Summary
- Ranzy Locker ransomware was first discovered in October 2020
- Ranzy Locker is an upgraded, rebranded version of ThunderX ransomware — which was obsoleted when a free decryptor was released
- Uses Salsa20 encryption algorithm with RSA-2048 encryption
- Kills AV processes and recovery services
- Performs anti-debugging checks
- Deletes data backups
Introduction
While its current name may be fairly new, Ranzy Locker is simply the latest evolution in a line of ransomware variants that began with MedusaLocker. Many of its details have since changed, including a shift in encryption algorithms from AES-256 to Salsa20. The distribution vectors for Ranzy Locker remain somewhat unclear, though spam campaigns have been indicated as one method.
The group behind Ranzy Locker operates a data leak site, simply called “Ranzy Leak,” to which exfiltrated sensitive data from infected systems is uploaded. If the victim refuses to pay the demanded ransom, the cybercriminals will publish this data publicly as retribution.
Pre-analysis
Ranzy Locker contains a manifest in which the requested execution level is set to Administrator. Since it requires administrative rights to launch, this malware doesn’t use any user account control (UAC) bypass techniques.
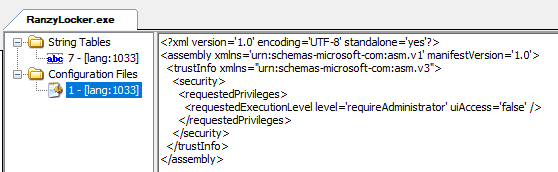
Another entry in the resource section contains the encrypted strings used during ransomware execution, including the configuration data.
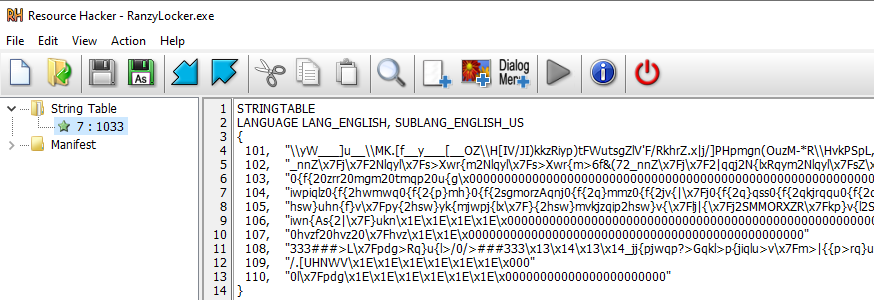
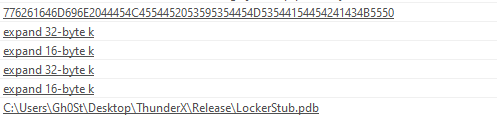
The strings point to the use of the Salsa20 encryption algorithm (or its modification and debug information), which connects Ranzy Locker with the previously-known ThunderX ransomware. For example:
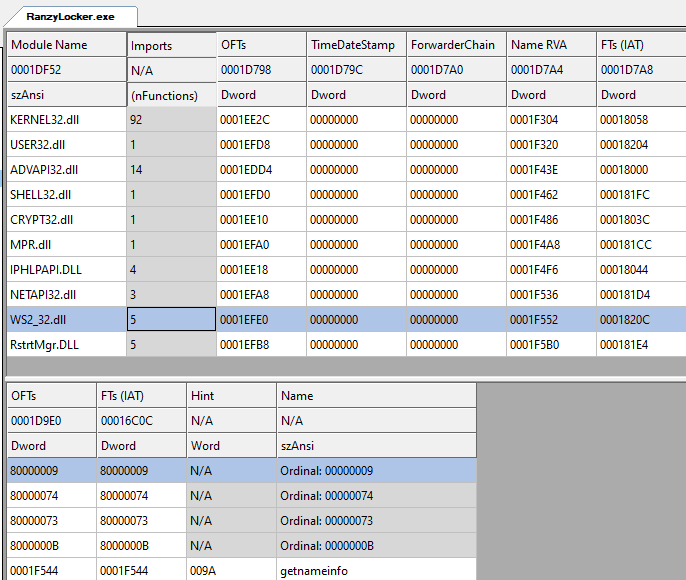
The executable imports DLLs used for networking, such as MPR.dll, NETAPI32.dll, IPHLPAPI.dll, and WS2_32.dll — which indicates network communications such as command and control traffic or the encryption of the network shared drives.
