then downloads malware like ransomware to your system. Criminals will study your social networks and other public information to learn details about you to make their phishing emails more believable, e.g., by discovering where you went to school and crafting a message that looks like it comes from your alumni association. Here’s a real-life ransomware example:
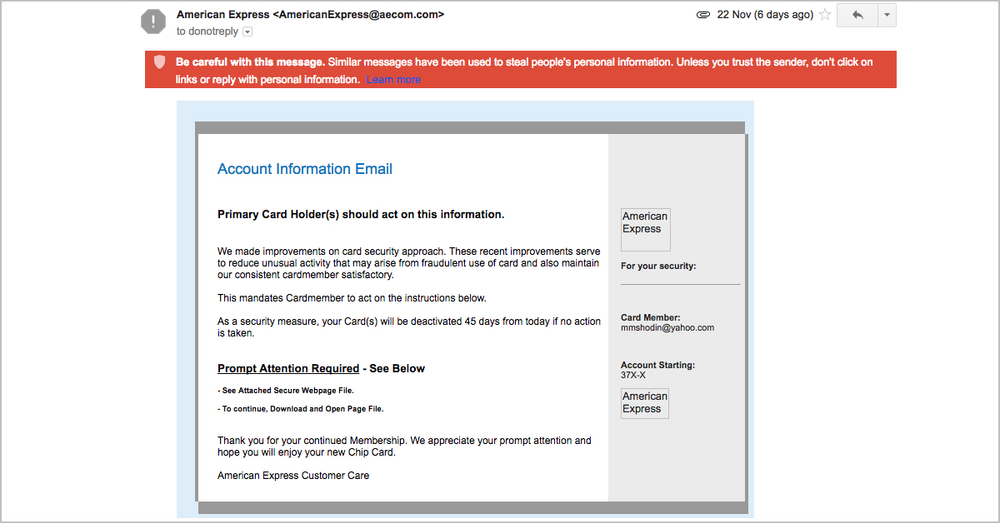
Image 1. Ransomware email caught by Gmail spam filter. Please note the “Prompt Attention Required” heading with a directive to open the attached file.
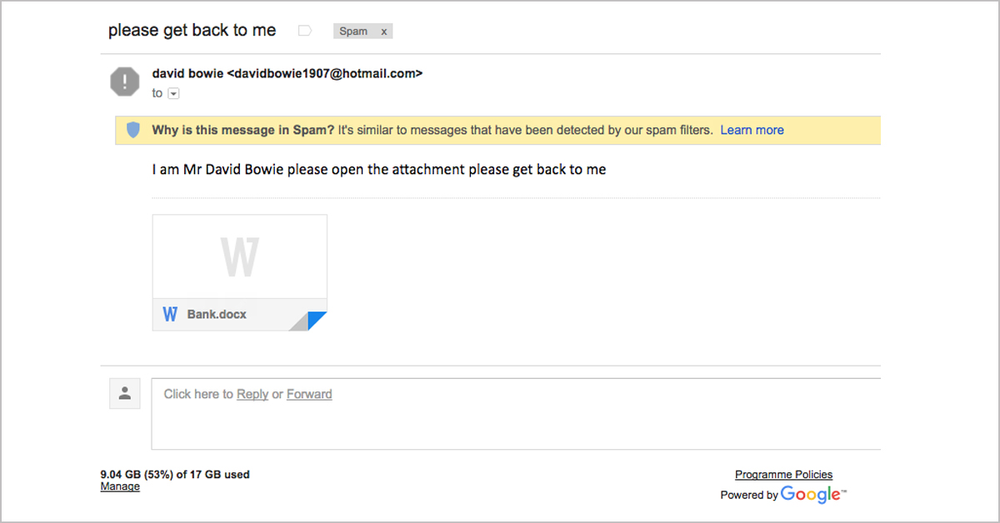
Image 2. Another ransomware email caught by Gmail spam filter. This email contains an attachment “Bank.docx” with Microsoft Visual Basic for Applications (VBA) macro code. When the attachment is opened, the enclosed malicious code executes, downloading and automatically installing ransomware on your system.
