The ALPHV ransomware variant, also known as Noberus, was first identified in November of 2021. Threat actors describe it as a next-generation ransomware-as-a-service (RaaS) version that includes four encryption modes and two encryption algorithms (AES and ChaCha20). ALPHV is true cross-platform malware and affects operating systems such as Windows, ESXI, Debian, Ubuntu and ReadyNas.
On March 16, 2022, security specialists identified a new version of BlackCat ransomware (so named because the software displays a black cat on the victim’s payment site). These experts also noted that some previous YARA rules no longer match, which will make it difficult to find malicious files.
Technical Details
Like the previous version of ALPHV, BlackCat is written in the Rust programming language and is not packed or obfuscated and is executed via a command line or PowerShell with necessary options.
Users can access a full list of options by executing the ransomware with the “--help” parameter. See below.
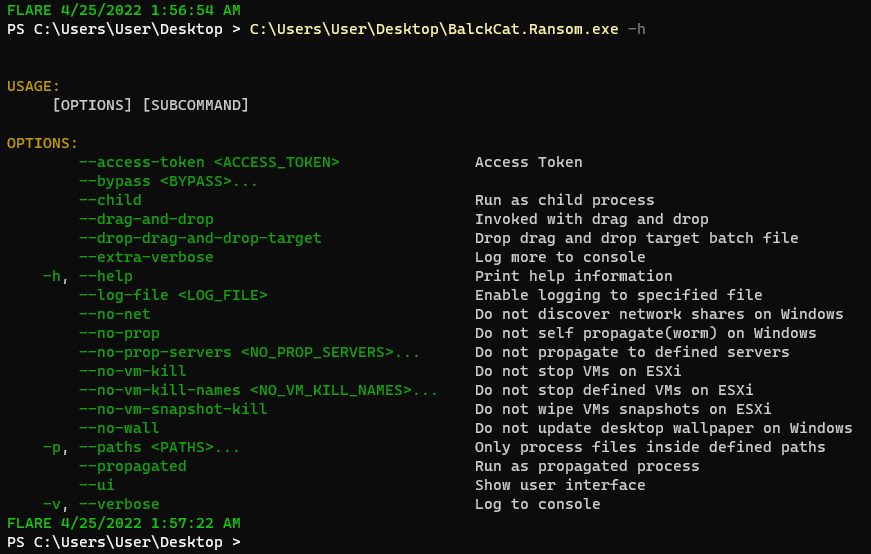
What’s New in BlackCat?
While BlackCat shares many similarities and capabilities with ALPHV, it does include many new functions. These include:
· --bypass
· --drag-and-drop
· --drag-and-drop target
· --extra-verbose
· --no-prop
· --no_vm_kill
· --no-vm-kill-names <NO_VM_KILL_NAMES>
· --no-vm-snapshot-kill
· --no-wall
BlackCat includes more functions that previous versions, and in addition, the configuration file is not embedded into the sample anymore. Instead, threat actors manually drop the configuration file into a victim’s environment.
How is BlackCat Executed?
BlackCat must be executed using the following order: --access-token <ACCESS_TOKEN> [OPTION] [SUBCOMMAND].
Similar to ALPHV, with BlackCat, the encryption process won’t start without the access token and produces an error message if users attempt to execute it.
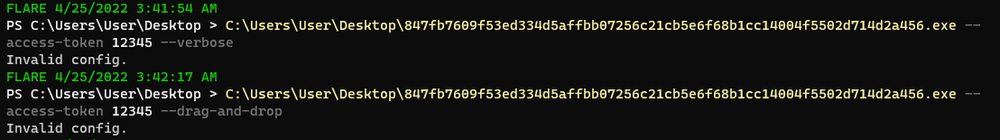
By viewing this sample statically, we can observe the similarity in the preparation process. To execute all commands, BlackCat uses the “cmd/c” string and the “Wevtutil.exe” Windows utility to obtain access to the event logs.