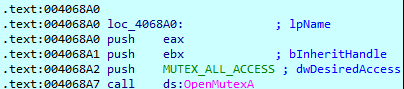
When started, Ranzy Locker tries to open the mutex “Global\35355FA5-07E9-428B-B5A5-1C88CAB2B488” in order to verify if another instance of the ransomware has already run (in which case execution of the current process will be stopped).
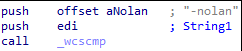
The ransomware can be launched with command line argument “-nolan” to skip encryption of the network shared drives.
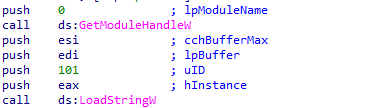
After the mutex is created, Ranzy Locker performs anti-debugging checks (as described in the next section) and retrieves each string from a manifest file specifying the string’s unique identifier.
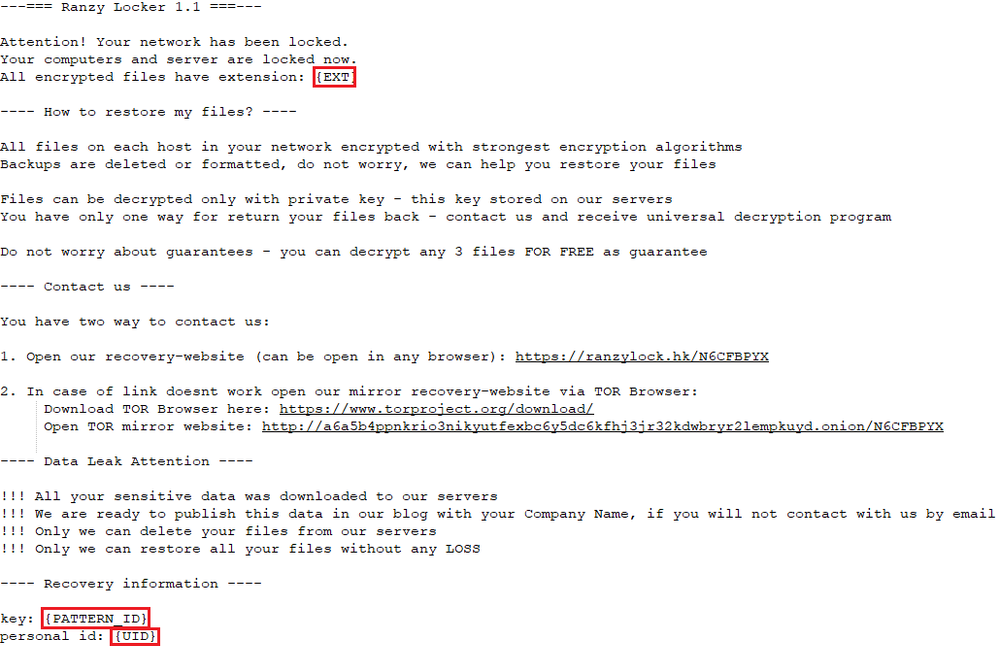
Every string is converted to multibyte characters and XORed with “0x1E.” The decrypted strings comprise the master RSA-2048 public key, a denylist of processes and services specified for encryption, an allowlist of directories and file extensions exempted from encryption, a ransom note without specified {EXT}, {PATTERN_ID} and {UID}, the .ranzy file extension. and “10EKVPIH” as a unique target identifier.
The ransom note template:
Anti-debugging checks
The ransomware performs three checks to detect an attached debugger and hardware breakpoints.