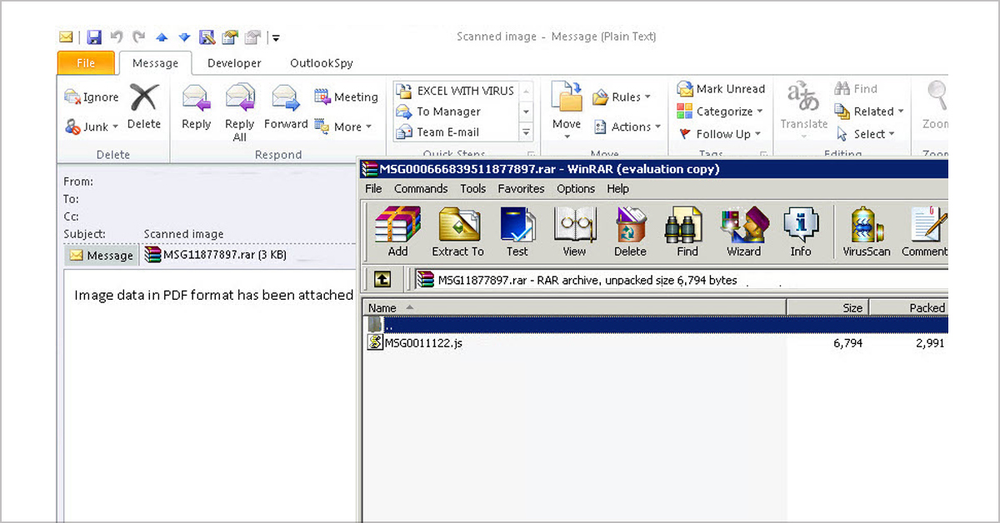
Image 3: Ransomware email in a desktop email client. It contains a compressed file with malicious JavaScript code. Depending on your email configuration, this file may already be inside your default Downloads folder. Extreme caution is required when browsing those files.
Social network ransomware attacks
One of the many new techniques that ransomware gangsters are using to distribute their malicious wares includes the use of social network and instant messaging apps.
For example, criminals may send you a Facebook Messenger post that includes a graphics attachment with the commonly-used .SVG file name extension. SVG files look legitimate to the Messenger app and your browser’s white-list filtering, and so execute automatically when viewed in a standard web browser. Once opened, the file executes and redirects the reader to a website which invites the user to install a browser extension so that they can view a (fake) YouTube video. Installing this extension opens the door for a ransomware infection.
How can you prevent ransomware attacks on social media?
Be wary of installing software or browser extensions in response to social media posts and instant messages.
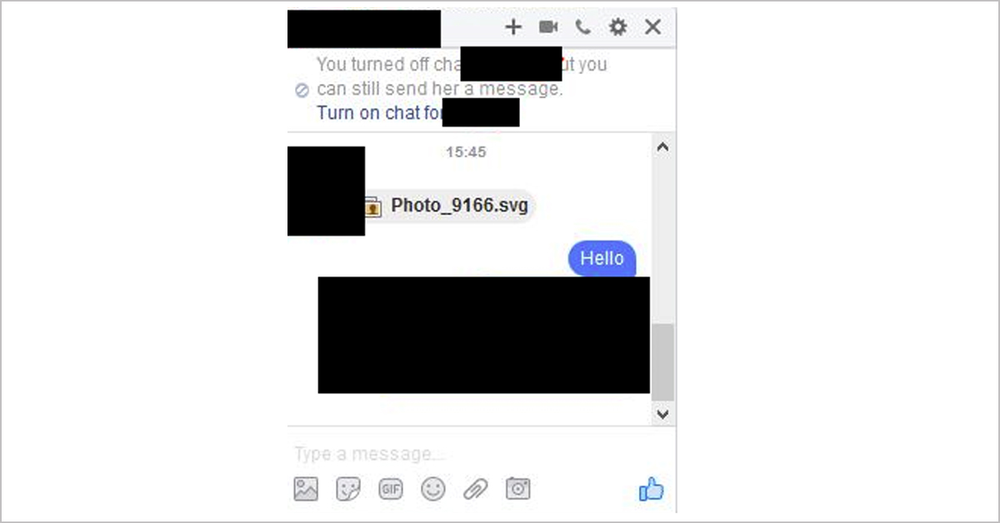
Image 4. Ransomware-infected .svg file sent through a social network messenger. Source: https://bartblaze.blogspot.com.au/2016/11/nemucod-downloader-spreading-via.html
Ransomware infected websites
Unprotected websites and unsecured web servers are another attack vector popular among ransomware gangsters. Cyber criminals look for websites with faulty code and insert ransomware distribution scripts into the web pages. If you see a warning similar to Image 5 below, it’s best to stay away from that website until the code is cleaned and the warning message goes away.