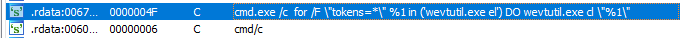
From there, BlackCat obtains the Machine GUID from the registry and UUID using the wmic command:
· SOFTWARE\\Microsoft\\Cryptography
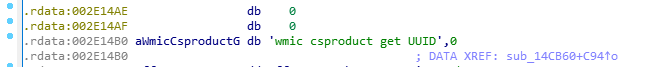
It uses the “fsutil” system utility to enable “remote-to-remote” and “remote-to-local” symbolic links:
· fsutil behavior set SymlinkEvaluation R2R:1
· fsutil behavior set SymlinkEvaluation R2L:1
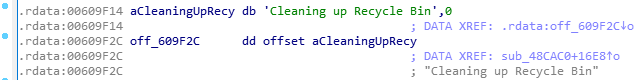
BlackCat deletes all volume shadow copies with the “vssadmin.exe” utility and empties the recycle bin.
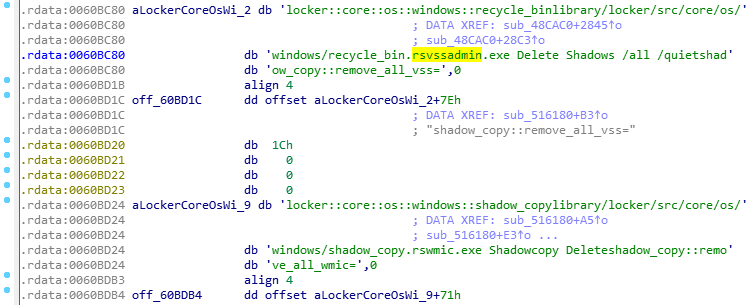
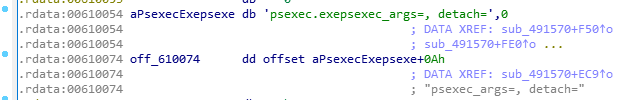
Also, BlackCat uses the “PsExec” utility, which is compressed with zlib and is stored in the sample. This utility enables users to execute programs on remote Windows machines.
It changes the maximum number of simultaneous outstanding client requests to the server by writing the maximum possible value (65535) to the “MaxMpxCt” parameter in the register.
· reg add HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\LanmanServer\\ Parameters/v MaxMpxCt /d 65535
File Encryption
When it comes to file encryption, BlackCat looks for all available volumes on the computer by obtaining their path names.
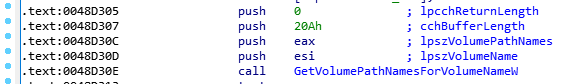
If the found volume doesn’t have a path name, it will be mounted.
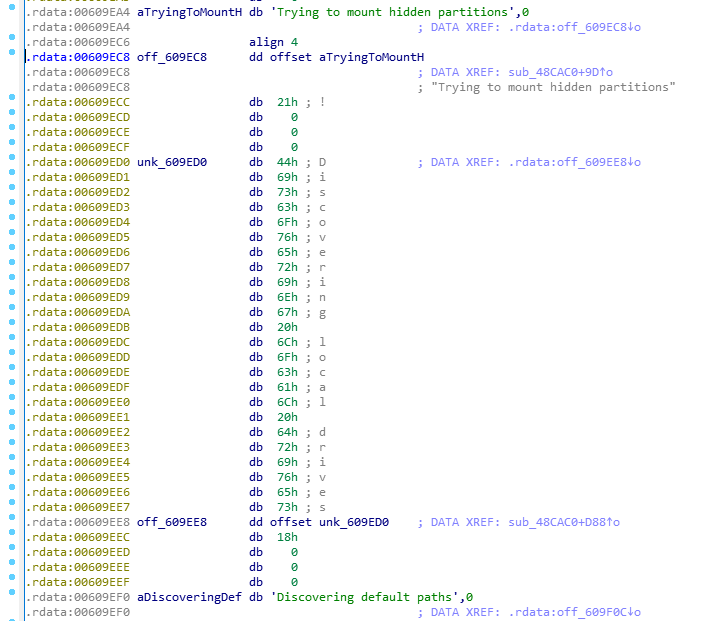
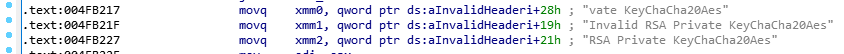
From there, BlackCat starts to search files using the “FindFirstFile” and “FindNextFile” functions. Like the previous version of ALPHV, BlackCat encrypts files with the AES encryptions algorithm and uses the hardware-supported instructions “aeskeygenassist,” “aesenc,” and “easimc.”