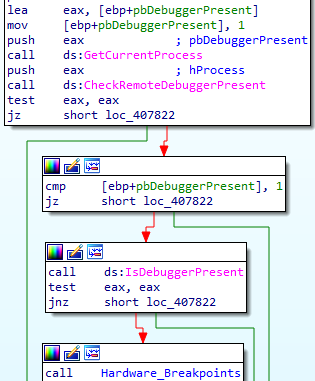
The first and second checks, CheckRemoteDebuggerPresent() and IsDebuggerPresent(), attempt to detect the debugger’s presence. CheckRemoteDebuggerPresent() checks whether the process is being debugged separately while IsDebuggerPresent() supposes that the process is run under a debugger.
The third check reviews a thread context for values in four debug registers that contain addresses of the hardware breakpoints. It is possible to set no more than four hardware breakpoints per thread.
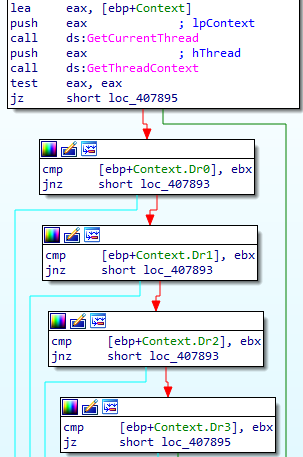
In the event that one of the checks fails, execution will be terminated.
Termination of processes and services
Ranzy Locker defines 30 processes and 12 services, retrieved from the encrypted resources section, to be terminated. This closes additional critical files so that they can be encrypted by the ransomware.
Ranzy Locker takes a snapshot of all running processes in the system using CreateToolhelp32Snapshot().
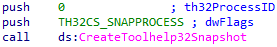
The malware uses Process32FirstW() and Process32NextW() to enumerate the processes. If the current process is included in the denylist, the locker opens the process and terminates it.
The denylist includes the processes of databases such as SQL and Oracle, and office applications including text processors and email clients.
Next, Ranzy Locker enumerates services from the denylist and tries to stop them using the code snippet taken from MSDN. The malware retrieves a handle to the specific service and queries its status using QueryServiceStatusEx() with SC_STATUS_PROCESS_INFO. The received buffer contains the _SERVICE_STATUS_PROCESS struct, where the second double word indicates the current state of the service — dwCurrentState.
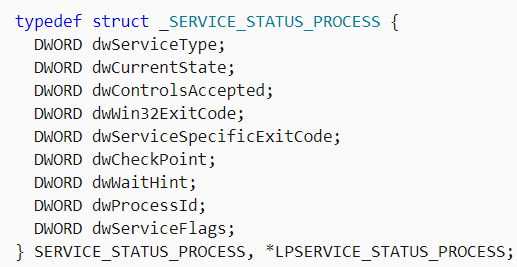
If QueryServiceStatusEx() fails or the service is already stopped, Ranzy Locker moves to the next service from the list. If the current state is SERVICE_STOP_PENDING, then the malware is waiting until the service is stopped.
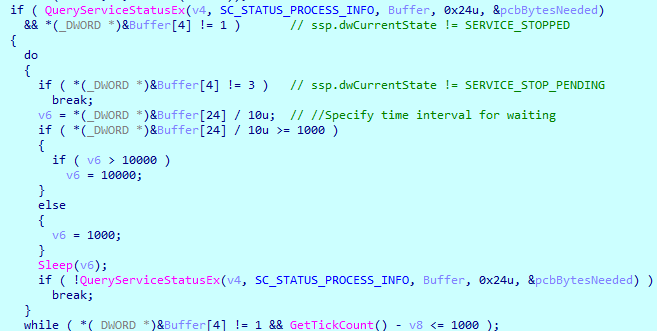
If the service is still working, the locker stops the dependent services by sending them a stop code. Finally, ControlService() dispatches a signal to stop the current service.
