Summary
- Use targeted attacks to hack into corporate networks of Israeli companies
- Attackers released 110 GB of data from H&M Israel, and 9 GB of data from the shipping company Veritas on their leak site
- Employs a client-server model for encrypting computers on target networks
- Supposedly connected with the Iranian operators of the ransomware Pay2Key
Attack vectors and recent targets
On Sunday, May 2, сybercriminal group N3TWoRM attacked the computer networks of the international clothing network H&M in Israel and threatened to release customer data. This was reported by the Israeli magazine Haaretz, which previously mentioned attacks on at least four Israeli companies and one non-profit organization.
Typically, these attackers gain network access either via spear-phishing emails with a malicious attachment or by purchasing RDP access credentials on the dark web.
The N3TWoRM gang set up a data leak site where they threatened — if the victims don't pay the demanded ransom — to publicly release 110 GB of data from H&M Israel and 9 GB of data from shipping company Veritas, including customer, account, employee and possibly billing information.
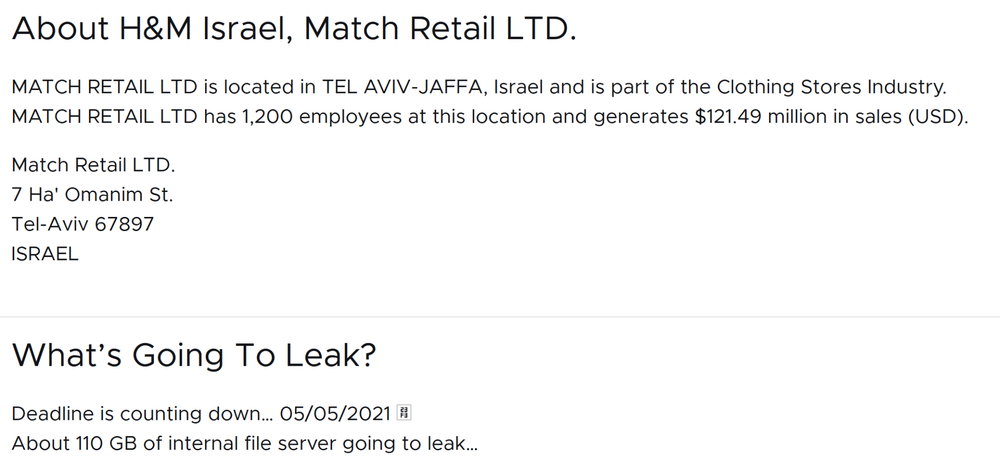
According to BleepingComputer, the group has already published the data stolen during the attack on Veritas.
Haaretz reports that the attackers demanded a ransom of 3 bitcoin (approximately $120,000 at the time of writing) to delete the stolen Veritas data, while a source from BleepingComputer gives the figure of 4 bitcoin (approximately $160,000).
Israeli cybersecurity sources speculate that ransom is not the primary goal of these cybercriminals — that they are in fact politically motivated, and want to undermine and damage Israel's status as a prominent cyber force. Experts reached these conclusions in part on N3TwoRM’s supposed connection with the Iranian operators of Pay2Key ransomware, which last year announced the hacking of Israel Aerospace Industries and the Israeli information security company Portnox. At the moment, though, N3TWoRM attacks have not been associated with other hacker groups.
The stolen data has since been published, indicating that these companies didn’t pay the ransom.
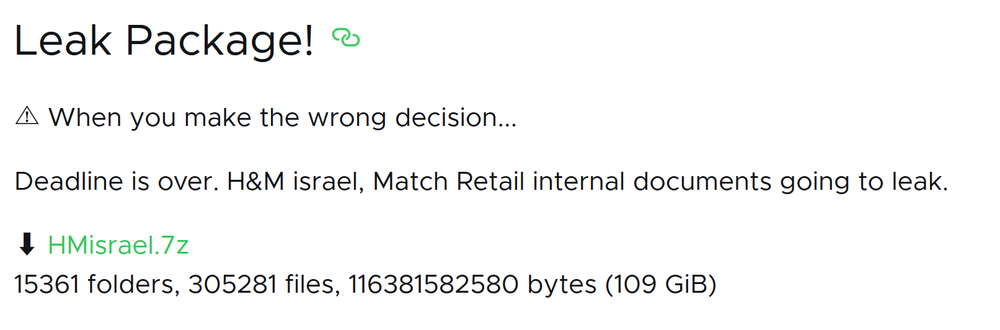
The hackers recently published information about one more victim from Israel — Ecolog Engineering Ltd., a private consulting and design firm specializing in environmental impact assessments.