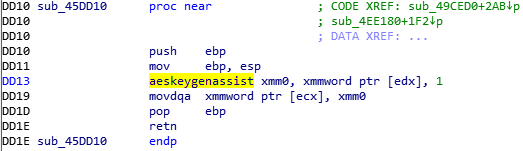
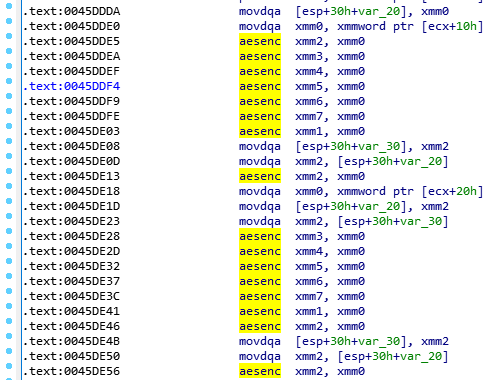
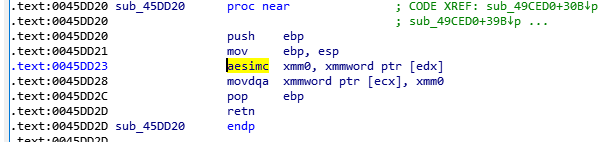
If AES is not supported, BlackCat will use the ChaCha20 encryption algorithm.
Conclusion
While BlackCat is a new version of ransomware, it does use functionality similar to that of the previous ALPHV version. For example, it still uses AES and ChaCha20 encryption algorithms; includes the packed “PsExec” utility; abuses the “fsutil” utility; searches the computer’s hidden partitions to mount it; changes the same registry keys; clears the recycle bin; and deletes shadow copies via “vssadmin.exe.”
However, the new version does not contain configuration, so it can be executed without it —functionality that makes it more difficult to analyze. Additionally, the old YARA rules that applied to the previous version do not work with the new version of BlackCat.
All of this makes it even more important to use the most effective anti-malware solutions possible. These solutions should be capable of identifying any cyberthreat ― even those they’ve never seen before so they can immediately shut them down before harm can be done.
Interested in learning more? Please visit our anti-malware site now or request a brief, no-obligation demo today.
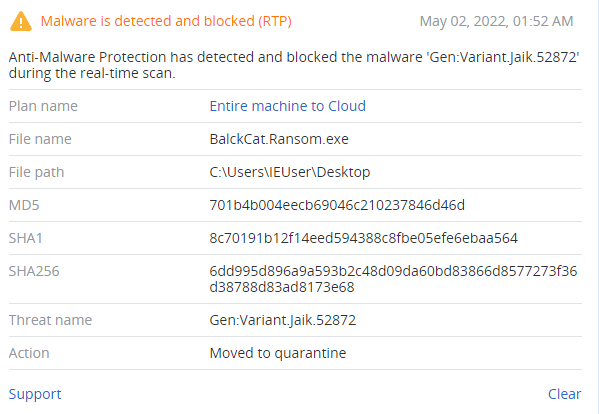
Detected by Acronis
IoCs
Files