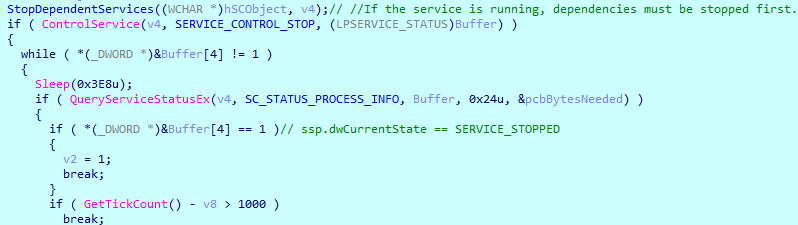
The ransomware aims to kill services related to Hyper-V, SQL database, Webroot, and ESET antiviruses.
Deletion of backups
Next, Ranzy Locker empties the Recycle Bin.
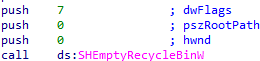
Ranzy Locker then executes the following commands five times:
wmic.exe SHADOWCOPY /nointeractive
wbadmin DELETE SYSTEMSTATEBACKUP
wbadmin DELETE SYSTEMSTATEBACKUP
-deleteOldest
bcdedit.exe /set {{default}}
recoveryenabled No
bcdedit.exe /set {{default}}
bootstatuspolicy ignoreallfailures
vssadmin.exe Delete Shadows /All
/Quiet
These commands are extracted from the encrypted strings in the resource section. Together, they delete shadow copies and system backups, disable recovery, and set the system to ignore all boot failures.
Encryption
To speed up the encryption process, Ranzy Locker uses an I/O port. First, it calculates the number of the parallel threads based on the number of logical processors.
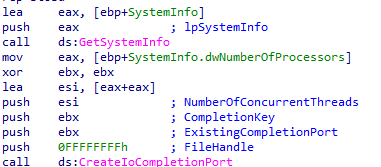
Once the I/O port is created, the ransomware uses GetQueuedCompletionStatus() and PostQueuedCompletionStatus() to operate with file encryption.
Ranzy Locker imports the master RSA-2048 public key stored in Base64 format, and passes it to CryptStringToBinaryA() to decode it:
BgIAAACkAABSU0ExAAgAAAEAAQDBVEWH1TW7uudLwgn7jXIkjmyDrH9X1LuvlD0fbt1CNVnsyp6QkdS34LBVhuNMnR2WZFpWcxdrMTOGxlnfnOc6SZFpDHmL4N+e915n0EIOkDg4xFPgRa4d/OPLWkHXHEsz/hggrJP+mGroIeelzeybIXpfoQYz4joKyKCAJSoUIpG9lyWEj04bxzz1BUpSJgV0x7qSY0ciek2YURuN68gZyeZzip9dCBPmBURT9B4lpgXrgIeJv5KjsC8Lo+vwRHPhrhXGf6OMrWZDrbabTIoKj27vhMaS4np2Gpu6Df0LC865eDiVJbDgJvbwx17Bw3zDvgajia/FFhe3MJ8gmHO+

After decoding, the RSA-2048 public key looks as follows:
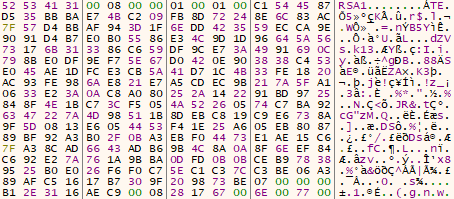
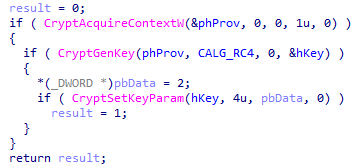
Ranzy Locker then randomly generates an RC4 key, but does not use it later in the execution chain. This might be a leftover artifact from previous versions.
The next step is the preparation of a {PATTERN_ID} value to be included to the ransom note, which is constructed with the following format:
{"ext":".ranzy","network":"true","subid":"14375","lang":"en-US."}
The values for the “ext,” “network,” and “subid” parameters are hardcoded and constant for the current malware sample, whereas language is determined using GetUserDefaultLocaleName(). The {PATTERN_ID} value is then encoded with Base64 and added to the ransom note.