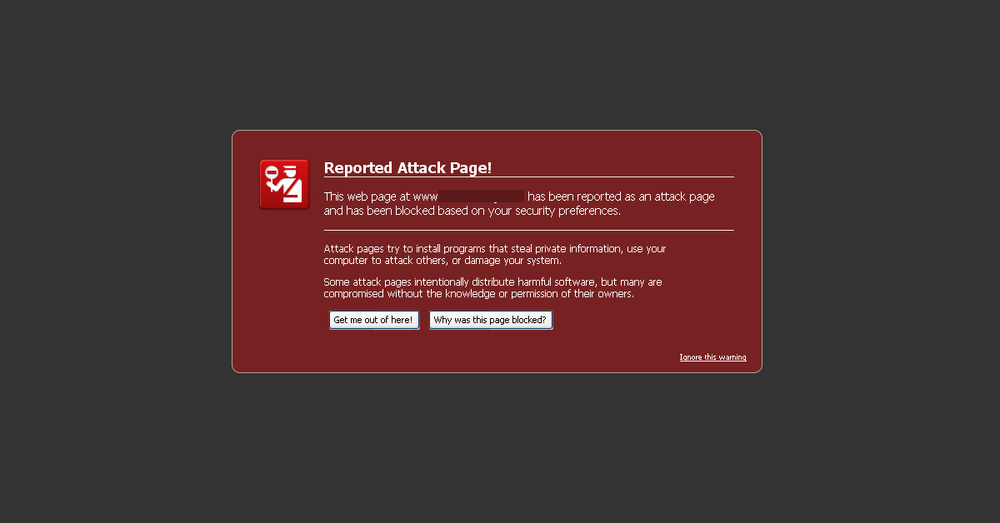
Image 5. A warning message preventing users from visiting an infected website.
What does a ransomware attack look like?
Ransomware is a well-developed one-billion-dollar criminal industry. There are many different types of ransomware, but most of them are similar in their execution:
- Ransomware file is downloaded to a user computer.
- Ransomware is installed on the computer — usually with the user’s help, e.g., opening an attachment or double-clicking a link as described above.
- Ransomware starts quietly encrypting the victim’s files (this can be either immediate, or delayed).
- When the file encryption process is complete, ransomware displays a ransom message with a countdown timer and instructions how to pay. Normally the victim is asked to download a Tor browser and make an anonymous payment using the online crypto-currency Bitcoin.
- Ransomware may also attempt to spread to other systems on the same network as the infected device, including local backup servers.