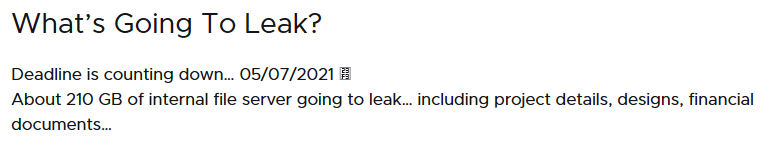
Self-defense
The ransomware employs the collection of anti-debugging techniques, using string encryption with XOR, Windows API to check for the presence of a debugger, checking for debugging flags, triggering unhandled exceptions, using a performance counter and so on.
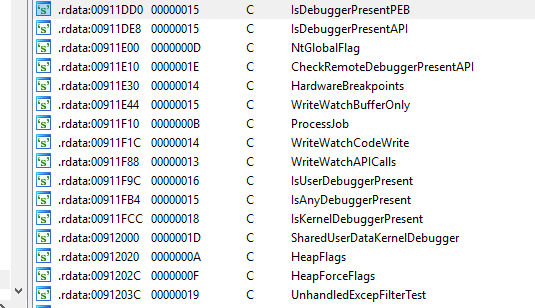
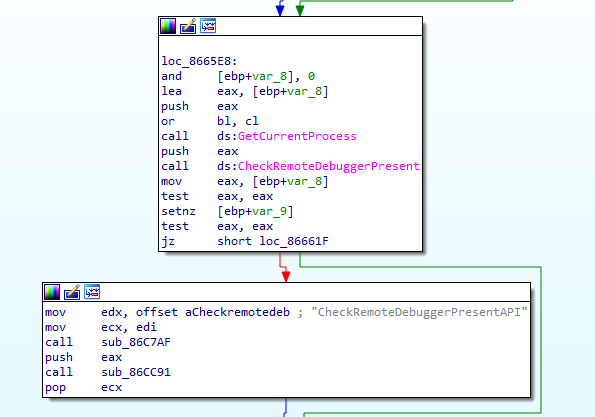
If debugging is detected, the ransomware shuts down the system.
Encryption
If we consider the principle of the ransomware attack, N3TWoRM has an unusual client-server encryption model.
Typically, attackers distribute a standalone ransomware executable to every device they want to encrypt. From discussions with Nachmias researchers, the N3TWoRM attacks use a different approach to encrypt data: a program is installed on the victim's server in order to listen for connections from connected workstations.
Once executed, ‘slave.exe’ sends to the server its RSA key, which will be used to encrypt the file encryption key. After that, it receives the command to start encryption.
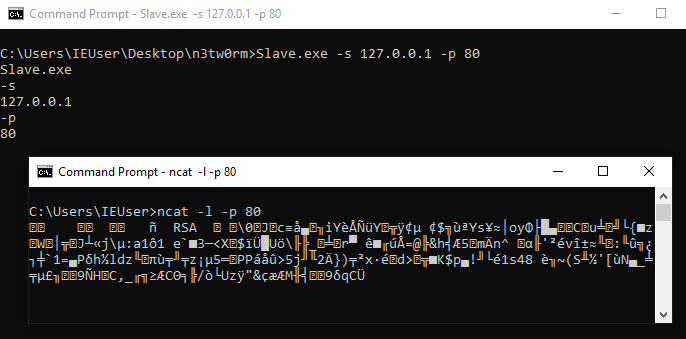

The Hackers use PAExec to deploy and run the ‘slave.exe’ client on all encrypted devices. Encrypted files ware given the “.n3tw0rm” extension.
Wiping free disk space
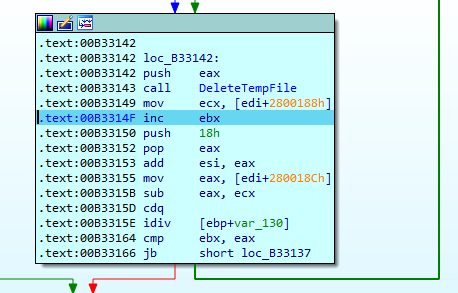
To prevent restoration of deleted files, the ransomware uses an interesting technique. It launches a so-called “free space worker” that creates many temporary files on network drives and fills them with zeros.