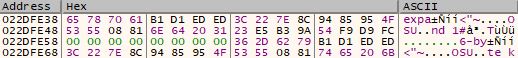
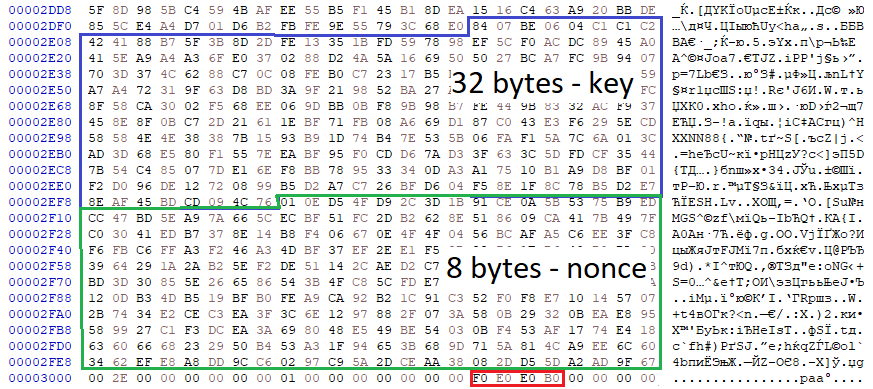
For each file, Ranzy Locker randomly generates 32 bytes used as a key and 8 bytes used as a nonce to autocomplete the matrix for Salsa20 encryption.
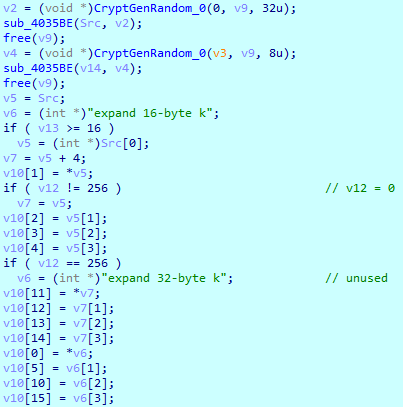
The following screenshot contains the generated 32 bytes used as the Salsa20 key:
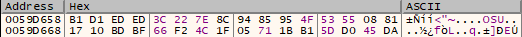
The following screenshot contains the generated 8 bytes used as nonce for Salsa20 algorithm:
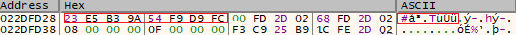
Ranzy Locker uses only the first 16 bytes of the key and is used to create the key matrix for the Salsa20 cipher. The initial state of Salsa20 looks as follows:
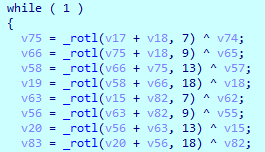
It uses Salsa20 in its traditional way with the default rotate positions.
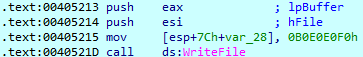
Later, the key and nonce are encrypted with RSA-2048 and stored in the file footer as well as “0x0B0E0E0F0” bytes.
Ranzy Locker defines two primary folders to start encryption:
C:\Program Files (x86)\Microsoft SQL Server
C:\Program Files\Microsoft SQL Server
The following folders and files are ignored during encryption:
The ransomware adds the .ranzy extension to the encrypted files. For example:
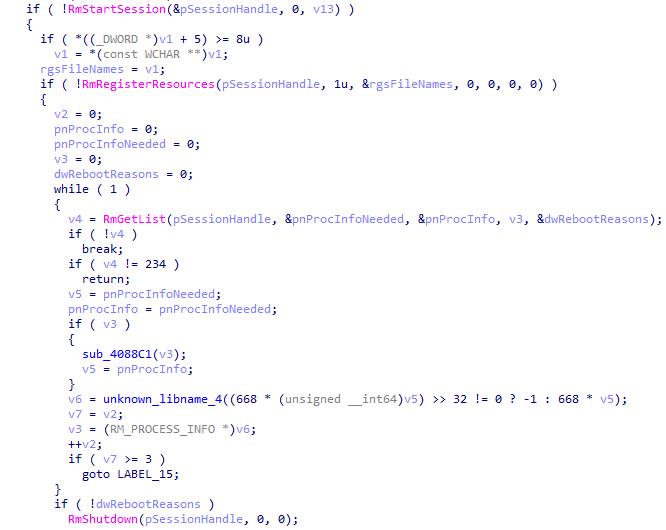
Ranzy Locker abuses Windows Restart Manager to forcibly terminate the processes and services that prevent files encryption.