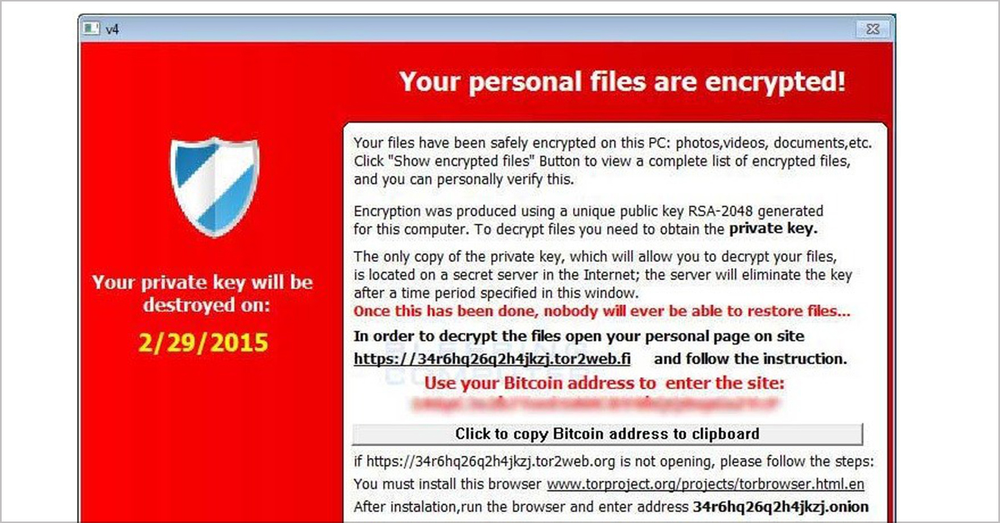
Image 6. CryptoLocker. CryptoLocker is one of the earliest ransomware types, the name has become synonymous with the entire concept of ransomware.
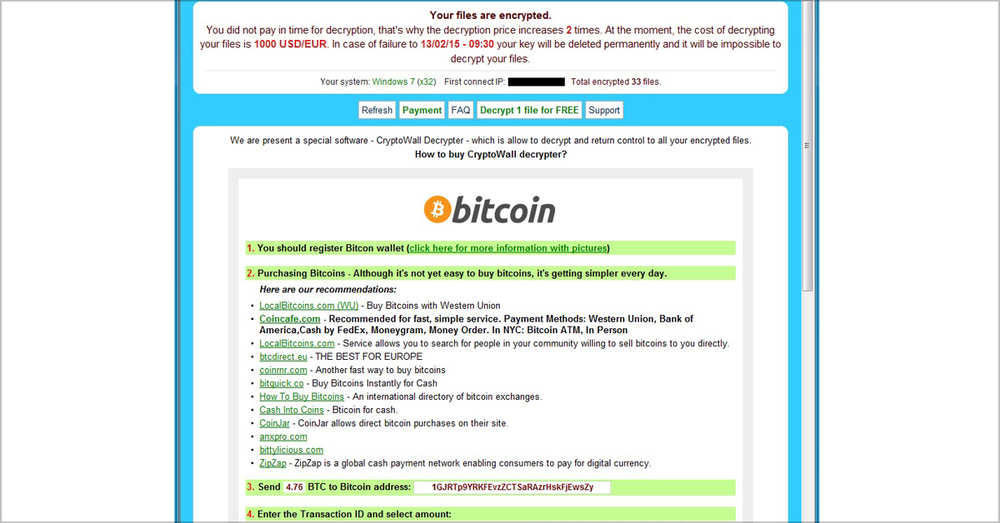
Image 7. CryptoWall. CryptoWall appeared in 2014 and has many different flavors, such as Cryptobit, CryptoDefense, CryptoWall 2.0 and CryptoWall 3.0.