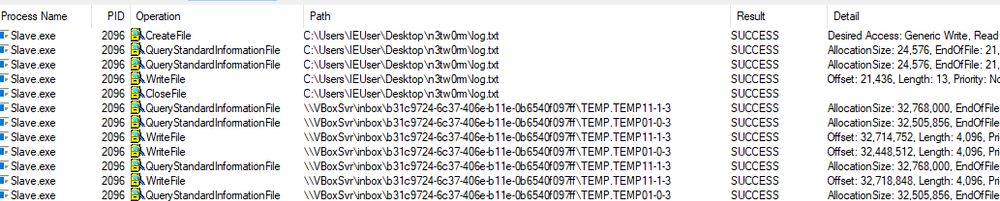
After all available space has been filled with temp files, the free space worker deletes them. In doing so, network drives are effectively wiped clean.

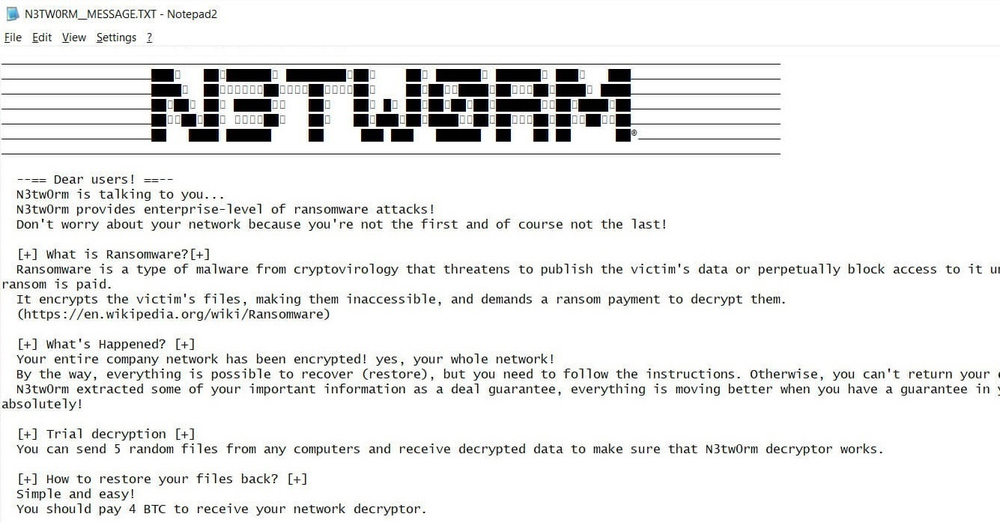
Ransom note
The ransom note looks as follows, and contains contact and payment information:
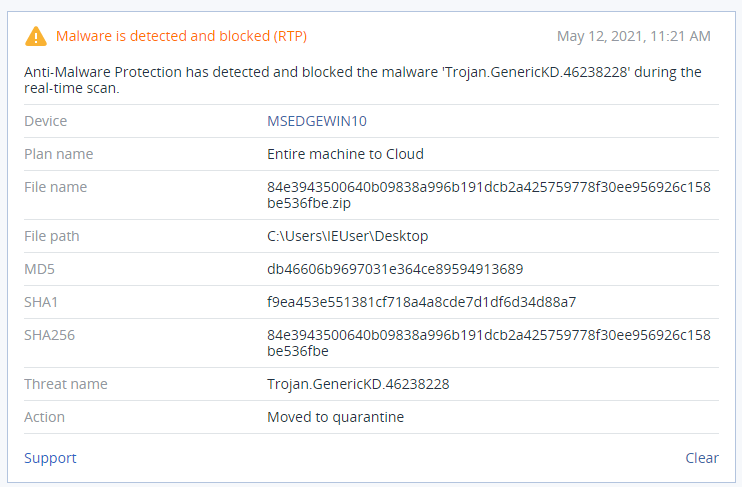
Detection by Acronis
The N3tw0rm ransomware is successfully detected by Acronis.
Conclusion
Some cybersecurity researchers believe that N3TWoRM belongs to Iranian hacker groups and is used to attack vulnerable systems. This ransomware has so far been used exclusively against Israeli companies and users.
IoCs
SHA256: 8c6fd14084820ec528749300222097d21197659535aaa50cdcc75831f73546c1