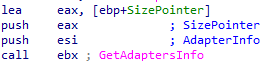
Ranzy Locker also looks for network shares to encrypt. First, it gets the IP of the current machine using GetAdaptersInfo().
Then, it enumerates the range of IP addresses in the current subnetwork (starting with the gateway IP address) and sends an IPv4 ICMP echo request. If the host is active and accessible in the local network, it answers with an echo reply.
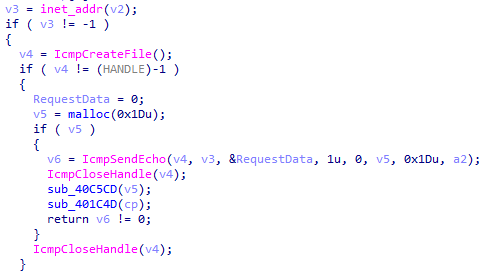
After the discovery of active hosts, Ranzy Locker retrieves shared resources and DFS namespaces associated with the host and encrypts them with the Salsa20 cipher.
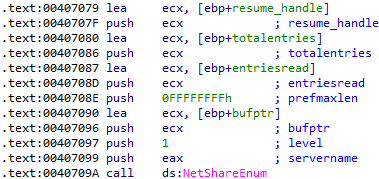
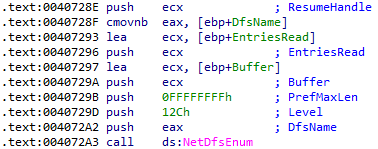
Ransom note
A ransom note with the name “readme.txt” is created in every folder, except for these mentioned in the allowlist. The note contains the version number for Ranzy Locker (currently 1.1) and links to the recovery sites.
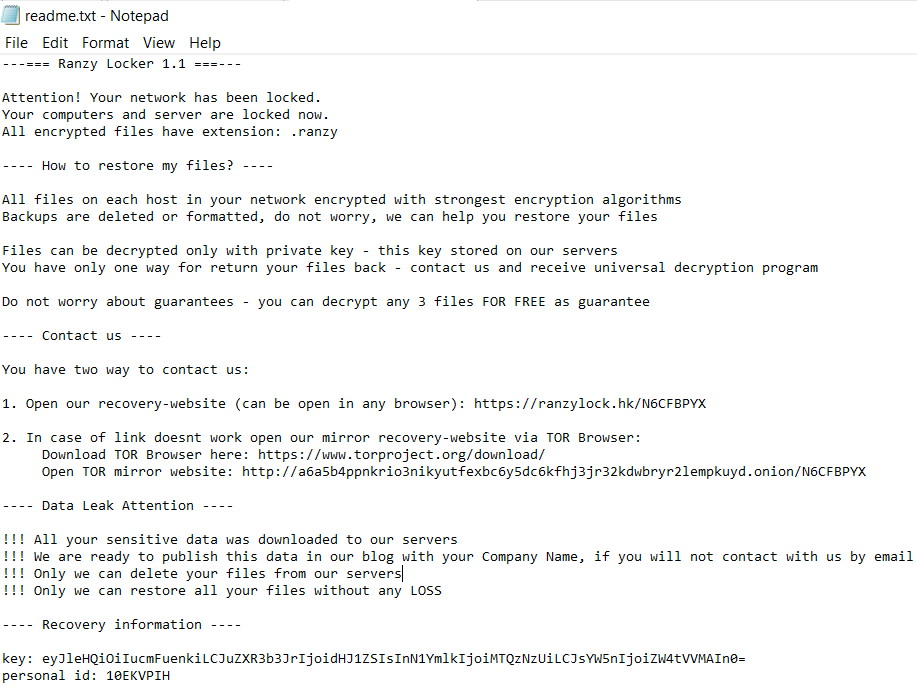
The attackers say that they’ve already uploaded the stolen data to their servers, in order to be able to publish it later on the leak site. This is a manual process carried out the by attackers before starting the ransomware — Ranzy Locker itself does not contain data exfiltration capabilities.