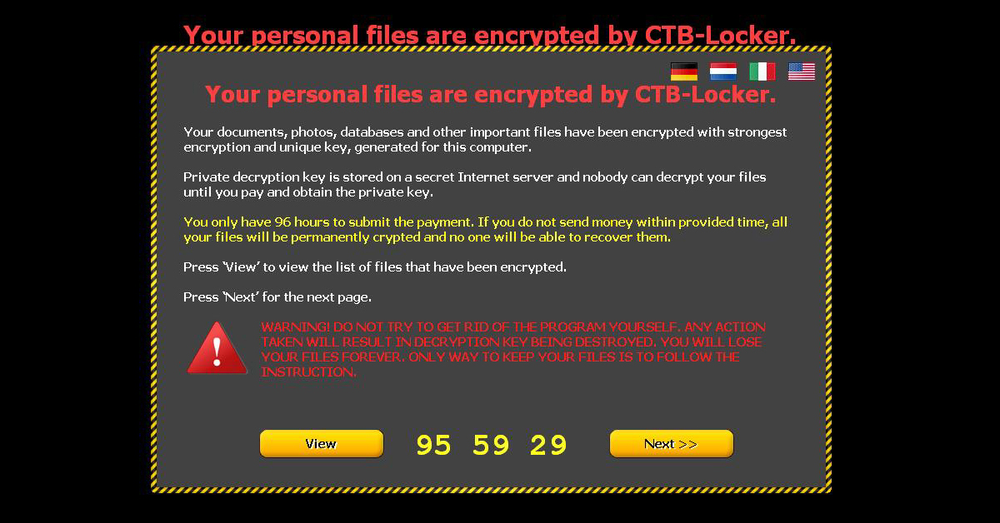
Image 8. CTB-Locker. CTB-Locker is mainly distributed through partners in exchange for a cut of the profits in a business model referred to as ransomware-as-a-service, reflecting how this method mimics the methods of the legitimate cloud software industry.
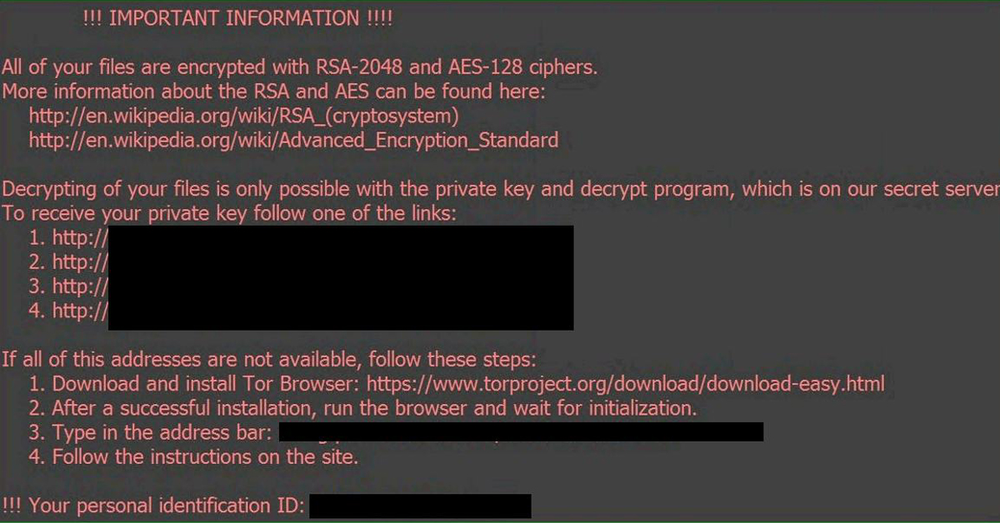
Image 9. Locky. Like many other viruses, Locky is spread in the form of an email message with malicious attachment disguised as an ordinary business file, personal photo, etc. When opened, the victim is instructed to enable macros, which in turn installs ransomware and starts the encryption process. The recently discovered Osiris Ransomware is an example of a Locky attack.
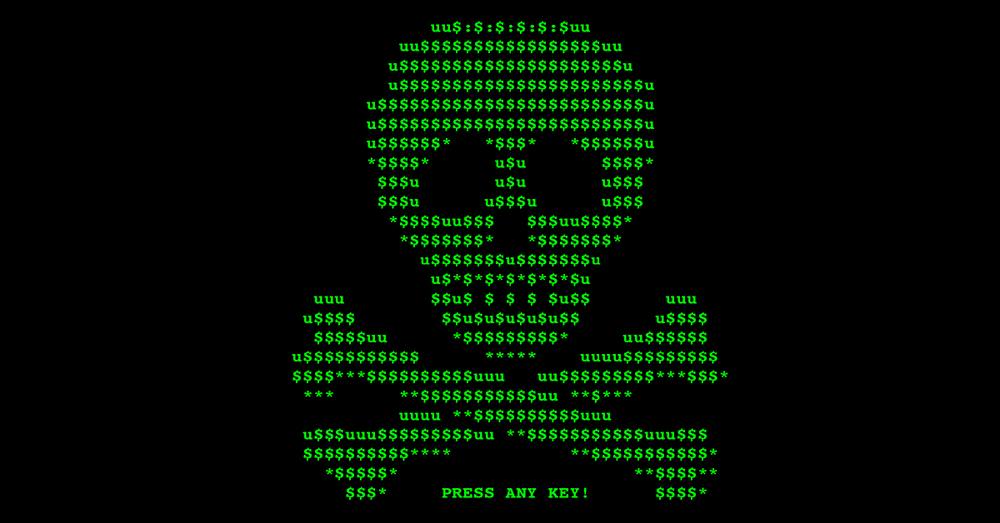
Image 10. Petya and Mischa. Petya and Mischa are often delivered to the user in one package. Petya locks up the entire computer by encrypting the Master File Table of the hard drive.