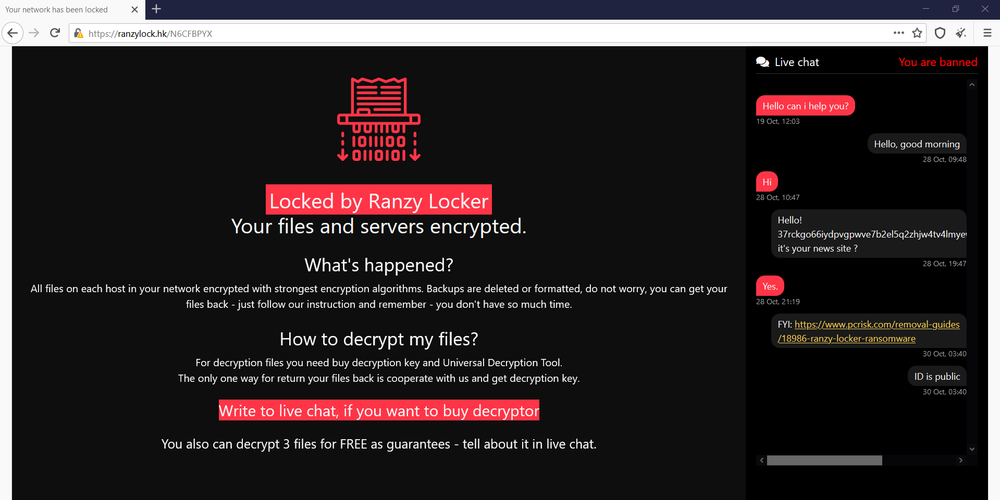
The decryption site can be accessed via the Web and Tor networks:
- https://ranzylock.hk/N6CFBPYX — for any users
- http://a6a5b4ppnkrio3nikyutfexbc6y5dc6kfhj3jr32kdwbryr2lempkuyd.onion/N6CFBPYX — for Tor users only
The decryption service appears as follows:
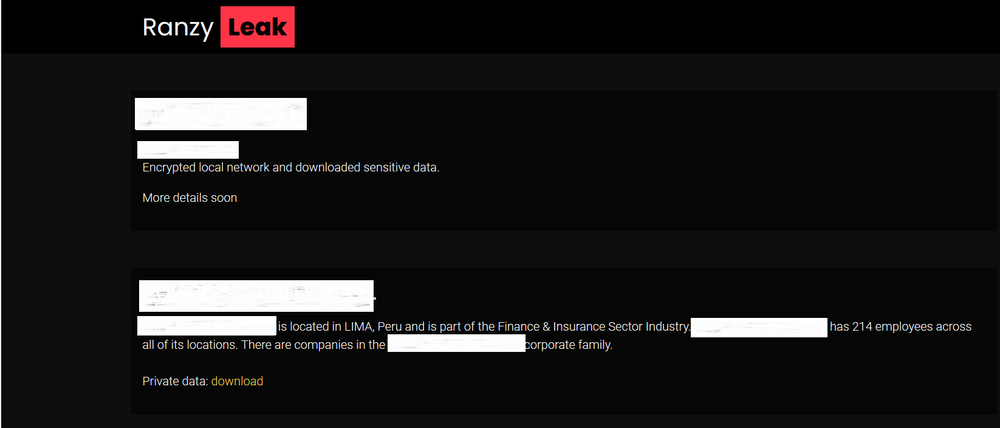
Ranzy Locker’s operators also have a leak site by the name of Ranzy Leak, where stolen data is published when victims refuse to pay the ransom.