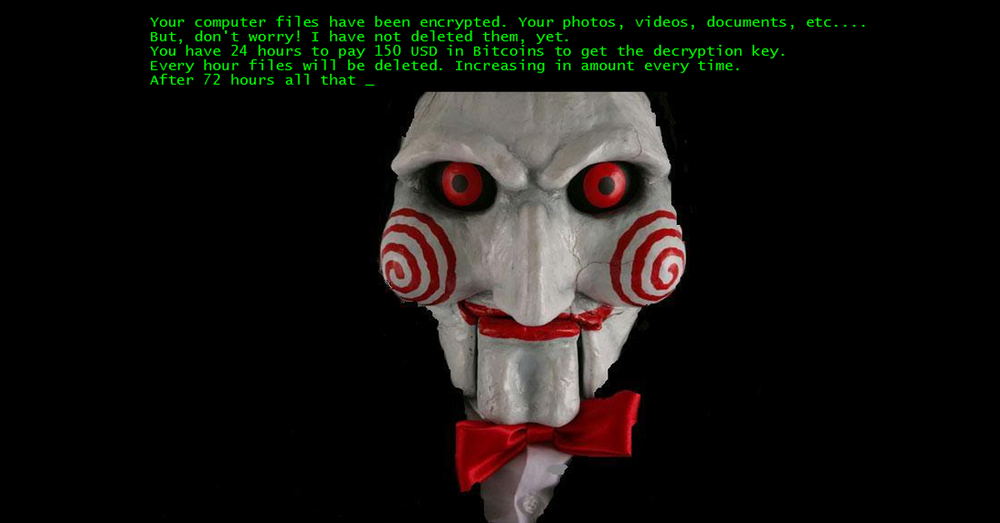
Image 11. Jigsaw. Jigsaw ransomware is setup to delete files one by one every hour until the ransom is paid.
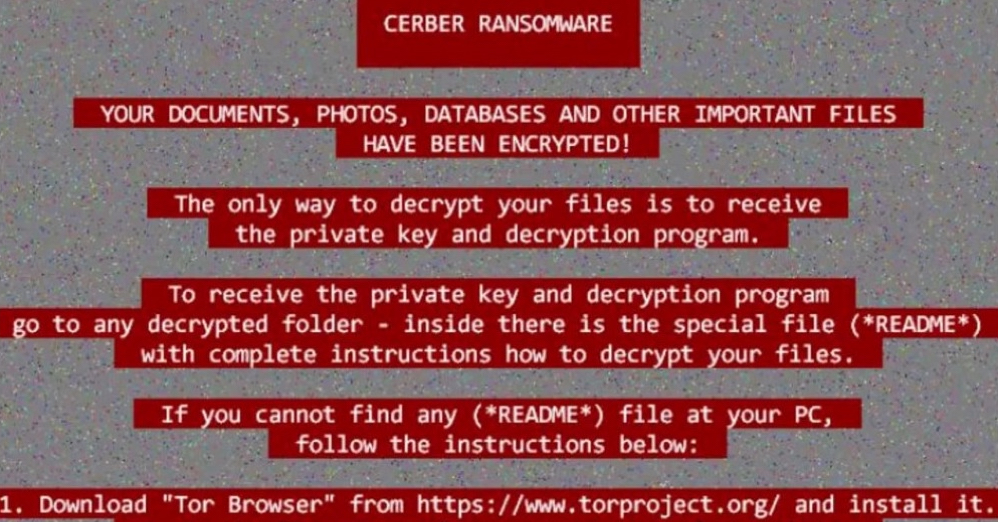
Image 12. Cerber. This type of ransomware is one of the most prominent early drivers of ransomware-as-a-service (RaaS).