http://37rckgo66iydpvgpwve7b2el5q2zhjw4tv4lmyewufnpx4lhkekxkoqd.onion/
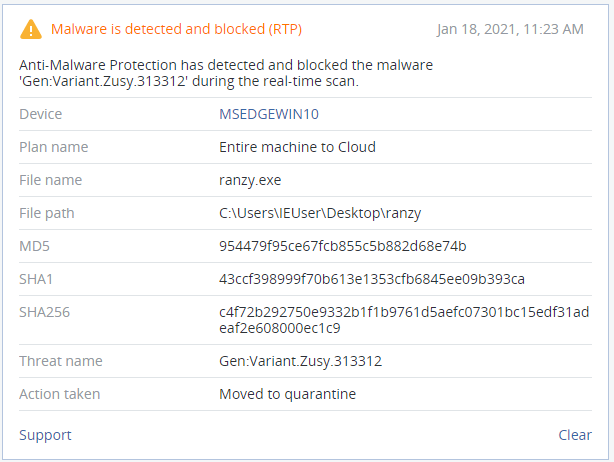
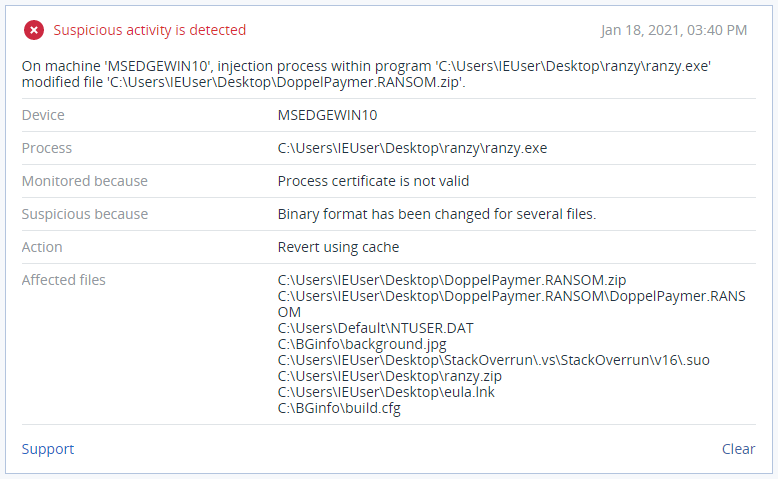
Detection by Acronis
Acronis Cyber Protect detects and blocks Ranzy Locker before it can impact your systems and encrypt your data. If the behavioral detection engine is enabled, Ranzy Locker’s activities will be suspicious enough to raise the alarm; if not, the Active Protection module will recognize it as a known threat.
IoCs
MD5: 954479f95ce67fcb855c5b882d68e74b
SHA256: c4f72b292750e9332b1f1b9761d5aefc07301bc15edf31adeaf2e608000ec1c9
Master RSA-2048 public key:
BgIAAACkAABSU0ExAAgAAAEAAQDBVEWH1TW7uudLwgn7jXIkjmyDrH9X1LuvlD0fbt1CNVnsyp6QkdS34LBVhuNMnR2WZFpWcxdrMTOGxlnfnOc6SZFpDHmL4N+e915n0EIOkDg4xFPgRa4d/OPLWkHXHEsz/hggrJP+mGroIeelzeybIXpfoQYz4joKyKCAJSoUIpG9lyWEj04bxzz1BUpSJgV0x7qSY0ciek2YURuN68gZyeZzip9dCBPmBURT9B4lpgXrgIeJv5KjsC8Lo+vwRHPhrhXGf6OMrWZDrbabTIoKj27vhMaS4np2Gpu6Df0LC865eDiVJbDgJvbwx17Bw3zDvgajia/FFhe3MJ8gmHO+
Mutex name: Global\35355FA5-07E9-428B-B5A5-1C88CAB2B488
Debug path: C:\Users\Gh0St\Desktop\ThunderX\Release\LockerStub.pdb