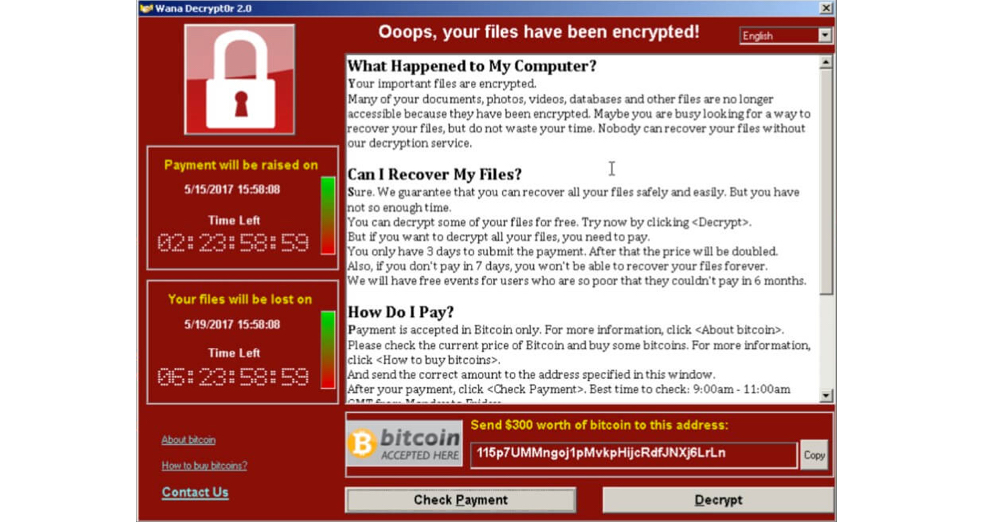
Image 13. WannaCry. WannaCry (also known as WannaCrypt, WannaCry, WanaCrypt0r, WCrypt, WCRY) exploited a Windows security vulnerability, infecting thousands of computers in more than 150 countries in May 2017.
What to do if you became a victim of a ransomware attack?
If you have become the victim of a ransomware attack, you have very few options:
- Restore your system from a backup.
- Format the hard drive to wipe out all data and then re-install the operating system and applications. You lose all of your personal data, may face costly additional licensing fees to restore your old software environment, and still face the threat of future ransomware attacks.
- Pay the ransom and hope that your data will be restored. (There are no guarantees that paying up will restore your files.) Some ransomware gangs don’t deliver the promised decryption key. Others may be caught by authorities, or disappear before they can deliver on their end of the ransom bargain.
What is the best way to protect your computer from ransomware?
Until an active protection technology becomes commercially available, backup (with a copy of backup data stored in the cloud) is the only sure way to recover your data after a ransomware attack without paying the ransom.
Run full image backup with Acronis True Image. If your system is compromised, you’ll be able to restore the entire system at once, without going through files one by one.
Ransomware poses a real threat to every computer user and every device connected to the internet. Get educated, be vigilant, and spread the world with your friends and family. Don’t be fooled, and protect your data with backup.
UPDATE Jan 20, 2017
On January 18, Acronis True Image 2017 New Generation with Acronis Active Protection™ feature was released. The innovative product received the GOLD Self-Protection Award from Anti-Malware Testing lab. The new feature provides users with a new level of ransomware protection as it detects first symptoms of new and known ransomware attacks, making the backup more secure, and reducing the number of times data needs to be restored from the backup.
READ MORE:
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



